Our detection team reported that they receive an IDS alert related to reconnaissance but they were unable to read the traffic as it was encrypted. Pcap files and analysis tools are available on the Desktop.
Scenario
Our detection team reported that they receive an IDS alert related to reconnaissance but they were unable to read the traffic as it was encrypted. Pcap files and analysis tools are available on the Desktop. Please note there any no issues with this lab – if you encounter a problem, try to solve it!
The Beginning
We’re supposed to use two tools that are made available for us, Wireshark and Network Miner. There are two PCAPNG files and sslkeylog.txt.
Let’s start with Tool named Network Miner. If we’d like to load PCAPNG it won’t work. 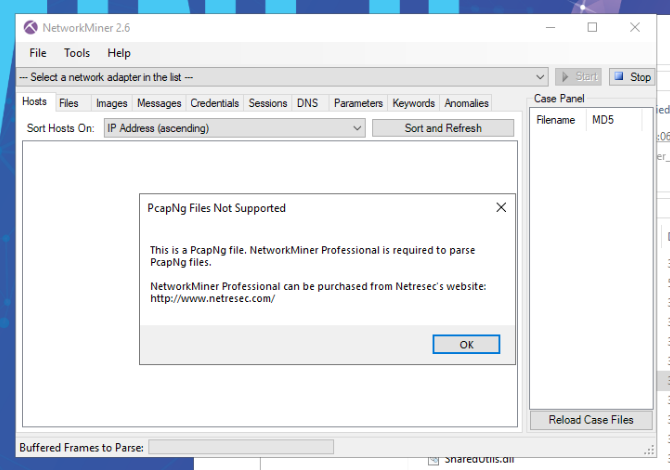
What to do? Open 1.pcapng and 2.pcapng in Wireshark and save them as .pcap and file should open in Network Miner.
Checking Anomalies found by Network Miner
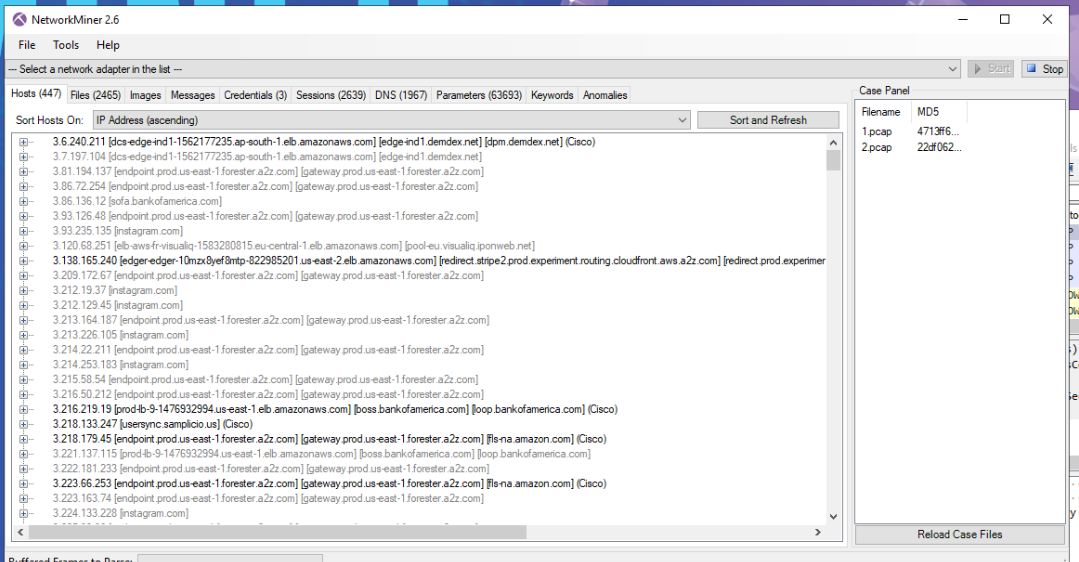
I’ve merged both files togheter into 3.pcap. Network Miner has found some anomalies, mostly speculating on EternalBlue. If we check the Frame in the Wireshark and follow TCP Stream we’ll see it’s running SMB above.
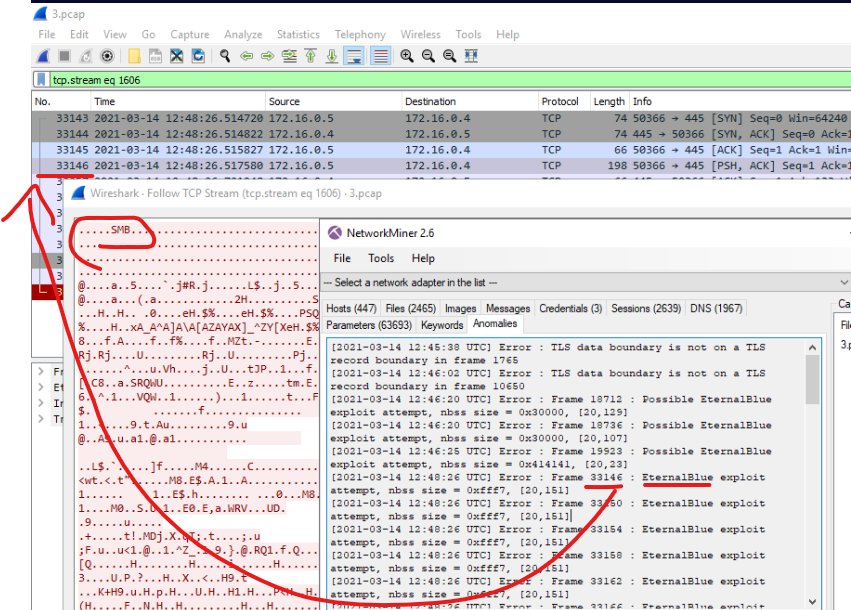
According to Network Miner, what exploit attempt is being made on what protocol? (5 points):
EternalBlue, SMB
Checking Network Miners Parameters
If we check Parameters and search for NMAP, we’d find NMAP hiding as value of SMB Native OSs paramenters.
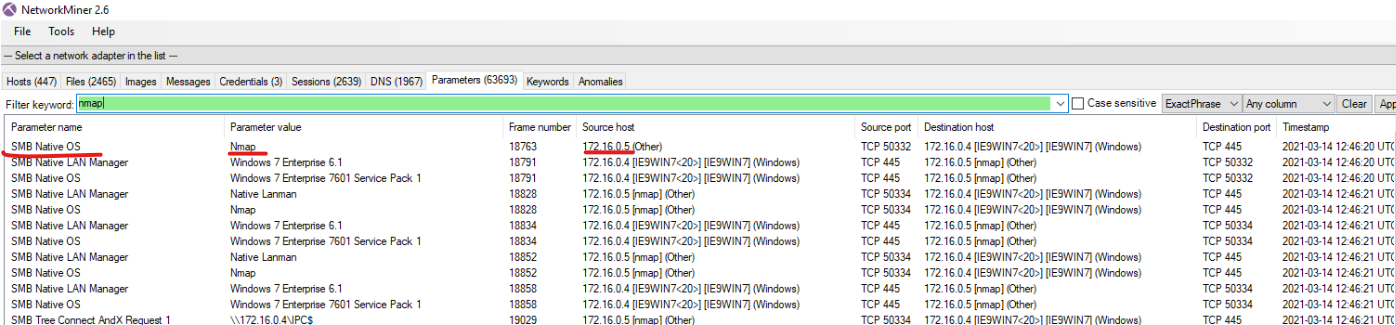
What is the IP address of the machine responsible that is conducting network scanning using Nmap? (5 points):
172.16.0.5
Finding Command and Control
In order to find the C2C server i tend (at the moment) to check statistics first. Now this may not always be possible if there’s a lot of traffic, and if that would be the case, more filtering would need to be done.
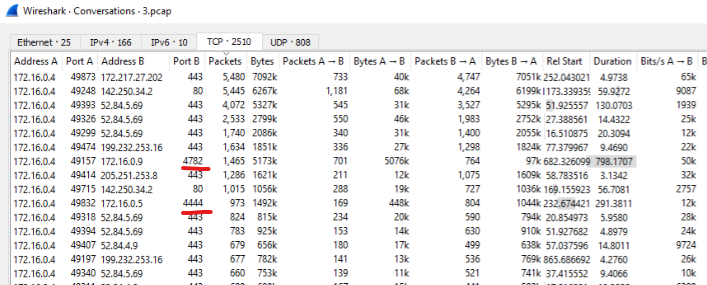
Two ports stick out, the first is 4444 which we know already from before (EternalBlue) and second one is 4782.
Checking the packets, we can see that it’s running on TLS and it’s encrypted. If we check the Certificate we can see that there is no certificate chain and CA os some Quasar Server CA.
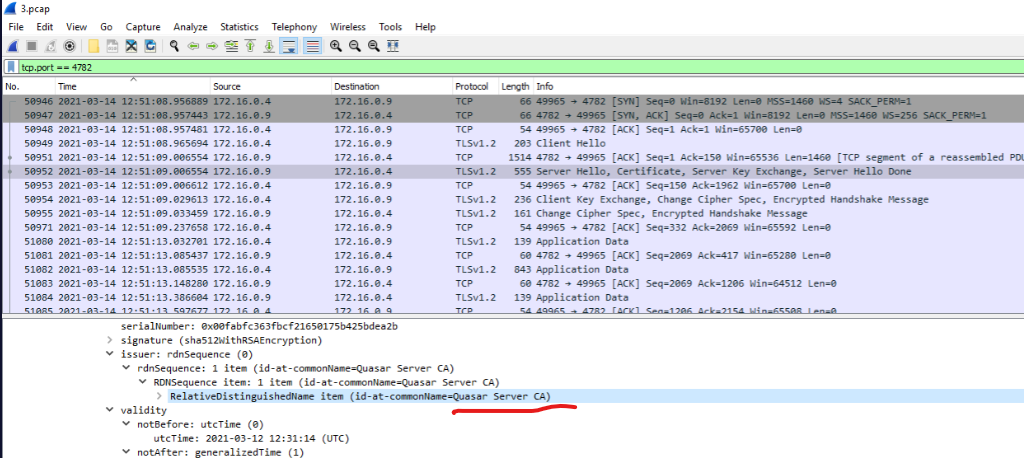
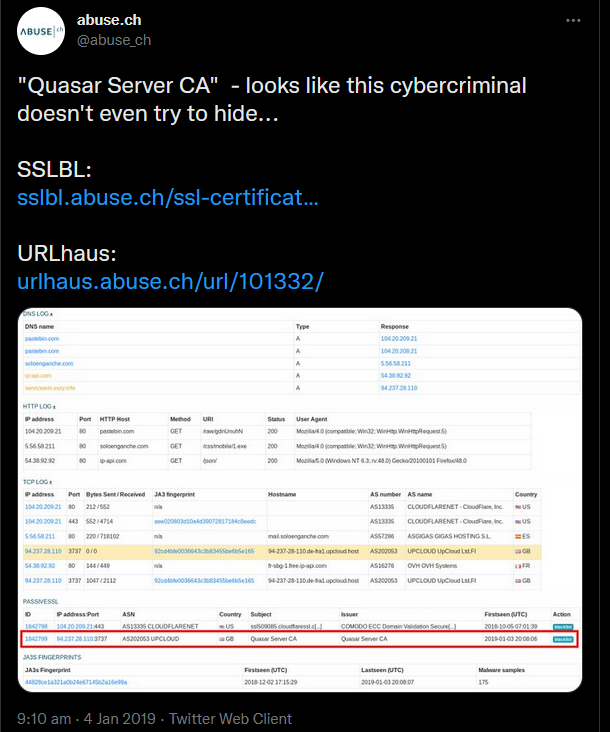
It’s weird connection to have in the internal/private network so it’s definately suspicious. Googling Quasar Server CA confirms the suspicious - first hit is some post on twitter:
We can see that filtering on Recieved Packets (Descending) the IP ranks pretty high.
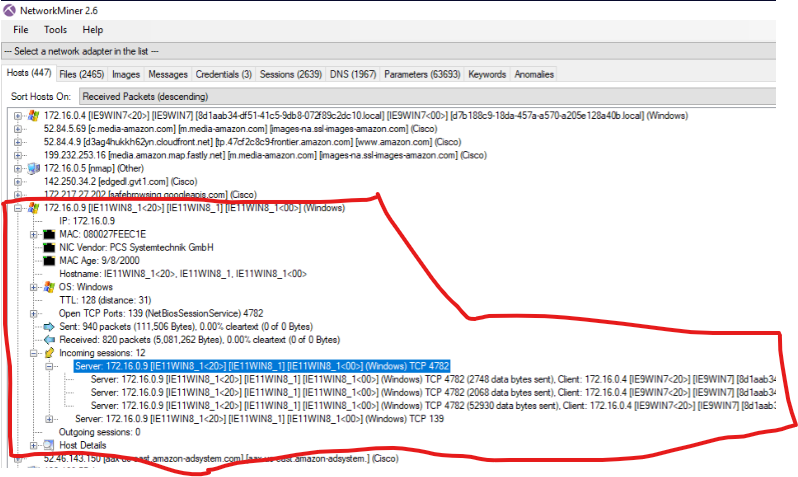
Identify the Command-and-Control server. What is the hostname, MAC address, and listening port numbers? (5 points):
IE11WIN8_1, 080027FEEC1E, 139, 4782
SSL/TLS Decryption - how?
Useful read: https://www.comparitech.com/net-admin/decrypt-ssl-with-wireshark/
Pre-master secret Keys were exported for us in sslkeylog.txt and we can import them and decrypt SSL/TLS in Wireshark 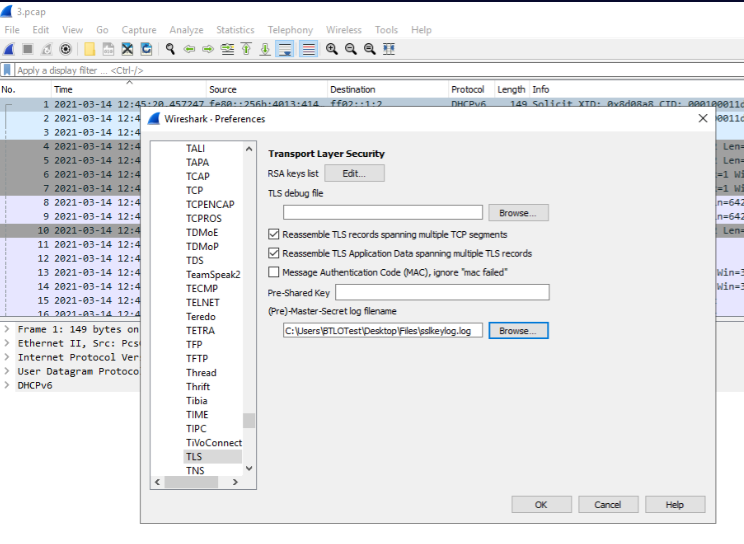
As credentials are usually sent over HTTP POST we can make use of
1
http.request.method=="POST"
We can make use of filter just by CTRL+F 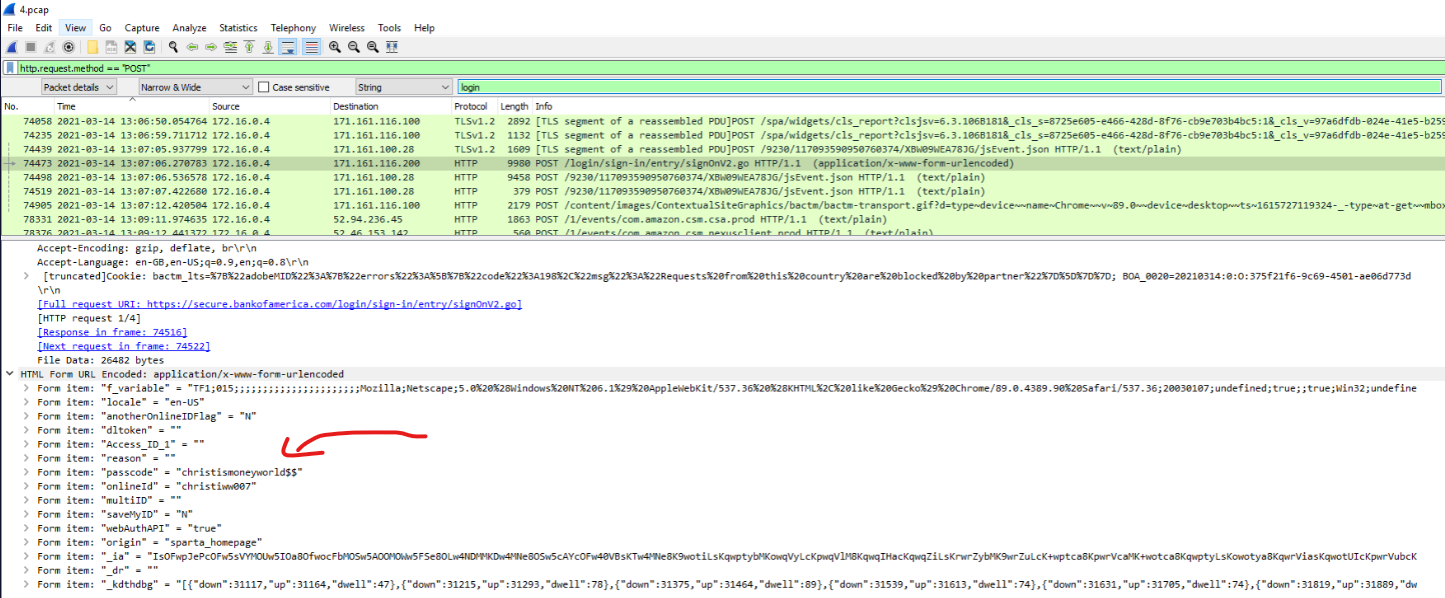
What are the banking credentials of the victim? (5 points): christiww007, christismoneyworld$$
Network Miners - Credentials found
Checking the credentials tab, there’re few hits: 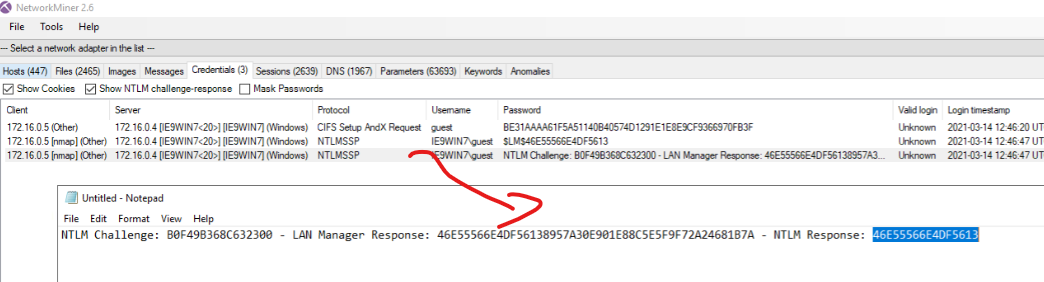
What is the observed NTLM Response for the challenge from VICTIM Machine (5 points): 46E55566E4DF5613

